A cloud security operations center is a centralized cybersecurity hub built on cloud infrastructure that monitors, detects, and responds to threats across your organization’s cloud environments 24/7. Unlike traditional SOCs that rely on on-premise hardware, cloud SOCs offer scalable, flexible, and cost-effective security operations powered by cloud-native tools and automation.
Key Benefits of a Cloud Security Operations Center:
- 24/7 threat monitoring across all cloud platforms and hybrid environments
- Faster incident response – organizations reduce detection time from hours to 15-30 minutes
- Scalable security that grows with your business without hardware investments
- Cost efficiency through subscription models vs. capital expenditure
- Advanced threat detection using AI, machine learning, and automated analysis
- Centralized visibility into multi-cloud environments from a single dashboard
The shift to cloud computing has fundamentally changed how businesses operate. According to Gartner research, 57% of board directors are preparing for greater risk as organizations adapt to cloud environments. This isn’t surprising – when your data, applications, and infrastructure move to the cloud, your security operations must evolve too.
Traditional security perimeters are dissolving. Your employees work from anywhere, your applications run across multiple cloud providers, and your data flows through networks you don’t control. The old model of fortress-like security with firewalls protecting a defined perimeter simply doesn’t work anymore.
This change creates both challenges and opportunities. While cloud adoption increases your attack surface, it also enables more sophisticated, scalable security operations. A cloud SOC doesn’t just monitor your systems – it becomes the nerve center that unifies all your security technologies and operations into a single, powerful defense mechanism.
The good news? Organizations implementing modern cloud SOCs report impressive results. Some achieve 240% ROI and can process 22 times more security data while closing investigations in half the time compared to traditional approaches.
Explore more about cloud security operations center:
What is a Cloud SOC and How Does It Differ from a Traditional SOC?
Think of a Security Operations Center (SOC) as your organization’s digital security command center. It’s where cybersecurity professionals work around the clock to monitor, detect, analyze, and respond to threats that could harm your business. Just like air traffic controllers keep planes safe in the sky, SOC teams keep your digital assets safe from cyber threats.
Now, here’s where things get interesting. A cloud security operations center takes this concept and boosts it by running entirely on cloud infrastructure. This isn’t just about watching over your cloud applications – it’s about using the cloud’s power to run your entire security operation.
The fundamental difference is like comparing a traditional brick-and-mortar store to an online marketplace. Traditional SOCs are built on physical hardware that sits in your data center. You buy servers, install software, and manage everything yourself. It’s reliable, but it’s also expensive, slow to change, and limited by what you can physically fit in your building.
A cloud security operations center operates completely differently. Instead of owning all that hardware, you tap into the vast computing power of cloud providers. This means you can scale up instantly when threats spike, access cutting-edge security tools without buying them, and analyze massive amounts of data that would overwhelm traditional systems.
The scalability difference is remarkable. Traditional SOCs require careful planning to expand. Need more processing power? You’ll need to budget for new servers, wait for delivery, install them, and configure everything. With a cloud SOC, you can double your capacity in minutes, not months.
Cost structures tell a different story too. Traditional SOCs demand huge upfront investments – sometimes millions of dollars for enterprise-grade hardware and software licenses. Cloud SOCs work more like a subscription service. You pay for what you use, when you use it, turning massive capital expenses into predictable monthly costs.
Here’s a clear comparison of the two approaches:
| Feature | Traditional SOC | Cloud SOC |
|---|---|---|
| Infrastructure | Physical servers and networking equipment in your data center | Cloud-native services that scale automatically |
| Scalability | Manual hardware purchases and installations | Instant, elastic scaling based on demand |
| Cost Model | Large upfront capital investment plus ongoing maintenance | Monthly subscription with pay-as-you-grow pricing |
| Data Sources | Limited by local storage and processing power | Can ingest data from anywhere – multi-cloud, SaaS, on-premise |
| Updates & Maintenance | Your IT team handles everything manually | Cloud provider manages infrastructure updates automatically |
| Flexibility | Changes require planning, purchasing, and installation | Adapt to new threats and requirements instantly |
The data ingestion capabilities alone make cloud SOCs game-changers. Traditional SOCs often struggle with data silos – your email security data might not talk to your network monitoring tools. Cloud SOCs excel at bringing together security data from everywhere: your AWS environment, Microsoft 365, on-premise servers, and even that new SaaS tool your marketing team started using last month.
For organizations still getting familiar with SOC fundamentals, our guide What is a SOC? Understanding Security Operations Centers provides deeper context on how these security command centers operate.
The bottom line? While traditional SOCs served us well in simpler times, today’s distributed, cloud-first business environment demands the agility and power that only a cloud security operations center can provide. It’s not just an upgrade – it’s a complete reimagining of how security operations should work in the modern world.
Designing an Efficient Cloud SOC: The Three Pillars
Building an effective cloud security operations center is like constructing a house – you need a solid foundation built on three essential pillars: Technology, People, and Process. Skip any one of these, and your entire security operation becomes wobbly. It’s not enough to simply migrate your existing tools to the cloud and call it a day.
Think of it this way: you wouldn’t build a race car by simply painting flames on a regular sedan. Similarly, designing a cloud security operations center requires intentional architecture focused on proactive security, intelligent automation, and seamless integration. We’re moving beyond the old “wait and see” approach to actually staying ahead of threats.
This means anticipating attacks before they happen, automating the routine stuff so your security experts can focus on the complex challenges, and ensuring all your tools work together like a championship team. To see how we put these principles into practice, check out our Advanced SOC Services.
Technology: The Engine of Your Cloud SOC
Technology forms the beating heart of any modern cloud security operations center, but we’re not talking about your grandfather’s security tools. Cloud-native capabilities have completely transformed what’s possible in security operations.
Cloud-native SIEM serves as the central nervous system where all your security data converges. Modern SIEM platforms can handle massive data volumes that would have crashed traditional systems. We’re talking about processing 22 times more security data while actually making it easier to find the needle in the haystack. These platforms provide lightning-fast queries on streaming data, which is crucial when every second counts during an incident.
SOAR platforms bring the magic of automation to security operations. Think of SOAR as your incredibly efficient digital assistant that never needs coffee breaks. It handles routine tasks like alert triage, data enrichment, and initial response actions through predefined playbooks. This frees up your skilled analysts to tackle the complex investigations that truly require human creativity and intuition.
Threat intelligence platforms help us stay one step ahead of attackers by integrating intelligence from multiple sources. Instead of playing defense all the time, we can actually predict and prevent attacks. It’s like having a crystal ball that shows you what the bad guys are planning next.
Extended Detection and Response (XDR) takes security visibility to the next level. Rather than looking at just endpoints or networks in isolation, XDR provides a holistic view across your entire digital environment – endpoints, networks, cloud platforms, and applications all working together to tell the complete story of what’s happening in your infrastructure.
Log management and analytics might sound boring, but it’s absolutely critical. Many attackers count on organizations not properly analyzing their log data, allowing malware to hide in plain sight. With cloud-native solutions, we can store and analyze virtually unlimited amounts of log data without worrying about running out of storage space.
AI and machine learning capabilities are woven throughout these technologies, automatically improving threat detection accuracy over time and even helping with investigations by summarizing complex data and recommending response actions. It’s like having a security expert who never gets tired and keeps getting smarter.
For more details on how we leverage these powerful technologies, explore our Threat Detection and Response Solutions.
People: The Critical Roles in a cloud security operations center
While technology provides the tools, people bring the expertise, judgment, and creativity that make a cloud security operations center truly effective. Building the right team requires understanding both traditional security roles and the unique demands of cloud environments.
SOC Managers serve as the strategic leaders who orchestrate the entire operation. They’re responsible for resource allocation, team development, compliance oversight, and ensuring everyone is working toward common goals. Think of them as the conductor of a security symphony.
Security Engineers are the architects who design, build, and maintain your cloud security infrastructure. They ensure your defenses are not just robust today, but can evolve with changing threats and business needs. These folks live and breathe cloud security technologies.
SOC Analysts operate in three specialized tiers, each with distinct responsibilities. Tier 1 Analysts handle initial alert triage, filtering out false positives and escalating genuine threats. Tier 2 Analysts dive deeper into complex investigations and guide remediation efforts. Tier 3 Analysts are your elite threat hunters who proactively search for hidden threats that automated systems might miss.
Threat Hunters deserve special mention because they’re like cybersecurity detectives, constantly looking for clues that something isn’t quite right. They use advanced techniques and intelligence to uncover threats that have managed to slip past your automated defenses.
Incident Response Specialists are your emergency response team. When things go wrong, they lead containment, eradication, and recovery efforts while ensuring minimal business disruption.
Compliance Auditors ensure all security operations meet regulatory requirements – and in the cloud, compliance complexity multiplies across different jurisdictions and frameworks.
Close collaboration with DevSecOps teams is essential in cloud environments. Security can’t be an afterthought bolted on at the end; it needs to be baked into development processes from day one.
For specialized industries, staffing considerations become even more nuanced. Learn about custom approaches in our guide to Cloud Security Strategies for Private Equity.
Process: The Blueprint for Success
Even with cutting-edge technology and brilliant people, a cloud security operations center needs well-defined processes to function effectively. Processes provide the roadmap that guides actions, ensures consistency, and prevents chaos during high-stress situations.
Incident response planning forms the foundation of effective security operations. When an attack happens, there’s no time to figure out who does what. A comprehensive incident response plan defines clear roles, communication protocols, containment strategies, and recovery procedures. We regularly test and refine these plans because theory and reality don’t always match.
Proactive threat hunting goes beyond simply responding to alerts. Our threat hunters actively seek out threats using hypothesis-driven investigations and advanced analytics. They’re constantly asking “what if” questions and looking for subtle patterns that might indicate compromise. This proactive approach often uncovers threats that would otherwise remain hidden for months. Learn more about this critical capability in our Proactive Threat Hunting guide.
Vulnerability management ensures we’re continuously identifying and addressing security weaknesses before attackers can exploit them. This includes regular assessments, penetration testing, and maintaining current patches and configurations across dynamic cloud environments.
Compliance monitoring has become more complex in cloud environments where data flows across multiple jurisdictions and platforms. Our processes ensure continuous adherence to regulations like GDPR, HIPAA, and industry-specific requirements while maintaining detailed audit trails.
Continuous improvement recognizes that security is never “finished.” The threat landscape evolves constantly, and so must our defenses. We regularly analyze our performance, learn from incidents, and adapt our strategies based on new intelligence and emerging threats.
Business continuity considerations are woven throughout all our processes. Security incidents will happen, but robust processes ensure your business can recover quickly and continue operating with minimal disruption.
These processes work together to create a cloud security operations center that’s not just reactive, but truly proactive in defending your cloud infrastructure and enabling your business success.
The Top Benefits of a cloud security operations center
Adopting a cloud security operations center is more than just a technological upgrade; it’s a strategic move that fundamentally transforms how your organization approaches cybersecurity. Think of it as upgrading from a neighborhood watch to a sophisticated security command center that never sleeps.
The change begins with dramatically improved threat detection. When your cloud security operations center can ingest and analyze massive volumes of data from every corner of your digital environment, it becomes incredibly good at spotting trouble. Modern cloud-native SIEM and XDR solutions don’t just collect data – they use AI and machine learning to identify complex attack patterns that would slip past traditional systems. It’s like having a security expert who never gets tired and can simultaneously watch thousands of data streams for the tiniest anomaly.
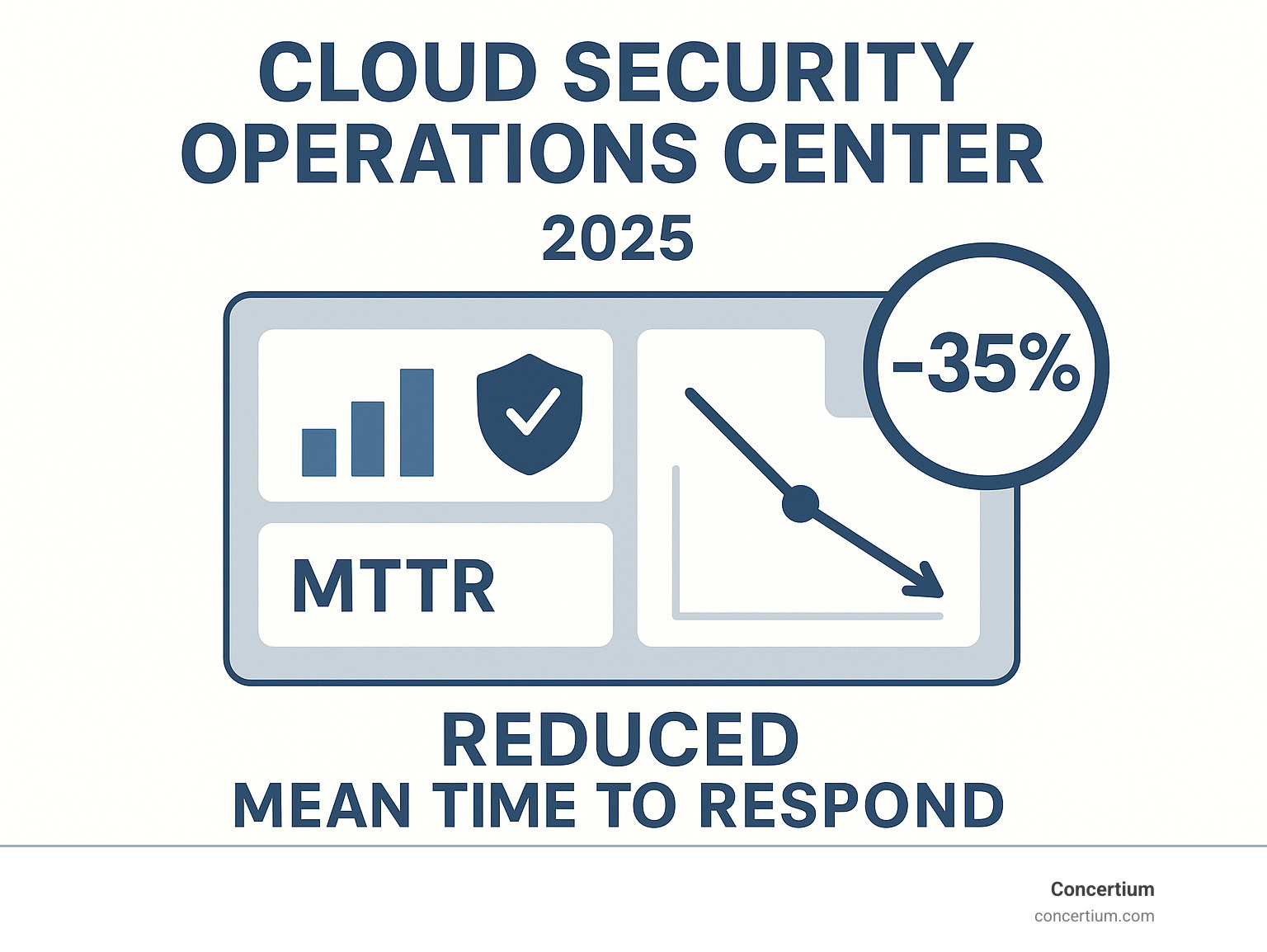
But detecting threats quickly means nothing if you can’t respond just as fast. This is where cloud security operations center solutions truly shine with lightning-fast response times. Through automation and orchestration, what used to take hours now happens in minutes. Some organizations have cut their detection and investigation time from 2 hours down to just 15-30 minutes. When you’re dealing with a cyberattack, every minute counts – and those saved minutes can mean the difference between a minor incident and front-page news.
The scalability and flexibility of cloud-based security operations is genuinely game-changing. Your security doesn’t just grow with your business; it adapts to whatever you throw at it. Expanding into new cloud platforms? Your SOC scales automatically. Facing a spike in threats during a busy season? Resources adjust on demand. It’s security that bends without breaking, no matter how your business evolves.
Let’s talk about something every CFO loves: significant cost savings. Moving to a cloud security operations center shifts you from the old model of buying expensive hardware upfront to a predictable subscription approach. No more surprise maintenance bills, no more obsolete equipment gathering dust, and no more emergency hardware purchases. Organizations implementing modern cloud SOCs often see impressive returns – some report 240% ROI while processing vastly more security data than ever before.
Perhaps most importantly, a cloud security operations center gives you centralized visibility across your entire digital ecosystem. Whether your data lives in AWS, Azure, Google Cloud, or still sits in your on-premise servers, you get one clear picture of your security posture. No more blind spots, no more security silos, and no more guessing games about what’s happening in different parts of your infrastructure.
All of these benefits work together to create something powerful: peace of mind. When your security operations are running smoothly in the cloud, you’re not just protecting your data – you’re enabling your business to innovate confidently. Your teams can focus on growth instead of constantly worrying about the next potential breach.
To explore how these benefits can be custom to your specific needs, consider our comprehensive Managed Detection and Response (MDR) services, which bring all these advantages together in a unified security solution.
Overcoming Key Challenges and Implementing Best Practices
While the benefits of a cloud security operations center are compelling, the path to implementation isn’t always smooth sailing. Think of it like building a sophisticated security command center in the cloud – you need to steer some tricky terrain along the way! The good news? We’ve helped countless organizations overcome these problems, and we’re here to share what we’ve learned.
The reality is that every organization faces unique challenges when transitioning to cloud-based security operations. Some struggle with technical integration issues, others grapple with skills gaps, and many find themselves overwhelmed by the sheer complexity of modern cloud environments. But here’s the thing – these challenges are absolutely surmountable with the right approach and guidance.
Understanding these obstacles upfront allows you to plan better and avoid common pitfalls that can derail your cloud security operations center initiative. Let’s explore the most common challenges we see and, more importantly, how to overcome them.
For organizations looking to build a solid foundation, our Cybersecurity Risk Management Frameworks provide essential guidance for navigating these complexities.
Common Implementation Problems
The journey to an effective cloud security operations center often involves navigating several key challenges that can trip up even well-prepared organizations.
Maintaining visibility and control across distributed cloud environments tops the list of concerns. When your infrastructure spans multiple cloud providers, on-premise systems, and countless SaaS applications, getting a complete picture becomes incredibly complex. Shadow IT deployments and configuration drift can create blind spots faster than you can say “security incident.” It’s like trying to monitor a city from space when half the streetlights keep moving around!
Integration complexity presents another significant hurdle. Most organizations aren’t starting from scratch – they have existing security tools, legacy systems, and established workflows. Making all these pieces work together harmoniously with your new cloud SOC tools requires careful orchestration. APIs don’t always play nicely together, and data formats can be frustratingly inconsistent across different platforms.
Data privacy and compliance considerations become even more nuanced in the cloud. You’re not just worried about securing your own data center anymore – you need to understand how your cloud providers handle data, where it’s stored geographically, and how to maintain compliance across multiple jurisdictions. The shared responsibility model means you’re still accountable for security, even when you don’t directly control the underlying infrastructure.
The cloud security skills gap remains one of the most pressing challenges. The rapid evolution of cloud technologies has outpaced the development of skilled professionals who truly understand cloud-native security. Finding analysts who can think beyond traditional network perimeters and understand the intricacies of container security, serverless architectures, and cloud-native attack vectors can feel like searching for unicorns.
Vendor lock-in concerns keep many security leaders awake at night. Becoming too dependent on a single cloud provider or security vendor can limit your flexibility and potentially increase costs over time. The fear of being painted into a corner often leads to analysis paralysis or overly complex multi-vendor architectures.
Alert fatigue becomes amplified in cloud environments where the volume of security events can be overwhelming. When your SOC analysts are drowning in notifications, critical threats can slip through the cracks. It’s the cybersecurity equivalent of crying wolf – eventually, people stop paying attention.
Best practices for your cloud security operations center
Successfully implementing and operating a cloud security operations center requires a strategic approach that addresses these challenges head-on. Here’s what we’ve learned works best in the real world.
Automation becomes your secret weapon for managing the complexity and volume of cloud security operations. By automating repetitive tasks like initial alert triage, data enrichment, and standard response procedures, you free up your skilled analysts to focus on the complex investigations that truly require human expertise. Think of automation as your security team’s force multiplier – it doesn’t replace human judgment, but it makes human judgment more effective.
Integrating comprehensive threat intelligence transforms your cloud security operations center from reactive to proactive. When you combine internal security data with external threat feeds, industry intelligence, and global attack indicators, you can anticipate threats before they hit your environment. It’s like having an early warning system that helps you prepare for storms before they arrive.
Developing and regularly testing a clear incident response plan cannot be overstated. When a security incident occurs, chaos often follows – unless you have a well-rehearsed playbook. Your incident response plan should define roles clearly, establish communication protocols, and outline step-by-step procedures for containment, eradication, and recovery. Regular tabletop exercises help ensure everyone knows their part when the pressure is on. Learn more about building effective response capabilities with our guide on Incident Response Cybersecurity.
Ensuring compliance with regulatory standards like GDPR, HIPAA, and PCI DSS requires ongoing attention in cloud environments. The dynamic nature of cloud infrastructure means compliance isn’t a one-time checkbox – it’s an ongoing process of monitoring, auditing, and adjusting. Your cloud security operations center should include automated compliance monitoring and regular assessment capabilities. For comprehensive guidance on this critical area, explore our insights on Cybersecurity Compliance Standards.
Fostering collaboration with DevOps teams through a DevSecOps approach ensures security becomes an enabler rather than a roadblock. When security is embedded into the development lifecycle from the beginning, you catch vulnerabilities early, reduce deployment risks, and create a culture where security is everyone’s responsibility. This collaboration helps bridge the gap between rapid innovation and robust security.
The key to success lies in viewing these best practices not as separate initiatives, but as interconnected elements of a comprehensive security strategy. When implemented thoughtfully, they transform potential obstacles into competitive advantages, making your cloud security operations center a powerful business enabler rather than just a necessary expense.
Frequently Asked Questions about Cloud SOCs
When organizations consider implementing a cloud security operations center, they naturally have questions about how it works, what it can do, and how it might fit into their existing security infrastructure. Let’s address the most common questions we hear from our clients.
What is the primary goal of a cloud security operations center?
The heart of any cloud security operations center is simple yet powerful: to keep your digital assets safe around the clock. Think of it as having a team of expert security guards who never sleep, never take breaks, and have superhuman abilities to spot trouble before it becomes a crisis.
More specifically, a cloud security operations center provides continuous 24/7 monitoring, detection, analysis, and response to cybersecurity threats across your cloud and hybrid environments. But it’s not just about watching for bad things to happen – it’s about preventing them from happening in the first place.
The ultimate goal goes beyond just security, though. We’re here to ensure your business can operate smoothly and confidently in the cloud. When your security operations are running efficiently, your teams can focus on innovation and growth rather than worrying about the next potential cyber attack. It’s about enabling business continuity while maintaining the highest levels of data and application security.
Can a cloud SOC monitor on-premise systems as well?
Absolutely! This is one of the most beautiful aspects of a modern cloud security operations center – it doesn’t discriminate based on where your systems live.
Your organization probably isn’t 100% cloud-native (few are), and that’s perfectly normal. You might have critical applications still running on-premise, legacy systems that can’t easily move to the cloud, or a hybrid setup that spans multiple environments. A well-designed cloud security operations center treats all of these as part of one unified security ecosystem.
We can ingest and analyze security data from virtually anywhere: your on-premise infrastructure, multiple cloud environments like AWS, Azure, and Google Cloud Platform, SaaS applications your teams use daily, and even IoT devices scattered throughout your organization. The magic happens when all this disparate data comes together in a single, unified dashboard.
This comprehensive approach is especially crucial in today’s business environment, where the traditional network perimeter has essentially disappeared. Your data flows between on-premise servers, cloud applications, remote workers’ devices, and third-party services. A cloud security operations center gives you that single pane of glass to see everything that’s happening across your entire digital footprint.
How does a cloud SOC improve incident response times?
Speed matters in cybersecurity – sometimes it’s the difference between a minor inconvenience and a business-threatening disaster. A cloud security operations center transforms incident response from a manual, time-consuming process into a swift, coordinated defense.
The secret sauce lies in automation and orchestration. When our systems detect a potential threat, they don’t just send an alert and wait for someone to notice. Instead, they immediately execute predefined playbooks through SOAR (Security Orchestration, Automation, and Response) platforms. These playbooks can automatically gather additional context, cross-reference threat intelligence databases, and even begin initial containment actions – all while a human analyst is still being notified.
But it’s not just about automation. Our analysts work with rich contextual data and integrated threat intelligence, which means they don’t have to spend precious minutes (or hours) figuring out what they’re looking at. When they receive an alert, they already have the full story: what happened, when it happened, what systems are affected, and what similar attacks have looked like in the past.
The results speak for themselves. Organizations that implement modern cloud security operations center approaches often see dramatic improvements in their response times. Some of our clients have reduced their time from detection to investigation from 2 hours down to just 15-30 minutes. In the cybersecurity world, that’s like going from a horse-drawn carriage to a sports car – the difference can literally save your business.
This speed isn’t just about technology, though. It’s about having the right processes in place, the right people with cloud security expertise, and systems that work together seamlessly. When everything clicks, incident response becomes less like emergency firefighting and more like a well-orchestrated performance.
Conclusion
The digital change has brought us incredible opportunities, but it’s also rewritten the rules of cybersecurity. As your business moves to the cloud, your security operations must evolve too. A cloud security operations center isn’t just keeping up with the times – it’s becoming the cornerstone of modern cybersecurity strategy.
Throughout this guide, we’ve explored how a cloud security operations center fundamentally differs from traditional approaches. The scalability means your security grows with your business without the headache of hardware procurement. The flexibility allows you to adapt quickly to new threats and business needs. The cost efficiency transforms security from a massive capital investment into predictable operational expenses.
Remember those three pillars we discussed? Technology provides the cloud-native tools and AI-powered automation that can process 22 times more security data than traditional systems. People bring the expertise and human insight that no algorithm can replace. Processes create the framework that turns chaos into coordinated defense. When these pillars work together, magic happens – response times drop from hours to minutes, and security becomes a business enabler rather than a roadblock.
The benefits are real and measurable. Organizations report 240% ROI, dramatically faster incident response, and the peace of mind that comes from centralized visibility across their entire digital landscape. Yes, there are challenges like skill gaps and integration complexity, but these problems become stepping stones with the right approach and partnership.
The future of SecOps is here, and it’s cloud-native. It’s about proactive defense that anticipates threats rather than just reacting to them. It’s about creating a security posture that’s as agile and innovative as the cloud environments it protects.
At Concertium, we’ve spent nearly 30 years perfecting cybersecurity solutions, and our Collective Coverage Suite (3CS) with AI-improved observability represents the cutting edge of cloud security operations. We understand that every organization’s cloud journey is unique, and we’re here to help you steer the complexities with confidence.
Your cloud environment deserves security that’s as sophisticated as your business ambitions. Ready to transform your cybersecurity from a necessary expense into a competitive advantage? Strengthen your defenses with our Managed Cybersecurity and Cloud Security services.