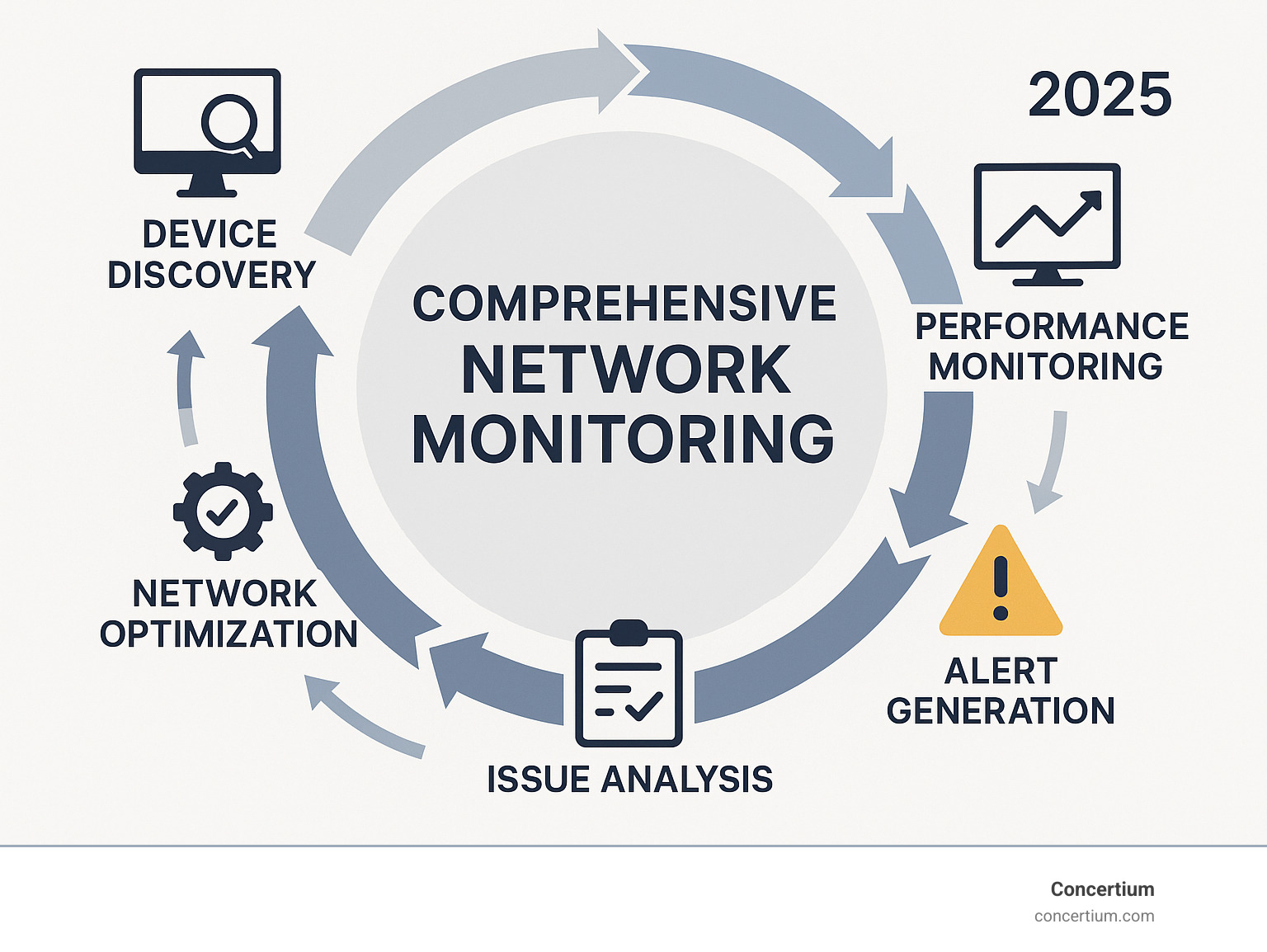
Network monitor software is an IT automation tool that finds, maps, and manages business networks to ensure optimal performance and availability. It provides critical visibility, enabling administrators to proactively identify and resolve issues before they impact users.
Key capabilities of network monitoring software:
- Device Findy – Automatically scans and identifies network devices (routers, switches, firewalls, servers)
- Performance Tracking – Monitors CPU utilization, memory usage, bandwidth consumption, and response times
- Real-Time Alerting – Sends immediate notifications when thresholds are breached or devices go offline
- Traffic Analysis – Examines data flows to identify bottlenecks and optimize network resources
- Visual Mapping – Creates network topology diagrams for better infrastructure understanding
- Historical Reporting – Generates performance trends and capacity planning insights
As IT manager Barry Kelly from Skyscanner notes, modern tools are essential: “If something went down half way across the world, we wouldn’t be woken up – we can rely on PRTG to identify the problem and alert us before it occurs.” This proactive approach prevents the dreaded 5 AM wake-up call when critical systems fail.
With today’s hybrid clouds, remote work, and cyber threats, a lack of monitoring leads to significant risks:
- Unplanned downtime that disrupts operations and damages customer trust
- Performance degradation that slows productivity and frustrates users
- Security breaches from undetected unauthorized access or suspicious activity
- Compliance violations due to inadequate network oversight and documentation
The right network monitoring solution transforms IT teams from reactive firefighters into proactive problem-solvers, ensuring business continuity and optimizing network investments.
Handy network monitor software terms:
Understanding the Fundamentals of Network Monitoring
Network monitor software acts as the nervous system for your IT infrastructure, using continuous monitoring to keep it healthy and performing at its best.
Effective monitoring goes beyond simple uptime checks. It provides a complete picture of your digital environment—how devices communicate, where bottlenecks form, and what patterns signal trouble. This visibility is the foundation for ensuring network availability and optimizing performance. This enables a shift from reactive troubleshooting to proactive management strategies, preventing issues before they impact users and turning IT teams from digital firefighters into network health specialists.
Core Functionalities of Network Monitor Software
Great network monitor software combines several key functions to provide a complete view of your network. These systems continuously monitor access points, routers, firewalls, and switches while tracking critical performance indicators.
- Device findy automatically scans the network to identify and inventory all connected assets, from routers and firewalls to vendor-specific devices like Cisco ACI or Palo Alto firewalls.
- Performance tracking monitors key metrics like CPU, memory, disk space, and interface statistics to spot degradation before it causes problems.
- The alerting system sends immediate notifications via SMS, email, or other channels when custom thresholds are breached, preventing both missed issues and alert fatigue.
- Reporting capabilities turn raw data into actionable insights on performance and availability, which is invaluable for capacity planning and compliance audits.
- Network mapping creates automated visual topology maps, providing context that makes troubleshooting more intuitive.
- Syslog and SNMP trap servers centralize log messages from network devices, allowing for immediate action on critical events.
These functionalities work together to provide the comprehensive visibility essential for effective Network Security Monitoring Service.
How SNMP Works in Network Monitoring
Simple Network Management Protocol (SNMP) is the universal language for monitoring. The SNMP Manager (in your software) requests information from an SNMP agent running on each network device. The agent collects data and stores it in a Management Information Base (MIB), a structured database of device health and configuration.
For proactive monitoring, agents send SNMP traps—immediate alerts for critical events like a port failure or high CPU usage. This SNMP foundation automates device findy, inventory, mapping, and health verification without manual intervention.
Network Device Monitoring vs. Network Traffic Monitoring
Understanding the distinction between device and traffic monitoring is crucial. Both are essential but serve different purposes.
Network device monitoring focuses on the health of infrastructure components: Are routers online? What is the CPU utilization? Is the hardware functioning correctly?
Network traffic monitoring analyzes the data flowing across the network: Who is using the bandwidth? Where are the bottlenecks? It uses protocols like NetFlow, sFlow, or IPFIX to analyze resource consumption.
Device monitoring tells you if your infrastructure is healthy, while traffic monitoring reveals how efficiently it’s being used. The most effective network monitor software combines both, providing a complete view of infrastructure health and traffic efficiency.
Key Features to Evaluate in Network Monitor Software
When selecting network monitor software, prioritize key features that align with your business needs. The right tool should be a reliable partner in maintaining network health.
- Scalability is crucial, ensuring the software grows with your business, whether you have 50 devices or 5,000.
- A user-friendly, customizable dashboard is essential for presenting complex data clearly to different roles, from engineers to executives.
- Broad vendor device support ensures all your equipment, from Cisco to Juniper to specialized IoT devices, is covered.
- Cross-stack data correlation is vital for connecting events across your IT ecosystem to understand the root cause of issues, not just the symptoms.
Essential Visualization and Alerting Tools
Visualization and alerting are the eyes and ears of your network monitor software. Without them, you’re flying blind.
- Network mapping provides visual diagrams of your infrastructure, with features like hop-by-hop analysis to trace data paths and pinpoint problems across on-premises, cloud, or hybrid environments.
- Customizable alerts allow you to move beyond default settings and create specific triggers based on complex conditions, reducing noise and focusing on what matters.
- Multiple delivery methods (SMS, email, app integrations) ensure alerts reach the right people through the right channels.
- A Quality of Experience (QoE) dashboard translates technical metrics into business impact, showing how network performance affects the actual user experience.
These visualization and alerting capabilities become even more powerful when combined with Automated Network Threat Detection services.
Integration with Other IT Management Systems
Your network monitor software is most valuable when integrated with other IT management systems for a unified view. Key integrations include:
- IP Address Manager (IPAM): Automates IP tracking and unifies DHCP and DNS management.
- Network Configuration Manager (NCM): Allows for bulk configuration changes, reducing errors and enforcing compliance.
- Help Desk Systems: Streamline incident response by automatically creating and assigning detailed tickets.
- Security Information and Event Management (SIEM): Improves threat detection by correlating network events with security logs.
| Integration Type | Benefits |
|---|---|
| NMS with IPAM | Automated IP tracking, unified management of IP addresses, improved network planning. |
| NMS with NCM | Automated configuration changes, compliance enforcement, reduced manual errors. |
| NMS with SIEM | Improved threat detection, centralized security event correlation, faster incident response. |
Support for Modern and Diverse Environments
Today’s networks are complex, spanning on-premises, cloud, and virtual environments. Your network monitor software must handle this diversity.
- Wireless monitoring is essential for visibility into access points, controllers, and client connections to quickly diagnose WiFi issues.
- Cloud monitoring extends visibility to services like Azure V-Nets, tracking performance in distributed cloud environments.
- Virtualization support provides detailed monitoring for platforms like VMware and Hyper-V, uncovering issues within virtual infrastructure.
- Hybrid environment support unifies monitoring across on-premises, cloud, and edge locations, providing a single dashboard for your entire infrastructure.
Choosing the Right Monitoring Approach and Deployment Model
Choosing the right network monitor software depends on your specific needs, including network distribution, budget, and team expertise. A small business in Tampa has different requirements than a multinational corporation, so consider your deployment model and monitoring approach carefully.
Agent-Based vs. Agentless Monitoring
This debate centers on how data is collected. Both methods have their place, and many modern solutions offer a hybrid approach.
Agent-based monitoring installs software on each device for deep, granular metrics. This provides incredible detail but requires management and consumes some system resources.
Agentless monitoring uses standard protocols like SNMP and WMI to collect data remotely. This offers faster deployment with less overhead on monitored systems, though with potentially less granular detail than agents provide.
On-Premises vs. Cloud-Based (SaaS) Solutions
Your deployment model affects cost, control, and accessibility.
On-premises solutions are installed on your own servers, offering full control over data and security, typically for a one-time licensing cost. However, your team is responsible for all maintenance, updates, and scaling.
Cloud-based (SaaS) solutions are hosted by the vendor and accessed via a web browser. This subscription model eliminates upfront hardware costs and maintenance burdens, offering easy access from anywhere, which is invaluable for remote or distributed teams.
For businesses exploring managed IT services, cloud-based solutions often integrate seamlessly with broader service offerings. More info about Managed IT Cloud Services Tampa Florida
Open-Source vs. Commercial Software
This choice often reflects a company’s internal resources and budget.
Open-source software is typically free and highly customizable, making it ideal for organizations with strong technical teams willing to handle setup, configuration, and ongoing maintenance. Support generally comes from community forums.
Commercial software offers a polished user experience, dedicated support, and extensive documentation in exchange for licensing fees. The decision comes down to whether you prefer to invest time and internal expertise or budget for a ready-to-use solution with professional support.
Best Practices for Implementation and Network Optimization
Deploying network monitor software is only the beginning. Real value comes from following best practices for implementation and using its insights for continuous network optimization. This transforms IT from a reactive to a proactive function, but it requires a strategic approach.
Implementing and Configuring Your Solution
A successful implementation requires a clear strategy. Start by following these key steps:
- Define monitoring goals to focus on what matters most, whether it’s uptime, security, or application performance.
- Establish performance baselines by collecting data for at least a week to understand what “normal” network behavior looks like.
- Configure device dependencies to prevent alert storms by identifying the root cause of an outage, not just its symptoms.
- Fine-tune alert thresholds beyond the defaults to create meaningful, actionable alerts that reduce noise.
- Schedule regular reviews to ensure your monitoring strategy evolves with your ever-changing network.
How to Optimize Performance and Troubleshoot Issues
Modern tools offer powerful features for optimization and troubleshooting. Use them to:
- Correlate data by connecting disparate metrics on a single timeline to find the root cause of an issue, reducing troubleshooting from hours to minutes.
- Visualize network paths with hop-by-hop analysis to trace data packets and visually spot delays or failures.
- Analyze bandwidth usage to identify which applications and users consume the most resources, enabling smarter policy decisions.
- Analyze historical trends to power intelligent capacity planning, helping you scale proactively instead of reactively.
These advanced capabilities become even more powerful when improved with artificial intelligence. AI Improved Observability takes pattern recognition and anomaly detection to the next level, identifying subtle issues that human analysis might miss.
Bolstering Network Security and Availability
Network monitor software is a key part of your security posture. It improves security and availability by:
- Detecting unauthorized devices the moment they connect to your network.
- Monitoring firewall configurations for unauthorized changes or policy drift.
- Identifying suspicious traffic patterns by analyzing deviations from normal behavior.
- Supporting compliance (e.g., HIPAA, PCI) with the comprehensive logs and audit trails needed for regulatory reviews.
This proactive security approach integrates seamlessly with comprehensive Network Threat Detection and Response strategies, creating multiple layers of protection for your critical business assets.
Frequently Asked Questions about Network Monitor Software
What is the primary purpose of network monitoring?
The primary purpose is to ensure the availability, performance, and security of a business network. By continuously tracking devices and traffic, network monitor software enables IT teams to move from reactive firefighting to proactive problem-solving, often fixing issues before users are impacted.
Can network monitoring software detect security threats?
Yes. By establishing a baseline of normal network activity, the software can detect security threats by identifying anomalies. This includes spotting unauthorized devices, unusual traffic patterns, or unexpected data flows that might indicate a malware infection or breach. It serves as a critical layer in a comprehensive Network Security Management strategy.
How much does network monitoring software typically cost?
Costs vary widely. Open-source tools are free but require significant technical expertise for setup and maintenance. Commercial solutions range from hundreds to tens of thousands of dollars annually, with pricing typically based on the number of devices, desired features, and support level. Models include one-time licenses and subscriptions. The best way to determine cost is to use free trials to evaluate which solution fits your needs and budget.
Conclusion: Proactive Monitoring for a Resilient Network
Imagine a network that runs perfectly while you sleep, free from 3 AM emergency calls. This is the reality of proactive control, achieved with the right network monitor software. As we’ve covered, effective monitoring transforms IT from reactive firefighting to strategic business enablement by providing a complete view of network health.
The choices you make—from agent-based vs. agentless to cloud vs. on-premises—directly impact your ability to protect and optimize your infrastructure. The future is even more promising, with AI and automation paving the way for predictive failure analysis and full-stack observability. Network monitoring is the foundation of business continuity, protecting revenue, productivity, and customer trust.
At Concertium, our Collective Coverage Suite (3CS) leverages nearly 30 years of expertise, combining AI-improved observability with automated threat eradication to build resilient networks. We understand that every network is unique, which is why we focus on custom solutions.
The bottom line? Proactive monitoring isn’t just a best practice; it’s a business necessity for peace of mind, better performance, and the ability to focus on growing your business.
Ready to transform your network monitoring from reactive to proactive? Learn more about our comprehensive approach at Managed IT: Network Monitoring Management and find how we can help you build a truly resilient network infrastructure.