A vulnerability risk assessment is a systematic process that identifies, evaluates, and prioritizes security weaknesses in your organization’s IT systems, applications, and infrastructure. It’s a proactive health checkup for your cybersecurity defenses, designed to find and fix problems before they become serious threats.
Quick Answer – Vulnerability Risk Assessment:
- Definition: A process to find and fix security weaknesses before attackers exploit them.
- Purpose: Proactive defense against cyber threats and data breaches.
- Benefits: Reduces risk, ensures compliance, and protects reputation.
- Frequency: Continuous monitoring with formal assessments at least quarterly.
- Cost: Significantly cheaper than recovering from a successful cyberattack.
According to IBM’s 2023 Cost of a Data Breach Report, the average cost of a data breach has hit $4.45 million. More importantly, organizations with robust security controls saved an average of $1.76 million compared to those without.
In today’s threat landscape, it’s not a matter of if you’ll face a cyberattack, but when. A vulnerability risk assessment provides a clear roadmap to find and fix security gaps before criminals can exploit them. It helps you answer critical questions: What systems are vulnerable? Which threats pose the greatest risk? Where should you invest your limited security budget?
Why Proactive Cybersecurity is Essential
Every part of our digital infrastructure, from customer databases to internal communication tools, is a potential target for threat actors—cybercriminals, state-sponsored groups, or even insiders. The financial fallout from a successful attack can be catastrophic, including long-term reputational damage, loss of customer trust, and regulatory fines.
Furthermore, regulatory compliance with laws like GDPR and HIPAA often mandates regular security assessments. By conducting these assessments, you not only protect your assets but also demonstrate due diligence, building trust with customers and stakeholders. This process is key to building cyber resilience—the ability to prepare for, respond to, and recover from cyberattacks.
5 Signs Your Organization Needs a Vulnerability Assessment
Here are five indicators that it’s time to schedule an assessment:
- Outdated or Unpatched Software: Running older software versions or being behind on security patches leaves your systems exposed to known, easily exploitable vulnerabilities.
- Increase in Security Incidents or Alerts: An uptick in phishing attempts, malware, or unusual network activity can indicate underlying weaknesses that a comprehensive assessment can uncover.
- Recent Network or Infrastructure Expansion: Migrating to the cloud, opening a new office, or adding a new application expands your attack surface, potentially introducing new vulnerabilities.
- New or Updated Compliance Requirements: Evolving regulations often require organizations to demonstrate a robust security posture, which includes regular assessments.
- Infrequent or Outdated Security Audits: If your last formal security audit was over a year ago, your defenses are likely out of sync with the current, rapidly evolving threat landscape.
Core Concepts: Vulnerability, Threat, and Risk Explained
Understanding a vulnerability risk assessment requires grasping three core concepts: vulnerabilities, threats, and risks. These elements are the ingredients for a security incident. A vulnerability is a weakness, a threat is an actor who might exploit it, and risk is the potential for harm if they succeed.
Every assessment aims to protect the CIA Triad: Confidentiality (keeping data private), Integrity (ensuring data is accurate), and Availability (making sure systems are accessible). When a threat exploits a vulnerability, one or more of these pillars is compromised.
Vulnerability: The Weak Link in Your Security Chain
A vulnerability is any weakness, flaw, or gap in your digital armor that could be exploited. These aren’t always malicious; they can be simple oversights or configuration mistakes.
- Technical vulnerabilities include unpatched software, misconfigured firewalls, weak encryption, or default passwords. The MOVEIT Transfer vulnerability, a technical flaw in file transfer software, led to massive data breaches.
- Human vulnerabilities are just as dangerous. These involve people and processes, such as an employee clicking a phishing link, using a weak password, or accidentally sharing sensitive data. A significant percentage of data breaches begin with the exploitation of a human vulnerability.
Threat: The Adversary and Their Intent
A threat is any person or event with the potential to harm your systems by exploiting a vulnerability. Threats have three components: opportunity (a vulnerability), capability (skills and tools), and intent (motivation).
- Malicious threats include cybercriminals seeking financial gain, state-sponsored actors targeting intellectual property, hacktivists driven by ideology, and insider threats from disgruntled employees.
- Non-malicious threats can be just as damaging. These include natural disasters, hardware failures, and unintentional errors made by well-meaning employees.
Common cyber threats include malware, phishing, and denial-of-service (DoS) attacks. The threat landscape is constantly evolving, making threat intelligence a crucial part of any effective vulnerability risk assessment.
Risk: Assessing the Potential Impact
Risk is the potential for loss or damage when a threat successfully exploits a vulnerability. It’s calculated with a simple formula: Risk = Likelihood × Impact.
- Likelihood is the probability that a threat will exploit a vulnerability. This depends on factors like attacker skill, vulnerability accessibility, and existing security controls.
- Impact is the magnitude of the harm if an exploit occurs. This includes financial losses, reputational damage, operational disruption, and legal penalties. The average data breach cost of $4.45 million is a clear example of impact.
A vulnerability risk assessment evaluates the risk to all assets, including servers, databases, intellectual property, and brand reputation. The goal isn’t to eliminate all risk—an impossible task—but to manage it effectively through continuous identification, assessment, and mitigation, often guided by frameworks like the NIST Cybersecurity Framework.
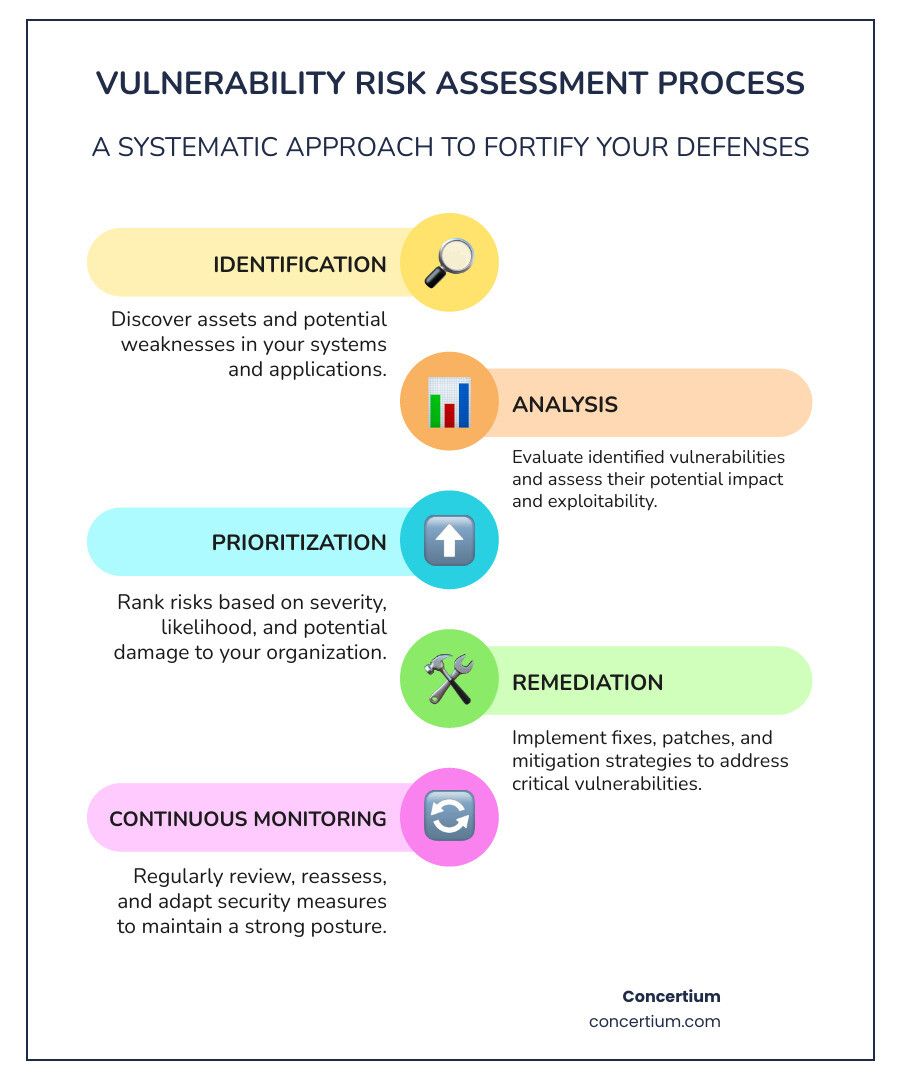
The 5 Key Steps of a Vulnerability Risk Assessment
A vulnerability risk assessment is a systematic, repeatable cycle. Following these five steps ensures a thorough process, while proper documentation provides a roadmap for improvement and evidence of due diligence.
Step 1: Identification and Scoping
First, you must know what you need to protect. This step involves creating an inventory of your digital assets and defining the scope of the assessment.
- Asset Inventory: Create a comprehensive catalog of all technology, including servers, workstations, network devices, cloud services, and mobile devices. Note each asset’s purpose and criticality.
- Define Assessment Boundaries: Clearly define what is in and out of scope for the assessment. You might focus on a single critical system or the entire network.
- Identify Vulnerabilities: Use a combination of automated scanning tools, manual configuration reviews, and team interviews to find potential weaknesses, such as default passwords or misconfigurations.
Step 2: Analysis and Classification
Once vulnerabilities are identified, you need to analyze and classify them to understand the true level of risk.
- Analyze Vulnerabilities: Investigate the root cause of each weakness. Is it a missing patch, a flawed process, or a misconfiguration?
- Severity Scoring: Use standardized systems like the Common Vulnerability Scoring System (CVSS) to rate vulnerabilities based on exploitability and potential impact.
- Assess Exploitability: Consider the real-world context. Is there public exploit code available? Are threat actors actively targeting this weakness? A medium-severity flaw can become critical if it’s being actively exploited.
Step 3: Prioritization and Remediation Planning
With limited resources, you must prioritize what to fix first. This step focuses on creating an actionable plan.
- Prioritize Risks: Rank vulnerabilities based on a combination of technical severity, business impact, and likelihood of exploitation. A critical flaw in a customer-facing application should be a top priority.
- Allocate Resources: Determine who will perform the remediation, how long it will take, and what resources are needed.
- Develop a Remediation Plan: Create a specific roadmap for each high-priority vulnerability, including what patches to apply, what configurations to change, and who is responsible.
Step 4: Remediation and Mitigation
This is where you implement the plan and actively reduce your risk.
- Implement Fixes: Apply patches and make configuration changes. This requires careful coordination to ensure fixes don’t disrupt business operations.
- Harden Systems: Implement quick wins like closing unnecessary ports, strengthening security settings, and removing default accounts to reduce the attack surface.
- User Training: Address the human element by training employees to recognize phishing attempts and follow security best practices.
- Document Actions: Keep a record of all actions taken for compliance audits, troubleshooting, and future assessments.
Step 5: Reporting and Continuous Improvement
The assessment process concludes by translating findings into lasting improvements.
- Report to Stakeholders: Create clear, concise reports that explain technical findings in terms of business risk. Provide actionable recommendations with timelines.
- Analyze Lessons Learned: Review the assessment to identify patterns. Are certain systems consistently vulnerable? Use these insights to prevent future problems.
- Integrate Findings: Use the assessment results to inform your incident response plan, technology purchasing decisions, and security policies.
- Schedule Reassessments: Cybersecurity is a moving target. Schedule regular assessments to identify new vulnerabilities and ensure old ones haven’t returned.
Tools, Techniques, and Best Practices for Vulnerability Risk Assessment
A successful vulnerability risk assessment combines the right tools with proven techniques and best practices. The goal is to balance automation with human expertise, letting technology do the heavy lifting while security professionals provide critical analysis.
Types of Vulnerability Assessment Tools
Different scanners are designed to find specific types of vulnerabilities across your digital environment.
- Network-based scanners patrol your network perimeter, looking for open ports and misconfigured devices.
- Host-based scanners are installed on individual systems (servers, workstations) to find unpatched software, review configurations, and detect malware.
- Application scanners specialize in web applications, using static and dynamic analysis to find code-level vulnerabilities.
- Database scanners focus on data repositories, checking configurations, user privileges, and encryption.
- Cloud environment scanners evaluate cloud configurations, API security, and Identity and Access Management (IAM) settings.
| Scanner Type | Primary Focus | Best Used For |
|---|---|---|
| Network-based | Network perimeter and devices | Port scanning, service detection, network device security |
| Host-based | Individual systems | Unpatched software, system configurations, malware detection |
| Application | Web apps and software | Code vulnerabilities, API security, application-specific flaws |
| Database | Data repositories | Database configurations, access controls, data encryption |
| Cloud | Cloud environments | Cloud configurations, IAM, API security, compliance |
Best Practices for Effective Vulnerability Risk Assessment
Using tools effectively requires a strategic and consistent approach.
- Regular Scanning Schedules: New vulnerabilities appear daily. Implement automated scanning at a frequency that matches your risk tolerance (e.g., daily for critical systems, weekly for others).
- Maintain Current Asset Inventories: You can’t protect what you don’t know about. Keep a continuously updated inventory of all hardware, software, and cloud assets.
- Robust Patch and Configuration Management: A disciplined approach to applying patches and maintaining secure configurations is the most effective way to reduce your attack surface.
- Align with Established Frameworks: Use frameworks like the NIST CSF and methodologies like the OWASP Risk Rating Methodology to provide structure and ensure a comprehensive assessment.
Advanced Techniques to Improve Your Assessment
To further mature your security program, consider these advanced techniques.
- Integrate Threat Intelligence: Use threat intelligence feeds to prioritize vulnerabilities that are actively being exploited by attackers.
- Periodic Penetration Testing: While assessments identify weaknesses, penetration tests attempt to exploit them in a controlled manner to validate their real-world risk.
- Develop and Test Incident Response Plans: An assessment can’t prevent every attack. A tested incident response plan ensures you’re prepared to act when an incident occurs.
- Threat Modeling and Code Reviews: Shift security left by identifying potential vulnerabilities during the design and development phases, before they reach production.
Frequently Asked Questions about Vulnerability Risk Assessment
Business leaders often have similar questions about vulnerability risk assessment. Here are answers to the most common ones.
What is the difference between a vulnerability assessment and a penetration test?
This is the most common question we get. The two are complementary but distinct:
- A vulnerability assessment is like a home inspection. It identifies and creates a comprehensive list of all potential weaknesses, such as open uped doors or windows, without attempting to enter.
- A penetration test is like hiring an ethical burglar. They actively try to exploit the identified weaknesses to prove they are a real threat and show what damage could be done.
Most organizations need regular vulnerability assessments to maintain a broad view of their security posture, supplemented by periodic penetration tests on their most critical systems.
How often should my organization perform a vulnerability risk assessment?
The ideal frequency depends on your risk profile, regulatory requirements, and how quickly your IT environment changes. A good baseline includes:
- Continuous Monitoring: Use automated tools to scan your most critical assets daily or weekly.
- Formal Assessments: Conduct comprehensive reviews at least quarterly to analyze trends and address new risks.
- Trigger-Based Assessments: Perform an assessment immediately following major changes, such as a cloud migration or new application deployment.
Compliance standards in your industry (e.g., HIPAA, PCI DSS) may also dictate a specific schedule.
Can we perform a vulnerability assessment internally, or should we hire an expert?
Both internal and external assessments have value, and the best approach often depends on your resources, expertise, and goals.
- Internal Assessments: Your internal team has deep knowledge of your environment and is best suited for routine, ongoing scanning. They understand your systems and what constitutes normal activity.
- External Assessments: An external expert brings a fresh perspective, specialized tools, and deep knowledge of the latest attack techniques. They can identify blind spots that an internal team might miss due to familiarity.
A hybrid model is often the most effective approach. Use your internal team for continuous monitoring and routine checks, and bring in external experts for periodic deep-dive assessments and to meet compliance requirements. This combines internal context with external validation.
Conclusion: Building a Resilient Security Posture
In a world of rising data breach costs and sophisticated cyberattacks, a vulnerability risk assessment is essential for business survival. It’s a proactive strategy to find and fix weaknesses before they can be exploited.
We’ve covered the systematic five-step process: identifying assets, analyzing vulnerabilities, prioritizing risks, remediating threats, and continuously improving. This isn’t a one-time task but an ongoing cycle that adapts as your business and the threat landscape evolve. By embracing this process, you move from a reactive to a proactive security stance.
The ultimate goal is to build a resilient security posture—one that not only defends against attacks but also strengthens your organization over time. Proactively managing vulnerabilities protects your data, your reputation, and your bottom line.
At Concertium, we’ve helped organizations steer these challenges for nearly three decades. Our Collective Coverage Suite (3CS) combines AI-improved observability with automated threat eradication, but our core mission is to provide custom solutions that fit your unique business needs.
We’re here to help you build stronger, more resilient security programs that work in the real world.
Learn more about vulnerability risk management with Concertium