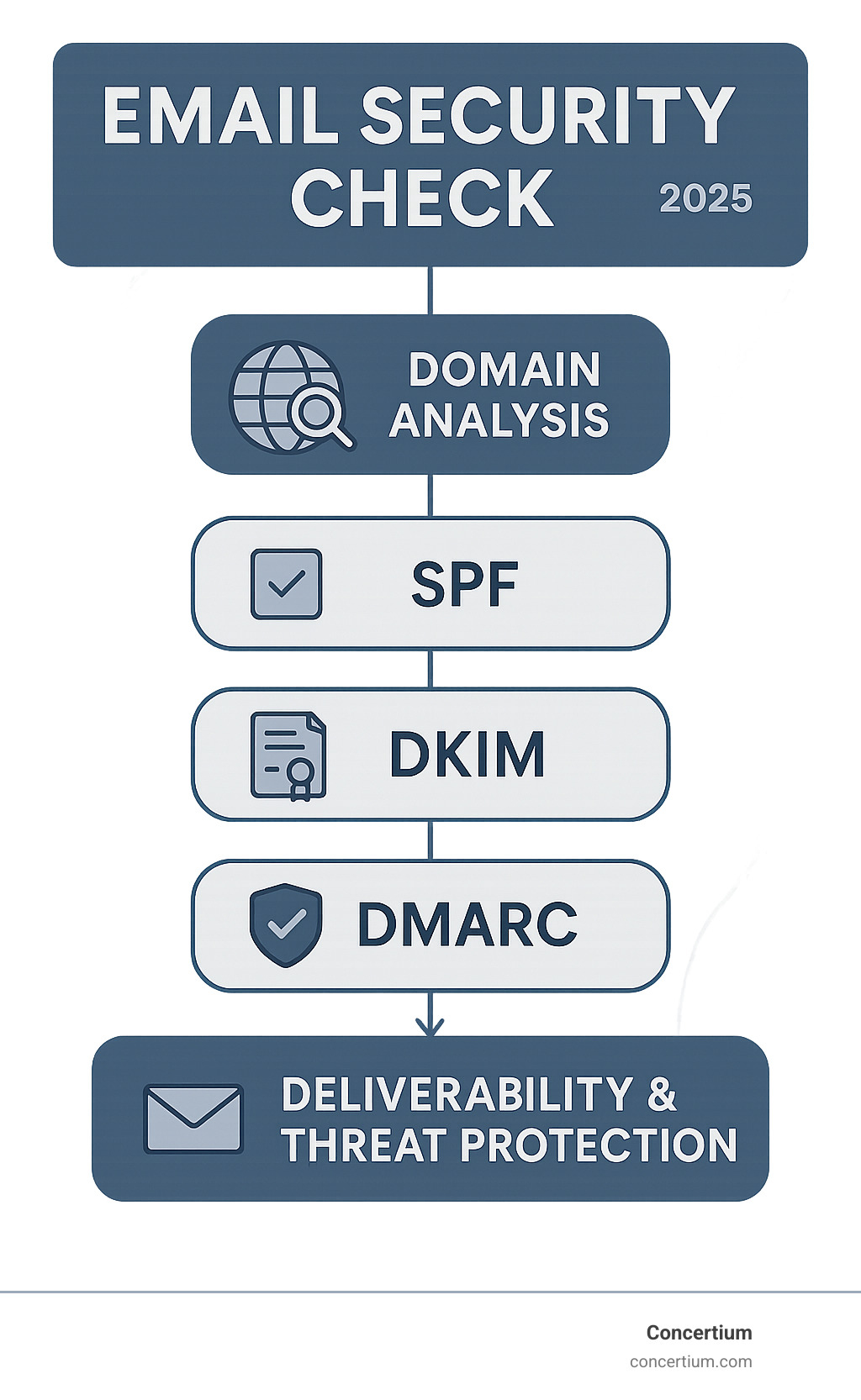
An email security check is a comprehensive analysis of your domain’s email infrastructure that tests authentication protocols (SPF, DKIM, DMARC), DNS configurations, SSL certificates, and blacklist status to prevent spoofing, improve deliverability, and protect against cyber threats.
Key components of an email security check include:
- SPF records – Verify authorized sending servers
- DKIM authentication – Confirm message integrity with digital signatures
- DMARC policies – Define how to handle failed authentication
- DNS health – Ensure proper domain configuration
- Blacklist monitoring – Check against 100+ spam databases
- SSL/TLS certificates – Validate secure connections
- BIMI setup – Display brand logos in inboxes
Every day, your business sends and receives hundreds of emails. But here’s what most business owners don’t realize: each message is either strengthening or weakening your cybersecurity posture.
With 14,985,877,835 pwned accounts found in data breaches and new email security requirements from Google and Yahoo taking effect in February 2024, performing regular email security checks isn’t optional anymore – it’s essential for business survival.
The good news? Modern email security tools can perform over 30 different domain tests in seconds, checking your mail servers against 100+ blacklists while monitoring your DNS configuration continuously. This means you can identify vulnerabilities before they become costly security incidents.
Common email security check vocab:
Why an Email Security Check is Non-Negotiable for Your Business
Your email system is like the front door of your business – and right now, cybercriminals are constantly testing the lock. An email security check isn’t just a nice-to-have anymore; it’s your essential defense against attacks that could devastate your business.
Here’s the reality: email remains the favorite playground for hackers. When your domain lacks proper authentication, you’re basically handing over the keys to your kingdom. Attackers can easily impersonate your business, sending malicious emails that look like they came from you. Your customers receive these fake messages, and suddenly your trusted brand becomes associated with fraud.
The numbers are sobering. A single successful phishing attack costs businesses an average of $4.88 million. But here’s what really keeps business owners up at night – the reputational damage is often permanent. When customers start receiving suspicious emails that appear to come from your domain, trust evaporates faster than morning dew.
At Concertium, we’ve seen this story play out too many times. But we’ve also witnessed the flip side: businesses that perform regular email security checks catch problems before they become disasters. One client avoided a major breach simply because we spotted misconfigured SPF records during a routine check. Another finded their domain had been blacklisted before it tanked their entire email marketing campaign.
The threats are real, but so is the protection. Understanding types of phishing attacks and knowing what is a common indicator of a phishing attempt gives you the knowledge to build stronger defenses.
Protecting Your Brand and Ensuring Deliverability
Every email you send carries your brand’s reputation in its digital envelope. When your messages consistently land in spam folders instead of inboxes, you’re not just missing communication opportunities – you’re training your customers to expect unreliable service from your business.
Email deliverability directly impacts your bottom line. We’ve worked with clients who watched their email open rates plummet by 60% simply because a compromised email account they didn’t know about got their domain blacklisted. Imagine losing more than half your email marketing effectiveness overnight.
Your sender score is the invisible force determining whether email providers trust your domain enough to deliver your messages. Think of it as your email credit score – once it drops, rebuilding takes time and effort. Regular email security checks help you maintain this crucial score by ensuring your mail servers stay off the 100+ public blacklists that email providers monitor.
Customer trust builds slowly but crumbles quickly. When recipients consistently see your emails in their inbox rather than spam, they develop confidence in your brand’s reliability. This trust ripples beyond email – customers who trust your digital communications are more likely to trust your products and services.
The technical foundation matters too. DNS records need proper configuration, SSL certificates must stay current, and authentication protocols require regular verification. These aren’t just IT checkboxes – they’re the building blocks of customer confidence.
Meeting New Sender Requirements from Google & Yahoo
February 1, 2024, marked a turning point in email security. Google and Yahoo didn’t just suggest new requirements – they made them mandatory. If you’re sending bulk emails (more than 5,000 per day), these rules now determine whether your messages reach their destination or disappear into the digital void.
The new bulk sender rules require four critical elements. First, you need properly configured authentication protocols – SPF, DKIM, and DMARC records must work flawlessly. Second, recipients must have one-click unsubscribe options that actually work. Third, your spam complaint rate must stay below 0.3%. Finally, your sending IP needs a valid reverse DNS record.
These changes weren’t designed to complicate your life – they’re about reducing spam and improving security for everyone. However, businesses that ignore these compliance requirements face serious consequences, including complete email blocking by Gmail and Yahoo Mail.
We’ve guided numerous clients through these new requirements, and the pattern is clear: organizations that proactively perform email security checks adapt smoothly, while those that wait until problems arise struggle with deliverability issues that can take months to resolve.
The silver lining? Compliance isn’t just about avoiding penalties – it actually improves your email performance. Properly authenticated emails enjoy higher open rates, better engagement metrics, and stronger customer relationships. When you meet these standards, you’re not just following rules; you’re building a more trustworthy digital presence.
How to Perform a Comprehensive Email Security Check
Running an email security check doesn’t require a computer science degree. In fact, it’s become refreshingly simple thanks to modern scanning tools that do the heavy lifting for you.
The process starts with something you probably do dozens of times a day – typing your domain name. Simply enter the part of your email address that comes after the “@” symbol into a reputable email security scanner. Within seconds, the tool springs into action, running dozens of tests simultaneously across your entire email infrastructure.
What happens next is pretty remarkable. The scanner examines your SPF records to verify which servers are authorized to send emails on your behalf. It checks your DKIM authentication to confirm your messages have proper digital signatures. Your DMARC policies get analyzed to ensure failed authentication attempts are handled correctly.
The tool also digs into your DNS health, making sure your domain configuration is solid. It scans 100+ blacklist databases to verify your domain isn’t flagged anywhere. Your SSL/TLS certificates get validated to confirm secure connections. Even your BIMI setup gets checked to see if your brand logos can display properly in recipient inboxes.
Here’s what makes this process particularly valuable: it uses only publicly available information. No personal data required, no software downloads, no complex installations. You’re essentially seeing your email infrastructure through the same lens that potential attackers would use – which gives you the perfect opportunity to fix vulnerabilities before they become problems.
The results appear as a comprehensive dashboard showing your email security health. Green checkmarks indicate everything’s working properly, while red warnings highlight areas needing attention. Don’t worry if you see some red flags – most domains have at least a few configuration issues that can be resolved quickly.
For businesses serious about staying protected, automated monitoring takes this a step further. Some tools can perform these checks continuously, sending immediate alerts when issues pop up. This proactive approach means you’ll know about problems before they affect your email deliverability or security posture.
This connects directly to cybersecurity threat detection at the email level. The same principles that protect your network – continuous monitoring, rapid response, and layered defenses – apply here too.
Key Protocols Analyzed in an Email Security Check
Understanding what gets examined during an email security check helps you appreciate why each piece matters for your business security. Think of these protocols as different layers of protection, each serving a specific purpose in your email defense strategy.
SPF (Sender Policy Framework) works like a guest list for your domain. It tells receiving mail servers exactly which IP addresses are allowed to send emails on behalf of your organization. When properly configured, SPF prevents attackers from sending emails that appear to come from your business. Without it, anyone can essentially impersonate your domain – and recipients have no way to know the difference.
DKIM (DomainKeys Identified Mail) functions as your email’s digital signature. It uses cryptographic technology to verify that messages haven’t been tampered with during transit. Think of it as a tamper-evident seal on every email you send. When DKIM is working correctly, recipients can be confident that the email they received is exactly what you sent, with no modifications along the way.
DMARC (Domain-based Message Authentication, Reporting & Conformance) serves as the policy enforcer. It tells receiving mail servers what to do when an email fails SPF or DKIM authentication. DMARC can instruct servers to quarantine suspicious emails, reject them entirely, or simply monitor and report on authentication failures. This protocol also provides valuable reporting data about who’s attempting to send emails using your domain.
BIMI (Brand Indicators for Message Identification) is the newest addition to email authentication. When properly configured, BIMI displays your company logo next to your emails in recipients’ inboxes. This not only improves brand visibility but also helps recipients quickly identify legitimate emails from your organization. It’s like having your company letterhead appear automatically on every message.
DNS health encompasses the underlying infrastructure that makes email delivery possible. Your DNS records must be properly configured for all other protocols to function correctly. Issues with DNS can cause email delivery failures, authentication problems, and security vulnerabilities that ripple through your entire email system.
SSL/TLS encryption ensures that communications between mail servers remain secure. When your mail servers have valid SSL certificates, it demonstrates that your organization takes security seriously and provides encrypted connections for all email-related communications.
These protocols work together like a well-coordinated security team. A weakness in any one area can compromise your entire email security posture, which is why thorough email security checks examine all components simultaneously.
Common Vulnerabilities an Email Security Check Can Uncover
Through our years of experience at Concertium, we’ve seen the same vulnerabilities appear repeatedly in email security checks. Recognizing these common issues helps you understand what to look for and why they matter for your business security.
Misconfigured SPF records top our list of frequent problems. Sometimes organizations have outdated SPF records that don’t include all their current email service providers. Other times, the SPF record is too permissive, allowing unauthorized servers to send emails on behalf of the domain. We’ve worked with clients who switched email providers but forgot to update their SPF records, causing their legitimate emails to be marked as spam.
Missing or broken DKIM signatures often occur when organizations change email systems without properly configuring digital signing. This happens frequently after email migrations or when companies start using new marketing automation platforms. Without proper DKIM configuration, your emails lose their digital authenticity verification, making them appear suspicious to receiving servers.
Absent DMARC policies leave your domain vulnerable to spoofing attacks. Many organizations implement SPF and DKIM but never create a DMARC policy to enforce authentication. This is like installing a security system but never turning it on – the protective mechanisms exist but aren’t actively protecting your domain from impersonation.
Open mail relays represent a serious security vulnerability where your mail server can be used to send emails on behalf of other domains. Attackers exploit open relays to send spam, which quickly gets your IP address blacklisted and damages your sender reputation. This can take months to recover from.
Expired SSL certificates on mail servers indicate poor security maintenance practices. Beyond affecting email functionality, expired certificates suggest that an organization may not be maintaining other critical security components properly.
Domain blacklisting can happen for various reasons – compromised email accounts, malware infections, or even being associated with other domains that have been blacklisted. Regular monitoring helps you catch blacklisting early, before it significantly impacts your email deliverability and business communications.
These vulnerabilities don’t exist in isolation – they create opportunities for more serious security incidents. Understanding different types of malware attacks helps you recognize how email vulnerabilities can be exploited for broader security breaches.
The key is addressing these issues proactively. Ransomware defense strategies often start with securing email systems, since email remains the primary delivery mechanism for ransomware attacks. By fixing these common vulnerabilities, you’re not just improving email deliverability – you’re strengthening your entire cybersecurity posture.
Beyond the Basics: Advanced Protection and Breach Prevention
Once you’ve mastered the fundamentals of email security checks, it’s time to think bigger. The threat landscape has evolved far beyond simple spam filters and basic authentication. Today’s attackers use sophisticated techniques that can slip past traditional defenses like a skilled pickpocket in a crowded market.
We’ve seen this evolution at Concertium. Business email compromise attacks now target executives with carefully crafted messages that look completely legitimate. These aren’t the obvious “Nigerian prince” scams of the past – they’re personalized, well-researched attacks that can fool even security-conscious employees.
Modern email security requires a multi-layered approach that combines cutting-edge technology with human intelligence. AI-powered threat prevention systems analyze millions of data points in real-time, looking for subtle patterns that indicate an attack. These systems can detect when an email’s writing style doesn’t match the supposed sender, or when a message contains social engineering techniques designed to create urgency.
Data Loss Prevention (DLP) technology acts like a vigilant security guard for your outbound emails. It scans every message leaving your organization for sensitive information like social security numbers, credit card data, or proprietary business information. When an employee accidentally tries to send confidential data, the system can block the transmission and alert your security team.
Account takeover protection monitors your email accounts for signs of compromise. This includes watching for unusual login locations, abnormal sending patterns, or suspicious changes to email forwarding rules. Think of it as having a security camera that never sleeps, constantly watching for signs that someone unauthorized has gained access to your systems.
The beauty of these advanced protections is how they work together. While your email security check ensures your technical configurations are solid, these additional layers provide defense against threats that bypass traditional security measures. It’s like having both a strong lock on your door and a security system inside your house.
How to Check for Past Email Breaches
Here’s something that might surprise you: with over 14,985,877,835 pwned accounts finded in data breaches, there’s a very good chance that some of your business email addresses have been compromised at some point. The question isn’t whether breaches happen – it’s whether you know about them.
Checking for past breaches should be a regular part of your security routine. Start by searching your business email addresses in reputable breach databases. These services maintain comprehensive records of email addresses found in security incidents, including many breaches that weren’t widely publicized.
When you find that email addresses have been breached, don’t panic – but do act quickly. Force password resets for all affected accounts immediately. Enable multi-factor authentication if it’s not already active. Review recent email activity for signs of unauthorized access, and check email forwarding rules for suspicious modifications.
The findy of breached accounts should trigger a broader security review. If attackers had access to email accounts, they may have gained valuable insights into your business operations, customer relationships, or internal processes. This information could be used for future, more targeted attacks.
Consider implementing breach notification services that alert you when your organization’s email addresses appear in new data breaches. Early notification allows you to respond quickly, potentially minimizing the impact of newly finded compromises.
Password managers become essential tools in this context. They allow you to generate and store strong, unique passwords for all accounts, reducing the risk that a breach in one system will compromise others. When employees use the same password across multiple systems, a single breach can cascade into much larger security incidents.
Our cyber incident response services often begin with email compromise investigations. The patterns we see consistently involve organizations that didn’t realize their email accounts had been breached until much later, when the damage was already extensive.
Proactive Defense with Security Awareness
The most sophisticated email security check and technical controls can’t protect against users who click on malicious links or share sensitive information with attackers. This is why security awareness training represents the human firewall in your cybersecurity strategy.
Effective security awareness goes far beyond those annual training sessions that everyone clicks through without really paying attention. Regular phishing simulations test employees’ ability to recognize and report suspicious emails in real-world scenarios. These simulations should be realistic but not punitive – the goal is education, not embarrassment.
When employees fall for simulated phishing attempts, provide immediate, constructive feedback that helps them recognize similar threats in the future. We’ve found that this “teachable moment” approach is far more effective than punishment-based systems.
Role-based training addresses the specific email security risks faced by different departments. Executives face different threats than accounting staff, and both groups need targeted training that addresses their unique risk profiles. A CEO might be targeted with sophisticated social engineering attacks, while accounting staff might face fake invoice scams.
Creating clear incident reporting procedures makes it easy for employees to report suspicious emails without fear of criticism. Many successful attacks could have been prevented if employees had felt comfortable reporting unusual emails they received. Make reporting simple, fast, and rewarding.
Regular security updates keep staff informed about new threats and attack techniques. The threat landscape changes rapidly, and yesterday’s training may not address today’s risks. Consider monthly security newsletters or brief updates that highlight current threats.
Most importantly, focus on creating a security culture where cybersecurity becomes everyone’s responsibility, not just the IT department’s concern. This cultural shift is essential for long-term security success.
Understanding how to protect yourself from social engineering attacks is particularly important for email security, since most social engineering attacks begin with email contact. The implementation of multi-factor authentication adds another crucial layer of protection.
At Concertium, our managed security awareness services help organizations build comprehensive training programs that address both technical and human factors in email security. The key to successful security awareness is making it relevant and practical – employees need to understand not just what they should do, but why it matters for the organization’s success and their own job security.
Conclusion: Make Email Security a Continuous Process
Think of email security checks like brushing your teeth – you wouldn’t do it once and expect lifelong protection, right? The same principle applies to your business email security. It’s not a “set it and forget it” situation, but rather an ongoing commitment that grows stronger with consistency.
The digital threat landscape never sleeps. While you’re focusing on running your business, cybercriminals are constantly developing new attack methods, finding fresh vulnerabilities, and adapting their tactics. DNS records can mysteriously change during routine server maintenance, SSL certificates expire (often at the worst possible moment), and new security requirements emerge that can affect your email deliverability overnight.
We’ve seen this pattern countless times at Concertium over our nearly 30 years in cybersecurity. The businesses that thrive are those that accept email security checks as a regular business rhythm, not a crisis response. They understand that proactive monitoring catches problems when they’re small and fixable, rather than waiting until customers start complaining about missing emails or, worse, receiving fraudulent messages.
Regular monitoring combined with automated alerts creates the perfect balance. Your systems can continuously scan for issues while you focus on your core business activities. When something needs attention, you’ll know immediately – not weeks later when the damage is already done.
The most effective approach layers multiple security strategies together. Technical controls like SPF, DKIM, and DMARC provide your foundation. Security awareness training ensures your team can recognize and respond to threats appropriately. Regular policy reviews keep your procedures current with evolving business needs and regulatory requirements.
This layered approach isn’t just about preventing attacks – it’s about building customer trust. When your emails consistently arrive in inboxes, when your domain isn’t associated with spam or phishing attempts, and when your customers feel confident communicating with your organization, you’re building a competitive advantage that compounds over time.
The return on investment extends far beyond avoiding security incidents. You’ll see improved email deliverability that boosts your marketing effectiveness, stronger customer relationships built on reliable communication, and better regulatory compliance that protects your business from costly penalties.
At Concertium, we’ve learned that cybersecurity isn’t a destination you reach – it’s a journey you commit to. The organizations that succeed are those that view security as an enabler of business success, not a barrier to overcome.
Ready to take the first step? Take our Email Security Quiz to assess your defenses! Our team is here to help you build a comprehensive email security program that protects your business while keeping communication flowing smoothly.
Don’t wait for a security incident to reveal gaps in your email protection. Start with a thorough email security check today, and make email security a cornerstone of your organization’s success story.