SOC 2 risk assessment is a structured process that identifies and evaluates potential threats to your organization’s information systems according to the AICPA Trust Services Criteria. If you’re preparing for SOC 2 compliance, here’s what you need to know about risk assessment:
| SOC 2 Risk Assessment Quick Guide |
|---|
| 1. Required annually or when significant changes occur |
| 2. Must cover Trust Services Criteria (at minimum Security) |
| 3. Must include vendor/third-party risks |
| 4. Must consider fraud risks |
| 5. Must document risk responses and control implementation |
Not all risk assessments are created equal. In the cult movie Wall Street, Gordon Gekko unapologetically proclaims, “I don’t throw darts at a board. I bet on sure things.” Similarly, effective SOC 2 risk assessment isn’t about guesswork—it’s about systematically identifying, evaluating, and addressing risks to your information assets.
For many organizations, SOC 2 risk assessment feels overwhelming. But at its core, it’s simply a formalized way to answer: “What could go wrong with our systems or data, how likely is it, how bad would it be, and what are we doing about it?”
The process involves five key steps:
- Define your business objectives
- Identify critical systems and assets
- Perform thorough risk analysis
- Document your risk responses
- Maintain consistency with regular reviews
A well-executed risk assessment not only satisfies auditors but strengthens your security posture and builds customer trust—making it worth the investment beyond mere compliance.
Simple soc 2 risk assessment glossary:
What You’ll Learn
In this comprehensive guide, we’ll walk you through everything you need to know about conducting an effective SOC 2 risk assessment, including:
- How to properly scope your assessment to meet auditor expectations
- Techniques for identifying and evaluating vendor risks (a critical must-do for compliance)
- Methods for incorporating fraud risk considerations into your assessment
- Best practices for establishing the right assessment cadence and triggers for reassessment
- Practical steps to document your process and prepare for auditor scrutiny
By the end of this article, you’ll have a clear roadmap for conducting a SOC 2 risk assessment that not only satisfies compliance requirements but also strengthens your overall security posture.
What Is a SOC 2 Risk Assessment and Why It Matters
Think of a SOC 2 risk assessment as the foundation of your security house. Without a solid foundation, even the fanciest security tools and policies might crumble when faced with real threats.
At its core, a SOC 2 risk assessment is a structured process where you systematically identify, analyze, and evaluate potential risks to your information systems based on the AICPA’s Trust Services Criteria. It’s not just paperwork to satisfy auditors—it’s your roadmap to meaningful security.
The heart of this assessment lives in Common Criteria 3 (CC3.0), which aligns with COSO Principles 6-9. These criteria aren’t arbitrary—they’re designed to ensure you’re thinking about risk in a comprehensive way by:
- Setting clear objectives so you know what you’re protecting and why
- Identifying and analyzing risks that could derail those objectives
- Considering fraud scenarios (because not all threats come from outside)
- Evaluating significant changes that might impact your controls
As one leading auditor from Linford & Company put it: “The risk assessment is the heart and soul of the SOC 2 report.” That’s not hyperbole—it’s reality.
Why should you care? Because a SOC 2 risk assessment isn’t optional—it’s required at least annually for compliance. But the real value goes far beyond checking a compliance box. It demonstrates due diligence to your customers and provides the framework for every security decision you make.
I remember working with a Tampa-based SaaS provider who initially viewed this process as a bureaucratic hurdle. After implementing a proper assessment with our guidance, they finded critical vulnerabilities in their vendor management that could have led to a major data breach. That single finding paid for their entire compliance investment. As they told me afterward, “We thought we were doing this for our customers, but we ended up protecting ourselves.”
Your SOC 2 risk assessment must include several key elements:
Vendor and third-party risks deserve special attention. Your security is only as strong as your weakest vendor, and SOC 2 explicitly requires you to evaluate these relationships. Fraud considerations might feel uncomfortable to discuss, but you must evaluate potential conflicts of interest and insider threats. If you’re pursuing the Availability criterion, environmental threats like power outages or natural disasters need evaluation too. And everything must align with your business objectives and service commitments.
The stakes extend far beyond compliance. Your reputation, customer trust, and business continuity all hang in the balance. As more organizations make SOC 2 compliance a vendor requirement (a trend that’s only accelerating), a robust Compliance and Risk Assessment process becomes not just nice-to-have, but essential for business growth.
Remember: in security, hope isn’t a strategy—but a thorough risk assessment is.
The 5-Step SOC 2 Risk Assessment Process
Let’s face it—tackling a SOC 2 risk assessment can feel like trying to eat an elephant. But remember the old saying: you do it one bite at a time. By breaking it down into five manageable steps, you’ll find the process not only doable but genuinely valuable for your organization.
Before rolling up your sleeves, you’ll need to choose a risk framework as your guide. Think of this as picking the right map before starting a journey:
- ISO 31000 is like the world atlas of risk frameworks—internationally recognized and comprehensive
- NIST 800-30 offers more detailed directions specifically for information security terrain
- COSO ERM works well if you’re already using COBIT 5 for your broader business journey
At Concertium, we’ve found that a hybrid approach works best for most organizations—combining elements from ISO 31000 and NIST 800-30, custom to fit your company’s unique size and complexity. This blended approach gives you both qualitative insights (the “gut feel”) and quantitative measurements (the hard numbers).
Step 1 – Define Objectives & Scope
Every great journey begins with knowing your destination. For your SOC 2 risk assessment, start by clearly mapping out:
Your service commitments—these are the promises you’ve made to customers about security, availability, and other criteria. Think of these as your North Star. What have you told customers about how you protect their data? What’s in your contracts and SLAs?
Next, document your system requirements—the technical and operational guardrails needed to fulfill those promises. Be specific about which Trust Services Criteria you’re including. While Security (the Common Criteria) is your baseline requirement, you might also include Availability, Processing Integrity, Confidentiality, or Privacy depending on your business needs.
Finally, draw clear boundaries around what’s in scope. One of our Florida healthcare tech clients initially tried to boil the ocean by including all five Trust Services Criteria in their first assessment. We helped them narrow their focus to just Security and Confidentiality for their first audit. This allowed them to build a solid foundation before expanding—much like learning to walk before running a marathon.
Remember what auditors always say: your risks must cascade directly from your objectives. Without this connection, you’re just shooting in the dark.
Step 2 – Identify Information Assets & Threats
Now that you know what you’re protecting and why, it’s time to take inventory of your valuable assets and identify what might threaten them.
Start by creating your asset inventory—a comprehensive registry of all the systems, applications, databases, and data repositories that fall within your scope. This is like taking inventory of all the valuable items in your home before buying insurance.
Next, classify your data based on sensitivity and business impact. Not all data is created equal—your customer payment information needs more protection than your company lunch menu.
Map how data flows through your systems and to third parties. This visual roadmap helps identify vulnerability points where threats might exploit gaps.
For each asset, brainstorm relevant threats from both inside and outside your organization. Don’t forget to catalog all vendors with access to your in-scope systems or data—third-party risk is a common blind spot.
If you’re pursuing the Availability criterion, also consider environmental threats relevant to your locations. Are you in hurricane territory? Earthquake zone? What about power outages or HVAC failures for your server rooms?
This inventory forms the cornerstone of an effective Enterprise Security Risk Assessment. After all, you can’t protect what you don’t know you have!
Step 3 – Score & Prioritize Risks
With your assets and threats identified, it’s time to evaluate each risk. This is where many organizations get stuck in the weeds—trying to balance meaningful risk scores without creating a mathematical monster.
We recommend keeping it straightforward: For each risk, assess both the likelihood (how probable is this threat?) and potential impact (how bad would it be?). Typically, a simple 1-5 scale works well for each dimension. Multiply these two factors, and voilà—you have your initial risk score.
Next, evaluate how well your existing controls mitigate each risk, which gives you your “residual risk”—what’s left over after your current protections are considered.
Here’s how qualitative and quantitative approaches compare:
| Aspect | Qualitative Approach | Quantitative Approach |
|---|---|---|
| Scoring Method | Low/Medium/High or 1-5 scales | Monetary values and percentages |
| Ease of Use | Simpler to implement | Requires more data and analysis |
| Communication | Less precise but easier to understand | More precise but requires translation |
| Example | Risk rated “High” based on 4/5 likelihood, 5/5 impact | 15% chance of $200,000 loss = $30,000 expected loss |
| Best For | Initial assessments, smaller organizations | Mature programs, larger organizations |
One of our Tampa clients started with color-coded ratings but later added dollar values to their highest risks. This helped them justify security investments to their board in the language executives understand best—money!
Your risk prioritization should align with your organization’s risk appetite—how much risk you’re comfortable accepting. This isn’t something to decide in isolation; get leadership buy-in on these thresholds before finalizing your assessment.
Step 4 – Map Controls & Spot Gaps
Now comes the detective work—mapping your existing controls to each risk and identifying where you’re exposed.
Start by documenting all your current security and compliance controls. Then play matchmaker, linking each control to the risks it helps mitigate. This process often reveals surprising gaps—high-risk areas with inadequate protection or controls that don’t actually address your most pressing risks.
For each control, assess both its design (is it appropriate for the risk?) and effectiveness (is it actually working as intended?). This two-part evaluation helps identify controls that look good on paper but fall short in practice.
When you find gaps—and you will—document the specific risk that’s not adequately addressed, potential remediation options, recommended actions, who’s responsible, and target completion dates. This creates your roadmap for improvement.
As one seasoned SOC 2 auditor put it, “A control gap is when a control does not exist, is improperly designed, or is not operating effectively to mitigate identified risks.” Finding these gaps yourself before your auditor does saves you both embarrassment and last-minute scrambling.
Step 5 – Review & Update Your SOC 2 Risk Assessment
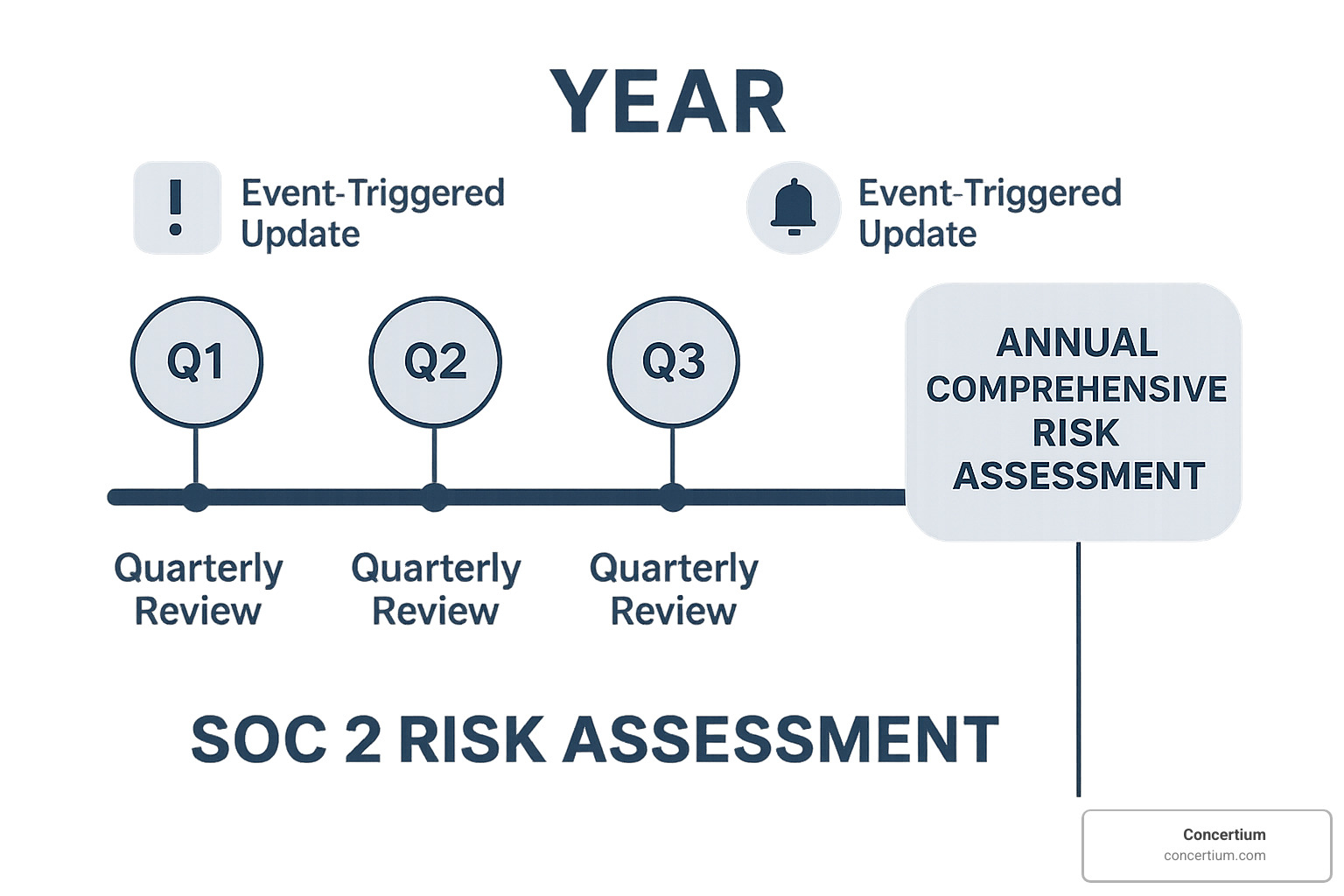
A SOC 2 risk assessment isn’t a “set it and forget it” affair—it’s more like gardening than building a monument. At minimum, you need to review and update annually, but several events should trigger reassessment sooner:
Business changes like mergers, acquisitions, new products, or organizational restructuring can introduce new risks overnight. When your business evolves, your risk assessment should too.
Technology changes including new systems, cloud migrations, or major infrastructure updates often create security blind spots if not properly evaluated.
External factors such as regulatory changes, emerging threats, or industry incidents might suddenly make previously acceptable risks unacceptable.
Internal events like security incidents, audit findings, or leadership changes can significantly alter your risk landscape.
We recommend quarterly light-touch reviews with a comprehensive annual reassessment. This cadence keeps your risk picture current without creating assessment fatigue.
Don’t forget to regularly report findings and remediation progress to your board or executive team. This visibility ensures leadership understands key security concerns and demonstrates your commitment to proactive risk management. Plus, it helps justify continued investment in your security program—everyone wins!
Treating Risks and Closing Control Gaps
So you’ve identified and prioritized your risks during your SOC 2 risk assessment. Now comes the million-dollar question: what are you going to do about them?
This is where many organizations hit a roadblock. They’ve got a beautiful spreadsheet of risks but struggle with the “now what?” part. Let’s break it down into something actionable.
There are four main ways to handle any risk, and they’re pretty straightforward when you think about it:
Mitigate the risk by implementing controls that reduce it to an acceptable level. This is like putting a fence around your swimming pool—you’re not filling it in, just making it safer.
Accept the risk as is, acknowledging that you understand it exists but have decided not to take additional action. This works for smaller risks where the cost of fixing outweighs the potential impact.
Transfer some of the risk burden to someone else, typically through insurance or outsourcing. You’re not eliminating the risk, just shifting who would take the hit if something goes wrong.
Avoid the risk entirely by eliminating the activity causing it. Sometimes the simplest solution is to just stop doing the risky thing!
When deciding which path to take, think about:
- How much risk remains after your existing controls (residual risk)
- What it would cost to implement more controls
- How much risk your organization is comfortable living with
- What regulations or contracts require you to do
For the number-crunchers among us, here’s a practical way to think about control ROI:
Imagine you have a 15% chance of a $200,000 loss, creating an expected annual loss of $30,000. A new control would cost $10,000 to implement plus $5,000 yearly to maintain, but would reduce your risk by 80%. That means your expected loss drops to $6,000, giving you a first-year net benefit of $9,000 ($24,000 in risk reduction minus $15,000 in costs). That’s a smart investment!
When tackling fraud risks—which SOC 2 explicitly requires you to address—remember the classic Fraud Triangle: opportunity, pressure, and rationalization. The most effective controls focus on reducing opportunities through checks and balances like segregation of duties. After all, even good people can make bad choices under the right (or wrong) circumstances.
Don’t forget about vendor risks! The AICPA is crystal clear that your SOC 2 risk assessment must include threats from third parties. This isn’t optional. For each important vendor, you should:
- Review their SOC 2 reports or security questionnaires (yes, you should actually read them)
- Get proper contractual protections in place
- Set up monitoring to catch issues early
- Have a backup plan if they drop the ball
One of our clients finded during this process that their critical payment processor had no disaster recovery plan. They quickly added a secondary processor as a backup, potentially saving themselves from a business-ending outage.
When accepting risks, formalize the decision. Small risks might be accepted by department heads, but significant ones should get executive or board approval. Document who accepted what risk and why—your auditor will ask!
At Concertium, our Risk Compliance Advisory Services help clients develop practical risk treatment strategies that not only check the SOC 2 compliance box but actually improve security and add business value. Because let’s be honest—if you’re going to put in the work, it should do more than just satisfy an auditor.
Maintaining Continuous SOC 2 Compliance
So you’ve achieved SOC 2 compliance—congratulations! But as any seasoned compliance professional knows, the real work is just beginning. Maintaining compliance is like tending a garden—it requires regular attention, not just a once-a-year visit from your auditor.
This ongoing commitment is particularly crucial for Type 2 reports, which examine how effectively your controls operate over time (typically 6-12 months). One of our clients described it perfectly: “Getting SOC 2 certified was the sprint; maintaining compliance is the marathon.”
The secret to continuous compliance isn’t magic—it’s methodical processes that keep your SOC 2 risk assessment relevant and your controls humming along. Think of it as building healthy habits for your organization:
First, you’ll need robust evidence collection. Your auditor won’t just take your word that controls are working—you need proof. This means systematically gathering and organizing everything from system logs to meeting minutes that show your controls in action.
Second, accept change management. As one auditor told us with a laugh, “The only constant in IT is change—and most compliance failures happen right after something changes.” Track and assess how changes to your environment might impact your risk profile.
Third, don’t wait for your auditor to find issues. Regular internal testing helps you catch and fix problems before they become audit findings. It’s like flossing before your dental checkup—a little prevention goes a long way!
Fourth, when incidents happen (and they will), document your response process thoroughly. How you handle security events speaks volumes about your program’s maturity.
Finally, look for opportunities to implement continuous monitoring. Manual checks are fine for smaller organizations, but as you grow, automation becomes your best friend.
“Many organizations struggle to understand CC3.4 without proper change monitoring,” a SOC 2 auditor recently told us. This requirement—identifying and assessing changes that could significantly impact your control environment—trips up even seasoned compliance teams.
At Concertium, we’ve found that building a rhythm of regular risk reviews keeps compliance from becoming overwhelming. Our Governance, Risk, and Compliance (GRC) Explained approach helps clients establish these critical processes as business-as-usual rather than panic-inducing scrambles before an audit.
Staying current with evolving Cybersecurity Compliance Standards is also essential for keeping your risk assessment aligned with industry expectations and regulatory requirements.
Automation Options for SOC 2 Risk Assessment
Let’s be honest—spreadsheets can work for tracking your SOC 2 risk assessment, but they’re about as exciting as watching paint dry. As your environment grows more complex, automation tools become worth their weight in gold.
Think of automation as hiring a dedicated assistant who never sleeps, never forgets, and never gets bored with compliance tasks. These tools can transform your approach by:
Automatically gathering evidence like system logs and configuration data (goodbye manual screenshots!)
Continuously monitoring controls to ensure they remain effective (no more “Oops, when did that stop working?”)
Flagging changes that might impact your risk profile (like that server someone spun up without telling anyone)
Routing approvals and notifications to the right people (no more chasing signatures)
Maintaining an audit trail that would make even the pickiest auditor smile
When evaluating automation tools, look for ones that play nicely with your existing systems, offer dashboards that don’t require a PhD to understand, alert you when something breaks, store evidence securely, and help track remediation efforts.
The efficiency gains can be remarkable. A healthcare client of ours in Orlando reduced their evidence collection time by 75% after implementing an automated solution. Their security team now spends more time on strategic improvements rather than hunting down screenshots—a win for security and sanity alike.
Our Compliance and Risk Management team can help you find the right balance of automation based on your organization’s size and complexity. The goal isn’t automation for its own sake—it’s making compliance sustainable.
Triggers for Re-Assessment & Documentation Updates
While your SOC 2 risk assessment requires annual renewal at minimum, waiting a full year to update it is like checking your smoke detectors only on New Year’s Day—not the best approach for ongoing safety.
Instead, certain events should trigger an immediate review:
New vendors or vendor changes deserve special attention. That new cloud provider might be amazing, but have you assessed how they impact your risk profile? Any third party with access to your in-scope systems requires careful evaluation.
Regulatory changes wait for no one. When laws or standards affecting your industry update, your risk assessment should too.
Product launches or major features often change how you process data. That cool new functionality might introduce risks you haven’t considered.
Infrastructure changes like cloud migrations or architectural shifts can fundamentally alter your risk landscape overnight.
Security incidents provide painful but valuable insights into vulnerabilities. Don’t waste these learning opportunities—update your assessment.
Organizational changes such as mergers, acquisitions, or restructuring can dramatically impact your control environment.
For each reassessment, document everything carefully: when it happened, why, who was involved, what risks changed, and how you’re responding. This documentation isn’t just for your auditor—it’s your organization’s memory, helping you make better decisions over time.
As one SOC 2 auditor frequently reminds clients, “The business must identify and assess changes that could significantly impact the system of internal control.” This isn’t just auditor-speak—it’s practical advice for maintaining an effective security program.
By treating your SOC 2 risk assessment as a living document rather than an annual checkbox, you’ll not only satisfy auditors but also build a more resilient organization. And isn’t that the real goal behind compliance anyway?
Conclusion
SOC 2 risk assessment isn’t just another compliance checkbox—it’s the cornerstone of a security program that genuinely protects your business and earns customer confidence. The five-step process we’ve outlined provides a practical roadmap that not only pleases auditors but delivers real value to your organization.
As you start on this journey, remember these essential principles:
Your assessment should begin with crystal-clear objectives that directly connect to what you’ve promised your customers. This foundation ensures everything that follows has purpose and direction. Be thorough when cataloging your assets, identifying threats, and mapping controls—shortcuts here will come back to haunt you later.
Consistency is key. Whether you choose a simple 1-5 scale or a sophisticated quantitative approach, stick with a methodology that makes sense for your team and produces actionable results. And while it might seem tedious, document everything. Your future self (and your auditor) will thank you when you can demonstrate exactly how you arrived at each decision.
Risk isn’t static. Your assessment needs regular refreshing when significant changes occur—whether that’s adding a new vendor, launching a product feature, or restructuring your team. This isn’t just good compliance practice; it’s good business sense.
Where it makes sense for your organization’s size and maturity, leverage automation tools to lighten the load. The right technology can transform risk assessment from a dreaded annual project into a more manageable, continuous process.
At Concertium, we’ve spent nearly three decades helping organizations steer the sometimes choppy waters of cybersecurity compliance. We understand there’s no one-size-fits-all approach—your business is unique, and your risk assessment should reflect that reality. Our team develops customized approaches that align with your specific environment, industry challenges, and business objectives.
Whether you’re taking your first steps toward SOC 2 certification or looking to lift an existing program, our consulting and compliance services can guide you with minimal disruption to your daily operations.
Think of SOC 2 risk assessment as a journey rather than a destination. Each cycle builds on the last, creating a virtuous loop of security improvement. When you accept risk assessment as a strategic asset rather than a necessary evil, you’ll not only achieve that coveted SOC 2 certification—you’ll build a more resilient organization that customers and partners genuinely trust.
And in today’s digital landscape, trust might be your most valuable asset of all.