Automated threat hunting is the proactive, AI-powered process of searching for cyber threats that have evaded traditional security defenses. It uses machine learning and advanced analytics to detect malicious activity at machine speed.
Key Benefits of Automated Threat Hunting:
- Speed: Reduces Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by up to 50%.
- Efficiency: Eliminates up to 99% of alert noise and false positives.
- Scale: Enables 24/7 continuous monitoring without human fatigue.
- Cost: Significantly reduces the average data breach cost (currently $4.25M).
- Coverage: Provides comprehensive threat detection across entire attack surfaces.
The cybersecurity landscape has changed. Sophisticated attackers use automation to breach networks and remain undetected for months. Meanwhile, security teams struggle with overwhelming alert volumes, analyst burnout, and a growing skills gap.
Traditional security measures like firewalls and antivirus software are no longer sufficient against today’s advanced persistent threats (APTs) and zero-day exploits. Organizations need a proactive approach that assumes threats are already present.
As one Chief Information Security Officer noted: “We had to advance our monitoring and response by taking a more proactive approach to security operations.”
This shift from reactive to proactive defense is where automated threat hunting becomes a game-changer. By combining human expertise with AI-powered automation, organizations can level the playing field against attackers who use their own sophisticated automated tools.
Key automated threat hunting vocabulary:
What is Automated Threat Hunting and Why is it Essential?
The cybersecurity world has shifted. The question isn’t if your network will be breached, but when. This reality has pushed security teams to abandon reactive approaches in favor of proactive automated threat hunting.
Think of automated threat hunting as a digital bloodhound that never sleeps. Instead of waiting for alarms, this technology actively searches your network for hidden threats that have slipped past initial defenses. We’re talking about sophisticated attackers who know how to stay invisible while they quietly collect data and credentials.
This matters because today’s attackers use automation to their advantage, lurking in networks for months—a period known as “dwell time.” The longer they stay hidden, the more damage they cause. The average data breach now costs organizations $4.25 million. Encouragingly, automated threat hunting can cut detection and response times by up to 50%, dramatically reducing potential damage. To fight automated attackers, you need automated defenders.
Our Cybersecurity Threat Detection services are built around this proactive philosophy.
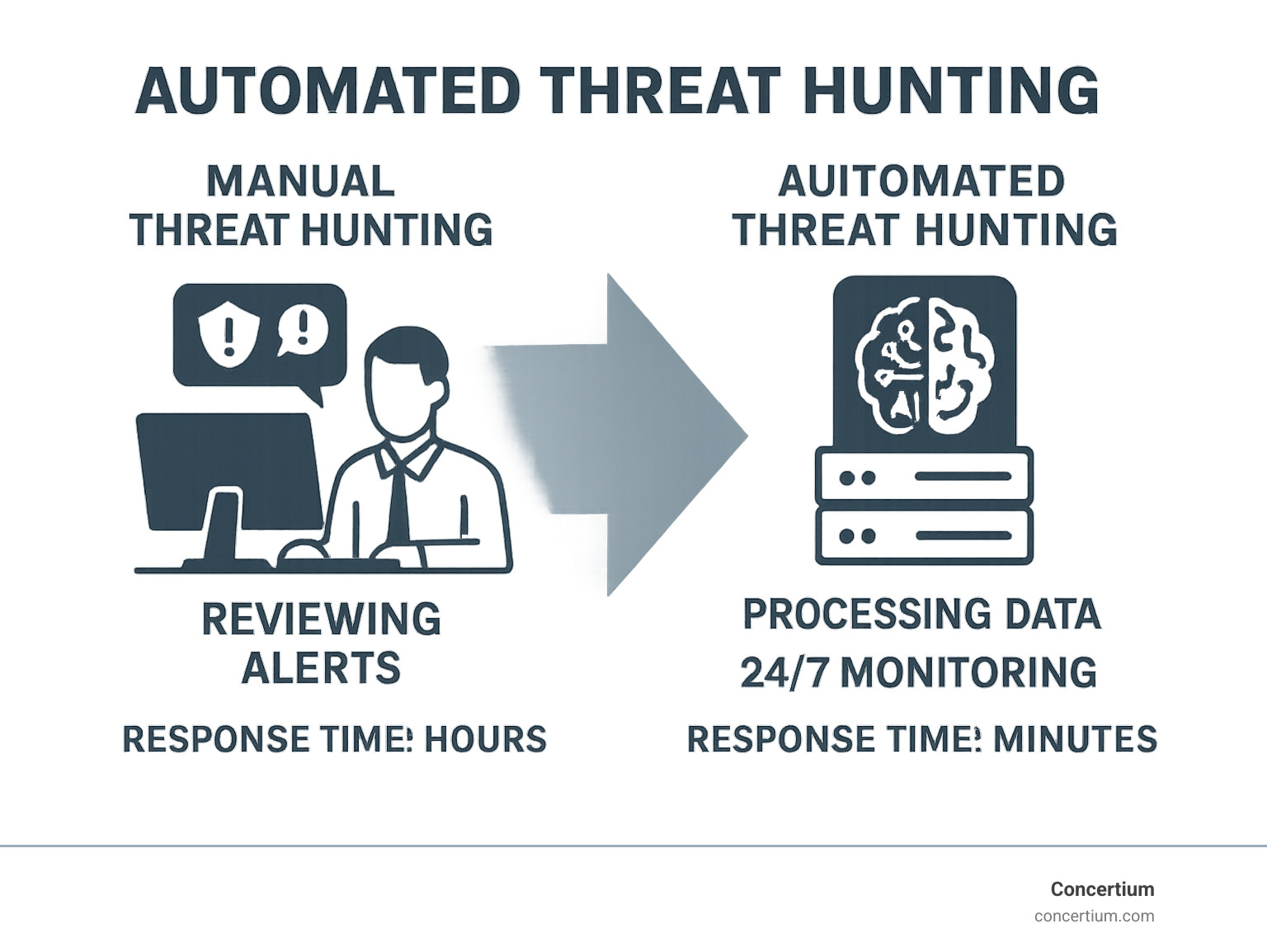
Traditional vs. Automated Threat Hunting
Traditional threat hunting involved skilled analysts manually sifting through mountains of data. While effective, this human-driven approach has serious limitations in speed and scale. There’s simply too much data for humans to process it all effectively.
| Feature | Traditional Threat Hunting | Automated Threat Hunting |
|---|---|---|
| Approach | Manual, Hypothesis-driven, Slow | Machine-speed, Continuous, Data-driven |
| Speed | Resource-intensive, limited by human capacity | Scalable, real-time processing |
| Coverage | Reactive, focused investigations | Proactive, comprehensive monitoring |
| Resource Use | Human-led analysis and decision making | Human-augmented, strategic oversight |
Automated threat hunting flips this script. It doesn’t replace human analysts; it augments them. The technology handles the heavy lifting—processing vast amounts of data and identifying patterns at machine speed. This frees up your experts to focus on what humans do best: strategic decisions, understanding context, and responding to complex threats. This shift to human-augmented hunting means your team can monitor your entire attack surface 24/7 without burning out.
The Critical Need in Today’s Threat Landscape
Today’s cyber threats are more sophisticated and persistent than ever. Advanced Persistent Threats (APTs) and zero-day exploits can bypass traditional signature-based security tools. Internally, security teams face immense operational pressures.
Alert fatigue is a real problem, as genuine threats get lost in a sea of notifications. This leads to analyst burnout and contributes to the broader cybersecurity skills gap. Meanwhile, the attack surface keeps expanding with cloud computing, remote work, and IoT devices, making manual monitoring impossible.
This is where automated threat hunting becomes essential. It addresses these challenges by providing continuous monitoring, reducing alert noise by up to 99%, and allowing your team to work more strategically. Instead of being overwhelmed, your analysts can focus on the sophisticated attacks that truly require human expertise.
For organizations looking to stay ahead, our Advanced Threat Protection solutions provide the comprehensive coverage needed in today’s threat landscape.
Core Methodologies and Components
Effective automated threat hunting relies on a solid methodology and the right tools. The process follows a logical sequence that transforms suspicion into action, starting with hypothesis generation based on threat intelligence or unusual patterns. This is followed by data collection and intelligence gathering from logs, network traffic, and endpoints.
During the investigation phase, analysts dive deep into the data to confirm or debunk the hypothesis. If a threat is found, the final step is response and resolution, which involves containing and eliminating the threat. What’s learned is fed back into the system to improve future hunts in a continuous cycle. Automating key elements of this process enables remarkable speed, a core principle of our Proactive Threat Hunting services.
Key Methodologies Driving the Hunt
Automation allows different hunting methodologies to be executed consistently and at scale.
- Structured hunting begins with a hypothesis, often guided by the MITRE ATT&CK Framework. It involves systematically searching for evidence of specific attacker tactics, techniques, and procedures (TTPs), also known as Indicators of Attack (IoAs).
- Unstructured hunting starts with an Indicator of Compromise (IoC), such as a suspicious IP address or file hash. The hunt then pivots to search through historical data to find patterns associated with that indicator.
- Entity-driven hunting prioritizes hunts based on high-value assets, vulnerable systems, or critical user groups, ensuring the business’s crown jewels are protected first.
The MITRE ATT&CK Framework provides a common language for understanding adversary behavior, giving automated platforms the intelligence to suggest specific queries and detections.
Essential Components of an Automated Platform
An effective automated threat hunting platform requires several key components working together seamlessly.
- Data Lake: A central repository designed to handle massive volumes of security data from across the IT environment, including endpoints, networks, and cloud services.
- Security Analytics Engine: The brain of the operation, powered by AI and machine learning. It processes data to identify patterns and anomalies that indicate suspicious activity.
- Automation Playbooks and Workflows: These handle repetitive tasks like running scheduled scans, validating queries, and enriching data automatically, often through low-code or no-code interfaces.
- Threat Intelligence Integration: The platform continuously ingests intelligence from various sources to enrich data, provide context, and inform hunting hypotheses.
- SIEM and XDR Integration: Ensures comprehensive visibility by working with existing Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solutions.
Our Collective Coverage Suite (3CS) is designed for this kind of comprehensive integration. When selecting components, our guide to Top Threat Detection Tools can help you make informed decisions.
The Transformative Role of AI and Machine Learning
AI and Machine Learning are the engines that power modern automated threat hunting. While a human analyst might review hundreds of alerts per day, AI can process millions of data points in seconds. But it’s not just about speed—it’s about intelligence. These systems excel at spotting subtle patterns and connections invisible to the human eye.
What makes AI truly transformative is its ability to learn and adapt. Unlike traditional tools that rely on known signatures, AI-powered systems continuously evolve, learning from every attack attempt and new piece of threat intelligence. This is essential for keeping pace with cybercriminals who are constantly developing new techniques. We need technology that can predict and anticipate rather than just react.
Our AI and Automated Threat Detection services harness this power to stay ahead of emerging threats.
How AI Improves Detection Capabilities
AI transforms threat detection by focusing on the intent behind suspicious behavior.
- Behavioral Analysis: AI creates detailed profiles of normal behavior for every user, device, and application. It immediately flags anomalies, such as a user accessing unusual files or logging in at odd hours. This approach catches threats that traditional tools miss, like those using stolen credentials.
- Anomaly Detection: Machine learning algorithms can identify irregularities in massive datasets without knowing what to look for in advance. They find the “unknown unknowns”—threats so new or sophisticated that no human has seen them before.
- Natural Language Processing (NLP): AI can read and understand threat intelligence from blogs, research papers, and forums, automatically incorporating this knowledge into hunting strategies.
- Noise Reduction: By correlating data points and learning from past investigations, AI dramatically reduces false positives. Some organizations see up to 70% fewer irrelevant alerts, letting security teams focus on real threats.
Our AI Improved Advanced Observability solutions bring these capabilities together for comprehensive threat visibility.
The Power of AI in an automated threat hunting strategy
When AI powers your automated threat hunting strategy, your security operation transforms from reactive to proactive.
- Continuous Monitoring: AI systems maintain a vigilant watch 24/7, never getting tired or losing focus. This is crucial because attackers don’t keep business hours.
- Real-Time Analysis: Threats are caught as they happen. The system processes events instantly, identifying suspicious patterns the moment they emerge.
- Automated Correlation: AI connects seemingly unrelated dots—like a failed login, unusual network traffic, and a new server process—to recognize them as a coordinated attack.
- AI-Driven Incident Response: When threats are confirmed, the system can automatically quarantine infected machines, block malicious IPs, and alert security teams within seconds.
This intelligent approach is the foundation of our Automated Network Threat Detection services.
Key Benefits: Boosting Security and Efficiency
Implementing automated threat hunting transforms your Security Operations Center (SOC) from a reactive fire department into a proactive prevention service. It acts as a force multiplier for your existing team, automating heavy lifting so your experts can focus on strategic thinking and complex problem-solving.
The results are tangible. Organizations often see a 35% improvement in Total Cost of Ownership after implementing automated solutions. This is about fundamentally improving your security posture and making your team more effective.
Our Managed Detection and Response services are built on these proven benefits, combining nearly 30 years of expertise with cutting-edge automation.
Drastically Reducing Detection and Response Times
In cybersecurity, time is everything. Automated threat hunting compresses critical time windows dramatically.
- Mean Time to Detect (MTTD): This measures how long it takes to spot a threat. With automated systems continuously monitoring data at machine speed, you can reduce MTTD by up to 50%, finding breaches in days instead of months.
- Mean Time to Respond (MTTR): This tracks how quickly you contain threats. Automated playbooks can initiate containment measures instantly, also cutting MTTR by 50% and turning week-long incidents into matters of hours.
Machine-speed investigation and automated containment mean threats are neutralized before they can cause significant damage. This rapid response is at the core of our Real-Time Threat Detection Services for Security.
Overcoming Operational Challenges
Automated threat hunting directly tackles the pain points that overwhelm modern security teams.
- Reduces Alert Fatigue: Automation cuts through the noise, reducing false positives by 70% and overall alert volume by up to 99%. This transforms a flood of notifications into a manageable stream of actionable threats.
- Mitigates Analyst Burnout: By automating repetitive tasks like log analysis, you free talented professionals to work on complex investigations and strategic improvements. This boosts job satisfaction and retention.
- Scales Security Operations: Automation allows you to increase your team’s capacity threefold without adding headcount. It handles larger data volumes and more complex environments with standardized workflows.
- Bridges the Cybersecurity Skills Gap: Automation makes sophisticated hunting capabilities accessible to less experienced team members, acting as a guide and force multiplier for your entire team.
With nearly 30 years of experience, we design solutions that address these operational realities while delivering robust risk management and compliance.
Implementing and Integrating Automated Threat Hunting
Getting started with automated threat hunting is about upgrading your security ecosystem, not replacing it. The goal is to make your existing tools work together more intelligently, changing your SOC into a unified, powerful defense system.
Success depends on understanding your current SOC maturity and setting realistic goals. You can start small by automating simple alert triage and scale up to more advanced AI-driven hunts. The process is one of continuous improvement, constantly refining AI models and learning from each investigation.
This strategic approach aligns with our comprehensive IT Governance, Risk and Compliance framework, ensuring your security evolution supports business objectives.
Integrating with Your Existing Security Operations
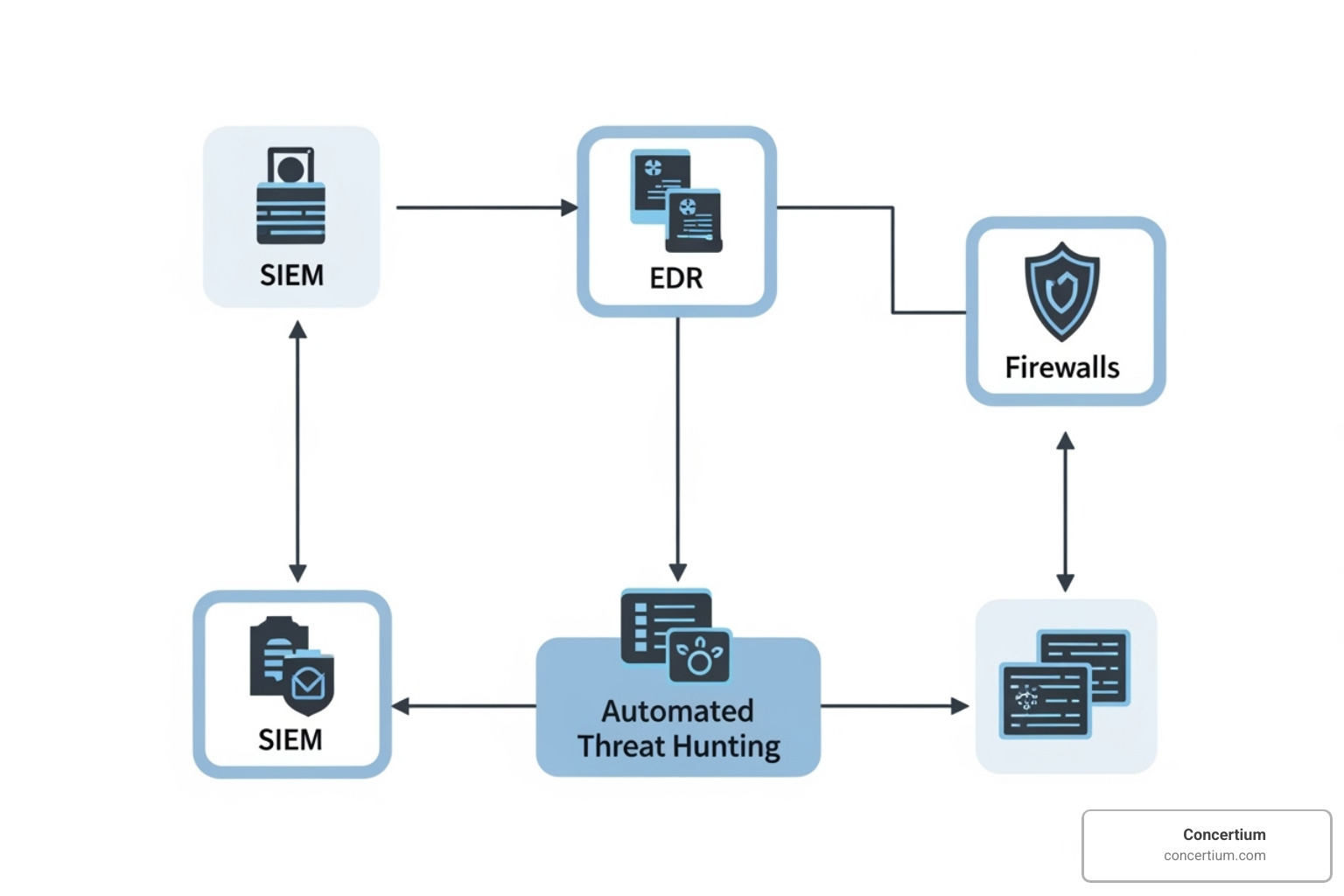
True power is open uped when all your security tools communicate and work as a team.
Modern automated threat hunting platforms are designed for integration. Through API integrations, they connect with your SIEM, EDR, firewalls, and cloud platforms. This creates centralized visibility, giving you a single, unified view of your security landscape instead of forcing you to jump between multiple consoles.
SOAR (Security Orchestration, Automation, and Response) platforms can act as the conductor, coordinating automated playbooks across your entire security stack. This ensures that when a threat is detected, the right actions happen automatically and immediately.
This integrated approach is the foundation of our Threat Detection and Response Solutions, designed to work with your existing infrastructure.
Common Adoption Challenges and How to Overcome Them
Implementing automated threat hunting can present challenges, but they are all manageable with the right approach.
- Data Complexity: Modern IT environments generate vast amounts of data. The solution is to leverage platforms that not only collect data but also enrich it with context, turning raw logs into actionable intelligence.
- Skill Gaps: You don’t need to be an AI expert. Modern platforms offer low-code/no-code automation, and partnering with a managed security service provider can bridge any knowledge gaps.
- Resource Allocation: Focus on the clear ROI. Show how automation reduces breach costs and improves team efficiency. Start with targeted projects that deliver quick wins to build the business case.
- Tool Selection: Choose platforms that integrate well with your existing tools, are scalable, and match your team’s capabilities. Focus on operational improvement, not just feature lists.
- Change Management: Moving to a proactive model requires a cultural shift. Ensure success with clear communication, comprehensive training, and celebrating early wins to build momentum.
Our Cybersecurity Risk Assessment Services help identify and address these challenges upfront.
Frequently Asked Questions about Automated Threat Hunting
This technology represents a significant shift in cybersecurity. Here are answers to the most common questions we hear.
Does automated threat hunting replace human analysts?
Not at all. Automated threat hunting gives your security analysts superpowers; it doesn’t make them obsolete. Automation handles the tedious, high-volume tasks—sifting through logs, running routine checks, and flagging anomalies. This frees up your talented analysts to do what they do best: high-level analysis and strategic thinking.
Human analysts are irreplaceable. They bring context, judgment, and creativity that machines lack. They understand your business, form complex hypotheses, and make critical decisions during an incident. The goal is a human-machine team where automation provides the speed and scale, and humans provide the intelligence and strategy.
How is the effectiveness of a threat hunt measured?
Measuring success is crucial for demonstrating value. We track several key metrics to gauge the effectiveness of an automated threat hunting program:
- Mean Time to Detect (MTTD): How quickly you spot a threat.
- Mean Time to Respond (MTTR): How fast you can contain and neutralize a threat.
- Detection Rate: The percentage of actual threats you successfully catch.
- False Positive Rate: The reduction in non-actionable alerts, which frees up analyst time.
- Dwell Time Reduction: The decrease in the amount of time an attacker can remain undetected in your network.
- MITRE ATT&CK Coverage: How comprehensively your program detects threats across different adversary techniques.
Improvements in these areas, along with increased analyst productivity, are clear indicators of a successful program.
What is the first step to implementing an automated threat hunting program?
Starting an automated threat hunting program is a strategic process, not an overnight change. The key is to build from a solid foundation.
- Assess Your Current State: Take inventory of your existing security tools, data sources, and potential visibility gaps. Understand your starting point.
- Define Clear Objectives: What are you trying to achieve? Are you focused on insider threats, ransomware, or reducing response times? Start with specific, actionable goals.
- Centralize Data Collection: Effective hunting requires comprehensive, high-quality data from endpoints, networks, and cloud environments flowing into a centralized platform for analysis.
- Select the Right Tools: Choose a platform that integrates with your existing stack, offers robust AI capabilities, and is intuitive for your team to use.
- Start Small and Iterate: Begin with a single, well-defined use case. Learn from the experience, refine your process, and then gradually expand your program. This approach builds confidence and delivers quick wins.
Partnering with an experienced cybersecurity provider can accelerate this journey and help you avoid common pitfalls.
Conclusion
The cybersecurity landscape has changed. Waiting for alarms is no longer a viable strategy. Automated threat hunting is the fundamental shift that allows organizations to move from merely surviving cyber attacks to thriving despite them.
Attackers use automation to operate at machine speed. To fight back effectively, defenders must do the same. Automated threat hunting levels the playing field by combining the analytical power of AI with irreplaceable human expertise.
This synergy allows you to drastically reduce detection and response times, eliminate up to 99% of the alert noise that overwhelms security teams, and transform reactive operations into proactive, intelligent defense systems. Your expert analysts are freed from mundane tasks to focus on strategic investigations and critical decision-making.
This is the future of security operations: a proactive posture where threats are actively hunted down before they can cause significant damage.
At Concertium, we’ve been perfecting this approach for nearly 30 years. Our Collective Coverage Suite (3CS) embodies this philosophy, combining AI-improved observability with automated threat eradication. We create custom solutions that fit your unique challenges and goals.
The question isn’t whether you need automated threat hunting—it’s whether you’re ready to take control of your cybersecurity destiny.
Ready to transform your security operations from reactive to proactive? Take your security from reactive to proactive with our Proactive Threat Hunting services.