Effective Employee Cybersecurity Training Programs: A Practical Guide for Business Owners
Security awareness training teaches staff how to spot cyber risks, adopt safer habits, and report concerns so your people act as a first line of defense instead of a liability. Industry data shows human error and social engineering are major drivers of breaches — well-designed training turns everyday cyber hygiene into measurable risk reduction. This guide walks business owners through designing, launching, and measuring employee security awareness programs that lower phishing success, increase incident reporting, and help meet compliance obligations.
You’ll learn why awareness matters, the core program components, a step‑by‑step implementation roadmap, how a managed service can help, which metrics prove success, and how training maps to common regulatory standards. We use terms like security awareness training, phishing simulation, human risk management, and compliance training to describe practical steps you can take to protect data and maintain business continuity.
Why employee security awareness training matters for your business
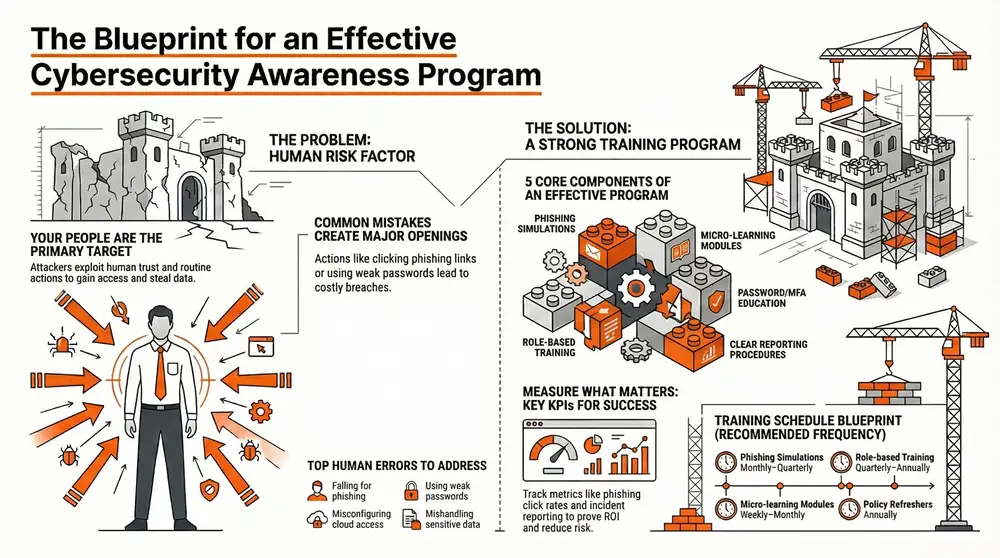
Attackers target people by exploiting trust and routine; training changes behavior, improves detection, and reduces opportunities for exploitation. Teaching staff to recognize social engineering and phishing lowers the chance of credential theft, data exposure, and costly response efforts. Training also builds a security-minded culture that supports resilience and protects reputation after an incident. The sections below unpack the typical human risks and how awareness programs cut incidents.
Employees create predictable exposure through actions like clicking malicious links, weak password habits, or mishandling sensitive files. Those mistakes can lead to credential compromise, lateral movement, or accidental data leaks — all of which drive investigation and remediation costs. Short-term mitigations (clear reporting paths and mandatory multi‑factor authentication) reduce immediate risk, while ongoing awareness programs change behavior across the workforce. Knowing these patterns helps you prioritize what to teach and which controls to pair with training.
What are the common human errors that increase cybersecurity risk?
Human error includes falling for phishing, reusing weak passwords, misconfiguring cloud permissions, or sending confidential data to the wrong recipient. These mistakes often lead to data breaches or give attackers initial access that enables ransomware and other attacks. Practical mitigations include enforcing password managers, educating staff about multi‑factor authentication, and running simulated phishing with targeted remediation for those who click. Start with a baseline assessment of behaviors and follow with regular reinforcement to lock in lasting change — which is where training’s impact becomes clear.
How does security awareness reduce breaches and phishing success?
Awareness programs reduce incidents by helping employees spot threats, report suspicious activity quickly, and adopt safer routines that eliminate attacker footholds. Training works best when it combines repetition with realistic practice — simulated phishing plus immediate feedback lowers click rates and raises reporting. Measurable outcomes include reduced phishing click‑through rates and faster time‑to‑report, which shorten attacker dwell time and limit escalation. Ongoing reinforcement and role‑specific content are essential to sustain those gains and translate training into tangible risk reduction.
Key components of an effective security awareness program
A strong program blends clear, engaging content, realistic simulations, well‑communicated policies, role‑based instruction, and meaningful measurement. Include interactive micro‑learning for retention, regular phishing simulations to test recognition, policy refreshers to align behavior, and technical education around MFA. The program must also provide straightforward incident reporting and feed results into your risk management process so behavior change informs security decisions. The table below compares common simulation cadences and delivery formats to help plan your approach.
Different cadences suit different risk profiles; this table shows typical approaches and recommended frequencies to help you choose the right mix.
This comparison shows higher‑risk groups benefit from more frequent simulations and role‑specific modules, and that combining short lessons with practical simulations improves retention. Next, we dig into how phishing simulations work and where password hygiene and MFA fit in.
When prioritizing components, focus on elements that directly change behavior and produce measurable improvement. Use this concise list as a checklist for program design.
- Phishing simulations and remediation to test and correct behavior.
- Micro-learning modules for sustained knowledge retention and brevity.
- Role-based security awareness training tailored to job-specific risks.
- Password security policies and multi-factor authentication education.
- Reporting procedures and integration with incident response workflows.
These parts work together to reduce human risk and generate evidence useful for compliance and audits.
How phishing simulations improve employee vigilance
Simulations expose employees to realistic threats in a safe environment, deliver instant feedback, and provide targeted remediation for those who click. Best practice is to vary templates, timing, and difficulty while tracking both click and reporting rates to shape follow‑up training. Pair simulations with short coaching modules that reinforce recognition cues. Interpret results by comparing baselines to targets and prioritize extra training for groups that show higher risk.
Why password hygiene and multi‑factor authentication matter
Passwords alone are vulnerable — stolen or reused credentials are a common vector for account takeover. Multi‑factor authentication (MFA) adds another barrier that greatly reduces the value of a compromised password. Teach staff how password managers work, how to create strong passphrases, and when to rotate access after incidents. Where possible, favor phishing‑resistant MFA factors and enforce MFA through policy and technical controls. Combined, password hygiene and MFA cut account compromise risk and lower the recovery burden after suspected exposure.
How to build a comprehensive security awareness training program
Building a program starts with assessment, then moves through customization, delivery, reinforcement, and continuous improvement. Benchmark current behaviors, identify high‑risk roles, and create a prioritized roadmap that aligns learning interventions to risk. Use a delivery mix of micro‑learning, simulations, and live sessions, and secure executive buy‑in to ensure policy alignment. The roadmap below gives business owners clear, actionable steps to implement a program focused on reducing human risk.
- Conduct a baseline assessment to measure phishing click rates, reporting, and knowledge gaps.
- Define role-based risk profiles and prioritize high-impact user groups for targeted training.
- Develop micro-learning modules and simulation schedules aligned to identified risks.
- Deploy training, enforce technical controls like MFA, and provide immediate remediation for failures.
- Measure KPIs, iterate content, and integrate outcomes into enterprise risk management.
This roadmap creates an iterative loop that ties behavior measurement to content updates. The sections that follow outline best practices and cadence guidance to help you execute each step.
If you need hands‑on help mapping the roadmap to your environment, managed services can fill capability gaps with assessments, content creation, and reporting. The next section covers content development best practices that feed directly into delivery and measurement.
Best practices for developing and delivering training content
Follow micro‑learning principles: short, focused lessons grounded in adult learning science and realistic scenarios. Make modules role‑aware — tailor examples to finance, HR, IT, and customer‑facing teams — and combine video, quizzes, and interactive decisions to boost engagement. Provide executive summaries and manager toolkits to encourage leadership reinforcement and accountability for completion. Well‑designed content increases retention and prepares employees to act correctly during an incident.
How often should training and reinforcement occur?
Balance frequency with fatigue: onboarding should include comprehensive initial training, then move to monthly micro‑lessons and quarterly phishing simulations for most staff. High‑risk roles may need more frequent simulations and annual deep dives. Remediation for users who fail simulations should be immediate and targeted. Continuous reinforcement — short lessons, simulated incidents, and policy reminders — sustains progress. Use metrics to adjust cadence so effort focuses where residual risk is highest.
How Concertium’s Managed Security Awareness service supports businesses
Concertium’s Managed Security Awareness service delivers end‑to‑end support: assessments, tailored content, simulated phishing, and reporting designed to reduce human risk across the enterprise. We align modules to your priorities, supplement internal teams with subject‑matter expertise, and integrate outcomes with compliance and risk processes. Key differentiators include a proactive program of ongoing simulation and measurement and audit‑ready deliverables mapped to regulatory needs. Contact Concertium to request a demo or assessment and evaluate how a managed engagement fits your organization.
Our managed approach lightens internal workloads by handling content creation, simulation cadence, and KPI reporting while advising on technical controls like MFA and password policy enforcement. This is especially valuable for small security teams or organizations without in‑house training expertise — enabling faster program launch and steady improvement based on measured results. Clients receive dashboards that translate human risk into actionable insights for leadership, accelerating risk reduction and simplifying oversight.
What unique benefits does Concertium bring to security awareness?
Concertium’s Managed Security Awareness pairs simulated phishing and micro‑learning with clear measurement and compliance mapping to deliver outcome‑focused results. Business owners can expect lower phishing click rates, streamlined audit evidence, and less operational burden on internal teams. Our service provides measurable dashboards and remediation plans that drive continuous human risk reduction — and we offer pilots or assessments to validate fit and outcomes.
How the service ties training to compliance and risk management
We map training activities to compliance frameworks by producing training records, attestation logs, and KPI dashboards auditors recognize as evidence of due diligence. Awareness metrics feed into risk registers to prioritize controls where human risk is high and supply artifacts useful for HIPAA, PCI DSS, GDPR, CMMC, and similar audits. Typical deliverables include user completion reports, simulation results, and policy acknowledgement logs that support enterprise risk programs and third‑party or insurance requirements.
How to measure the success of your security awareness program
Success starts with the right KPIs, reliable data collection, and a closed‑loop improvement process that turns impressions into action. Core KPIs include training completion rate, phishing click‑through rate, incident reporting rate, and mean time to report — together these show engagement and risk reduction. Dashboards that combine these metrics help stakeholders prioritize remediation and justify investment in awareness and complementary technical controls. The table below lists common KPIs with example baselines and targets to guide realistic goal‑setting.
Use these KPI mappings to set targets and track progress. Below are the most actionable metrics to monitor operationally.
- Phishing click-through rate: indicates susceptibility to social engineering.
- Reporting rate: reflects employee vigilance and willingness to escalate.
- Completion and remediation rates: measure program reach and corrective action.
- Time-to-detect / time-to-report: correlates with containment speed and reduced impact.
Which KPIs track engagement and real risk reduction?
Define KPIs clearly: completion rate shows engagement, phishing click rate shows susceptibility, incident reporting rate shows proactive behavior, and time‑to‑report shows detection speed. Baselines vary by industry and exposure, but staged targets work well — for example, halve phishing click rates in 12 months while raising completion above 90%. Separate behavior‑change KPIs (click and reporting rates) from administrative KPIs (module completion) so decisions focus on reducing risk. Clear definitions let leadership assess program ROI and prioritize next steps.
How to use metrics to continually improve training
Follow an analyze → adapt → test cycle: review KPI dashboards to find weak spots, tailor content for targeted groups, run focused simulations, and measure again. Prioritize groups with high click rates or low reporting and adjust content with role‑specific scenarios or mandatory remediation. Over time, metrics will show whether interventions lower risk or whether additional controls are needed. Regular KPI reviews keep training aligned with new threats and organizational change.
Many regulations expect security awareness as part of reasonable safeguards; mapping your training to those frameworks creates demonstrable due diligence. Training artifacts — completion logs, policy acknowledgements, and drill records — help during audits and strengthen contractual and insurance positions. The table below maps common regulations to their training expectations and typical evidence to keep on file.
Keeping these deliverables organized streamlines audits and demonstrates proactive control of human risk. The next section explains how training maps to specific framework expectations.
How training supports HIPAA, PCI DSS, GDPR, and CMMC compliance
Training ties to each framework by addressing workforce controls: privacy and handling of protected information, secure card data processing, safe personal data handling, and cybersecurity practices for controlled information. Evidence includes completion records, updated policies, and simulation outcomes for sensitive roles. For auditors, those artifacts show the organization educated staff and monitored effectiveness — which can reduce regulatory and contractual exposure and support insurance discussions.
Why demonstrating due diligence matters for business owners
Documented training reduces legal exposure, supports insurance claims, and reassures customers and partners that you manage human risk deliberately. Clear training records tell a story of preventive steps taken before an incident, which can mitigate liability and speed discussions with regulators or insurers. Maintaining artifacts and showing continuous improvement are practical governance signals that influence third‑party risk assessments and contracts — making training a critical part of enterprise resilience.
Frequently Asked Questions
What challenges do businesses commonly face when rolling out security awareness training?
Common challenges include employee resistance, low engagement, and limited resources for ongoing delivery. Organizations also struggle to tailor content by role and keep material relevant. Overcome these issues with executive sponsorship, regular employee feedback, and interactive, scenario‑based content that keeps learning practical and engaging.
How can organizations keep their training programs effective over time?
Adopt a continuous improvement approach: regularly measure performance (phishing click rates, reporting), use feedback to refine content, and add refresher courses when threats change. Maintain a feedback loop that adapts content to new risks and employee needs so awareness stays current and effective.
What role should leadership play in a successful security awareness program?
Leaders set the tone. When executives participate and communicate the importance of security, employees take training more seriously. Leadership support also secures funding and ensures accountability by tying security awareness to performance goals.
How can businesses measure the ROI of security awareness training?
Measure ROI by tracking KPIs such as reduced phishing click rates, increased incident reporting, and improved completion and remediation rates. Quantify cost savings from avoided incidents and compare them to program costs to assess value. Dashboards that translate behavior change into risk reduction help justify continued investment.
What delivery methods work best for security awareness training?
Use a mix of micro‑learning, interactive simulations, and live sessions. Micro‑learning fits into busy schedules, simulations provide hands‑on practice, and live sessions add context for high‑risk groups. Gamification and on‑demand resources can boost engagement and retention.
How can organizations tailor training by role?
Start with a role‑based risk assessment to identify specific threats and responsibilities. Customize scenarios and examples for departments like finance, IT, and customer service so employees see how security applies to their daily work. Role‑specific training makes the content more relevant and actionable.
What happens if an organization neglects employee cybersecurity training?
Neglecting training increases vulnerability to attacks, data breaches, and financial loss. Employees may fall for phishing or mishandle sensitive information, leading to reputational damage and regulatory penalties. Investing in training is one of the most cost‑effective ways to reduce these risks.
Conclusion
Effective security awareness training strengthens your organization by turning employees into active defenders. Focus on tailored content, realistic simulations, and continuous measurement to reduce risks tied to human error and to meet compliance needs. If you need help getting started or scaling your program, managed services like Concertium’s can streamline delivery and provide expert support. Begin by assessing your current training gaps and take the first step toward a more secure workplace today.