Let’s face it – in today’s digital landscape, it’s not a matter of if your organization will face a cyber incident, but when. That’s why having a robust cyber incident response strategy isn’t just nice to have – it’s essential.
Cyber incident response is your organization’s systematic approach to managing and mitigating cybersecurity threats. Think of it as your playbook for when things go wrong. It brings together the people, processes, and technologies needed to detect, analyze, contain, eradicate, and recover from security incidents that threaten your systems or data.
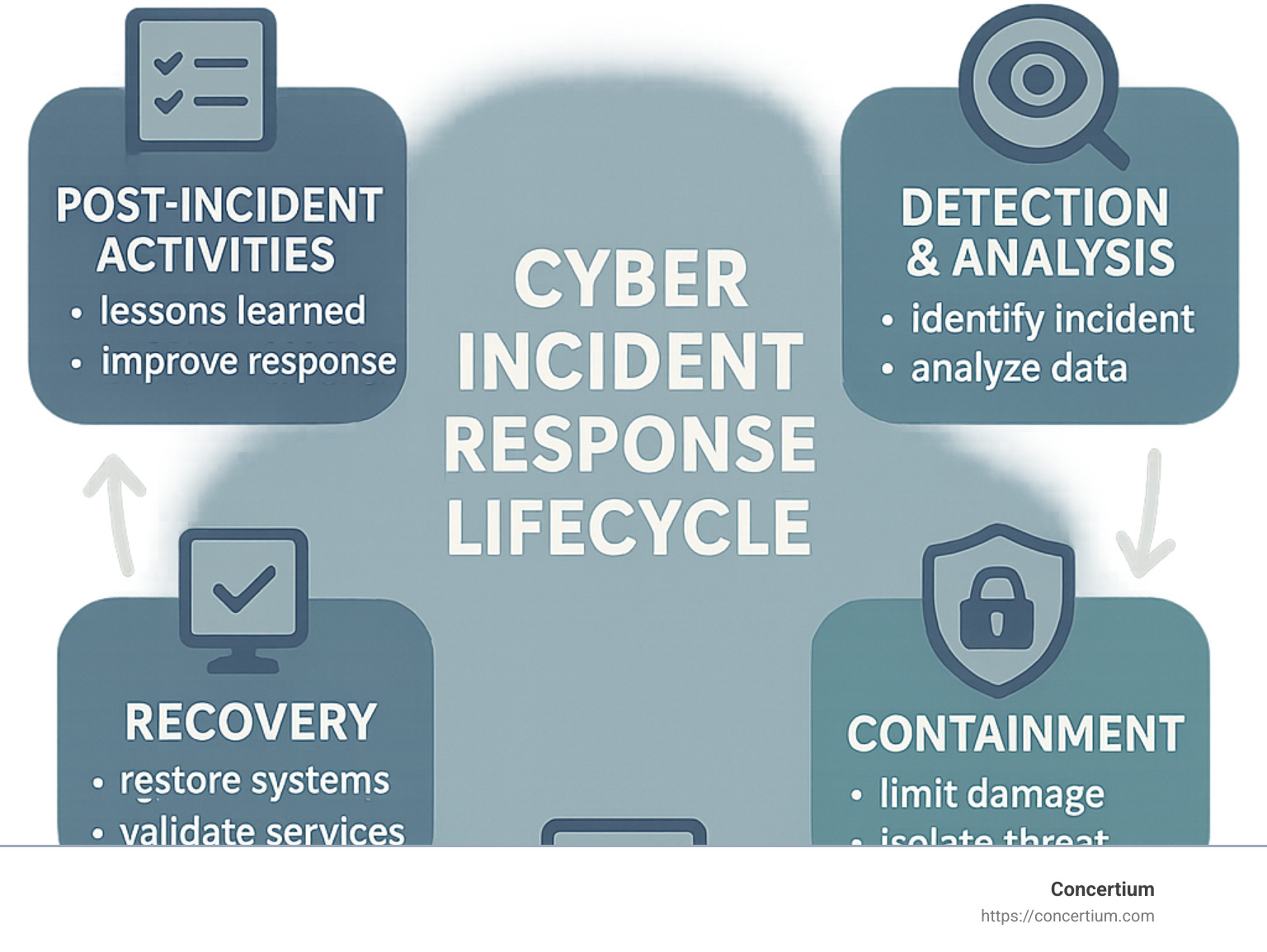
The heart of effective cyber incident response lies in six key elements that work together as a continuous cycle. It starts with preparation – developing plans and capabilities before incidents occur. When threats emerge, detection and analysis kick in to identify and investigate potential security events. Once identified, containment strategies limit damage by isolating affected systems. The eradication phase removes the threat entirely, followed by recovery efforts to restore normal operations. Finally, post-incident activities help you learn and improve for next time.
The numbers tell a sobering story. In 2023 alone, the United States experienced over 3,200 data breaches – nearly double the 1,800 reported in 2022. These breaches affected more than 350 million people, leaving organizations scrambling to respond.
“By investing in response preparedness, organizations can help reduce the costly, disruptive effects of data breaches, support operational continuity and help preserve their relationships with customers, partners and other key stakeholders.” – IBM Cost of a Data Breach Report
For mid-sized businesses, the financial case for preparedness is compelling. IBM’s research reveals that organizations with an incident response team and formal plans in place save nearly half a million dollars ($473,706) on average when dealing with breaches. That’s a significant return on investment for preparedness.
Despite these clear benefits, the preparedness gap remains alarming. About 77% of organizations lack a consistent, formal incident response plan across their operations. Even more concerning, among those with plans, only 32% describe their initiatives as “mature.”
Perfect security simply doesn’t exist. What truly separates resilient organizations from vulnerable ones isn’t whether they’ll face an incident – it’s how effectively they respond when the inevitable happens.
Cyber Incident Response 101: Definition, Importance & Incident Types
When your organization’s security defenses are breached—and let’s be honest, it’s usually a matter of “when” not “if”—what happens next can make all the difference. That’s wherecyber incident response comes in, serving as your organization’s immune system against digital threats.
Cyber Incident Response: A Working Definition
Think of cyber incident response as your organization’s emergency plan when cybersecurity goes sideways. It’s the coordinated approach that kicks in after detecting a security breach, helping you contain the damage, kick out the intruders, and get back to business as quickly as possible.
NIST defines a cybersecurity incident quite simply as “an occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits.”
When done right, effective incident response helps you:
Protect your critical assets and sensitive data, minimize business downtime, contain incidents before they spread, meet those pesky regulatory requirements, preserve evidence if legal issues arise, and—perhaps most importantly—learn how to prevent similar headaches in the future.
As many security professionals will tell you, cyber incident response isn’t about perfect prevention—it’s about building resilience through continuous learning and improvement. It’s like developing antibodies after getting sick—your security gets stronger with each challenge it faces.
Cyber Incident Response vs. Disaster Recovery
While these terms often get tossed around interchangeably at executive meetings, they’re actually complementary but distinct aspects of keeping your business running:
Cyber incident response focuses on the immediate security breach—like when someone breaks into your digital house. It’s tactical, urgent, and security-focused, with specialized teams working to identify how attackers got in and remove them.
Disaster recovery, meanwhile, is more about rebuilding after the storm—whether that storm was a cyber attack, a flood, or a power outage. It centers on restoring your IT systems with those critical RTO (Recovery Time Objective) and RPO (Recovery Point Objective) metrics guiding the way.
As JJ Cranford wisely notes, “Because an incident response plan is not solely a technical matter, the IR plan must be designed to align with an organization’s priorities and its level of acceptable risk.”
Today’s organizations face an evolving lineup of threats that keep security teams up at night:
Ransomware has become the digital equivalent of a hostage situation, now accounting for 20% of network attacks. Attackers encrypt your data and demand payment for the keys.
Phishing and social engineering remain frustratingly effective, using our human trust and habits against us to steal credentials or plant malware.
Insider threats remind us that sometimes the call is coming from inside the house—whether from a disgruntled employee or someone who simply made a mistake.
DDoS attacks can overwhelm your systems with traffic, causing outages and disruptions that affect customer experience and your bottom line.
Supply chain attacks have grown increasingly sophisticated, allowing attackers to compromise your systems through trusted vendors—as we all learned from the SolarWinds incident.
The reality is sobering: 77% of organizations lack a formal incident response plan that’s consistently applied across their operations. Only 32% of those with plans describe their programs as “mature.” This gap leaves businesses unnecessarily vulnerable when incidents inevitably occur.
For deeper insights into managing these threats, check out our Comprehensive Guide to Managing Incident Types and learn How to Respond to a Data Security Incident.
The 6 Essential Cyber Incident Response Steps
When chaos erupts during a security breach, having a clear roadmap makes all the difference. That’s exactly what a structured cyber incident response process provides – a reliable path through uncertainty. While the industry has two dominant frameworks (NIST and SANS), they both cover the same critical phases, just with slightly different terminology.
1. Preparation
Think of preparation as building your security foundation before the storm hits. This crucial first step is where smart organizations invest significant time and resources.
During preparation, you’ll develop formal incident response plans and playbooks that serve as your team’s guide during high-stress situations. You’ll establish clear team structures with defined roles so everyone knows their responsibilities when minutes count. This phase also includes implementing robust detection tools, conducting regular training exercises, and creating communication templates for various scenarios.
As security experts often warn: “Not having recorded evidence of a Cyber Security Incident Response Plan will signal to auditors that you aren’t taking the prospect of a data breach seriously.” Preparation isn’t just good practice – it’s essential for compliance and organizational resilience.
2. Detection & Analysis
You can’t respond to what you don’t know about. The detection phase is your organization’s security radar system, constantly scanning for potential threats.
This phase involves actively monitoring alerts from your security tools like SIEMs and EDRs, analyzing system logs for suspicious patterns, and investigating user reports of unusual activity. The real skill lies in distinguishing genuine threats from false alarms – a balance of technology and human expertise.
Security professionals consistently emphasize that “Incident prioritization is the most important decision point in the process.” Not all incidents are created equal, and proper analysis helps you direct resources where they’ll have the greatest impact. Documentation begins here too, establishing a timeline that could prove invaluable for both technical response and potential legal proceedings.
3. Containment
When you’ve confirmed a security incident, your priority shifts to stopping the bleeding. Containment is about building a firewall around the problem before it spreads.
This phase typically involves quick actions like isolating affected systems from your network, blocking communication with malicious IP addresses, and disabling compromised user accounts. Think of containment in two timeframes: short-term tactics to halt immediate damage, and longer-term strategies that provide sustainable protection while you investigate further.
A critical but often overlooked aspect of containment is preserving forensic evidence. The steps you take now will determine what information you have available later for both improving your defenses and potential legal proceedings.
4. Eradication
Containment stops the spread, but eradication eliminates the threat entirely. This is where you roll up your sleeves and remove every trace of the attacker from your environment.
During eradication, your team will identify and eliminate root causes – not just symptoms. This includes removing all malware and malicious code, patching the vulnerabilities that were exploited, resetting any compromised credentials, and hardening your systems against similar future attacks.
Thoroughness is essential here. Missing even a small backdoor or persistent access point can mean doing this all over again in the near future.
5. Recovery
With the threat eliminated, it’s time to restore normal operations – but cautiously. Recovery isn’t about rushing back online; it’s about returning to business safely.
This phase includes validating that systems are truly clean before restoration, carefully restoring data from verified clean backups, implementing additional security controls based on what you’ve learned, and gradually returning systems to production while monitoring closely for any signs of remaining threats.
As experienced incident responders often caution: “Verify that backups are uncompromised before system restoration.” The last thing you want is to reintroduce the very threat you just worked so hard to remove.
6. Post-Incident Activities
The incident may be over, but your work isn’t. The final phase – often overlooked but incredibly valuable – transforms a painful experience into organizational wisdom.
Post-incident activities include conducting a thorough analysis of what happened, documenting the complete incident timeline and your response actions, identifying specific improvements to security controls and processes, updating your incident response plans based on lessons learned, and sharing relevant threat intelligence with trusted partners.
This phase creates a powerful feedback loop that strengthens your security posture over time. Each incident, properly analyzed, makes you more resilient against the next one.
For organizations looking to implement these processes effectively, we recommend exploring our detailed guide on the NIST Incident Response Process. The structured approach outlined there can help transform these principles into practical, actionable steps for your organization.
| Framework Comparison | NIST SP 800-61 | SANS |
|---|---|---|
| Phase 1 | Preparation | Preparation |
| Phase 2 | Detection & Analysis | Identification |
| Phase 3 | Containment | Containment |
| Phase 4 | Eradication | Eradication |
| Phase 5 | Recovery | Recovery |
| Phase 6 | Post-Incident Activity | Lessons Learned |
Building a Resilient Incident Response Plan & Team
When a cyber incident strikes, you don’t want to be caught scrambling. That’s why building both a solid cyber incident response plan and assembling the right team are absolutely crucial for your organization’s security posture.
Think of your incident response plan as your emergency playbook – it’s what keeps everyone calm and focused when alarms are blaring. And your response team? They’re your cyber firefighters, ready to jump into action at a moment’s notice.
Drafting the IRP
Creating an effective incident response plan doesn’t have to be overwhelming. Start with the basics and build from there:
Begin by clearly defining what counts as an “incident” for your organization. Is it any suspicious login attempt, or only confirmed breaches? Setting this scope helps prevent both overreaction and dangerous complacency.
Next, take inventory of what really matters – your critical systems, sensitive data, and their business importance. You can’t protect what you don’t know you have!
The heart of your plan should include detailed response procedures – essentially step-by-step playbooks for common incidents like ransomware attacks or data breaches. These playbooks save precious time when minutes count.
Communication flows are equally vital. Who needs to know what, and when? Your plan should clearly map out when to notify executives, customers, regulators, or law enforcement. Having pre-drafted communication templates can be a lifesaver during a crisis.
As one security expert puts it: “Having incident response plans that are customized to an organization’s environment is key to reducing the time to respond, remediate and recover.”
Don’t forget to include an escalation matrix showing exactly who has decision-making authority at each stage. This prevents the all-too-common paralysis that happens when nobody feels empowered to make tough calls during an incident.
Staffing the Team
A well-rounded Cyber Security Incident Response Team (CSIRT) brings together diverse skills and perspectives. At its core, you’ll need an incident commander who keeps the big picture in view while coordinating all response activities. This person needs both technical knowledge and leadership skills to thrive under pressure.
Your security analysts will be on the front lines, investigating alerts and performing technical analysis to understand what’s happening. Meanwhile, forensic specialists dig deeper, collecting evidence to determine how attackers got in and what they touched.
Don’t underestimate the importance of a skilled communications lead. This person manages both internal updates and external messaging – a critical role when reputation and trust are on the line.
Every effective team needs an executive sponsor who can provide authority and resources when needed. Legal counsel should also be readily available to steer the increasingly complex regulatory landscape around breaches.
Your team structure might follow one of three common models. A centralized approach puts one team in charge of all incidents across the organization – great for consistency but potentially overwhelmed during major events. The distributed model spreads responsibility across business units, offering faster local response but risking inconsistency. Many organizations find success with a coordinated approach, where a core team guides the overall response while working with distributed technical resources.
Regular practice makes perfect. Schedule tabletop exercises at least quarterly to test both your plan and your team’s readiness. These simulations reveal gaps in your procedures and ensure everyone understands their roles before a real crisis hits.
Building response capability is a journey, not a destination. Start where you are, improve incrementally, and don’t wait for perfection before implementing basic response protocols.
For more comprehensive guidance on building your response capabilities, explore our Cyber Incident Management Framework and Incident Response Frameworks resources.
Tools, Automation & AI in Cyber Incident Response
The modern approach to cyber incident response has evolved far beyond manual processes. Today’s security teams rely on powerful technologies that dramatically improve their ability to detect, analyze, and respond to threats quickly and effectively.
Selecting and Integrating Technologies
The security technology landscape can feel overwhelming, but several core tools have proven essential for robust cyber incident response:
Think of Security Information and Event Management (SIEM) systems as your security command center. They collect logs from across your network, correlate events, and help identify patterns that might indicate a breach. Without good log management, you’re essentially flying blind during an incident.
Security Orchestration, Automation, and Response (SOAR) platforms take things a step further by automating repetitive response tasks. When every minute counts during a breach, having pre-programmed playbooks that execute automatically can make all the difference.
For protecting endpoints—like laptops, servers, and mobile devices—Endpoint Detection and Response (EDR) tools are your front-line defense. They monitor for suspicious activity and give responders the power to isolate compromised devices before an attack spreads.
The newer Extended Detection and Response (XDR) solutions break down silos between security tools, giving teams unified visibility across endpoints, networks, cloud environments, and more. This holistic view helps connect the dots during complex attacks.
Insider threats remain a persistent challenge, which is why User and Entity Behavior Analytics (UEBA) has become invaluable. These tools learn what “normal” looks like for each user and alert when someone’s behavior suddenly changes—like accessing sensitive data at 3 AM or downloading unusually large files.
The most effective security programs don’t treat these tools as standalone solutions but integrate them into a cohesive ecosystem. This integration enables enrichment of security data with threat intelligence and creates a multiplier effect on your detection and response capabilities.
As research has consistently shown, these investments pay off. Organizations using AI-powered security solutions save an average of USD 2.2 million in breach costs compared to those relying on traditional approaches. That’s a compelling return on investment by any standard.
The Future: Hyper-Automation
We’re entering an era of hyper-automation in cyber incident response, where artificial intelligence and machine learning are changing what’s possible.
AI-powered anomaly detection is like having thousands of security analysts working 24/7, spotting subtle patterns that would be impossible for humans to detect. These systems can identify the faintest signals of compromise amid the noise of normal network traffic.
The most exciting development may be predictive analytics, where machine learning models analyze historical attack data and current threat intelligence to forecast where attackers might strike next. This shift from reactive to proactive security represents a fundamental change in how we approach defense.
Alert fatigue has long plagued security teams, but smart automation is addressing this challenge. Advanced systems now automatically prioritize alerts based on their potential business impact, ensuring analysts focus on what matters most.
The intelligence of SOAR platforms continues to advance as well. Rather than following rigid playbooks, these systems can now dynamically adjust response workflows based on the specific characteristics of an incident, much like an experienced responder would.
Even threat intelligence processing is being revolutionized. Natural language processing allows systems to read and understand threat reports the way humans do, automatically extracting actionable information and applying it to your security controls.
At Concertium, we’ve acceptd these advancements in our Incident Response Cybersecurity services. Our AI-improved observability capabilities help spot threats earlier, while our automated eradication tools ensure rapid response when minutes matter.
The future belongs to organizations that accept these technologies—not to replace human expertise, but to amplify it. By combining human judgment with machine speed and scale, we’re creating security operations that are more resilient than ever before.
Post-Incident Improvement, Compliance & Metrics
The dust has settled after a security incident—now what? This crucial phase is where the real growth happens in your cyber incident response program. It’s your chance to turn a negative experience into a positive change for your organization’s security posture.
Lessons Learned Process
The post-incident review isn’t just a box to check—it’s where the magic happens. Start by mapping out the complete incident timeline from first detection to final resolution. This chronology helps everyone visualize what actually happened versus what should have happened.
Root cause analysis is where you dig beneath the surface symptoms to uncover the true vulnerabilities that allowed the incident to occur. Was it a missed patch? An overlooked configuration error? A training gap? The goal isn’t to assign blame but to identify fixable problems.
“Regular post-mortem meetings with all stakeholders can help improve overall security and incident handling procedures,” note security professionals. These meetings should feel like a safe space where team members can honestly evaluate what worked well and what fell short during the response.
The output should be a concrete, prioritized roadmap of specific improvements—not vague recommendations that never get implemented. Each action item needs an owner and a deadline to ensure accountability.
Compliance Considerations
Security incidents often trigger a cascade of regulatory obligations that can feel overwhelming if you’re not prepared. For European operations, GDPR gives you just 72 hours to notify authorities of certain breaches. California residents affected by a breach? CCPA/CPRA has specific notification requirements you’ll need to follow. Public companies must now disclose material cybersecurity incidents under new SEC Rules, while industries like healthcare (HIPAA) and payment processing (PCI DSS) have their own specialized requirements.
Evidence preservation becomes critical during this phase. Think of it like a crime scene—you need to maintain detailed incident logs, preserve forensic images, and document a clear chain of custody for all evidence. This attention to detail not only helps with regulatory compliance but can prove invaluable if legal proceedings arise later.
Metrics and Program Maturity
You can’t improve what you don’t measure. Smart incident response teams track key metrics that reveal the health of their program:
Mean Time to Detect (MTTD) shows how quickly your team identifies incidents—are they catching threats in minutes or months? Mean Time to Respond (MTTR) measures how rapidly your team springs into action once something suspicious is detected. Mean Time to Contain (MTTC) reflects your ability to isolate and stop threats from spreading, while Mean Time to Recover (MTTR) captures how quickly you can restore normal operations.
Beyond response times, tracking your Incident Rate by type and severity helps identify patterns and recurring issues. Understanding the Cost Per Incident—both direct expenses and hidden costs like productivity loss—helps justify security investments to leadership.
These metrics feed into broader assessments using frameworks like the NIST Cybersecurity Framework or Capability Maturity Model, giving you a roadmap for growth.
For comprehensive guidance on what to do after an incident, explore our resources on What to Do After a Cybersecurity Breach? and Post-Breach Services.
Continuous Program Maturity
Building a mature incident response capability is like training for a marathon—it’s an ongoing journey, not a one-time event. Update your incident response plan at least annually, but don’t wait for the calendar if there are significant changes to your IT environment, business operations, or the threat landscape.
Quarterly drills keep your team sharp—mix up the scenarios to test different muscles in your response capabilities. Today’s ransomware simulation might be tomorrow’s insider threat exercise.
The most mature organizations don’t just wait for incidents to happen—they actively hunt for threats that might have slipped past automated defenses. They also bring in outside experts periodically for fresh perspectives on their incident response program.
Industry engagement through information-sharing communities helps you learn from others’ mistakes instead of making them yourself. As one CISO put it, “The best incident response teams are constantly comparing notes with their peers.”
As your program matures, you’ll find yourself shifting from purely reactive incident response to proactive threat management—building resilience that helps your organization bend without breaking when faced with evolving cyber threats.
Frequently Asked Questions about Cyber Incident Response
How often should we review our incident response plan?
Your cyber incident response plan isn’t a “set it and forget it” document. At minimum, you should dust it off and give it a thorough review once a year. But in today’s rapidly evolving threat landscape, that’s really just the baseline.
Think of your plan as a living document that needs to grow and adapt alongside your organization. When your company undergoes significant structural changes, implements new technologies, or retires legacy systems, that’s your cue to revisit the plan. The same goes for shifts in regulatory requirements or changes in the threat landscape that might affect your industry.
Had a security incident recently? That’s perhaps the most compelling reason to review your plan while lessons are still fresh. As the saying goes, never waste a good crisis – use it as a learning opportunity to strengthen your defenses.
For organizations in heavily regulated industries dealing with GDPR, CCPA, SEC rules, or ISO 27001 audits, quarterly reviews might make more sense. Each review should include practical checks like validating contact information (people change roles!), verifying your tools still work as expected, and making sure your procedures remain relevant to current threats.
Which external partners should be on retainer?
Even the most capable in-house security teams sometimes need reinforcements. Having the right external partners on speed dial can make all the difference when you’re in the thick of an incident.
Digital forensics experts bring specialized skills that most organizations don’t maintain internally. They know exactly how to investigate complex breaches while preserving evidence that might be needed later.
Legal counsel with cybersecurity expertise is invaluable when navigating the maze of regulatory requirements that follow a breach. They’ll help you understand your obligations and minimize legal exposure.
Public relations specialists who understand cyber crises can help craft messaging that protects your reputation without creating additional legal issues. Research shows organizations that fumble their communications, allowing breaches to linger in headlines, often suffer greater reputational damage.
Incident response service providers can augment your internal team during major incidents, bringing extra hands and specialized expertise exactly when you need them most.
Ransomware negotiation specialists might seem like an unusual addition, but if you ever face that particular nightmare scenario, you’ll be glad to have experts who understand the dynamics of these situations.
When selecting partners, look for those who understand your industry and its regulatory environment. Establish clear engagement procedures before you need them, and ensure they can respond within your required timeframes. The middle of a crisis is not the time to be negotiating contracts or explaining your business.
How do we measure incident response effectiveness?
You can’t improve what you don’t measure, and cyber incident response is no exception. Effective measurement combines hard numbers with more nuanced qualitative assessments.
On the quantitative side, time-based metrics tell an important story. How long does it take to detect incidents (MTTD)? To respond (MTTR)? To contain the threat (MTTC)? And finally, to fully recover (MTTR)? Tracking these metrics over time reveals whether your program is becoming more efficient.
Volume metrics provide additional insights. Track the number and types of incidents you face, noting which ones are caught by automated tools versus human reporting. This helps you understand where to focus your detection efforts. Also track your containment success rate – how often do you stop threats before data is exfiltrated?
Cost metrics complete the quantitative picture. Calculate both direct costs (response, recovery, legal) and indirect costs (business disruption, reputation damage) per incident. This helps justify security investments by demonstrating cost avoidance through early detection and rapid response.
Numbers only tell part of the story, though. Complement them with structured post-incident reviews that dig into what worked well and what didn’t during each significant incident. Tabletop exercise results provide similar insights in a controlled environment. Gather feedback from business stakeholders about their experience during incidents, and periodically assess your program’s maturity against established frameworks like NIST CSF or ISO 27001.
It’s worth noting that ambition and reality often diverge when it comes to recovery capabilities. Research shows that while 98% of organizations target a one-day Recovery Time Objective (RTO), only 2% actually achieve it. Realistic metrics and continuous improvement efforts help close this gap over time.
At Concertium, we help organizations develop measurement frameworks that provide meaningful insights without creating unnecessary administrative burden. The right metrics should drive improvement, not just generate reports.
Conclusion
When it comes down to it, cyber incident response isn’t just another IT checkbox—it’s become essential to business survival. Throughout this guide, we’ve seen how the ability to quickly detect, contain, and bounce back from security incidents can be the difference between a minor hiccup and a full-blown disaster that makes headlines.
Think about what we’ve covered together:
First, preparation truly is everything. The organizations that weather cyber storms best are those that invested time in planning, running drills, and equipping their teams before trouble ever knocked on their door. It’s like having a fire evacuation plan—you hope you’ll never need it, but you’d never want to be without one.
Second, following a structured process matters enormously. Whether you prefer NIST or SANS frameworks, having a clear roadmap for your response means you won’t be making critical decisions during the chaos of an active incident.
Third, your people make all the difference. Even with the best technology in the world, you need a skilled incident response team with clearly defined roles. Everyone needs to know exactly what they’re responsible for when seconds count.
Fourth, smart technology amplifies your capabilities. Today’s advanced tools and automation can dramatically improve how quickly you spot threats and how efficiently you respond to them. The research showing $2.2 million in potential savings from AI-powered security solutions speaks volumes.
Finally, learning never stops. Each incident, whether major or minor, offers valuable lessons to strengthen your security posture. The organizations that treat incidents as learning opportunities consistently build greater resilience over time.
Here at Concertium, we’ve been in the trenches with organizations just like yours for nearly 30 years. We’ve seen how building a mature incident response capability is a journey, not a destination. Our Collective Coverage Suite (3CS) provides the enterprise-grade protection you need with AI-improved visibility and automated threat elimination that helps you respond decisively when every minute counts.
The reality we all face is straightforward: cyber incidents will happen. But their impact on your organization isn’t predetermined. By implementing the approaches we’ve outlined throughout this guide, you can significantly reduce the financial hit, operational disruption, and reputation damage that security breaches often cause.
Want to learn more about strengthening your incident response capabilities? Explore our Incident Response Frameworks and find how our 3CS approach can lift your security resilience to new heights.
The real question isn’t if you’ll face a cyber incident—it’s whether you’ll be ready when it happens. And with the right preparation, you absolutely can be.