AI Overview: Why PCI DSS Risk Assessment Examples Matter for Your Business
A PCI DSS risk assessment is a systematic process to identify, analyze, and mitigate threats to cardholder data. It’s not just compliance paperwork — it’s a proactive security tool that helps prevent breaches, protect customer trust, and avoid regulatory fines. PCI DSS Requirement 12.2 makes annual risk assessments mandatory, plus additional assessments after major environment changes.
Why PCI DSS Risk Assessment Examples Matter for Your Business
A pci dss risk assessment example helps organizations understand how to systematically identify, analyze, and mitigate security risks in their cardholder data environment. Here’s what a typical PCI DSS risk assessment includes:
Key Components of a PCI DSS Risk Assessment:
- Scope Definition: Map your Cardholder Data Environment (CDE) and all connected systems
- Asset Inventory: Document all hardware, software, people, and processes handling card data
- Threat Identification: Catalog potential risks like hackers, malware, insider threats, and physical breaches
- Vulnerability Analysis: Identify weaknesses in systems, processes, and controls
- Risk Rating: Assess likelihood and impact using High/Medium/Low scales
- Treatment Plan: Define how to mitigate, transfer, avoid, or accept each identified risk
- Documentation: Create formal reports with findings, recommendations, and remediation timelines
If you handle credit card data, PCI DSS Requirement 12.2 mandates annual formal risk assessments. But here’s the thing – most business owners find this requirement overwhelming. The good news? It doesn’t have to be.
Risk analysis is a foundational tool to help organizations identify and prioritize potential threats and vulnerabilities within their environment. With PCI DSS v4.0 introducing Targeted Risk Analysis (TRA), organizations now have more flexibility in how they approach risk management while maintaining strong security.
Whether you’re a small retailer processing a few hundred transactions monthly or a mid-sized enterprise handling thousands, understanding the risk assessment process protects your business from data breaches, hefty fines, and damaged customer trust.
Pci dss risk assessment example word guide:
What is a PCI DSS Risk Assessment and Why is it Important?
Picture this: you’re running a successful business that processes credit card payments, and suddenly you find that customer payment data has been compromised. The headlines write themselves, and they’re not pretty. This nightmare scenario is exactly why PCI DSS risk assessment examples exist – to help you spot vulnerabilities before cybercriminals do.
The Payment Card Industry Data Security Standard (PCI DSS) serves as your security roadmap for protecting credit card information. Think of it as the gold standard for keeping sensitive payment data safe from digital thieves. Whether you’re a small coffee shop or a growing e-commerce business, if you handle credit cards, PCI DSS applies to you.
A PCI DSS risk assessment is your systematic detective work – a formal process where we identify, analyze, and evaluate potential threats to your Cardholder Data Environment (CDE). It’s not just paperwork to satisfy auditors; it’s your early warning system that spots trouble before it becomes a crisis.
Why does this matter so much? Beyond the obvious fact that nobody wants their business featured in a data breach news story, the consequences run deep. A single breach can trigger devastating financial losses, destroy years of customer trust, and result in regulatory fines that can cripple smaller businesses. The legal battles that follow can drag on for years.
PCI DSS Requirement 12.2 makes this crystal clear: organizations handling cardholder data must perform risk assessments annually. This isn’t optional – it’s mandatory. Additionally, whenever you make significant changes to your card data environment, another assessment is required.
Your Cardholder Data Environment (CDE) encompasses everything that touches payment card information – the people who handle it, the processes that move it, and the technology that stores or transmits it. Understanding your CDE boundaries is like drawing a security perimeter around your most valuable assets.
Key Benefits of Regular PCI DSS Risk Assessments
Regular risk assessments transform compliance from a burden into a business advantage. They’re like having a security consultant constantly watching your back, identifying problems before they become expensive disasters.
Prioritizing security investments effectively becomes much easier when you know where the real dangers lurk. Instead of spreading your security budget thin across every possible threat, risk assessments help you focus resources on the vulnerabilities that pose the greatest danger to your business.
Reducing the scope of your CDE often happens naturally during assessments. Many organizations find they’re storing cardholder data unnecessarily or in unexpected places. By eliminating this data or properly isolating it through network segmentation, you shrink your attack surface and simplify ongoing compliance efforts.
Protecting your organizational reputation requires proactive thinking. Customer trust, built over years, can evaporate overnight after a data breach. Risk assessments help prevent these reputation-destroying incidents by identifying and addressing vulnerabilities before attackers exploit them.
Enabling ongoing compliance means moving beyond the annual audit mentality. While yearly validations provide snapshots, regular risk assessments give you continuous visibility into your security posture. This ongoing awareness helps you adapt to new threats and environmental changes throughout the year.
The broader benefits include improved data protection as your primary goal, better decision-making based on concrete risk data rather than guesswork, and improved incident response capabilities. When you’ve already mapped out potential attack scenarios through risk assessment, your team can respond more quickly and effectively if an actual incident occurs.
PCI DSS Requirements for Risk Assessment
The PCI DSS requirements for risk assessment are straightforward but comprehensive. Annual assessment requirements mandate that organizations conduct formal risk assessments at least once per year. This ensures your security measures evolve alongside the constantly changing threat landscape.
Assessments after significant changes are equally important. Whenever you implement new systems, update software, or modify your network topology, these changes can introduce new risks. Fresh assessments ensure that security keeps pace with business evolution.
The requirement for a formal, documented risk assessment process means you can’t just think through risks informally. Everything must be documented – the threats you’ve identified, the vulnerabilities you’ve finded, and the formal risk ratings you’ve assigned. This documentation serves dual purposes: it guides your security improvements and demonstrates compliance to auditors.
For organizations seeking detailed guidance on implementation, the PCI DSS risk assessment guidelines provide comprehensive direction from the PCI Security Standards Council. These guidelines offer practical frameworks and methodologies that make the assessment process more manageable and effective.
Step-by-Step PCI DSS Risk Assessment Example
When we sit down with clients who are feeling overwhelmed by PCI DSS requirements, we always start with the same reassuring message: conducting a pci dss risk assessment example doesn’t have to be rocket science. It’s detailed work, but when you break it down into logical steps, it becomes much more manageable.
Think of it like planning a road trip. You wouldn’t just hop in your car and start driving without knowing your destination, checking your route, or making sure you have enough gas, right? A risk assessment follows the same principle – we’re mapping out potential security hazards before they become expensive problems.
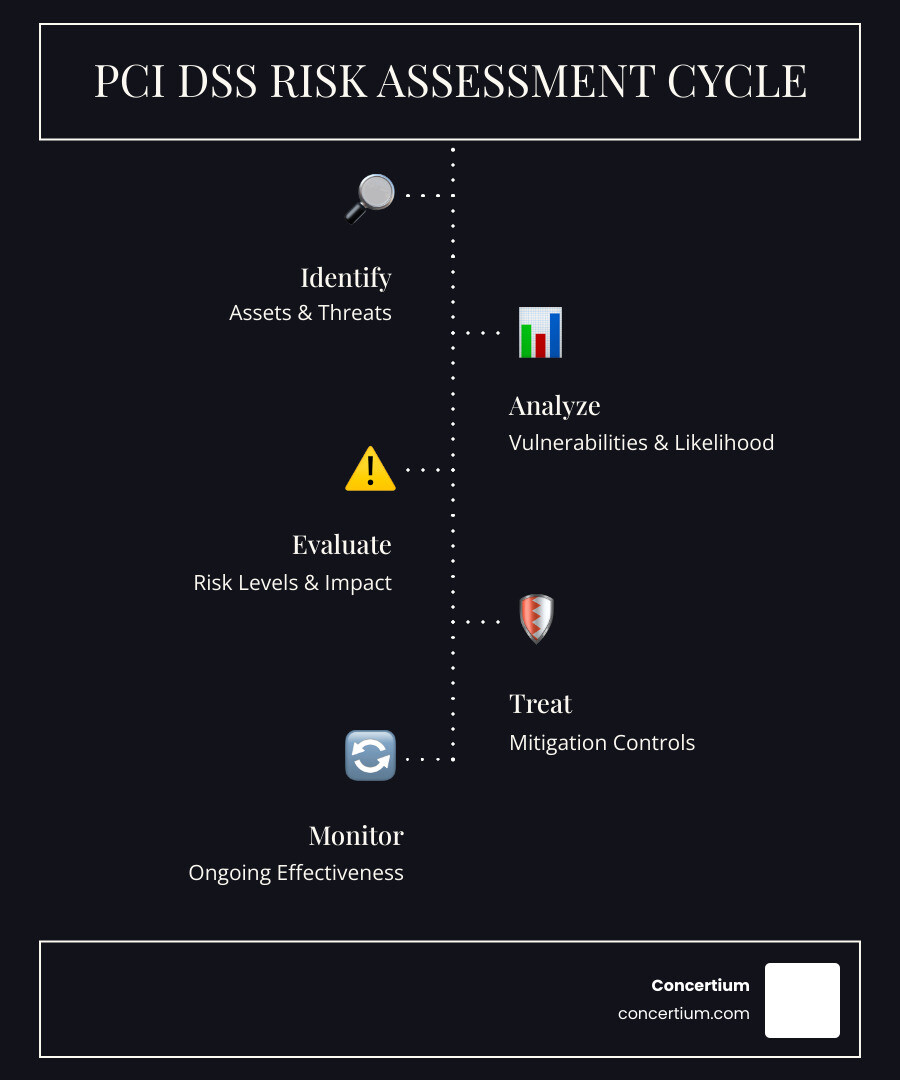
Our tried-and-true process walks through six essential stages: scoping your environment, identifying what could go wrong, assessing vulnerabilities, analyzing the real risk levels, creating a treatment plan, and documenting everything properly. Let’s explore each step with a practical example.
Step 1: Define the Scope and Select a Methodology
The foundation of any solid risk assessment starts with clearly defining your Cardholder Data Environment (CDE). We often tell clients this is like drawing a fence around everything that touches credit card data – you need to know exactly what’s inside that fence before you can protect it.
Scoping the CDE and mapping data flows involves creating a detailed picture of how cardholder data moves through your organization. We trace every path: from the moment a customer swipes their card at your point-of-sale terminal, through your payment processor, into your databases, and anywhere else it might travel. This often reveals surprising data flows that businesses didn’t even realize existed.
Next comes the inventory of systems, people, and processes. We document every piece of hardware, software application, database, and network component within your CDE. But it’s not just about technology – we also catalog which employees handle cardholder data, what business processes involve this sensitive information, and how third-party vendors might interact with your systems.
For methodology selection, we don’t reinvent the wheel. The cybersecurity community has developed excellent frameworks that we can adapt to your specific needs. NIST Special Publication 800-30 provides a systematic approach that most auditors recognize and respect. ISO 27005 offers another solid foundation, particularly for organizations already following ISO standards. Some clients prefer OCTAVE, which takes a more business-focused approach to risk assessment.
The key is picking a methodology that fits your organization’s size and complexity. A small retail shop doesn’t need the same heavyweight approach as a multinational corporation. You can explore a detailed structured approach in this Risk Assessment Methodology.docx to see how these frameworks translate into practice.
Step 2: Identify Threats and Vulnerabilities
Now comes the part that keeps business owners up at night – figuring out what could actually go wrong. But here’s the thing: most threats follow predictable patterns, which means we can prepare for them systematically.
External threats typically grab the headlines, and for good reason. Hackers are constantly probing for weaknesses, looking for easy targets with valuable data. Malware and ransomware can encrypt your entire system, bringing business to a grinding halt. Phishing attacks trick well-meaning employees into handing over their credentials or clicking malicious links. These aren’t theoretical risks – they’re happening to businesses every single day.
But internal threats can be just as dangerous, and they’re often overlooked. Insider threats don’t always involve malicious employees plotting data theft. Sometimes it’s the well-intentioned worker who writes down passwords on sticky notes or the contractor who accidentally misconfigures a firewall. Physical security matters too – we’ve seen cases where sensitive data was compromised because someone left a laptop open uped in a coffee shop.
On the vulnerability side, unpatched software remains one of the biggest culprits. Cybercriminals love exploiting known security flaws in outdated systems. Weak passwords are another gift to attackers – “password123” might be easy to remember, but it’s also easy to crack. System misconfigurations can accidentally expose databases to the internet or leave default credentials unchanged.
Employee training gaps create human vulnerabilities that no technical control can fully address. When staff don’t recognize phishing emails or don’t understand why certain security procedures matter, they inadvertently become the weakest link in your security chain.
We examine all your payment channels – whether you’re processing face-to-face transactions, running an e-commerce website, or handling mail/telephone orders. Each channel presents unique risks that need individual attention. This Sample Risk Assessment Example shows how real organizations document these threats and vulnerabilities in practice.
Step 3: Analyze and Rate Risks
Here’s where we move from “what could happen” to “what’s actually likely to happen and how much would it hurt.” This step transforms a scary list of possibilities into a manageable action plan.
Assessing likelihood and impact requires honest conversations about your specific environment. For likelihood, we ask questions like: “How often do employees click on suspicious links?” and “When did you last update your firewall rules?” For impact, we consider: “What would happen if this system went down for a day?” and “How much would a data breach cost in fines, legal fees, and lost customers?”
We typically use both qualitative and quantitative approaches. Qualitative analysis uses terms like “high,” “medium,” and “low” – it’s faster and works well for initial assessments or smaller organizations. Quantitative analysis assigns dollar figures and percentages, which helps larger organizations make budget decisions and calculate return on security investments.
Most of our clients find success with a semi-quantitative approach that combines the best of both worlds. We use descriptive ratings but back them up with rough financial estimates when possible.
Our risk rating matrix becomes the visual tool that makes everything click. Here’s how a typical matrix might look:
| Likelihood \ Impact | Low (1) | Medium (2) | High (3) |
|---|---|---|---|
| Low (1) | Low (1) | Low (2) | Medium (3) |
| Medium (2) | Low (2) | Medium (4) | High (6) |
| High (3) | Medium (3) | High (6) | Critical (9) |
In this example, we multiply likelihood by impact to get a risk score. Scores of 1-3 might be acceptable risks that we monitor but don’t immediately address. Scores of 4-9 represent unacceptable risks that demand prompt action. The beauty of this approach is that it helps prioritize your security budget – you tackle the “9s” before worrying about the “2s.”
Step 4: Develop a Risk Treatment Plan
Once you know which risks need attention, you have four strategic options for dealing with each one. Think of these as your risk management toolkit – different situations call for different tools.
Mitigation is our go-to approach for most PCI DSS risks. This means implementing controls to reduce either the likelihood or impact of a threat. For example, encrypting cardholder data dramatically reduces the impact if someone does steal your database – the thieves get useless scrambled information instead of valuable credit card numbers. Strong access controls reduce the likelihood that unauthorized people can reach sensitive systems in the first place.
Risk transfer involves shifting the burden to someone else, usually through insurance or outsourcing. Some organizations move to cloud-based payment processors that handle PCI compliance on their behalf. Others invest in cyber insurance to cover potential breach costs. This doesn’t eliminate the risk, but it changes who pays when things go wrong.
Risk avoidance means eliminating the activity that creates the risk entirely. If storing certain cardholder data creates unacceptable risk, stop storing that data. Many businesses find they’re keeping information they don’t actually need for operations. Reducing data retention periods or eliminating unnecessary data collection can dramatically shrink your risk profile.
Risk acceptance is the conscious decision to live with certain risks. This typically applies to low-impact, low-likelihood scenarios where the cost of mitigation exceeds the potential loss. However, this must be a documented management decision, not just neglect disguised as strategy.
Our priority always focuses on high and critical risks first. We implement a combination of administrative controls (like security policies and employee training), technical controls (such as firewalls and encryption), and physical controls (including locked server rooms and badge access systems) to bring risks down to acceptable levels.
Step 5: Document and Report Findings
Here’s where many organizations stumble – they do great work identifying and addressing risks, then fail to document it properly. From a compliance perspective, if it’s not documented, it didn’t happen.
A well-structured risk assessment report serves multiple audiences and purposes. The executive summary gives busy leadership the key points in two pages or less – what are the biggest risks, what’s it going to cost to fix them, and what happens if we don’t act? The detailed scope section proves to auditors that you’ve properly identified your CDE boundaries.
Your asset inventory becomes a valuable reference document beyond just compliance. IT teams use it for system maintenance, business continuity planning, and future technology decisions. The risk analysis section shows your methodology and reasoning, demonstrating that you’ve thought through the threats systematically rather than just guessing.
Risk ratings and treatment plans create accountability and timelines. When you document that the unencrypted database represents a “critical” risk with a 90-day remediation deadline, it’s much harder for that project to get pushed aside for other priorities.
Version control and review dates ensure your risk assessment stays current. We recommend updating the document whenever significant changes occur in your environment – new systems, new processes, new threats, or new vulnerabilities.
This documentation becomes your roadmap for security improvements and serves as a crucial artifact during your PCI DSS audit. More importantly, it helps ensure that all the hard work you put into understanding your risks actually translates into meaningful security improvements.
PCI DSS v4.0: The Move to Targeted Risk Analysis (TRA)
The payment card industry is constantly evolving, and so are the threats we face. That’s why PCI DSS v4.0 introduces a game-changing approach called Targeted Risk Analysis (TRA). Think of it as the standard’s way of saying, “Hey, we get it – your business is unique, and your security approach should be too.”
This shift represents a fundamental move toward more flexible, outcome-based security. Instead of rigid, one-size-fits-all requirements, v4.0 acknowledges what we’ve known all along: effective security needs to be custom to your specific environment and risks.
The beauty of TRA lies in its precision. While the comprehensive annual pci dss risk assessment example for your entire CDE remains important (and required), TRA allows us to zoom in on specific controls and requirements. It’s like having a magnifying glass that helps us examine particular security aspects more closely and make informed decisions about how to implement them in your unique environment.
Two Types of TRA in PCI DSS v4.0
PCI DSS v4.0 introduces two distinct flavors of TRA, each serving a specific purpose in your security strategy. Understanding these differences is crucial for implementing them effectively.
TRA for determining activity frequency gives you the flexibility to adjust how often you perform certain security activities based on your actual risk profile. Instead of blindly following a prescribed “monthly” or “quarterly” schedule, you can use data and analysis to determine what makes sense for your environment. For example, if your access logs show minimal suspicious activity and you have robust monitoring in place, a TRA might justify reviewing them less frequently than a higher-risk environment would require.
TRA for customized controls opens up exciting possibilities for innovation in security. If you’ve developed a creative solution that achieves the same security objective as a standard requirement – perhaps through automation or a novel technical approach – a TRA helps you demonstrate that your customized control provides equivalent or better protection. This is particularly valuable for organizations with unique technology stacks or business models.
The PCI DSS v4.x: Targeted Risk Analysis Guidance document provides detailed direction on implementing both types effectively.
This emphasis on flexibility and outcome-based security means you’re no longer stuck with cookie-cutter solutions. Instead, you can implement security measures that truly make sense for your business while still meeting the standard’s objectives. For deeper insights into how this works in practice, Targeted Risk Assessments in PCI DSS 4.0: A Closer Look offers valuable real-world perspectives.
How TRA Differs from Traditional Risk Assessments
The introduction of TRA marks a significant evolution from the more rigid approach of previous PCI DSS versions. Where v3.2.1 primarily focused on that big annual organizational risk assessment, v4.0 takes a more nuanced approach.
Organization-wide annual assessment vs. control-specific analysis represents perhaps the biggest shift. Your comprehensive annual risk assessment remains the foundation – it’s still required and still valuable. But now, instead of treating risk assessment as a once-a-year event, TRA encourages ongoing, focused analysis throughout the year. Think of it as the difference between getting an annual physical and monitoring your health daily with a fitness tracker.
Ongoing, risk-based decision-making becomes the new norm rather than the exception. This means security decisions are made continuously based on current data and evolving threats, rather than waiting for the next annual cycle. It’s a much more dynamic and responsive approach that aligns with how modern threats actually behave.
The practical impact is profound. Instead of implementing a control because “the standard says so,” you now implement it because your analysis shows it’s the right fit for your specific risk profile. This justification through analysis approach requires more upfront thinking but results in more effective, custom security.
It’s worth noting that TRAs are considered best practice until March 31, 2025, after which they become mandatory. This gives organizations time to develop their TRA capabilities and processes, but waiting until the last minute isn’t advisable. The sooner you start incorporating targeted risk analysis into your security strategy, the better positioned you’ll be to leverage its benefits.
Building Your Risk Assessment Team and Leveraging Results
A successful PCI DSS risk assessment isn’t a solo mission—it’s a team effort that brings together diverse expertise and perspectives. Think of it like assembling a security dream team where each member contributes unique insights that strengthen your overall defense strategy. The real magic happens not just in identifying risks, but in changing those findings into actionable improvements that continuously evolve your security posture.
When we talk about risk management strategy and continuous improvement, we’re really talking about creating a living, breathing security ecosystem that adapts to new threats and business changes. It’s not about checking boxes once a year and forgetting about security until the next assessment cycle.
Who Should Be Involved in the Assessment?
Building an effective risk assessment team is like putting together a puzzle—each piece needs to fit perfectly to see the complete picture. We’ve found that a cross-functional team approach delivers the most comprehensive and practical results.
Your CISO or security leader serves as the quarterback, providing strategic direction and ensuring the assessment aligns with broader organizational goals. They understand the big picture threats and can prioritize resources effectively.
The IT and security teams bring the technical muscle, diving deep into system configurations, network architectures, and application vulnerabilities. These folks know where the digital skeletons are buried and can spot technical risks that others might miss.
Don’t underestimate the value of business managers and process owners. They understand how cardholder data actually flows through your organization day-to-day. They can identify operational risks and help ensure that security recommendations are practical and won’t break critical business processes.
Internal auditors add an extra layer of objectivity and help ensure your assessment methodology is sound and defensible. They’re skilled at asking the tough questions and spotting gaps in logic or coverage.
A Qualified Security Assessor (QSA) brings external expertise and an independent perspective that’s invaluable. They’ve seen how other organizations handle similar challenges and can provide guidance on PCI DSS requirements and industry best practices. This is especially important for reviewing Targeted Risk Analyses in PCI DSS v4.0.
Your legal and compliance teams ensure that risk treatment plans align with regulatory requirements and contractual obligations, while HR representatives help address people-related risks like insider threats and training needs.
Using Assessment Results to Improve Security
The moment you finish documenting your risk assessment findings, the real work begins. This is where we separate organizations that treat assessments as compliance theater from those that use them as powerful security improvement tools.
Turning findings into actionable steps starts with creating clear ownership and timelines for each identified risk. When we find that unpatched software poses a high risk, we don’t just note it—we assign specific team members to develop a patch management schedule, allocate budget for testing, and establish ongoing monitoring procedures.
Policy updates often emerge naturally from assessment findings. Maybe we find that remote access controls are weaker than expected, leading to revised policies that require multi-factor authentication and VPN access logs. These aren’t just documents gathering dust—they’re living guidelines that reflect current threats and business realities.
Control improvements might involve implementing new security technologies or enhancing existing ones. Perhaps the assessment reveals that network segmentation isn’t as robust as assumed, prompting investment in next-generation firewalls or network access control systems.
Employee training becomes targeted and relevant when driven by assessment findings. Instead of generic security awareness sessions, we can focus on specific risks like phishing techniques that target your industry or proper handling of cardholder data in your unique environment.
Incident response planning gets boostd when informed by risk assessment insights. We can develop specific playbooks for the most likely attack scenarios and test them through tabletop exercises that reflect realistic threats to your environment.
The assessment process naturally helps define and often reduce the scope of your CDE. By mapping data flows and identifying where cardholder data lives, we frequently find opportunities for data minimization or network segmentation that can significantly reduce compliance burden.
Adapting to evolving threats requires treating your risk assessment as a living document rather than an annual snapshot. We recommend establishing regular review cycles, integrating threat intelligence feeds, and maintaining continuous monitoring capabilities that can trigger assessment updates when new risks emerge.
Example PCI DSS Risk Assessment Finding
Let’s walk through a real-world pci dss risk assessment example that illustrates how findings translate into action. During a recent assessment, we finded that a client’s development team was using a test database containing actual Primary Account Numbers (PANs) from their production environment. This database was accessible by multiple developers and wasn’t properly isolated from the corporate network.
The finding was clear: “PANs stored unencrypted in a test database within the CDE, violating PCI DSS Requirement 3.4.”
The risk assessment revealed multiple concerning factors: unauthorized access potential from both internal malicious actors and external hackers, unencrypted storage of sensitive data, excessive access permissions, and inadequate network segmentation.
We rated this as a Critical risk due to the medium likelihood (multiple access points and network connectivity) combined with high impact (direct exposure of cardholder data leading to potential breach).
Our recommended treatment plan included immediate and long-term actions: First, we advised immediate removal of all unencrypted PANs from the test database. Then we recommended implementing proper data masking or tokenization for test environments, restricting database access to authorized personnel only, isolating the test environment through network segmentation, updating data handling policies, and conducting targeted training for development teams.
This example shows how a specific vulnerability becomes a rated risk with clear mitigation steps. The key is moving quickly from “what we found” to “what we’re going to do about it”—and then actually doing it. That’s how risk assessments become powerful tools for continuous security improvement rather than just compliance exercises.
Frequently Asked Questions about PCI DSS Risk Assessments
We get a lot of questions from clients about PCI DSS risk assessments – and honestly, that’s perfectly normal! This stuff can feel overwhelming at first, but most concerns boil down to a few key areas that we’re happy to clarify.
How often should a PCI DSS risk assessment be performed?
Here's the straightforward answer: PCI DSS requires a formal risk assessment at least annually. But that's just the baseline. You'll also need to conduct a new assessment whenever there are significant changes to your cardholder data environment - think new systems, major software updates, network changes, or even organizational restructuring that affects how you handle card data.
With PCI DSS v4.0, things get a bit more nuanced. The new Targeted Risk Analyses (TRAs) may require additional assessments based on specific requirements. For instance, if you're using a TRA to determine how often you review access logs, you might need to revisit that analysis more frequently than annually. The frequency really depends on what the TRA itself determines is appropriate for your environment.
Think of it this way: the annual assessment is your comprehensive health check-up, while TRAs are more like specialized consultations when specific situations arise.
What are common threats identified in a PCI DSS risk assessment?
When we conduct risk assessments, we see certain threats pop up again and again. Malware and ransomware top the list - these nasty pieces of code can encrypt your data or steal it outright. Phishing attacks are incredibly common too, where cybercriminals trick your employees into clicking malicious links or sharing credentials.
Unpatched systems create huge vulnerabilities. It's surprising how often we find critical security updates that haven't been applied. Weak access controls are another frequent issue - maybe too many people have access to sensitive data, or passwords aren't strong enough.
Don't overlook insider threats, either. These can be malicious employees or contractors, but more often they're good people who make honest mistakes. Physical security breaches might seem old-fashioned, but they're still a real risk - think stolen laptops or unauthorized access to server rooms.
Denial-of-service attacks can also disrupt your payment processing, even if they don't directly steal data. The key is that every organization's threat landscape looks a bit different based on their industry, size, and setup.
Can I use a template for my PCI DSS risk assessment?
Absolutely! Templates can be a fantastic starting point, giving you a solid framework to build from. They help ensure you don't miss important elements and can save you significant time in getting started.
But here's the important part: templates must be customized to your specific environment. A generic template won't capture the unique risks in your particular setup. Your pci dss risk assessment example needs to reflect your actual systems, processes, and threat landscape - not some hypothetical organization's.
The good news is that the PCI Security Standards Council provides official guidance and sample templates. You can find these valuable resources in the PCI SSC Document Library. These official templates are especially helpful because they align with current PCI DSS requirements and expectations.
Just remember: a template is your starting point, not your finish line. The real value comes from tailoring it to your organization's specific needs, technologies, and risk profile.
Conclusion: Turning Compliance into a Security Advantage
Navigating PCI DSS compliance doesn’t have to feel like climbing Mount Everest in flip-flops. As we’ve walked through this pci dss risk assessment example together, you’ve seen how what might initially seem like a daunting regulatory requirement actually becomes your secret weapon against cyber threats.
Think of it this way: every time you systematically define your Cardholder Data Environment, identify those sneaky vulnerabilities, and build robust treatment plans, you’re not just ticking compliance boxes. You’re actually constructing a digital fortress around your business. Your customers’ data stays safe, your reputation remains intact, and your bottom line stays protected from the devastating costs of a breach.
The beauty of PCI DSS v4.0’s Targeted Risk Analysis approach is that it finally acknowledges what we’ve always known: your business is unique, and your security should be too. Instead of forcing square pegs into round holes, TRA lets you tailor your security efforts to what actually matters in your specific environment. It’s like having a custom-custom suit instead of grabbing something off the rack.
Here’s what really excites us about this evolution: proactive security becomes your competitive advantage. While other businesses scramble to recover from breaches, you’re already three steps ahead, anticipating threats and building resilience into every aspect of your operations. Your risk assessments transform from annual compliance exercises into ongoing strategic tools that guide smart security investments.
At Concertium, we’ve been in the cybersecurity trenches for nearly three decades, and we’ve seen how the right approach to PCI DSS can revolutionize a business’s security posture. Our Collective Coverage Suite (3CS) brings AI-improved observability and automated threat eradication to the table, but more importantly, we bring the human expertise to make sense of it all. We don’t just help you achieve compliance – we help you build business resilience.
The threat landscape keeps evolving, but with a solid risk assessment foundation and the right partner, you’re not just keeping up – you’re staying ahead. Your compliance journey becomes your security advantage, and that’s exactly where every smart business wants to be.
Ready to turn your PCI DSS requirements into a strategic security advantage? We’d love to show you how our custom approach can strengthen your defenses while simplifying your compliance journey.
Contact Concertium for expert PCI DSS compliance support
Author:
This article was written by the cybersecurity and compliance experts at Concertium, dedicated to helping organizations achieve and maintain PCI DSS compliance with confidence.