Managed detection and response is a cybersecurity service that combines advanced technology with human expertise to provide 24/7 threat monitoring, detection, investigation, and response capabilities for organizations that lack the resources to build comprehensive in-house security operations.
Key Benefits of MDR Services:
- 24/7 Expert Monitoring – Continuous threat detection by skilled security analysts
- Faster Response Times – Reduce time-to-detect from 277 days to minutes
- Cost-Effective Security – Enterprise-grade protection without hiring full security teams
- Proactive Threat Hunting – Identify hidden threats before they cause damage
- Regulatory Compliance – Meet data protection requirements with detailed reporting
The cybersecurity landscape has fundamentally changed. As one security professional noted after implementing MDR: “Red Canary brought to life a lot of activity in our environment that we were previously blissfully ignorant of — it was like flipping the lights on and watching the cockroaches scramble.”
The numbers tell the story. 88% of ransomware attacks happen outside normal business hours when your team is offline. There’s a shortage of 4.76 million cybersecurity experts globally. Meanwhile, Gartner predicts that 50% of all enterprises will adopt MDR services by 2025, with the market expected to reach $6.29 billion by 2030.
For tech-savvy business owners managing mid-sized enterprises, MDR solves a critical challenge: how do you get enterprise-level security without the enterprise-level budget and staffing requirements? The answer lies in outsourcing your detection and response capabilities to experts who live and breathe cybersecurity every single day.
Simple guide to managed detection response terms:
What is Managed Detection and Response (MDR)? A Foundational Guide
Picture having a team of cybersecurity experts who never sleep, never take vacations, and are constantly watching over your business like digital guardians. That’s essentially what managed detection and response (MDR) brings to your organization.
Managed detection and response is a comprehensive cybersecurity service that goes far beyond simply installing security software and hoping for the best. It’s a complete solution that combines cutting-edge technology with human expertise to provide round-the-clock protection against cyber threats. Think of it as the difference between having a basic home alarm system versus having a full security team monitoring your property 24/7.
What makes MDR special is its proactive approach. Instead of waiting for something bad to happen and then reacting, MDR services actively hunt for threats, investigate suspicious activities, and respond to incidents before they can cause serious damage. This means leveraging advanced tools for Real-Time Threat Detection in Cybersecurity while having skilled analysts interpret what those tools are telling us.
The beauty of MDR lies in this human-technology partnership. Machines are excellent at processing massive amounts of data and spotting patterns, but humans excel at understanding context, making judgment calls, and crafting appropriate responses. Together, they create a defense system that’s both fast and smart.
The Core Purpose of MDR Services
Let’s address the elephant in the room: building your own security operations center (SOC) is expensive, complicated, and often unrealistic for most businesses. We’re talking about millions of dollars in technology, hiring specialized experts who are in extremely short supply, and maintaining operations around the clock.
Managed detection and response services exist to solve this fundamental challenge. Instead of trying to build your own cybersecurity dream team, you get instant access to a fully operational team of experts who have been doing this for years. It’s like having a fire department on speed dial, except they’re preventing fires before they start.
The real magic happens when MDR takes the pressure off your internal IT team. Your IT folks are probably already juggling a dozen different responsibilities – from keeping the email running to managing software updates. Adding “become cybersecurity experts” to that list is unfair and unrealistic. MDR lets them focus on what they do best while the security experts handle what they do best.
This approach dramatically improves your overall security posture. You’re not just getting better protection; you’re getting enterprise-grade security that would normally be reserved for large corporations with massive budgets. Our Cybersecurity Risk Assessment Services can help identify exactly where your current defenses need strengthening.
Key Business Challenges Solved by MDR
The modern threat landscape is frankly intimidating, and businesses face challenges that didn’t exist even five years ago. Sophisticated cyberattacks have evolved from simple viruses to complex, multi-stage operations run by organized criminal groups. These aren’t teenagers in basements anymore – they’re well-funded professionals using advanced techniques specifically designed to slip past traditional security measures.
The talent shortage in cybersecurity is absolutely staggering. There are nearly 5 million unfilled cybersecurity positions globally, and the average salary for a security analyst can easily exceed six figures. Even if you can afford to hire someone, finding qualified candidates is like searching for unicorns. MDR eliminates this problem entirely by giving you access to teams of experts without the recruitment headaches.
Regulatory compliance adds another layer of complexity. Whether you’re dealing with GDPR, HIPAA, PCI DSS, or industry-specific regulations, the requirements for data protection and incident reporting are becoming increasingly strict. The fines for non-compliance can be business-ending. MDR services help ensure you meet these requirements with proper documentation and audit trails.
From a cost perspective, MDR makes enterprise-level security accessible to businesses that could never justify the expense of building their own SOC. Instead of spending millions upfront and hundreds of thousands annually on staff, you get predictable monthly costs and superior protection.
Perhaps most critically, 24/7 coverage is no longer optional. Cybercriminals specifically target nights, weekends, and holidays when they know your team isn’t watching. A staggering 88% of ransomware attacks happen outside normal business hours. MDR ensures someone is always watching, even when you’re sleeping or on vacation.
These challenges aren’t going away – they’re getting worse. But with the right MDR partner, they become manageable. To see how this applies specifically to smaller businesses, check out 5 Ways SMEs Benefit from MDR.
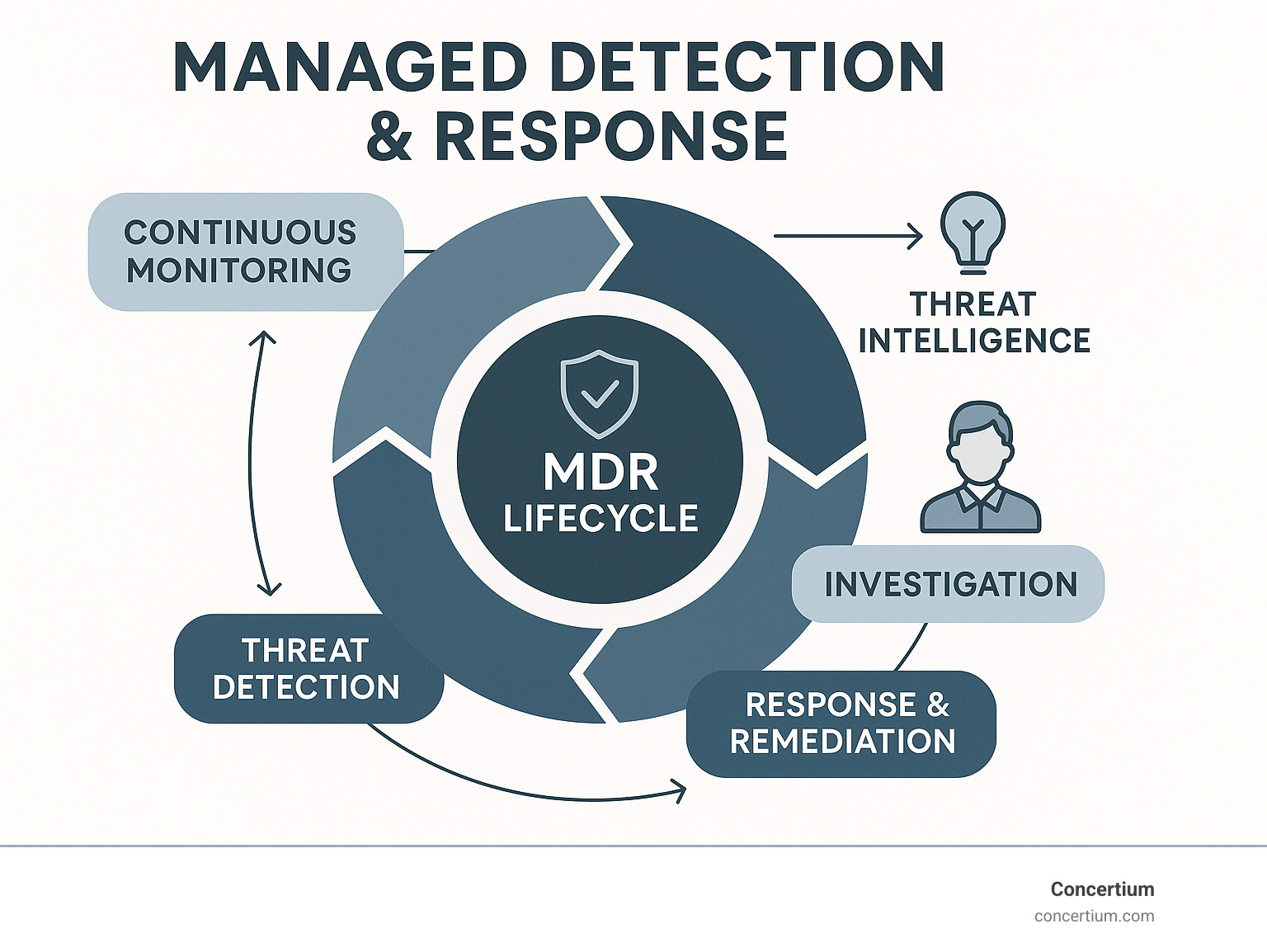
How MDR Works: The Lifecycle of Threat Mitigation
Think of managed detection and response as your digital bodyguard – one that never sleeps, never takes a coffee break, and has eyes everywhere. Understanding how MDR operates reveals why it’s become such a game-changer for businesses that need enterprise-level security without the enterprise-level headaches.
The beauty of MDR lies in its systematic approach to cybersecurity. It’s not just about reacting when something goes wrong; it’s about creating a continuous cycle of protection that gets smarter and stronger over time. This process flows seamlessly from one stage to the next, creating an impenetrable shield around your digital assets.
The entire system runs on cutting-edge threat intelligence – think of it as a constantly updated database of the bad guys’ latest tricks. This real-time information feeds into proactive threat hunting, where our experts actively search for threats that might be lurking undetected in your systems. When something suspicious is found, we provide guided response actions that contain the threat quickly and effectively.
But we don’t stop there. After neutralizing the immediate danger, we dig deep with root cause analysis to understand exactly how the attack happened. This isn’t just about fixing today’s problem; it’s about preventing tomorrow’s headaches. This commitment to continuous improvement means your security posture gets stronger with every incident we handle. Our comprehensive approach is detailed in our Threat Detection and Response Solutions.
The Core Components of a Managed Detection and Response Service
Every effective managed detection and response service operates on five fundamental pillars that work together like a well-orchestrated symphony. Each component plays a crucial role in keeping your business safe from cyber threats.
Prioritization is where we separate the wheat from the chaff. Your security systems might generate thousands of alerts daily, but not all alerts are created equal. We use sophisticated filtering and human expertise to focus on what really matters – the genuine threats that could harm your business. This eliminates the dreaded “alert fatigue” that paralyzes many security teams.
Threat hunting is where our human experts truly shine. While automated systems are excellent at catching known threats, skilled hunters can spot the subtle signs of sophisticated attackers who’ve learned to fly under the radar. They look for behavioral anomalies and unusual patterns that might indicate someone is already inside your network, quietly planning their next move.
Investigation transforms suspicions into facts. When we detect something unusual, our analysts become digital detectives, gathering evidence from across your entire IT environment. They correlate events from your endpoints, network traffic, cloud services, and other security tools to build a complete picture of what’s happening.
Guided response provides you with clear, actionable steps to contain and eliminate threats. Depending on your service agreement, we might execute these actions directly or guide your team through the process. Either way, you get expert-led response that minimizes damage and gets you back to business quickly.
Remediation ensures threats are completely eradicated, not just temporarily contained. We help restore affected systems, implement additional safeguards, and strengthen your defenses against similar future attacks. It’s about getting you back to normal and making sure “normal” is more secure than before.
The Role of AI and Automation in Modern MDR
The cybersecurity world moves at lightning speed, and even the most skilled human analysts need technological superpowers to keep up. This is where artificial intelligence and automation transform managed detection and response from good to extraordinary.
AI excels at processing massive amounts of data at superhuman speeds. Machine learning algorithms can analyze network traffic, endpoint behaviors, and user activities across your entire environment simultaneously. They spot patterns and anomalies that would take human analysts days or weeks to identify manually. This dramatically faster detection capability means threats are caught in minutes rather than months.
One of AI’s greatest gifts to cybersecurity is its ability to learn and adapt. Modern AI systems continuously refine their understanding of what’s normal versus suspicious in your specific environment. This leads to reduced false positives – fewer midnight phone calls about “threats” that turn out to be legitimate business activities.
Behavioral analysis powered by AI is particularly powerful against advanced threats. Instead of just looking for known bad signatures, AI systems learn how your users, applications, and systems normally behave. When something deviates from these established patterns, it triggers an investigation, even if the activity isn’t obviously malicious.
The magic happens when AI and human expertise work together. While AI handles the heavy lifting of data processing and initial threat identification, human analysts provide the context, intuition, and strategic thinking that machines simply can’t replicate. They make the complex decisions about response priorities and customize remediation strategies for your specific business needs.
Our AI-Improved Advanced Observability capabilities exemplify this perfect marriage of technology and human insight. Combined with our Automated Threat Detection, this approach ensures you get both the speed of machines and the wisdom of experienced security professionals protecting your business around the clock.
MDR vs. Other Security Approaches: Clarifying Key Differences
The cybersecurity world is packed with acronyms that can make your head spin. While many services and technologies promise to keep your business safe, managed detection and response stands out because it combines cutting-edge technology with real human experts who actively hunt down threats and respond to them. It’s like having a security guard who doesn’t just watch the cameras but actually chases down the bad guys.
Let’s clear up the confusion by comparing MDR to some other common cybersecurity approaches you’ve probably heard about:
| Feature | MDR (Managed Detection & Response) | EDR (Endpoint Detection & Response) | SIEM (Security Information & Event Management) | MSSP (Managed Security Service Provider) |
|---|---|---|---|---|
| Primary Function | Proactive threat hunting, 24/7 monitoring, investigation, and active response/remediation of confirmed threats | Tool for collecting and analyzing data from endpoints to detect and investigate suspicious activity | Aggregates and analyzes log data from various sources for centralized security monitoring | Broad range of outsourced security services like firewall management and basic monitoring |
| Human Expertise | Core component: Dedicated security analysts, threat hunters, and incident responders actively investigate and respond | Requires skilled in-house team to manage, analyze, and respond to alerts generated by the tool | Requires skilled analysts to configure and interpret alerts, often leading to alert fatigue | Typically focuses on managing technology and generating alerts; response is usually left to you |
| Response Actions | Active response: Can perform containment, eradication, and remediation on your behalf | Provides data for your team to respond; some automated response capabilities like isolation | Primarily for alerting; no direct response capabilities | Generally provides alerts and recommendations; direct response is usually out of scope |
| Scope | Endpoints, network, cloud, identity, email – comprehensive threat mitigation | Focuses specifically on endpoint activity | Broad log collection, but requires significant tuning to be effective | Varies widely, but typically broader infrastructure management with less deep threat hunting |
| Proactivity | Highly proactive: Continuous threat hunting to find hidden threats | Reactive detection based on endpoint data; hunting depends on your team using the tool | Reactive to alerts; proactivity depends on analyst capabilities | Often reactive, focused on compliance and basic monitoring |
| Value Proposition | Comprehensive, human-led threat detection and response as a service, addressing skills gaps with 24/7 coverage | Provides endpoint visibility but requires significant internal resources to use effectively | Centralized logging and alerting, but can be overwhelming without a dedicated team | Outsourced management of security infrastructure, but often lacks deep, active threat response |
The key difference is that MDR is a service with humans in the driver’s seat, while many other approaches are tools that require you to have the expertise to use them effectively. For a deeper dive into these distinctions, check out our detailed comparison in MDR vs EDR vs SIEM.
MDR vs. In-House Security Operations Center (SOC)
Building your own Security Operations Center sounds impressive, but the reality can be quite different from the dream. An in-house SOC requires a massive upfront investment in security tools, infrastructure, and the ongoing costs of licensing and maintenance. More challenging than the technology costs is assembling a team of highly skilled security analysts, threat hunters, and incident responders who can work around the clock.
Here’s the tough truth: the cybersecurity talent shortage is real. Finding qualified professionals is difficult enough, but keeping them is even harder. You’re competing with tech giants and specialized security firms for the same pool of experts. Even if you manage to hire a great team, providing true 24/7 coverage means you need multiple shifts, vacation coverage, and backup plans for when people inevitably move on to new opportunities.
Managed detection and response offers a completely different approach. Instead of building your own SOC, you get access to our team of experts who live and breathe cybersecurity every day. We provide the people, processes, and technology of a world-class SOC as a service. You gain instant access to seasoned professionals without the headaches of hiring, training, or managing them.
The 24/7 coverage is built right in, ensuring your organization stays protected even during nights, weekends, and holidays when many attacks actually occur. This model scales beautifully with your business – as you grow, your security grows with you without having to constantly expand your internal team. You get superior depth of analysis and rapid incident response without the complexity and costs of building your own operation from scratch.
MDR vs. Endpoint Detection and Response (EDR)
This comparison trips up a lot of people because EDR technology is often a key component within a managed detection and response service. The crucial distinction is simple: EDR is a powerful tool, while MDR is a comprehensive service that uses tools like EDR to deliver complete protection.
Think of EDR as a sophisticated security camera system for your computers, servers, and devices. It monitors and records activities in real-time, detects suspicious behaviors, and can even automatically isolate compromised devices. EDR gives you incredible visibility into what’s happening across your endpoints – it’s like having a high-tech surveillance system watching every digital move.
But here’s where it gets tricky: raw EDR data can be overwhelming. Without skilled security analysts to manage, configure, analyze, and respond to the alerts, an EDR tool is just an expensive data collector. It can tell you what happened, but not necessarily why it happened or what you should do about it. Many organizations install EDR thinking it will solve their security problems, only to find themselves drowning in alerts they don’t know how to prioritize or investigate.
Managed detection and response takes that powerful EDR tool and adds the crucial human element. Our expert analysts provide the threat analysis needed to make sense of the data, investigate suspicious alerts, eliminate false positives, and take decisive action on the threats that actually matter. We transform EDR from a surveillance system into a fully operational security team, complete with active threat hunting and managed response capabilities.
It’s the difference between owning a Formula 1 race car and having a professional pit crew and driver to actually win the race. The car is impressive, but without the expertise to operate it effectively, you’re not going anywhere fast.
Key Benefits and Strategic Value of MDR
When you’re considering managed detection and response, it’s important to understand that this isn’t just another cybersecurity checkbox to tick off. It’s a strategic investment that transforms how your organization approaches digital security, delivering value that extends far beyond basic threat protection.
Think of MDR as your organization’s cybersecurity insurance policy – but one that actively works to prevent claims rather than just paying out after disasters strike. The reduced risk alone makes MDR invaluable. With 24/7/365 monitoring and proactive threat hunting, you’re catching threats in their infancy rather than finding them months later when the damage is already done. Organizations without proper threat detection capabilities often don’t realize they’ve been compromised for an average of 277 days – that’s nearly nine months of potential data theft, system manipulation, and business disruption.
The cost-effectiveness of MDR becomes clear when you consider the alternative. Building an in-house security operations center requires massive upfront investments in technology, infrastructure, and talent. You’d need to hire multiple security analysts, threat hunters, and incident responders to provide round-the-clock coverage, plus invest in expensive security tools and ongoing training. MDR delivers enterprise-grade protection at a predictable monthly cost that’s typically a fraction of what you’d spend building similar capabilities internally.
Improved compliance is another significant advantage that many organizations find after implementing MDR. Whether you’re dealing with HIPAA, PCI DSS, GDPR, or industry-specific regulations, MDR services provide the continuous monitoring, detailed incident reports, and audit trails that compliance frameworks demand. It’s like having a compliance officer who never sleeps, constantly documenting your security posture and response activities.
Perhaps the most critical benefit is the dramatic improvement in faster response times. MDR can reduce your Mean Time to Detect (MTTD) from months to minutes, and your Mean Time to Respond (MTTR) by 50% or more. When you consider that 88% of ransomware attacks occur outside normal business hours, this 24/7 vigilance isn’t just convenient – it’s essential for business survival.
MDR also provides access to expert talent without the recruitment headaches. Instead of competing for scarce cybersecurity professionals in a market with a 4.76 million person skills gap, you gain instant access to a team of seasoned analysts, threat hunters, and incident responders. It’s like having your own cybersecurity dream team on speed dial.
For more insights on how this translates into real-world protection, explore our comprehensive guide to Managed Threat Detection and Response.
Enhancing Your Security and Compliance Posture
One aspect of managed detection and response that often surprises business leaders is how significantly it lifts their overall security and compliance posture. It’s not just about stopping the bad guys – though it certainly does that – it’s about building a demonstrable culture of security that regulators, auditors, and stakeholders can see and appreciate.
From a security standpoint, MDR creates a foundation of proactive defense that goes far beyond what most organizations can achieve on their own. The continuous threat hunting means vulnerabilities are identified and patched before they become entry points. Active threats are neutralized in their early stages, before they can establish persistence or move laterally through your network. This constant vigilance builds layers of resilience that make your organization a much harder target.
Regulatory compliance becomes significantly more manageable with MDR in place. Most compliance frameworks require specific security capabilities: 24/7 monitoring, documented incident response procedures, detailed logging of security events, and evidence of proactive threat management. MDR services deliver all of these requirements as standard operating procedure.
The data protection aspect is particularly valuable in our current regulatory environment. By actively defending against breaches and rapidly containing incidents when they do occur, MDR directly supports your obligations under various data privacy laws. When auditors ask about your data protection measures, you can point to concrete evidence of continuous monitoring, threat detection, and rapid response capabilities.
The audit trails and reporting that come with MDR services are goldmines during compliance assessments. Every detected threat, investigation, and response action is carefully documented. These detailed records demonstrate due diligence and provide the evidence auditors need to verify your security posture. It’s the difference between saying “we take security seriously” and proving it with comprehensive documentation.
Our experts often bring deep knowledge of various compliance standards, providing valuable guidance to help align your security practices with specific regulatory requirements. This expertise becomes part of your Cybersecurity Risk Management Frameworks, making compliance less of a burden and more of a competitive advantage.
Common Use Cases for a Managed Detection and Response Solution
Understanding where managed detection and response delivers the most value helps clarify whether it’s the right fit for your organization. The beauty of MDR is its versatility – it adapts to protect against the specific threats that keep business leaders awake at night.
Ransomware defense is perhaps the most compelling use case in today’s threat landscape. Ransomware attacks have evolved from simple opportunistic strikes to sophisticated, multi-stage operations that can cripple entire organizations. MDR’s 24/7 monitoring can detect the early warning signs – reconnaissance activities, privilege escalation attempts, or unusual file access patterns – and initiate containment before the encryption phase begins. Since 88% of ransomware attacks occur outside business hours, having experts monitoring your systems around the clock isn’t just helpful, it’s critical.
Phishing attack mitigation showcases MDR’s layered approach to security. While your email filters catch most malicious messages, some inevitably slip through. When an employee clicks that convincing fake link or opens that seemingly legitimate attachment, MDR can detect the subsequent malicious activity – malware execution, credential theft attempts, or communication with command-and-control servers – and respond immediately to prevent a full compromise.
As organizations accept cloud security, new challenges emerge. Cloud environments offer tremendous flexibility and scalability, but they also create new attack vectors. MDR services monitor cloud activity, identify suspicious configurations, detect unauthorized access attempts, and respond to threats targeting your cloud infrastructure. It’s like having security guards who understand both your physical office and your virtual workspace.
Insider threat detection addresses one of the most challenging security scenarios. Whether dealing with malicious insiders or well-meaning employees who accidentally compromise security, MDR can monitor user behavior patterns, detect unusual access requests, and identify potential data exfiltration attempts. This capability is particularly valuable because insider threats often bypass traditional perimeter defenses.
Lateral movement prevention is where MDR’s continuous monitoring really shines. Once attackers gain initial access, they typically try to move through your network to reach more valuable targets. MDR can detect these subtle movements – unusual network traffic patterns, privilege escalation attempts, or unauthorized access to sensitive systems – and stop attackers before they reach their ultimate objectives.
For organizations struggling with the cybersecurity skills gap, MDR provides an immediate solution to hybrid workforce security challenges. With employees working from various locations using different devices, the traditional network perimeter has dissolved. MDR provides centralized visibility and protection across distributed environments, ensuring consistent security regardless of where your team is working or what devices they’re using.
These real-world applications demonstrate how MDR transforms from a security service into a strategic business enabler, allowing you to operate confidently in an increasingly digital world.
How to Choose the Right MDR Provider
Selecting the right managed detection and response provider is one of the most important cybersecurity decisions you’ll make for your organization. Think of it like choosing a business partner who will have deep access to your systems and will be responsible for protecting your most valuable digital assets. This isn’t just about finding someone to monitor your network – you’re looking for experts who will become an extension of your security team, understanding your business and responding to threats as if they were sitting right next to you.
The foundation of any great MDR service starts with expertise and certifications. You want a provider whose security analysts, threat hunters, and incident responders have proven track records and the credentials to back up their claims. Don’t be shy about asking for specifics – what certifications do their team members hold? How many years of experience do they have with the types of threats your industry faces?
The technology stack is equally crucial. The best MDR providers use cutting-edge tools that can integrate seamlessly with your existing security infrastructure. Whether you’re running endpoint detection tools, cloud security platforms, or identity management systems, your MDR provider should be able to work with what you already have while filling in the gaps you didn’t even know existed.
Communication protocols might not sound exciting, but they become critically important at 2 AM when your systems are under attack. How quickly will they contact you? Who gets called first? What’s their escalation process? Clear, timely communication during a security incident can mean the difference between a minor disruption and a business-threatening crisis.
Service Level Agreements (SLAs) give you concrete expectations about response times. Look for providers who can commit to specific timeframes for detection, investigation, and remediation. These aren’t just numbers on paper – they represent how quickly your business can get back to normal after a security event.
Scalability ensures your security can grow with your business. As you expand, add new locations, or adopt new technologies, your MDR provider should be able to scale their services accordingly. You don’t want to outgrow your security partner just when you need them most.
When evaluating potential partners, consider their approach to threat intelligence, response capabilities, and reporting and visibility. The best providers don’t just react to threats – they proactively hunt for hidden dangers and give you clear insights into what’s happening in your environment.
Finding the right Managed Cybersecurity Services Provider means finding someone who truly understands your unique needs and can deliver reliable, effective protection that lets you sleep better at night.
Critical Questions to Ask Potential Providers
When you’re sitting across from potential managed detection and response providers, the questions you ask will reveal everything you need to know about their capabilities and approach. Think of this as a job interview where the stakes are your entire organization’s security.
Start by digging into their analyst expertise. Ask them directly: “What kind of expertise do the analysts who will be monitoring our systems possess?” You want to know about their certifications, their specializations, and their average experience level. If your business operates in healthcare, finance, or another regulated industry, make sure they have analysts who understand your specific compliance requirements and threat landscape.
Understanding how they stay current is equally important. The cyber threat landscape changes daily, so ask: “How does your MDR team stay current on the latest threats targeting organizations like ours?” The best providers have dedicated threat intelligence teams and continuous training programs that keep their analysts ahead of emerging attack methods.
Get specific about their response procedures. When they detect a threat in your environment, what exactly happens next? What are their Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) commitments? Can they take action on your behalf, or will they just provide recommendations? Understanding their escalation process helps you know what to expect during a real incident.
Integration capabilities can make or break an MDR implementation. Ask: “How will you integrate with our existing security tools and infrastructure?” They should be able to work with your current endpoint protection, network monitoring, cloud security platforms, and identity management systems. If they can’t integrate with your existing tools, you might end up with security blind spots.
Don’t forget about visibility and reporting. You need to understand what kind of ongoing insights you’ll receive. How often will you get reports? What metrics will they include? Will you have access to a real-time portal where you can see what’s happening in your environment? Transparency builds trust, and trust is essential in a security partnership.
Finally, ask about their approach to false positives. Nobody wants to be woken up at 3 AM for a false alarm. How do they filter out noise? What’s their process for ensuring you only get actionable, high-priority alerts? The best providers have sophisticated methods for enriching alerts with context, so you know immediately whether something requires urgent attention.
These conversations will help you find a provider who not only has the technical capabilities you need but also the operational maturity to be a true partner in protecting your business.
Frequently Asked Questions about Managed Detection and Response
When it comes to managed detection and response, we get a lot of great questions from business owners who want to understand exactly what they’re investing in. Let’s explore the most common ones we hear, and hopefully clear up any confusion you might have.
What is the difference between an MDR service and an in-house Security Operations Center (SOC)?
Think of an MDR service as getting all the benefits of having your own world-class security team without any of the headaches that come with building one from scratch. When you partner with an MDR provider, you’re essentially outsourcing the people, processes, and technology of a Security Operations Center to experts who live and breathe cybersecurity every single day.
Here’s the reality: building an in-house SOC is incredibly expensive and complex. You need to invest heavily in cutting-edge security tools, robust infrastructure, and most challenging of all, you need to find and keep a team of highly skilled cybersecurity professionals who can provide 24/7 coverage. With the current cybersecurity talent shortage affecting organizations worldwide, this is often easier said than done.
An MDR service solves this challenge neatly. Instead of spending months or years recruiting security analysts, threat hunters, and incident responders, you get immediate access to a dedicated team of experts. They’re already trained, certified, and experienced in handling the latest threats. Plus, you get that crucial 24/7 monitoring without having to worry about shift schedules, vacation coverage, or employee turnover.
While an in-house SOC does give you direct control over your security operations, MDR gives you something potentially more valuable: proven expertise and continuous coverage at a fraction of the cost and complexity.
How does MDR improve Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)?
This is where managed detection and response really shines, and the numbers are pretty impressive. Most organizations without proper MDR capabilities take an average of 277 days to detect a breach. That’s more than nine months of an attacker potentially having free rein in your systems!
MDR changes this game completely by combining the speed of advanced technology with the insight of human expertise. Our automated tools can instantly flag suspicious activities and anomalies across your entire digital environment. But here’s where it gets really powerful: instead of just generating another alert that might sit in a queue, our security analysts immediately review, investigate, and validate these detections.
This human element is crucial because it provides the context that machines simply can’t. Our experts can quickly eliminate false positives, correlate seemingly unrelated events, and understand the true scope of a threat. This means we can confirm real threats in minutes rather than days or weeks.
Once a threat is confirmed, our team doesn’t just send you a report and wish you luck. We initiate immediate response actions to contain and neutralize the threat. Many of our clients report seeing a 50% or greater reduction in both MTTD and MTTR after implementing our MDR services. What could have been a devastating months-long breach becomes a contained incident resolved in minutes.
Can MDR services integrate with my existing security tools?
Absolutely, and this is actually one of the biggest advantages of working with a quality managed detection and response provider. We understand that you’ve likely invested significant time and money in your current security infrastructure, and the last thing we want to do is force you to start from scratch.
Leading MDR providers are designed to work seamlessly with a wide range of existing security technologies. Whether you’re using endpoint detection tools, firewalls, SIEM systems, cloud security platforms, or identity management solutions, we can typically integrate with what you already have in place.
This integration approach does more than just preserve your existing investments – it actually makes them more powerful. By ingesting and correlating data from all your security tools, we create a unified view of your security posture that provides much richer context for threat detection and investigation. Instead of having multiple tools generating separate alerts that your team has to piece together, we consolidate everything into a comprehensive security picture.
The result is improved detection capabilities, faster investigations, and more effective responses. Your existing tools become force multipliers rather than isolated point solutions, ensuring you get maximum value from every security investment you’ve made.
Conclusion: Partnering for a More Secure Future
The cybersecurity landscape has fundamentally shifted. Managed detection and response isn’t just another security service—it’s become the strategic partnership that forward-thinking organizations rely on to stay ahead of increasingly sophisticated threats. When cyberattacks are evolving faster than ever and skilled security professionals are harder to find than a parking spot at the mall during the holidays, traditional defenses simply can’t keep up.
What we’ve explored throughout this guide shows that MDR offers something unique: the perfect marriage of cutting-edge technology and human expertise. It’s not about replacing your team or overwhelming them with more tools. Instead, it’s about giving them the support they need to focus on what matters most—growing your business while knowing your digital assets are under constant, expert protection.
The benefits speak for themselves. Organizations using managed detection and response see dramatic improvements in their security posture, often reducing their Mean Time to Detect from months to minutes. They gain 24/7 coverage that never sleeps, proactive threat hunting that catches what automated tools miss, and rapid incident response that minimizes damage when attacks do occur.
But perhaps most importantly, MDR addresses the human element. It solves the cybersecurity skills gap by providing instant access to a team of dedicated experts who live and breathe security every day. These aren’t just technicians monitoring screens—they’re seasoned professionals who understand the nuances of modern threats and can guide you through even the most complex incidents.
At Concertium, we’ve spent nearly 30 years in the trenches of cybersecurity, and we’ve seen how the threat landscape has evolved. Our Collective Coverage Suite (3CS) combines AI-improved observability with automated threat eradication because we believe in solutions that adapt and grow with your business. We don’t just monitor your systems; we become an extension of your team, committed to keeping you secure so you can focus on what you do best.
Choosing an MDR provider isn’t just about outsourcing a security function—it’s about finding a partner who’s as invested in your success as you are. It’s about peace of mind, knowing that while you’re building your business, experts are actively defending it around the clock. That kind of partnership isn’t just valuable—it’s essential for future-proofing your organization against whatever threats tomorrow might bring.
Managed Detection and Response