Incident response and computer forensics have become essential defenses against the rising tide of cyberattacks. When hackers strike, every second counts—and having the right processes in place can save your business millions.
Key Components of Incident Response and Computer Forensics:
• Incident Response (IR) – Rapid detection, containment, and recovery from active cyber threats
• Digital Forensics – Scientific collection and analysis of digital evidence for investigations
• DFIR Integration – Combined approach that preserves evidence while stopping attacks
• Goal – Minimize damage, restore operations, and support legal action against attackers
The stakes couldn’t be higher. Data breaches now cost an average of $4.45 million, with organizations taking 277 days to identify and contain attacks. But here’s the good news: companies with tested incident response plans save $1.49 million per breach and experience 35% lower costs overall.
Yet only 39% of organizations have consistent, enterprise-wide incident response plans. This gap leaves businesses vulnerable to ransomware, data theft, and regulatory penalties.
As one cybersecurity expert put it: “Listening to the news on a daily basis suggests that it is a matter of when rather than if any given computing device will be compromised.”
The solution isn’t just faster response—it’s smarter response. Modern DFIR combines real-time threat hunting with forensic-grade evidence collection. This dual approach lets you stop attackers while building the legal case to hold them accountable.
Easy incident response and computer forensics word list:
Incident Response vs. Computer Forensics: Two Sides of Incident Response and Computer Forensics
When a cyberattack hits your organization, you need two different superpowers working together. Incident response and computer forensics might sound like the same thing, but they’re actually complementary disciplines that tackle different parts of the cybersecurity puzzle.
Think of it this way: incident response is like the emergency room—fast, focused, and designed to save lives. Computer forensics is more like the detective work that happens afterward—methodical, thorough, and built to stand up in court.
The magic happens when these two approaches work together as DFIR (Digital Forensics and Incident Response). Instead of having your emergency responders accidentally trampling over the crime scene, you get a coordinated response that stops the bleeding and preserves the evidence.
| Incident Response | Computer Forensics |
|---|---|
| Speed and containment | Thoroughness and legal admissibility |
| Minimize damage | Preserve evidence |
| Restore operations | Support investigations |
| NIST 800-61 framework | Scientific methodology |
| Hours to days | Days to months |
What Is Incident Response and Computer Forensics?
Incident response is your organization’s cyber-911 service. When attackers breach your defenses, IR teams jump into action to detect threats, contain the damage, and get your systems back online. Speed is everything here—every minute counts when ransomware is encrypting your files or hackers are stealing customer data.
Computer forensics takes a completely different approach. It’s the scientific process of collecting, preserving, and analyzing digital evidence with the same rigor you’d expect from a crime lab. Forensic investigators need to prove not just what happened, but exactly how it happened and who did it—all while maintaining evidence that will hold up in court.
The beauty of incident response and computer forensics working together is that you don’t have to choose between speed and thoroughness. DFIR teams can simultaneously stop attackers and preserve the digital crime scene.
At the heart of both disciplines is protecting what security professionals call the CIA triad: Confidentiality (keeping sensitive data private), Integrity (preventing unauthorized changes), and Availability (ensuring systems work when you need them).
Why DFIR Matters for Modern Security
Here’s the sobering reality: the average data breach takes 277 days to identify and contain. That’s more than nine months of attackers potentially roaming around your network, stealing data, and causing havoc.
But organizations that invest in proper incident response and computer forensics capabilities see dramatic improvements. Companies with tested incident response plans save an average of $1.49 million per breach—that’s 35% lower costs compared to organizations flying blind.
The threat landscape isn’t getting any easier either. Ransomware was involved in 24% of all breaches in 2023, and these attacks are becoming more sophisticated every year. The old approach of hoping for the best simply doesn’t work anymore.
What does work is combining the speed of modern incident response with the precision of digital forensics. Organizations using security AI and automation extensively can reduce their breach lifecycle by 108 days. That’s the difference between a manageable incident and a company-ending disaster.
The frameworks have evolved too. While both NIST and SANS provide excellent guidance, modern DFIR goes beyond traditional playbooks to include threat intelligence, automated response, and real-time forensic collection.
Incident Response Cybersecurity has transformed from reactive firefighting to proactive threat hunting. The goal isn’t just responding to incidents—it’s building the capability to detect, contain, and investigate threats before they become front-page news.
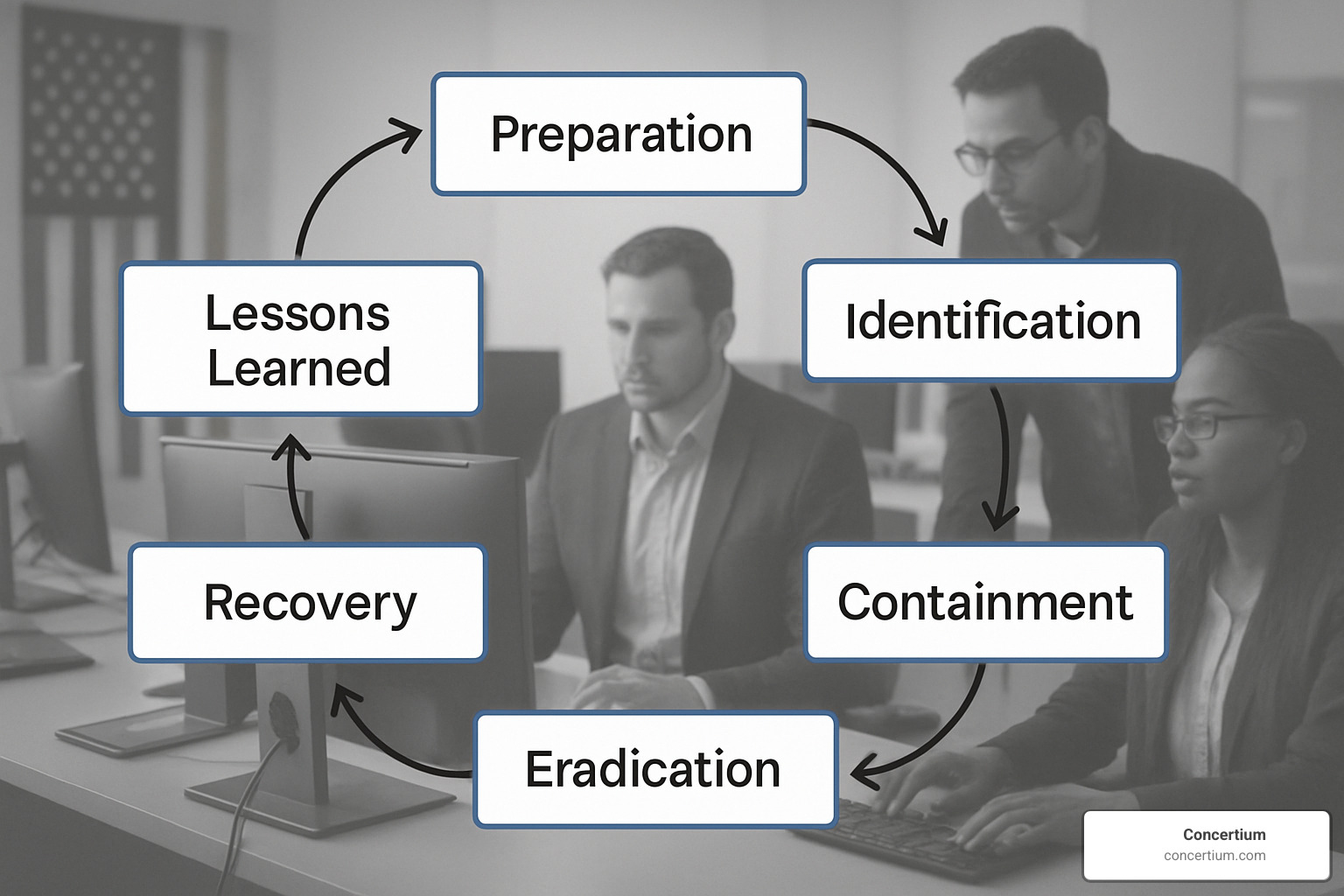
The Incident Response Process: From Alert to Recovery
Picture this: it’s 2 AM, and your security monitoring system starts blaring alerts. A potential breach is underway. What happens next could determine whether you’re dealing with a minor incident or a million-dollar disaster.
This is where incident response and computer forensics truly shine. The NIST framework gives us a roadmap with six essential phases that transform chaos into controlled, methodical action.
Preparation sets the foundation before any attack occurs. Think of it as your cybersecurity insurance policy. Your Computer Security Incident Response Team (CSIRT) needs clearly defined roles, tested procedures, and ready access to forensic tools. This phase also involves creating policies that balance rapid response with evidence preservation—a critical balance for effective DFIR operations.
When threats emerge, detection and analysis becomes your early warning system. Modern Security Information and Event Management (SIEM) systems can process millions of events hourly, but human expertise separates real threats from false alarms. Security Orchestration, Automation, and Response (SOAR) platforms, Endpoint Detection and Response (EDR) tools, and Extended Detection and Response (XDR) solutions work together to accelerate this crucial phase.
Containment operates on two levels. Short-term containment might involve quickly isolating infected systems or blocking malicious IP addresses—stopping the bleeding immediately. Long-term containment focuses on implementing temporary fixes while planning permanent solutions. The key challenge here is moving fast without destroying the digital evidence that forensic investigators will need later.
Eradication goes beyond surface-level fixes. You’re not just removing malware or disabling compromised accounts—you’re identifying and fixing the root cause that allowed the attack to succeed. This might involve patching vulnerabilities, updating security configurations, or strengthening access controls.
Recovery brings your organization back to normal operations safely. This phase includes validating that systems are truly clean, monitoring for signs of re-infection, and gradually restoring services. Recovery often takes weeks or months for complex incidents, requiring patience and thorough testing.
Lessons learned completes the cycle with a post-incident review. What worked well? What fell short? How can your team improve? This phase feeds directly back into preparation, creating a continuous improvement loop that strengthens your defenses over time.
Key Objectives of Incident Response
Every incident response effort aims to achieve four critical goals that protect your organization’s future.
Damage control means stopping attackers before they can spread throughout your network or steal more sensitive data. Speed matters here—every minute of delay can exponentially increase the scope of compromise.
Business continuity keeps your critical operations running even during an active incident. This requires careful planning to determine which systems absolutely must stay online and which can be temporarily sacrificed for security.
Regulatory compliance ensures you meet legal notification requirements within mandated timeframes. Many regulations require breach notifications within 72 hours, making rapid incident classification essential.
Communication balances transparency with security. Stakeholders need timely updates without creating panic or providing attackers with information about your response efforts.
Common IR Frameworks You Can Adopt
While NIST SP 800-61 provides the gold standard for incident response, other frameworks offer valuable perspectives custom to different organizational needs.
NIST Cybersecurity Framework 2.0 integrates incident response across six functions: Govern, Identify, Protect, Detect, Respond, and Recover. This approach treats IR as part of continuous risk management rather than a standalone emergency activity.
SANS Institute offers practical, hands-on methodologies with detailed playbooks for specific incident types like ransomware, data theft, or insider threats. Their approach emphasizes real-world applicability and includes extensive training resources for building team capabilities.
The key is choosing a framework that fits your organization’s size, industry, and risk profile. A small business needs different procedures than a multinational corporation, and healthcare organizations face different regulatory requirements than financial services companies.
Modern incident response increasingly relies on automation to reduce response times from hours to minutes for common incident types. These technologies handle routine tasks automatically, freeing your human experts to focus on complex analysis and strategic decisions.
For detailed guidance on implementing these frameworks effectively, explore our comprehensive Incident Response Frameworks guide. You’ll also find practical steps in our guide on How to Respond to a Data Security Incident.
The Digital Forensics Process: Collecting Court-Ready Evidence
When it comes to incident response and computer forensics, the forensics side is where patience pays off. While incident responders race against time to stop attacks, digital forensics investigators take a different approach—methodical, precise, and designed to build evidence that will stand up in court.
Think of digital forensics as detective work for the digital age. Every click, every file transfer, and every login leaves traces. The trick is collecting and analyzing these digital breadcrumbs without accidentally stepping on them in the process.
The forensic process follows four critical phases that ensure your evidence is bulletproof: collection, examination, analysis, and reporting. Miss a step or cut corners, and your evidence could be thrown out of court faster than you can say “objection.”
Evidence preservation starts the moment you suspect a security incident. Forensic investigators use specialized hardware called write-blockers to create exact copies of storage devices. These tools ensure that reading data doesn’t accidentally change it—because even accessing a file can alter its metadata.
Forensic imaging creates bit-for-bit copies of entire hard drives, capturing not just active files but also deleted data, hidden partitions, and file fragments. It’s like taking a perfect snapshot of a crime scene, preserving everything exactly as it was found.
Chain of custody documentation begins immediately. Every person who touches the evidence, every tool used, and every analysis performed gets recorded. This paper trail proves the evidence hasn’t been tampered with between collection and courtroom.
Data collection extends beyond traditional hard drives. Modern investigations must gather evidence from memory dumps that capture what was running in RAM, system logs that record user activities, network packets that show data movement, and cloud artifacts scattered across multiple service providers.
Examination and analysis involve powerful forensic tools that can process terabytes of data to find relevant evidence. Investigators look for patterns, correlate events across systems, and build timelines of attacker activity. This phase requires both technical skills and investigative instincts.
Reporting translates technical findings into clear, understandable language. The best forensic analysis means nothing if you can’t explain it to a jury or executive team. Reports must be detailed enough for peer review yet accessible enough for non-technical audiences.
Critical Evidence Sources
Digital evidence comes from everywhere in modern IT environments, and each source tells part of the story. Disk images provide the most comprehensive view, capturing entire file systems including deleted files and system metadata. They’re like digital time capsules that preserve everything that happened on a computer.
Memory dumps reveal what was actually running when the incident occurred. This volatile data shows active malware, network connections, and encryption keys that exist only in RAM. Since many modern attacks use “fileless” malware that never touches the hard drive, memory forensics has become absolutely critical.
System logs create detailed timelines of user activities and system events. Windows Event Logs, Linux syslog files, and application logs record who did what and when they did it. The challenge is correlating logs from multiple systems to build a complete picture of the attack.
Network packet captures show how data moved across your network. They can reveal command-and-control communications, data theft, and how attackers moved between systems. Of course, encrypted traffic requires additional techniques to analyze effectively.
Cloud and SaaS artifacts present unique challenges since evidence might be scattered across multiple providers in different countries. Cloud forensics requires specialized tools and careful coordination to collect evidence without disrupting business operations.
Legal Considerations and Chain of Custody
For digital evidence to be admissible in court, it must meet strict legal standards. The evidence must be authentic, complete, reliable, and believable. This isn’t just about having good technical analysis—it’s about proving that analysis is trustworthy.
Hash integrity verification uses mathematical algorithms like SHA-256 to create unique fingerprints for files and disk images. If even a single bit changes, the hash value changes too. This provides ironclad proof that evidence hasn’t been altered since collection.
Documentation requirements are extensive and unforgiving. Investigators must record who collected the evidence, when and how it was collected, where it was stored, and who had access to it. Any gap in this chain of custody can lead to evidence being excluded from legal proceedings.
Compliance considerations vary by jurisdiction and industry. Federal laws like the Computer Fraud and Abuse Act impose restrictions on how digital evidence can be collected and used. Organizations must work closely with legal counsel before conducting forensic investigations to ensure they don’t inadvertently break the law while investigating crimes.
The intersection of technology and law creates complex challenges that require both technical expertise and legal knowledge. That’s why many organizations partner with experienced forensics providers who understand both the technical and legal requirements.
For more detailed guidance on conducting proper forensic investigations, check out our Data Breach Analysis Guide which covers best practices for preserving evidence while meeting legal requirements.
How Incident Response and Computer Forensics Work Together
Here’s where things get interesting. When incident response and computer forensics work as a unified team, you get something much more powerful than either discipline alone. Think of it like having both a paramedic and a detective at a crime scene—one saves lives while the other preserves evidence.
Traditional incident response teams often face a painful choice: stop the attack quickly or preserve evidence carefully. Rush to contain the threat, and you might destroy crucial evidence. Take time to collect forensics, and the attack spreads further. Integrated DFIR solves this dilemma by doing both simultaneously.
When a ransomware attack hits, for example, an integrated team doesn’t just pull network cables. They isolate infected systems while capturing memory dumps and disk images. They preserve volatile evidence that disappears the moment you power down a computer, all while preventing the malware from encrypting more files.
Threat intelligence creates a feedback loop that makes both sides stronger. Forensic analysis from one incident reveals new attack techniques that improve future response playbooks. Meanwhile, rapid incident response provides fresh malware samples for deeper forensic analysis, creating intelligence that protects other organizations too.
Consider a recent data exfiltration case. Security monitoring detected unusual network traffic at 2 AM—large amounts of data flowing to an unknown external server. The incident response and computer forensics team worked in perfect sync. They blocked the suspicious communications while preserving network packet captures. They analyzed system logs to identify exactly what data was stolen while implementing additional monitoring to catch any remaining backdoors.
This integrated approach revealed that attackers had been inside the network for three months, slowly mapping systems and identifying valuable data. Pure incident response would have stopped the immediate threat but missed the bigger picture. Pure forensics would have provided a complete timeline but allowed ongoing data theft.
Our Comprehensive Guide to Managing Incident Types shows how this integrated approach works across different attack scenarios, from insider threats to advanced persistent threats.
Automation’s Impact on DFIR (SOAR, EDR, XDR)
The cybersecurity world moves too fast for purely manual responses. Modern DFIR teams leverage Security Orchestration, Automation, and Response (SOAR) platforms that can execute response playbooks in minutes instead of hours. When malware is detected, SOAR can automatically isolate the infected system, collect initial forensic data, and alert the human team—all before a human analyst even sees the alert.
Endpoint Detection and Response (EDR) tools act like security cameras with superpowers. They record everything happening on endpoints and can automatically collect forensic artifacts when suspicious activity is detected. Instead of manually imaging hard drives, EDR tools can instantly provide detailed timelines of exactly what the attacker did and when.
Extended Detection and Response (XDR) takes this a step further by correlating data across endpoints, networks, and cloud services. This gives investigators a complete picture of attack campaigns that span multiple systems. Imagine trying to solve a puzzle where pieces are scattered across different rooms—XDR brings all the pieces together.
The results speak for themselves: organizations using extensive security automation reduce their breach lifecycle by 108 days. That’s nearly four months faster recovery, which translates to millions in cost savings for large breaches.
But automation isn’t about replacing human expertise—it’s about amplifying it. While machines handle routine data collection and initial analysis, skilled analysts focus on the complex investigative work that requires human intuition and creativity. Our Incident Management Maturity Model helps organizations find the right balance between automation and human expertise.
In-House vs. Outsourced DFIR Services
Building your own DFIR team sounds appealing until you see the price tag. Skilled DFIR professionals command six-figure salaries, and you need them available 24/7 since cyber attacks don’t respect business hours. Enterprise forensic tools can cost hundreds of thousands of dollars, and keeping analysts trained on the latest techniques requires ongoing investment.
Many organizations find they can’t justify the full-time cost for capabilities they hope never to use. It’s like maintaining a full fire department for a single building—the expertise is crucial when you need it, but the utilization might not support the investment.
Outsourced DFIR services provide immediate access to expert capabilities without the overhead. Specialized providers maintain teams of certified analysts, invest in the latest tools, and see a variety of incidents that keeps their skills sharp. They can often respond faster than internal teams because they’re already mobilized and ready to go.
The downside? External providers need time to understand your unique environment, and they might not be instantly available when seconds count. They also cost more per hour than internal staff, though the total cost is often lower when you factor in benefits, training, and tool licensing.
Smart organizations often choose a hybrid approach. They maintain basic incident response capabilities internally—enough to handle initial containment and common incidents. For complex forensic investigations or major breaches that exceed internal capacity, they partner with specialized providers.
Key questions to ask when evaluating DFIR services: Do they have forensic expertise with your specific technologies? Are their analysts certified and experienced? Do they understand your industry’s regulatory requirements? Can they respond quickly to your geographic locations? What’s included in their service scope—just reactive response or proactive threat hunting too?
Our Post-Breach Services can help you steer these decisions and find the right balance of internal capabilities and external expertise for your organization’s specific needs and budget.
Building a High-Performance DFIR Capability
Creating an effective DFIR program requires the right combination of people, processes, and technology. Whether you’re building internal capabilities or working with external providers, certain elements are essential for success.
Essential DFIR Skills span both technical and soft skills:
- Technical Expertise – Operating systems, networking, malware analysis, forensic tools
- Investigative Skills – Critical thinking, attention to detail, documentation
- Communication – Ability to explain technical findings to non-technical audiences
- Legal Knowledge – Understanding of evidence handling and legal requirements
- Stress Management – Ability to work effectively under pressure during incidents
Key Certifications validate DFIR expertise:
- GIAC Certified Incident Handler (GCIH) – Foundational incident response skills
- GIAC Certified Forensic Analyst (GCFA) – Windows forensics and incident response
- GIAC Certified Forensic Examiner (GCFE) – Advanced forensic analysis
- SANS FOR508 – Advanced incident response, threat hunting, and digital forensics
- Certified Computer Security Incident Handler (CSIH) – Incident handling methodology
Essential DFIR Tools include both open-source and commercial options:
Forensic Analysis:
- Autopsy (open-source digital forensics platform)
- Volatility (memory forensics framework)
- Sleuth Kit (file system analysis tools)
- YARA (malware identification and classification)
Incident Response:
- MISP (threat intelligence sharing platform)
- TheHive (incident response platform)
- GRR (remote live forensics framework)
- Velociraptor (endpoint visibility and collection)
Network Analysis:
- Wireshark (network protocol analyzer)
- NetworkMiner (network forensic analysis tool)
- Zeek (network security monitoring)
- Suricata (intrusion detection system)
Malware Analysis:
- REMnux (Linux distribution for malware analysis)
- Cuckoo Sandbox (automated malware analysis)
- IDA Pro (disassembler and debugger)
- Ghidra (reverse engineering framework)
The global digital forensics market is projected to reach $8.7 billion by 2027, growing at 10.9% annually. This growth reflects increasing demand for DFIR capabilities as cyber threats continue to evolve.
Preparing Before the Breach Happens
Proactive preparation is the foundation of effective DFIR. Organizations that prepare before incidents occur respond faster and more effectively when attacks happen.
Policies and Procedures should define:
- Incident classification criteria
- Escalation procedures and contact information
- Evidence handling requirements
- Communication protocols
- Legal notification requirements
Asset Inventory must be current and comprehensive. You can’t protect what you don’t know about. Automated findy tools can help maintain inventories of hardware, software, and data across your environment.
Monitoring and Detection capabilities should provide visibility across:
- Network traffic and communications
- Endpoint activity and process execution
- User behavior and access patterns
- Cloud services and SaaS applications
- Physical security systems
Backup and Recovery systems must be tested regularly and protected from attack. Ransomware often targets backup systems, so air-gapped or immutable backups are essential.
Tabletop Exercises test your incident response procedures without the pressure of a real incident. These exercises help identify gaps in your plans and build muscle memory for your response team.
Our Post-Breach Guide provides detailed checklists for incident preparation and response.
Common Challenges and How to Overcome Them
Even well-prepared organizations face challenges when implementing DFIR capabilities:
Alert Fatigue occurs when security tools generate too many false alarms. Analysts become overwhelmed and may miss real threats. Solutions include tuning detection rules, implementing threat intelligence, and using automation to filter low-priority alerts.
Evidence Sprawl happens as data spreads across multiple systems, cloud services, and geographic locations. Modern investigations might need to collect evidence from dozens of systems across multiple time zones. Centralized logging and standardized forensic procedures help manage this complexity.
Remote Endpoints complicate evidence collection, especially for organizations with distributed workforces. Cloud-based EDR tools and remote forensic capabilities can help, but organizations need policies for handling personal devices and home networks.
Encryption can protect data from attackers but also complicates forensic analysis. Organizations need key management procedures that balance security with investigative needs. Memory forensics can sometimes recover encryption keys from RAM.
Frequently Asked Questions about Incident Response and Computer Forensics
When organizations face cyber incidents, they often have urgent questions about how incident response and computer forensics work together. Here are the most common questions we hear from security teams and business leaders.
How does digital forensics support legal investigations?
Digital forensics serves as the scientific backbone for any legal proceeding involving cyber incidents. Think of forensic investigators as digital detectives who must follow strict protocols to ensure their findings will hold up in court.
The process starts with evidence preservation. Forensic experts use specialized tools to create exact copies of digital devices without altering the original data. Every file, deleted item, and system log gets captured using techniques that maintain the evidence’s integrity.
Chain of custody documentation tracks every person who handles the evidence from collection to courtroom. This paper trail proves the evidence hasn’t been tampered with. Investigators use cryptographic hashes—digital fingerprints—to verify that evidence remains unchanged throughout the investigation.
The evidence collected can make or break legal cases. Forensic analysis might reveal how attackers entered your systems, what data they accessed, and whether they had inside help. This information supports criminal prosecutions, helps with insurance claims, and provides the foundation for civil lawsuits against attackers.
For regulatory investigations, forensic evidence demonstrates whether your organization followed required security practices. This can be the difference between facing penalties or showing you acted responsibly when the incident occurred.
What are the main steps in an incident response plan?
Every effective incident response plan follows a structured approach, though real incidents rarely unfold as neatly as the textbooks suggest. The NIST framework provides six phases that guide response teams through the chaos.
Preparation happens long before any incident occurs. Your team develops policies, trains staff, and deploys monitoring tools. This phase also includes creating contact lists, establishing communication procedures, and testing your backup systems.
Detection and Analysis involves spotting potential incidents and determining if they’re real threats. Modern organizations face thousands of security alerts daily, so this phase requires both automated tools and human expertise to separate genuine incidents from false alarms.
Containment focuses on stopping the attack from spreading while preserving evidence. Short-term containment might involve isolating infected computers or blocking malicious network traffic. Long-term containment implements temporary fixes while you plan permanent solutions.
Eradication removes the threat completely and fixes the vulnerabilities that allowed the attack. This might involve patching software, removing malware, or disabling compromised user accounts.
Recovery brings your systems back online safely. Teams monitor carefully for signs that attackers might return while gradually restoring normal operations. This phase often takes weeks or months for complex incidents.
Lessons Learned completes the cycle with a thorough review of what worked and what didn’t. These insights feed back into the preparation phase, improving your response for next time.
These phases often overlap. Analysis continues throughout the incident as new evidence emerges, and you might need to return to earlier phases if the situation changes.
Which certifications are most valuable for DFIR professionals?
The cybersecurity field values hands-on experience over academic credentials, and incident response and computer forensics certifications reflect this practical focus. The most respected programs require candidates to demonstrate real-world skills, not just memorize theory.
GIAC certifications lead the industry for DFIR professionals. The GCIH (Certified Incident Handler) provides foundational incident response skills that every security professional should master. It covers threat detection, analysis techniques, and response coordination.
For deeper forensic expertise, the GCFA (Certified Forensic Analyst) focuses on Windows forensics and incident response integration. This certification teaches investigators how to extract evidence from compromised systems while supporting ongoing response efforts.
The GCFE (Certified Forensic Examiner) takes forensic analysis to the next level with advanced techniques for complex investigations. Professionals with this certification can handle sophisticated attacks and provide expert testimony in legal proceedings.
SANS training courses often accompany these certifications and provide immediate value. FOR508 (Advanced Incident Response, Threat Hunting, and Digital Forensics) combines incident response with proactive threat hunting, reflecting how modern DFIR teams operate.
FOR572 (Network Forensic Analysis) specializes in analyzing network traffic to understand how attackers moved through compromised environments. This skill becomes crucial as attacks increasingly target cloud services and remote workers.
These certifications require significant investment in time and money, but they demonstrate commitment to the field and provide skills that employers desperately need. The global shortage of qualified DFIR professionals means certified experts often command premium salaries and have excellent career prospects.
The key is choosing certifications that match your career goals and your organization’s needs. Someone focused on malware analysis might prioritize different credentials than someone leading incident response teams.
Conclusion
The reality is simple: incident response and computer forensics aren’t nice-to-have capabilities anymore—they’re your organization’s lifeline when cyber threats strike. With attacks costing businesses an average of $4.45 million and taking 277 days to fully resolve, every organization faces the same critical question: not if you’ll be targeted, but how prepared you’ll be when it happens.
The integrated DFIR approach we’ve explored throughout this guide offers something powerful—the ability to fight back intelligently. You get the speed of rapid incident response combined with the precision of forensic investigation. This isn’t just about stopping attacks; it’s about learning from them and building stronger defenses for the future.
The financial benefits speak for themselves. Organizations with tested incident response plans consistently save $1.49 million per breach and see 35% lower overall costs. That’s not just savings—that’s the difference between a manageable incident and a business-threatening crisis.
But here’s what the statistics don’t capture: the peace of mind that comes from knowing you’re prepared. When your security team can respond confidently to threats, when your forensic capabilities can uncover the full scope of an attack, and when your leadership trusts your security program—that’s when cybersecurity transforms from a cost center into a competitive advantage.
At Concertium, we’ve spent nearly 30 years helping organizations build exactly this kind of confidence. Our Collective Coverage Suite (3CS) brings together AI-improved observability with automated threat eradication, creating the foundation for effective incident response and computer forensics. We understand that no two organizations face identical threats, which is why we focus on custom solutions that fit your specific environment and risk profile.
Whether you choose to build internal DFIR capabilities, partner with external experts, or blend both approaches, the most important step is taking action today. Cyber threats evolve constantly, but the fundamentals of good preparation remain the same: clear processes, trained people, and the right technology working together seamlessly.
Your journey toward stronger incident response and computer forensics capabilities doesn’t have to be overwhelming. Start with the basics—assessment, planning, and gradual implementation. Focus on building capabilities that match your risk profile and business needs. Most importantly, even small improvements in preparation can lead to dramatic improvements in outcomes.
Ready to take the next step? Our team can help you evaluate your current DFIR readiness and develop a strategy that makes sense for your organization. Learn more about building comprehensive capabilities with our guide to Incident Response Frameworks and find how the right preparation can help you turn cyber incidents from disasters into manageable events.