AI Overview:
Learn how to monitor and manage network connections in 2025 with AI, SNMP, and NetFlow. Discover key metrics, tools, and best practices to improve uptime, performance, and security across hybrid and cloud networks.
How to monitor and manage network connections: Critical 2025
Why Network Connection Monitoring is Critical for Modern Business
Learning how to monitor and manage network connections is essential for business survival. With 91% of large enterprises reporting that a single hour of IT downtime costs at least $300,000—and nearly half saying it costs millions—the stakes have never been higher.
Quick Answer: How to Monitor and Manage Network Connections
- Check connectivity status – Use built-in tools like Windows
netstator mobile APIs. - Set up monitoring protocols – Enable SNMP, NetFlow, or ICMP on network devices.
- Track key metrics – Monitor bandwidth, latency, packet loss, and uptime.
- Create dashboards – Visualize network topology and real-time performance.
- Configure alerts – Set thresholds for proactive issue detection.
- Analyze and respond – Use logs and metrics to troubleshoot problems.
Your network is the nervous system of your business. Every transaction, video call, and cloud application depends on stable connections. When networks fail, productivity plummets and customer service grinds to a halt.
Modern businesses face a storm of complexity from hybrid clouds, remote work, and IoT devices. The traditional approach of waiting for users to report problems is no longer viable. Proactive monitoring changes everything. By spotting issues like high router CPU or unusual traffic patterns before they escalate, you prevent outages and security breaches.
This guide covers the essential concepts, practical steps, and best practices to turn network monitoring into a strategic business advantage.
Similar topics to how to monitor and manage network connections:
- best network monitoring tools open source
- manage and monitor devices on a network
- network monitor software
The Pillars of Network Monitoring: Key Concepts and Components
Effective network monitoring is like a continuous health checkup for your digital infrastructure, aiming to catch problems before they become expensive disasters. It involves several key areas:
- Network Performance Monitoring (NPM): Focuses on speed and efficiency, ensuring data moves fast and applications respond quickly.
- Network Availability Monitoring: Acts as a 24/7 guard, ensuring devices and services remain online and accessible.
- Configuration Management: Keeps a detailed maintenance log of all device settings and changes.
- Cloud Monitoring: Extends your watch to cloud-based services and applications, which are integral to most modern businesses.
Core Metrics to Track for Optimal Performance
Understanding how to monitor and manage network connections means tracking the right numbers. These are your network’s vital signs:
- Bandwidth Utilization: Shows how much of your network’s capacity is in use. Consistently high usage (80%+) signals a need for upgrades.
- Latency: Measures data transfer delays. High latency cripples real-time applications like VoIP and video calls.
- Packet Loss: Occurs when data packets don’t reach their destination. Even 1% loss can disrupt streaming and file transfers.
- Uptime and Downtime: Reveals network reliability. Most businesses need 99.9% uptime or better, as 99% still means over 7 hours of downtime per month.
- Jitter: Refers to inconsistent packet timing, causing robotic-sounding voice calls and unwatchable video.
- Error Rates: High error rates on network interfaces often point to hardware problems or bad cables.
- Throughput: Measures actual data transfer speeds, which are often lower than theoretical bandwidth.
- CPU and Memory Usage: High usage on devices like routers and switches creates bottlenecks that slow the entire network.
Essential Protocols and Data Collection Methods
These protocols are the backbone of data collection for any monitoring system:
- Simple Network Management Protocol (SNMP): The universal language for network devices, allowing tools to collect performance data and status information.
- NetFlow and sFlow: Provide detailed traffic analysis, showing who is talking to whom and which applications consume the most bandwidth.
- Internet Control Message Protocol (ICMP): Powers diagnostic tools like ping and traceroute to test device reachability.
- Windows Management Instrumentation (WMI): Offers deep visibility into Windows systems without requiring agents.
- Secure Shell (SSH): Enables secure, encrypted monitoring and management of Unix and Linux systems.
- Extended Berkeley Packet Filter (eBPF): A cutting-edge technology for detailed packet analysis with minimal performance impact.
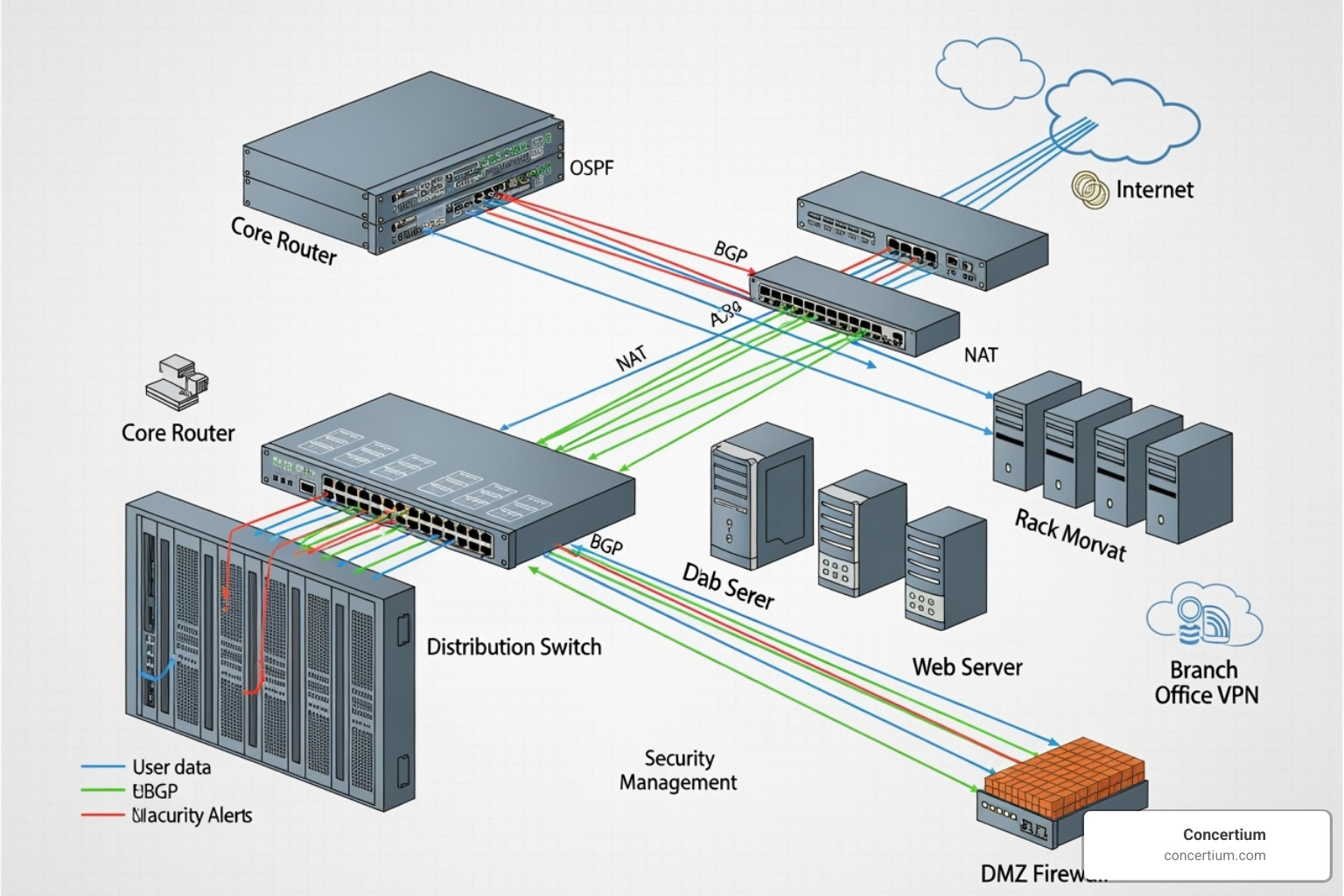
Devices and Infrastructure Under the Microscope
Effective monitoring requires watching every component in your digital ecosystem:
- Routers and Switches: The network backbone. Monitoring them prevents bottlenecks and outages.
- Firewalls: Must be monitored to balance security with performance, as an overloaded firewall can slow traffic to a crawl.
- Physical and Virtual Servers: Host critical applications. Monitoring their network interfaces is crucial for performance.
- Cloud Infrastructure (Azure, AWS): Requires modern monitoring solutions that can adapt to dynamic, scalable environments.
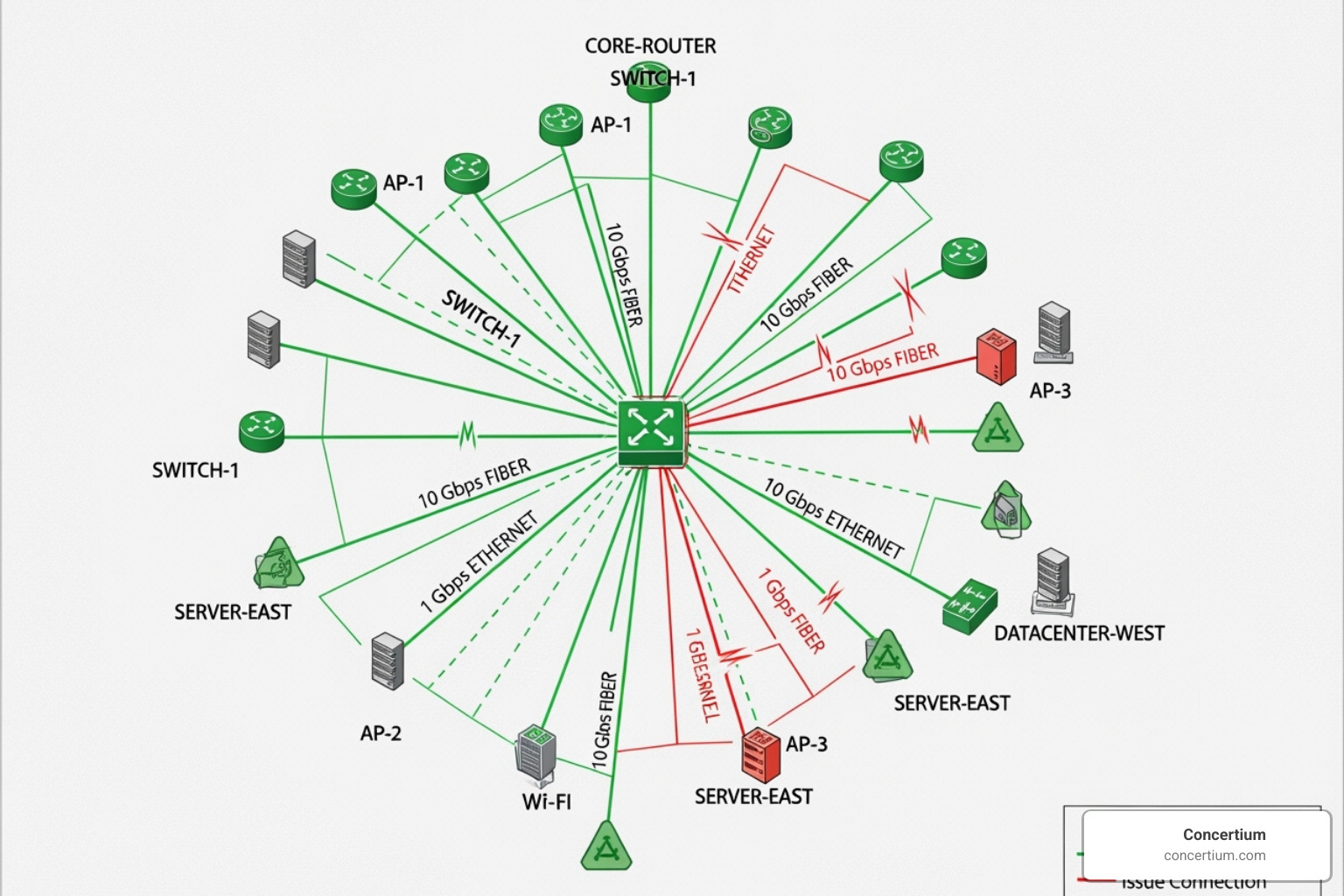
- Wireless Networks: Monitoring signal strength and access point performance ensures reliable mobile connectivity.
- Containerized Applications (Kubernetes): Need modern tools that can track ephemeral network connections.
- DNS Servers: Failures are catastrophic. Monitoring response times and accuracy is essential.
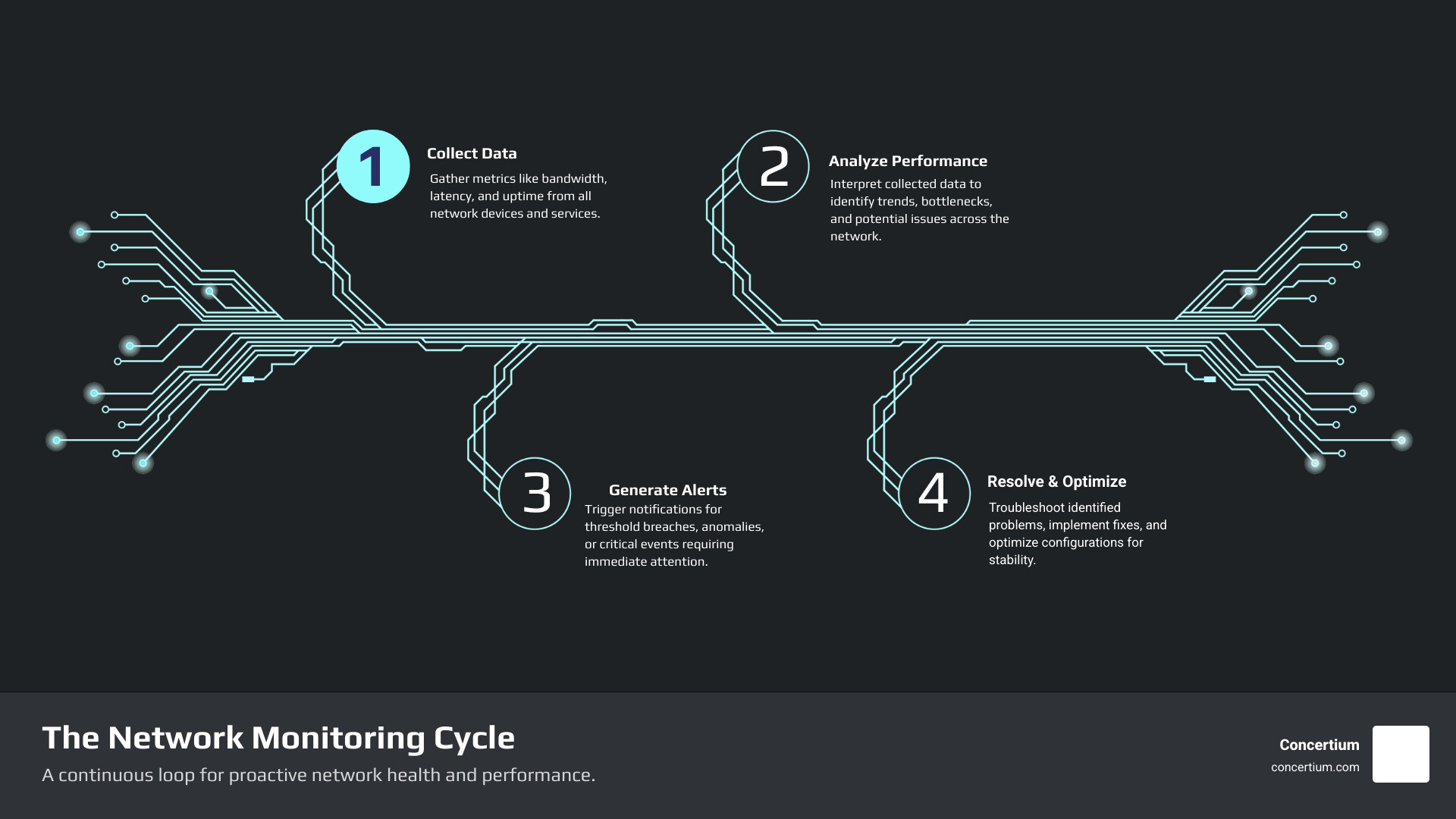
How to Monitor and Manage Network Connections: A Practical Guide
Effectively learning how to monitor and manage network connections involves three key activities: data collection using protocols like SNMP and NetFlow, network topology mapping to visualize how devices are connected, and alerting and reporting to transform raw data into actionable insights.
Setting Up Your Monitoring System: From Data to Dashboards
Building an effective monitoring system follows a structured approach:
- Define Clear Monitoring Objectives: What are you trying to achieve? Prevent outages? Improve application performance? Your goals will guide all subsequent decisions.
- Choose the Right Tools and Protocols: Select tools based on your objectives and infrastructure. A Cisco-heavy network may favor NetFlow, while a Windows environment will rely on WMI.
- Configure Your Devices: Enable SNMP agents on routers, install cloud monitoring extensions, and ensure devices can communicate with your monitoring system.
- Establish Performance Baselines: You must know what “normal” looks like to spot anomalies. Collect data during typical operations to understand average utilization, latency, and CPU usage. Without baselines, you risk alert fatigue.
- Create Dashboards and Visualizations: Transform raw data into clear, actionable insights. A good dashboard should tell a story at a glance, showing overall health while allowing you to drill down into problem areas.
- Set Up Intelligent Alerting: Define meaningful thresholds (e.g., CPU usage over 90% for five minutes) and configure notifications via email, SMS, or integration with your IT operational tools.
A Practical Guide on How to Monitor and Manage Network Connections
Powerful insights can come from simple, built-in tools:
- On Windows: The
netstatcommand is a powerful ally. Runningnetstat -areveals all active TCP connections, whilenetstat -bshows which programs are using them. For a full walkthrough, see this guide on How to View Network Connections in Every Windows OS. - On Android: The
ConnectivityManagerAPI allows developers to monitor network status in real-time. UsingNetworkRequestandNetworkCallback, apps can adapt intelligently to changing network conditions. Learn more from the Android Developer documentation. - Check Tool Logs: When troubleshooting, logs are digital breadcrumbs. Correlating timestamps across different tools is key. If your dashboard shows a latency spike at the same time your firewall logs unusual traffic, you’ve likely found a strong lead to the root cause.
Implementing Proactive Alerting and Incident Response
Collecting data is just the start; acting on it is what matters.
- Threshold-based alerts are the foundation, triggering notifications when a metric like CPU usage or packet loss exceeds a predefined limit. Platforms like Azure Monitor allow you to easily set metric-based alerts on the data.
- Anomaly detection uses machine learning to identify unusual patterns that might not breach a fixed threshold but still signal trouble, such as a sudden traffic spike at 3 AM.
- Reducing alert fatigue is crucial. Refine your strategy with dynamic baselines and alert correlation to ensure your team receives actionable intelligence, not just noise.
- Integration with IT operational tools automates incident response. Connecting your monitoring system to ticketing and on-call platforms ensures alerts are routed to the right people and trigger predefined workflows.
Strategic Benefits and Best Practices for Success
Mastering how to monitor and manage network connections isn’t just a technical task; it’s a strategy that open ups significant business value. It’s an early warning system that can mean the difference between a minor hiccup and a major catastrophe, giving businesses a competitive edge.
Effective monitoring delivers tangible benefits like early issue detection, improved application performance, and a stronger security posture. It also allows for more efficient IT resource use and data-driven capacity planning, turning guesswork into science.
Opening up Business Value: Performance, Security, and Compliance
The business case for network management is compelling:
- Minimizing Downtime: Proactive monitoring saves money by preventing costly outages.
- Improving User Experience: Fast, reliable network performance is critical for customer and employee satisfaction.
- Identifying Security Threats: Anomaly detection in network traffic can be the first sign of a cyberattack, such as data exfiltration or botnet activity.
- Aiding Compliance: Monitoring provides the detailed logs and audit trails required for regulations like GDPR and HIPAA.
- Optimizing Network Costs: Identify and eliminate inefficient traffic routing and underused resources, especially in the cloud.
- Supporting Business Growth: Ensure your infrastructure can scale reliably as your business expands.
Best Practices for Effective Network Connection Management
Success depends on following proven practices:
- Establish Clear Objectives: Define your primary goals, whether it’s preventing outages, improving performance, or meeting compliance.
- Document Your Network: Maintain up-to-date records of your topology, configurations, and IP addresses. This documentation is invaluable during troubleshooting.
- Implement Proactive Monitoring: Shift from a reactive “break-fix” model to a predictive strategy that catches issues before they fail.
- Train Your Staff: Ensure your team knows how to interpret monitoring data and respond effectively to alerts.
- Perform Routine Audits: Regularly review your monitoring strategy to ensure it keeps pace with your evolving network.
- Eliminate Network Blind Spots: Systematically work to gain comprehensive visibility across your entire infrastructure, including cloud and remote environments.
The Future of Network Management: AI, Hybrid Clouds, and Security
Modern networks are incredibly complex, processing millions of packets each second across hybrid clouds and virtualized environments. Understanding how to monitor and manage network connections today means embracing new technologies like software-defined networks (SDN) and observability—which moves beyond knowing what happened to understanding why.
How to Monitor and Manage Network Connections with AI and Machine Learning
Artificial Intelligence and Machine Learning are revolutionizing network monitoring, as old methods can no longer keep up with modern complexity.
- Predictive Analytics: AI analyzes historical data to predict future failures, allowing you to perform proactive maintenance and prevent outages.
- Automated Root Cause Analysis: When an issue occurs, AI instantly correlates data from across your infrastructure to pinpoint the source, reducing troubleshooting time from hours to minutes.
- Dynamic Performance Baselining: AI learns your network’s unique rhythms, creating intelligent baselines that reduce false positives and understand that normal traffic on a Monday morning is different from a Friday afternoon.
- AI-Driven Alert Correlation: Instead of bombarding your team with dozens of alerts for a single failure, AI groups them into one coherent incident, fighting alert fatigue.
- Deep Packet Analytics (DPA): Advanced AI can analyze the content and context of data packets, enabling automated threat detection that once required manual analysis.
Differentiating Network Monitoring from Network Security Monitoring
Network monitoring (performance-focused) and network security monitoring (threat-focused) are different but complementary disciplines. One ensures the network is fast and available; the other ensures it’s safe.
| Feature | Network Monitoring | Network Security Monitoring |
|---|---|---|
| Primary Goal | Optimize network availability and overall performance | Protect the network from unauthorized access, misuse, and theft |
| Focus | Metrics like latency, bandwidth, uptime, CPU/memory usage, error rates | Malicious patterns, unauthorized access attempts, unusual login attempts, data exfiltration |
| Key Questions Answered | Is the network working? Is it fast enough? Is it available? | Is the network under attack? Is data being stolen? Is there unauthorized access? |
| Typical Tools/Technologies | Network Performance Monitors (NPMs), SNMP, NetFlow, ICMP, WMI, SSH | Security Information and Event Management (SIEM), Intrusion Detection/Prevention Systems (IDS/IPS), Firewalls, Endpoint Detection and Response (EDR) |
These two approaches work together perfectly. A traffic spike flagged by network monitoring could be the first indicator of a data breach investigated by security monitoring. At Concertium, our services integrate both to provide comprehensive protection and performance insights.
Tackling Modern Challenges: Hybrid Environments and Data Volume
Modern IT infrastructure presents significant monitoring challenges:
- Hybrid and Multi-Cloud Environments: Require tools that can create a unified view across on-premises data centers and multiple cloud providers like Azure and AWS.
- Ephemeral Containerized Workloads: Traditional tools struggle to track containers that spin up and disappear in minutes. Monitoring must be adapted for this dynamic nature.
- Massive Data Volumes: Modern networks generate enormous amounts of data. AI and ML are essential to filter the noise and find meaningful signals.
- Security Across Distributed Networks: Maintaining consistent security policies and monitoring coverage across remote offices, mobile devices, and cloud edges is a growing challenge.
Frequently Asked Questions about Network Connection Management
Here are answers to common questions businesses have when learning how to monitor and manage network connections.
No schema found.Conclusion
Mastering how to monitor and manage network connections is no longer optional—it’s a business necessity. Your network is the lifeline of your modern enterprise, and its health directly impacts your revenue and reputation.
We’ve covered the core metrics, essential protocols, and practical steps to build a monitoring system that moves your organization from reactive firefighting to proactive problem-solving. This strategic approach improves security, optimizes resources, and supports business growth.
The future of network management lies in AI-improved observability, which is changing the field with predictive analytics and automated root cause analysis. These intelligent systems are essential for managing the complexity of today’s hybrid cloud and containerized environments.
At Concertium, we have nearly three decades of experience helping businesses steer these challenges. Our Collective Coverage Suite (3CS) with AI-improved observability doesn’t just watch your network; it understands it, turning your infrastructure into a competitive advantage.
Effective monitoring is the foundation for ensuring compliance, protecting against cyber threats, and delivering a seamless user experience. It’s the key to building a resilient and high-performing digital business.
Learn more about our Network Monitoring & Management services