AI Overview:
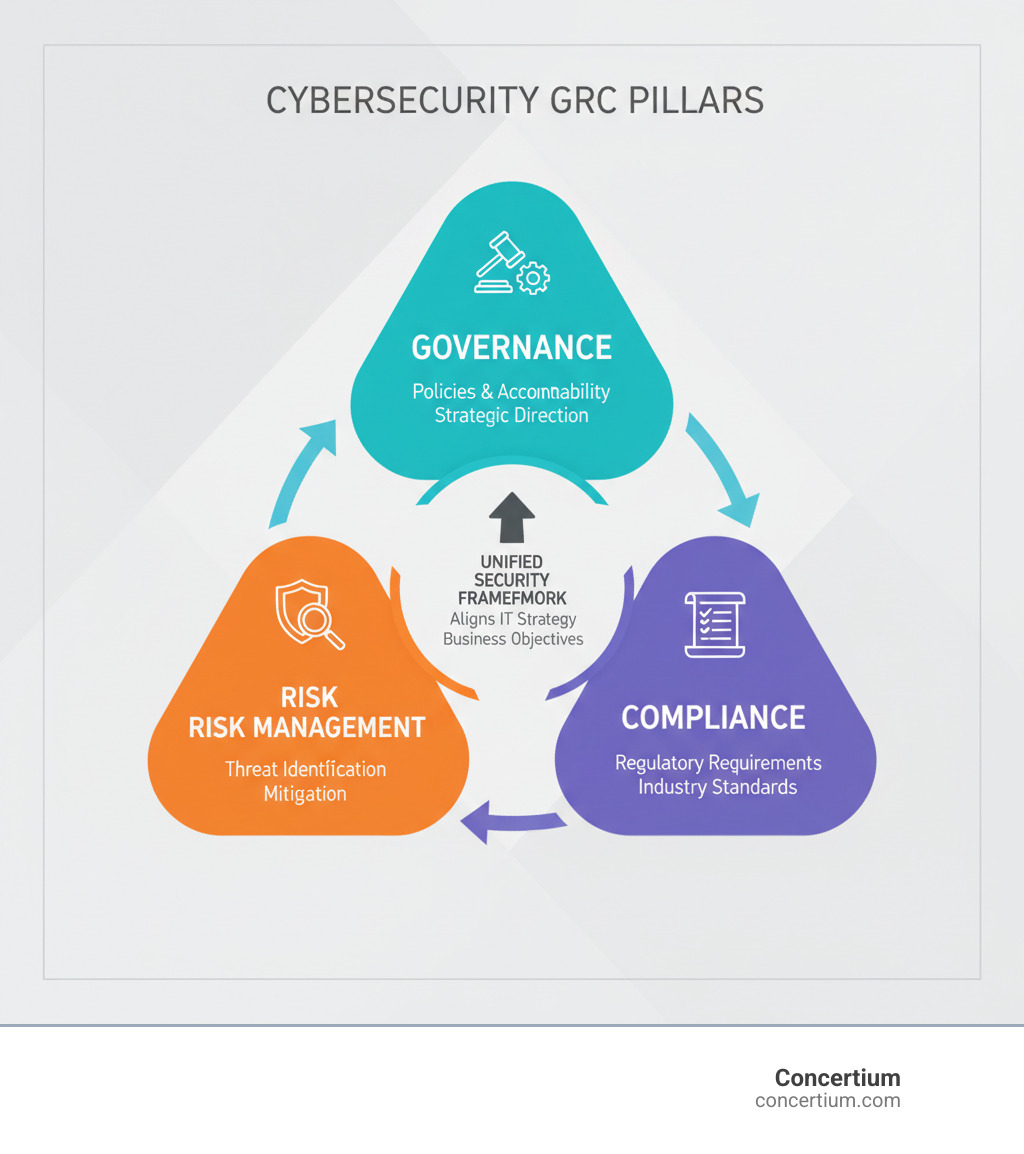
Cybersecurity Governance, Risk, and Compliance (GRC) provides the structured framework businesses need to stay secure, compliant, and efficient in an increasingly threat-filled digital world. It integrates governance (policy and accountability), risk management (identifying and mitigating threats), and compliance (meeting legal and industry standards such as GDPR and HIPAA). The result is a proactive, unified defense system that aligns IT security with business strategy.
Cyber security governance risk and compliance: Best Tools 2025
Why Cybersecurity GRC Is Non-Negotiable for Modern Businesses
Cyber security governance risk and compliance (GRC) is the structured framework that keeps your business secure and operational when cyber threats strike. Here’s a quick overview:
- Governance = Policies, accountability, and strategic direction for cybersecurity
- Risk Management = Identifying, assessing, and mitigating cyber threats
- Compliance = Meeting legal requirements and industry standards (GDPR, HIPAA, etc.)
- Goal = Align IT security with business objectives while reducing cyber risk
As Scott Mitchell from the Open Compliance and Ethics Group puts it: GRC ensures businesses don’t just meet requirements but operate better overall.
The numbers don’t lie: SMBs are prime targets for cyberattacks. Without a unified GRC approach, organizations face disjointed operations and reactive security measures that leave gaps for attackers. GRC combines governance, risk management, and compliance into one coordinated model, helping companies reduce waste, increase efficiency, and make better decisions. The challenge is finding GRC tools that are effective, affordable, and easy to operate.
Cyber security governance risk and compliance helpful reading:
- why is governance risk and compliance important
- cybersecurity risk management frameworks
- enterprise compliance risk management
What is Cybersecurity GRC and Why Does It Matter?
Cyber security governance risk and compliance is the framework that keeps your organization on course amid swirling cyber threats. Think of GRC as the bridge between your IT team and the boardroom, translating complex security challenges into the language of business objectives.
GRC transforms organizations from reactive firefighters into proactive defenders. Instead of scrambling when threats appear, you’re already ahead with data-driven decision-making and an improving cybersecurity posture. This is especially crucial for small and medium businesses, which face sophisticated threats without the luxury of a massive security team. GRC provides the structure to defend effectively.
Properly integrated Governance, Risk, and Compliance (GRC) and IT Governance, Risk, and Compliance don’t add complexity; they reduce it by creating clear paths for decision-making and accountability.
The Core Components of GRC
Let’s break down the three pillars of GRC:
Governance is your organizational backbone, establishing clear corporate policy, resource management, and accountability. It sets the rules of the game: who makes decisions, how policies are managed, and who is responsible. Good governance ensures security efforts are strategic moves supporting business goals.
Risk Management focuses on Cybersecurity Risk Mitigation through systematic risk identification and assessment. Instead of waiting for problems, you actively hunt for them, evaluate their potential impact, and build defenses before they cause damage.
Compliance keeps you aligned with legal and industry expectations. Whether it’s regulatory requirements like GDPR and HIPAA or standards like ISO 27001, compliance ensures you meet necessary benchmarks. Understanding What is Cybersecurity Compliance? helps avoid fines and reputational damage.
Key Benefits of a Unified GRC Approach
When these pillars work together, the benefits are significant:
- Improved decision-making: Decisions are based on complete information, not guesswork.
- Reduced wastage: Eliminates duplicate tools, overlapping audits, and conflicting policies, leading to increased efficiency.
- Improved collaboration: Everyone speaks the same language, from legal and IT to the executive team.
- Proactive risk identification: Your security posture shifts from reactive to preventive, stopping incidents before they happen.
This unified approach, supported by Enterprise Cybersecurity Solutions, is key to building stakeholder trust and making your organization stronger, more resilient, and better positioned for growth.
Key Features to Look for in Effective GRC Tools
Effective GRC tools put these principles into practice. They are the engines that drive your cyber security governance risk and compliance strategy by automating tasks, providing real-time insights, and ensuring consistency. The best platforms act as a central command center, unifying governance, risk, and compliance into a single dashboard for a complete view of your security landscape.
At the heart of any effective GRC tool is a centralized risk register—your single source of truth for all identified risks, their assessments, and mitigation plans. It replaces scattered spreadsheets and centralizes risk data.
Automated compliance monitoring is another game-changer. These tools continuously scan your environment and flag deviations from regulatory requirements automatically.
The policy management lifecycle feature handles the entire journey of your security policies, from creation and approval to distribution and version control.
Real-time dashboards and reporting transform complex security data into visual insights for everyone, from IT teams to C-suite executives.
Audit trail generation is crucial. An automated record of all activities, changes, and approvals saves countless hours during audits.
These features, often powered by GRC Automation Tools, transform GRC from a manual burden into an efficient, data-driven process.
Features for Risk Management
For the “Risk” component of cyber security governance risk and compliance, your tools need to be intelligent.
- Risk assessment workflows guide your team through structured qualitative and quantitative risk assessments, often using industry-standard methodologies.
- Threat intelligence integration connects your GRC platform to external threat feeds, providing an early warning system for emerging threats.
- Vulnerability tracking and management helps you find, prioritize, and track the remediation of vulnerabilities across your infrastructure. This is the core of effective Vulnerability Risk Management.
- Mitigation planning and tracking features help you develop and monitor risk reduction controls, assign owners, and track progress.
- Risk scoring and prioritization algorithms objectively score risks based on likelihood and impact, allowing you to focus resources effectively.
These capabilities are integral to our Cybersecurity Risk Assessment Services, ensuring a clear picture of the threat landscape.
Features for Compliance and Auditing
The compliance features of GRC tools are critical for avoiding regulatory penalties.
- Framework mapping and control libraries: Pre-built templates for frameworks like NIST, ISO 27001, GDPR, and HIPAA map your internal controls to external requirements.
- Automated evidence collection: Streamlines gathering proof for audits, reducing manual effort and making you audit-ready.
- Audit management and workflow: Manages the entire audit process, from planning and evidence submission to findings and remediation tracking.
- Control mapping: Ensures your security controls align with multiple regulatory requirements, demonstrating compliance to auditors.
These tools are fundamental for navigating complex regulations and maintaining our Cybersecurity Compliance Standards, whether for GDPR Compliance in Cybersecurity or HIPAA Compliance: Covered Entities, CES, and Business Associates (BAs).
A Breakdown of cyber security governance risk and compliance Tools by Function
Choosing the right cyber security governance risk and compliance tools involves deciding between all-in-one platforms and specialized point solutions.
- Integrated platforms are ideal for organizations wanting a single, unified system. They reduce vendor management complexity and offer better data correlation across GRC functions.
- Standalone solutions offer best-in-class functionality for specific needs, providing flexibility but requiring more integration work.
The cloud-based versus on-premise decision is also key. Cloud solutions offer scalability and lower upfront costs, while on-premise solutions provide maximum control over data and customization.
Risk & Vulnerability Management Platforms
These platforms are the workhorses of your risk management program, providing continuous monitoring instead of periodic manual assessments. Key features include:
- Asset inventory and management: Maintains a real-time picture of all network assets and their criticality.
- Risk scoring and prioritization: Uses algorithms to help you focus on the vulnerabilities that pose the greatest business risk.
- Threat intelligence integration: Connects internal risk data with external threat feeds to understand which vulnerabilities are being actively exploited.
These capabilities are essential for a thorough Enterprise Security Risk Assessment and support comprehensive Risk Advisory Services in Cybersecurity.
Compliance Automation Tools for cyber security governance risk and compliance
Compliance automation tools transform compliance from a reactive scramble into a proactive, manageable process.
- Automated regulatory updates and mapping: When regulations change, the system automatically flags new requirements and shows their impact on your current controls.
- Compliance gap analysis: Systematically compares your security posture against frameworks like NIST, ISO 27001, or GDPR, highlighting areas for improvement.
- Automated reporting: Generates comprehensive compliance reports with a few clicks, leveraging continuous evidence collection to keep you audit-ready.
This automation is crucial for effective Compliance Risk Analysis and streamlined Compliance and Risk Management processes.
Policy & Governance Management Software
This software ensures your security policies guide daily operations, not just sit in a folder.
- A centralized policy library acts as the single source of truth for all policies, standards, and procedures, with automatic version control.
- Policy distribution and attestation is a streamlined process that notifies staff of updates and tracks acknowledgments.
- Linking policies to controls creates a clear connection between your governance framework and your security implementations, which is invaluable during audits.
Robust Cybersecurity Governance Frameworks depend on these capabilities to maintain consistency.
Incident Management Tools for cyber security governance risk and compliance
When a security incident strikes, incident management tools transform chaotic response into coordinated, efficient action. They are the difference between a contained event and a business-threatening crisis.
| Feature | Manual Incident Response | GRC-Tool-Assisted Incident Response |
|---|---|---|
| Detection | Often reactive, relies on human vigilance or basic alerts | Automated, real-time alerts, integrated SIEM data |
| Response Plan | Ad-hoc, fragmented, difficult to scale | Standardized playbooks, automated workflows |
| Communication | Slow, inconsistent, prone to human error | Automated notifications, centralized communication hub |
| Evidence Collection | Manual, time-consuming, potential for missed data | Automated logging, forensic data collection |
| Tracking & Remediation | Spreadsheets, ad-hoc tasks, difficult oversight | Centralized ticketing, automated task assignment, SLA tracking |
| Reporting | Manual compilation, often delayed | Automated reports, real-time status updates, post-mortem analysis |
| Compliance Impact | Difficult to ensure regulatory reporting deadlines | Automated compliance reporting, audit trail generation |
Key features include incident lifecycle tracking to guide response, response plan automation to execute predefined workflows, and post-mortem analysis to learn from every incident and build organizational resilience.
These tools are fundamental to an effective Cyber Incident Management Framework, advancing your Incident Management Maturity Model, and knowing What to do after a Cybersecurity Breach.
Overcoming GRC Implementation Challenges with the Right Tech
Implementing a comprehensive cyber security governance risk and compliance program can be overwhelming. Common challenges include:
- Limited resources: A shortage of skilled people, time, and budget, especially for SMBs.
- Expertise gap: The specialized knowledge required for GRC is hard to find and expensive.
- Siloed departments: IT, compliance, and risk teams often work with different systems and goals.
- Evolving regulatory landscape: Keeping up with new laws and changing standards is a constant struggle.
- Complexity and resistance to change: GRC’s complexity can cause pushback from employees.
- Clashing priorities: Security initiatives are sometimes seen as a roadblock to business goals.
Here’s the good news: the right technology can transform these challenges into manageable stepping stones. Our Compliance Risk Management Services leverage these solutions to help organizations steer these exact problems.
How Technology Solves Common GRC Problems
Automation is a force multiplier for tight resources. GRC software handles time-consuming tasks like data collection and reporting, freeing your team for strategic work.
Pre-built templates and frameworks bridge the expertise gap. Quality GRC tools include templates for NIST, ISO 27001, GDPR, and HIPAA, so you don’t have to start from scratch.
Centralized platforms break down silos by creating a single source of truth for IT, compliance, and risk teams.
Scalability in cloud-based GRC solutions means the system grows with your business without requiring a complete overhaul.
Continuous monitoring provides real-time visibility into your security and compliance posture, so you can keep pace with evolving threats and regulations.
Technology doesn’t just solve GRC problems—it turns your security program into a competitive advantage.
Frequently Asked Questions about Cybersecurity GRC
Business leaders often have questions about cyber security governance risk and compliance, as it can seem overwhelming. Let’s tackle the most common concerns.
What is the main goal of a cybersecurity GRC program?
The main goal is to align cybersecurity efforts with business objectives. A GRC program creates a structured framework to manage risk, meet legal and regulatory requirements, and protect valuable assets. It's about strengthening your security posture and operating better as a whole organization, not just checking boxes.
How does GRC contribute to an organization's overall resilience?
GRC builds resilience by shifting your organization from a reactive to a proactive security posture. By systematically identifying risks, ensuring compliance, and establishing clear governance, you can make decisive, informed decisions during a crisis. This framework helps you not only survive cyber incidents but also recover more effectively and learn from them. This process of continuous improvement leads to long-term stability and growth.
Can small businesses benefit from GRC tools?
Absolutely. SMBs are prime targets for cybercriminals who know they often lack resources for sophisticated security. GRC tools level the playing field by offering automation, pre-built compliance frameworks, and centralized management that provide enterprise-level visibility without the complexity.
For SMBs, GRC tools are a cost-effective way to implement a structured security program. They allow you to prioritize risks intelligently and maintain compliance without a large team. In today's threat landscape, GRC isn't just beneficial for small businesses—it's non-negotiable.
Conclusion
Cyber security governance risk and compliance is the backbone of business resilience. It’s the unified approach that bridges IT strategy with business goals, allowing you to stop playing defense and start taking control.
The right GRC tools are a force multiplier, changing overwhelming manual processes into streamlined, automated workflows for risk management, compliance, and incident response.
Our experience shows that organizations with a structured GRC approach don’t just survive incidents—they build resilience that becomes a competitive advantage. They make data-driven decisions, allocate resources effectively, and enable the business to grow securely.
The journey to a mature cyber security governance risk and compliance program is worth the effort. It creates a security program that enables your business instead of slowing it down.
Ready to take the next step? We can help you explore what a custom GRC strategy could look like for your organization. Learn more about our IT Governance, Risk, and Compliance services.