AI Overview: Why Every Business Must Understand Cybersecurity Incidents
Cybersecurity incidents are unavoidable in today’s digital landscape—and knowing how to identify, respond to, and learn from them is what separates resilient organizations from vulnerable ones.
Why Every Business Must Understand Cybersecurity Incidents
A cybersecurity incident is any occurrence that actually or potentially compromises the confidentiality, integrity, or availability of your information systems or data. According to NIST, these incidents include both successful attacks and imminent threats that violate your security policies or procedures.
Here’s what you need to know about cybersecurity incidents:
- Definition: An event that jeopardizes your data security or violates security policies
- Impact: Can result in data theft, system damage, business disruption, or financial loss
- Types: Include ransomware, phishing, data breaches, insider threats, and malware infections
- Response: Requires immediate action following a structured incident response plan
- Reporting: Critical infrastructure and federal agencies must report to CISA within specific timeframes
Every day, another company gets caught off guard by a data breach. The harsh reality? There’s no such thing as perfect security. What separates resilient businesses from victims isn’t the absence of incidents – it’s how well they prepare for and respond to them.
The difference between a minor security hiccup and a business-ending disaster often comes down to one thing: preparation. Organizations with formal incident response plans can reduce breach costs by almost half a million dollars on average, according to IBM’s research.
Whether you’re dealing with a suspicious email that slipped through your filters or a full-blown ransomware attack, understanding what constitutes a cybersecurity incident is your first line of defense. This knowledge helps you distinguish between false alarms and real threats, ensuring you respond appropriately when it matters most.
Quick cybersecurity incident definitions:
- Cybersecurity compliance assessment
- cyber security crisis management
- cyber security tabletop exercises
What Exactly Is a Cybersecurity Incident?
So, what exactly are we talking about when we say “cybersecurity incident”? It’s more than just a vague feeling that something is wrong. According to the National Institute of Standards and Technology (NIST) and other authoritative sources, a cybersecurity incident is formally defined as:
An occurrence that results in actual or potential jeopardy to the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
Let’s break that down, because it’s a mouthful! At its core, a cybersecurity incident impacts one or more of the three pillars of information security, often referred to as the CIA Triad:
- Confidentiality: Ensuring that information is accessible only to those authorized to have access. Think data breaches where sensitive information is stolen.
- Integrity: Maintaining the accuracy and completeness of data. This could be data alteration, corruption, or unauthorized modification.
- Availability: Guaranteeing that systems and information are accessible when needed by authorized users. Denial-of-Service (DoS) attacks are a prime example here.
Beyond impacting the CIA Triad, an incident can also be a violation—or even an imminent threat of a violation—of your organization’s security policies, procedures, or acceptable use policies. This means an incident doesn’t always have to be a successful breach; a credible threat that almost happened still counts, prompting the need for investigation and response.
CISA (Cybersecurity and Infrastructure Security Agency) echoes this sentiment, defining a cybersecurity incident as an occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system, or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies. Essentially, if it’s bad for your digital assets or your rules, it’s an incident.
Common Types of Incidents
Cyber threats are as varied as the attackers behind them. Our daily news feeds are filled with stories of organizations falling victim to different types of cybersecurity incidents. Here are some of the most common ones we encounter:
- Ransomware: Malicious software that encrypts your data or locks you out of your systems, demanding a payment (ransom) to restore access. It’s like a digital hostage situation.
- Phishing Attacks: Deceptive communications, usually emails, designed to trick individuals into revealing sensitive information (like login credentials) or downloading malware. We’ve all seen those suspicious emails, haven’t we?
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks: Overwhelming a system, server, or network with a flood of traffic, making it unavailable to legitimate users. Imagine a traffic jam so bad, no one can get to their destination.
- Insider Threats: Security risks that come from within your organization, either from malicious employees or, more commonly, negligent ones who accidentally expose sensitive data or introduce vulnerabilities.
- Data Breaches: Unauthorized access to, or acquisition of, sensitive, protected, or confidential data. This is often the incident that makes headlines and leads to significant financial and reputational damage.
- Malware Infections: A broad category encompassing various malicious software (viruses, worms, Trojans, spyware) designed to disrupt, damage, or gain unauthorized access to computer systems.
- Supply Chain Attacks: Targeting an organization by compromising less secure elements in its supply chain, such as vendors or software providers. If one link in the chain breaks, the whole system can be vulnerable.
The Difference Between a Security Event and a Cybersecurity Incident
It’s easy to use the terms “security event” and “cybersecurity incident” interchangeably, but there’s a crucial distinction. Think of it this way: all incidents are events, but not all events are incidents.
- Security Event: Any observable occurrence in a system or network. This could be a user logging in, a file being accessed, or even a failed login attempt. Most security events are benign and part of normal operations.
- Cybersecurity Incident: A security event that has been determined to have an impact on the organization, prompting the need for response and recovery. It’s an unwanted or unexpected event (or series of events) that either has compromised business operations or has a significant probability of compromising them.
For example, a security event might be a hundred failed login attempts to an account. If this is a normal occurrence for a specific system (e.g., a honeypot), it might not escalate to an incident. However, if those failed attempts are followed by a successful login from an unusual location, that event chain quickly becomes a cybersecurity incident because it indicates potential unauthorized access and a compromise of confidentiality and integrity.
The process of distinguishing events from incidents is called triage. Our security teams constantly monitor for events, then analyze and prioritize them to determine which ones warrant a full incident response. This careful differentiation saves resources and ensures we focus our efforts where they’re truly needed.
The Anatomy of an Effective Response: The NIST Framework
When a cybersecurity incident hits, having a plan isn’t just helpful—it’s the difference between a manageable crisis and a company-ending disaster. Think of it like having a fire escape route: you hope you’ll never need it, but when smoke starts billowing, you’ll be grateful you took the time to map it out.
The National Institute of Standards and Technology (NIST) has done the heavy lifting for us with their Special Publication 800-61 Rev. 2, the “Computer Security Incident Handling Guide.” This framework has become the gold standard for incident response, and for good reason—it works.
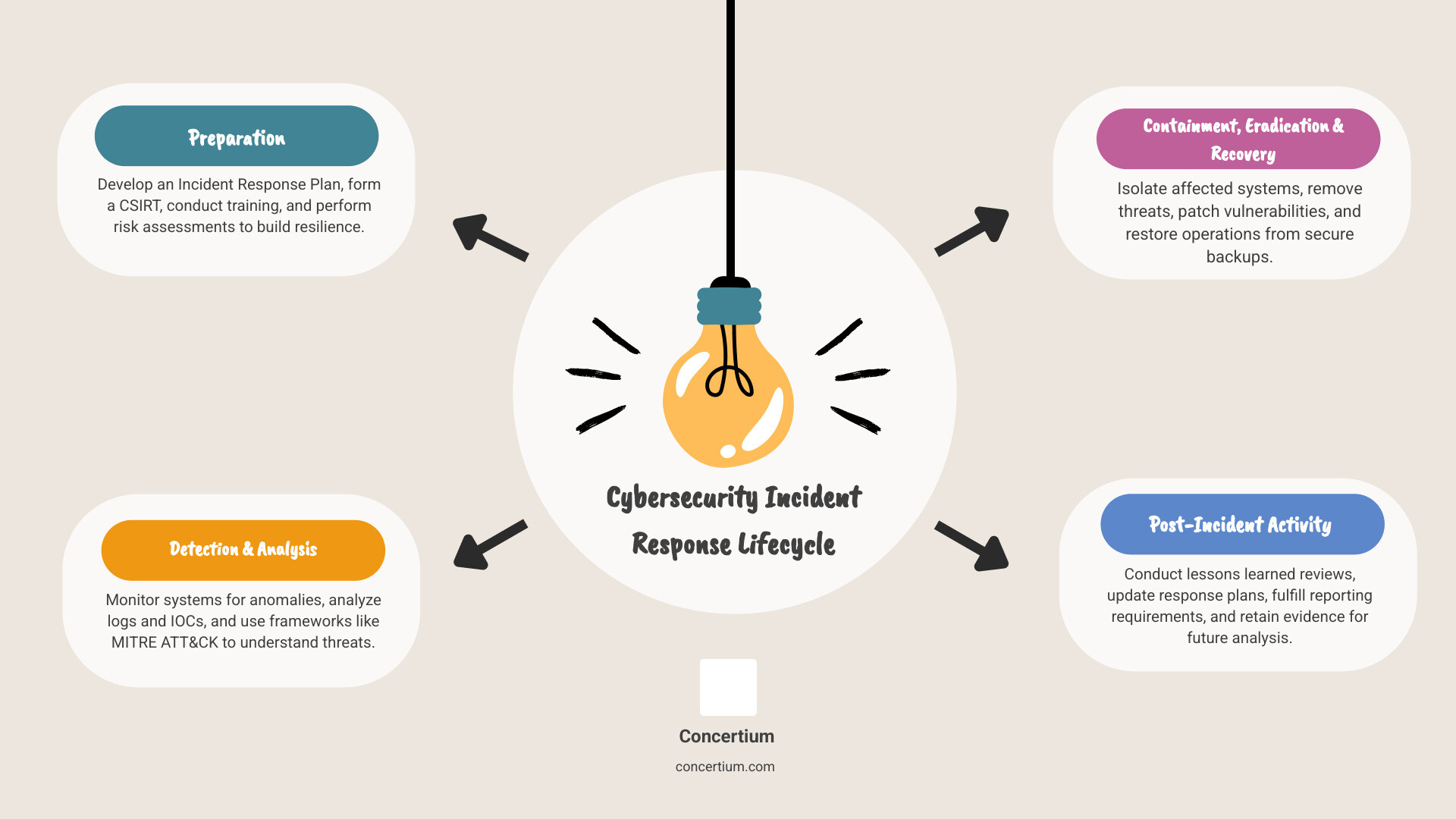
The NIST Incident Response Lifecycle follows four distinct phases that flow naturally from one to the next. It’s not a straight line, though. Think of it more like a cycle where lessons from each incident feed back into better preparation for the next one. The framework balances proactive preparation (getting ready before anything happens) with reactive response (dealing with incidents when they occur).
Phase 1: Preparation
You wouldn’t try to assemble IKEA furniture without the instructions, right? The same logic applies to incident response. Preparation is where we do all the groundwork before chaos strikes, and it’s honestly the most important phase of the entire process.
Building an effective Incident Response Plan (IRP) is your first priority. This isn’t some dusty document that sits in a drawer—it’s your playbook for when things go sideways. Your IRP should outline who does what, how everyone communicates, and what technical steps to take for different types of incidents. The key is customizing it for your specific organization, because a generic plan is about as useful as a chocolate teapot.
Next, you’ll want to designate a Computer Security Incident Response Team (CSIRT). This is your incident response squad—the people who spring into action when a cybersecurity incident occurs. Even smaller organizations need at least a few people who know their roles inside and out. Pro tip: always have backup people trained for key roles, because Murphy’s Law says your primary responder will be on vacation when you need them most.
Don’t forget about user training and awareness. Your employees are often your first line of defense, and they’re also the most likely to spot something suspicious before your fancy security tools do. Regular training on recognizing phishing attempts, reporting weird behavior, and following security protocols can prevent many incidents from ever becoming serious problems.
Risk assessments help you understand what you’re protecting and where you’re most vulnerable. You can’t defend everything equally, so knowing your crown jewels and biggest weaknesses lets you focus your efforts where they’ll do the most good. Similarly, establishing system baselines means documenting what “normal” looks like, which makes it much easier to spot when something’s off.
Finally, you’ll need the right tools in your security arsenal. This includes Security Information and Event Management (SIEM) systems to collect and analyze logs, Endpoint Detection and Response (EDR) tools to monitor individual devices, and other specialized security technologies that fit your environment and budget.
Phase 2: Detection and Analysis
This is where things get interesting—and sometimes a little nerve-wracking. Detection and analysis is all about figuring out if something bad is actually happening and, if so, how bad it really is.
Detecting incidents happens through multiple channels. Your security tools are constantly scanning for suspicious activity and generating alerts, but don’t overlook the power of a sharp-eyed employee who notices something doesn’t look right. Sometimes the most sophisticated attacks are caught by someone saying, “Hey, this email seems weird.”
Once you’ve detected a potential incident, the real detective work begins. Log analysis becomes crucial as you dig through firewall logs, server logs, and application logs to piece together what happened. It’s like reconstructing a crime scene, except the evidence is scattered across dozens of different systems and buried in thousands of log entries.
The MITRE ATT&CK framework becomes invaluable during analysis, helping you understand the attacker’s Tactics, Techniques, and Procedures (TTPs). Instead of just knowing “someone got in,” you can start understanding how they got in, what they’re trying to accomplish, and where they might go next.
Your analysis should answer the critical questions: Who is involved or affected? What systems or data are compromised? When did this start and when was it finded? Where did it originate and spread? Why did this happen—what vulnerability was exploited? How did the attacker gain access and move around your network?
This phase is about gathering enough information to make smart decisions about what to do next, without accidentally making things worse or tipping off the attacker that you’re onto them.
Phase 3: Containment, Eradication, and Recovery
Now comes the action phase—time to stop the bleeding, clean up the mess, and get back to business. This three-part process requires careful coordination to avoid making things worse in your rush to fix them.
Containment is your first priority, and it comes in two flavors. Short-term containment involves quick actions to stop the incident from spreading further—think disconnecting infected computers from the network or blocking malicious IP addresses at your firewall. It’s like putting up traffic cones around an accident scene.
Long-term containment is more strategic, involving measures like network segmentation or implementing stronger access controls around your most sensitive systems. You’re essentially building better walls around what matters most while you figure out your next moves.
Eradication means removing the threat completely. This involves removing malware from infected systems, patching vulnerabilities that allowed the attack to succeed, and thoroughly reviewing affected systems to make sure no backdoors or persistent threats remain. It’s meticulous work that requires patience—rushing through eradication often means the attacker comes right back.
Recovery focuses on getting everything back to normal operations safely. Restoring from backups becomes critical, especially after ransomware attacks (which is why having good, regularly tested backups is so important). Before bringing systems back online, you need to verify system integrity through thorough testing to ensure everything works properly and securely.
Throughout recovery, improved monitoring of restored systems helps catch any signs that the attacker might be trying to regain access.
Phase 4: Post-Incident Activity
Here’s where many organizations drop the ball, but it’s actually one of the most valuable phases of the entire process. Post-incident activity transforms a crisis into a learning opportunity that makes your organization stronger.
The post-incident review, often called a “hotwash” or “lessons learned” meeting, brings everyone together to honestly discuss what went well, what could have been better, and what needs to change. This isn’t about pointing fingers—it’s about improving your defenses for next time.
Based on what you learn, you’ll want to update your Incident Response Plan and related procedures. Every incident teaches you something new about your environment, your team’s capabilities, or emerging threats.
Don’t forget about reporting requirements. Depending on your industry and the nature of the incident, you might need to notify regulators, law enforcement, or affected customers. For critical infrastructure and federal agencies, this often means reporting to CISA through their Cyber Incident Response services.
Finally, evidence retention ensures you preserve forensic data and documentation according to legal and organizational requirements. You never know when this information might be needed for legal proceedings or future investigations.
This phase turns every cybersecurity incident into a stepping stone toward better security. Each crisis becomes a catalyst for improvement, making your organization more resilient with every challenge you face.
Advanced Incident & Vulnerability Management
The world of cybersecurity has evolved far beyond simply reacting to threats as they appear. Today’s most effective organizations take a proactive stance, combining intelligence-driven defense with sophisticated vulnerability management. It’s like the difference between waiting for a burglar to break in versus studying crime patterns and reinforcing your doors before anything happens.
Cyber Threat Intelligence (CTI) serves as the backbone of modern incident response, providing crucial insights into how attackers think, operate, and target their victims. Rather than flying blind during a cybersecurity incident, CTI gives response teams a roadmap of adversary Tactics, Techniques, and Procedures (TTPs), threat actor profiles, and likely targets.
This intelligence transforms how we approach security at every level. Proactive defense becomes possible when we understand which attack vectors are trending and can strengthen those specific areas before they’re exploited. Our detection capabilities sharpen dramatically when monitoring tools are configured to watch for specific TTPs or Indicators of Compromise (IOCs) that intelligence sources have identified as active threats.
When incidents do occur, CTI accelerates the analysis phase considerably. Instead of starting from scratch to understand an attack’s nature, teams can quickly match observed behaviors to known threat actors and predict their likely next moves. This knowledge proves invaluable during eradication and recovery as well—knowing exactly how an adversary operates helps ensure we remove all traces of their presence and secure systems against their specific re-infection methods.
A Deeper Look at a Major Cybersecurity Incident
Not every security hiccup deserves the same level of attention. A major incident carries weight that extends far beyond IT departments, potentially affecting national security, economic stability, or public safety. According to OMB Memorandum M-20-04, these incidents pose demonstrable harm to national security interests, foreign relations, the U.S. economy, public confidence, civil liberties, or public health and safety. Data breaches involving Personally Identifiable Information (PII) of 100,000 or more people also qualify.
The stakes become particularly high for Federal Civilian Executive Branch (FCEB) organizations, where reporting requirements reflect the serious nature of these incidents. Agencies must notify CISA within one hour of determining that an incident qualifies as “major”—a timeline that underscores the urgency these situations demand.
CISA coordination during major incidents isn’t just bureaucratic red tape; it’s a strategic lifeline. As the lead agency for asset response activities, CISA coordinates government-wide efforts, provides cutting-edge cyber threat intelligence, and serves as the central hub for agencies needing technical assistance. Think of them as the emergency response coordinator for the digital world.
The beauty of the federal response lies in its multi-agency coordination. CISA handles the technical heavy lifting through “Asset Response”—providing technical assistance, sharing threat intelligence, and coordinating defensive actions across federal agencies and critical infrastructure. Meanwhile, the FBI takes charge of “Threat Response,” focusing on law enforcement aspects, investigating cybercrimes, attributing attacks, and pursuing the bad actors behind them. The Office of the Director of National Intelligence (ODNI) rounds out the trio by providing intelligence support and insights into nation-state actors and their capabilities.
This coordinated approach ensures that both immediate technical mitigation and long-term investigative efforts receive proper attention. You can dive deeper into federal reporting requirements in CISA’s Cyber Incident Reporting unified message.
Incident Response vs. Vulnerability Response
While incident response and vulnerability response work hand-in-hand, they tackle security from opposite ends of the timeline. Incident response deals with active threats that have already materialized—the digital equivalent of calling the fire department when your house is burning. Vulnerability response, on the other hand, focuses on identifying and fixing weaknesses before they can be exploited—like installing smoke detectors and fire extinguishers before any flames appear.
| Feature | Incident Response | Vulnerability Response |
|---|---|---|
| Primary Goal | React to and mitigate active attacks or breaches | Proactively identify and fix weaknesses before exploitation |
| Trigger | Detection of a security event that indicates compromise | Identification of a potential weakness (e.g., scan, report) |
| Focus | Containing, eradicating, and recovering from an active threat | Patching, reconfiguring, or mitigating potential threats |
| Timeframe | Often urgent, real-time, and reactive | Can be scheduled, proactive, and preventative |
| Key Question | “What happened, and how do we stop it and recover?” | “What could happen, and how do we prevent it?” |
| Overlap | Incident analysis often uncovers exploited vulnerabilities | Timely vulnerability patching can prevent incidents |
Vulnerability response playbooks create the proactive shield that complements reactive incident response efforts. These structured processes define how organizations identify, evaluate, prioritize, and remediate security weaknesses in systems and applications. By addressing vulnerabilities before attackers can exploit them, we significantly reduce the attack surface and prevent many potential cybersecurity incidents from occurring.
The most critical aspect of vulnerability response involves responding to actively exploited vulnerabilities—those weaknesses that attackers are already using in real-world attacks. These represent immediate and severe risks that demand urgent attention.
CISA’s Known Exploited Vulnerabilities (KEV) Catalog serves as an essential resource here, maintaining a continuously updated list of vulnerabilities that threat actors are actively exploiting. Federal agencies must remediate KEV vulnerabilities within specific timelines, but smart organizations of all types treat this catalog with the same urgency.
When facing actively exploited vulnerabilities, rapid response patching becomes the priority, often bypassing normal change management processes in favor of emergency procedures. However, when patches aren’t immediately available, compensating controls provide crucial interim protection—disabling vulnerable services, reconfiguring firewalls, or deploying intrusion prevention rules to mitigate risk until permanent fixes can be applied.
By weaving together robust vulnerability management with strong incident response capabilities, organizations create a comprehensive defense strategy that both prevents threats and responds effectively when prevention isn’t enough.
Frequently Asked Questions about Cybersecurity Incidents
When it comes to understanding cybersecurity incidents, we hear the same questions over and over again from our clients. And honestly? That’s a good thing! It means organizations are taking security seriously and want to get it right. Let’s tackle the most common questions we encounter.
What constitutes a cybersecurity incident according to NIST?
Here's the official definition that matters: A cybersecurity incident is an occurrence that actually or imminently jeopardizes the confidentiality, integrity, or availability (the famous CIA triad) of an information system or the information it processes, stores, or transmits. But it doesn't stop there.
The definition also includes violations or imminent threats of violation of security policies, procedures, or acceptable use policies. This means you don't need a successful breach to have an incident on your hands. Even a credible threat that almost happened counts and requires your attention.
Think of it this way: if something bad happened to your digital assets, or if something bad almost happened and violated your security rules, you're dealing with a cybersecurity incident. The key word here is "imminently" - NIST recognizes that sometimes the threat of an incident is just as serious as the incident itself.
What are the four main phases of incident response?
The NIST framework breaks incident response into four primary phases that create a complete lifecycle for managing incidents from start to finish:
Phase 1: Preparation is where you get your house in order before anything bad happens. This includes building your incident response plan, training your team, and setting up the tools you'll need when crisis strikes.
Phase 2: Detection & Analysis is the detective work phase. You're figuring out what happened, who's involved, and how bad things really are. This is where your monitoring tools and threat intelligence really shine.
Phase 3: Containment, Eradication, & Recovery is the action-packed phase where you stop the bleeding, clean up the mess, and get back to business. It's like being a digital paramedic, surgeon, and physical therapist all rolled into one.
Phase 4: Post-Incident Activity is where you turn crisis into opportunity. You're conducting lessons learned sessions, updating your plans, and making sure the next incident response goes even smoother.
This lifecycle provides a structured approach that prevents panic and ensures nothing important gets forgotten when you're under pressure.
Who should I report a major cybersecurity incident to?
This depends on who you are and what kind of incident you're dealing with, but here's the breakdown:
For critical infrastructure and federal agencies, incidents must be reported to the Cybersecurity and Infrastructure Security Agency (CISA). They're the government's go-to team for cybersecurity coordination and can provide technical assistance, threat intelligence, and guidance during your response.
If your incident involves criminal activity - and many do - you'll also want to coordinate with law enforcement agencies like the FBI. They handle the investigative side of things, working to track down the bad guys and potentially recover stolen data or assets.
The timing matters too. For major incidents, federal agencies have just one hour to notify CISA once they determine an incident qualifies as "major." That might sound scary, but remember - CISA is there to help, not to punish.
For private sector organizations, while reporting requirements vary by industry and state, it's often wise to establish relationships with these agencies before you need them. When you're in the middle of a crisis is not the time to be figuring out who to call for help.
Conclusion: Turning a Crisis into a Catalyst for Stronger Security
Here’s the hard truth about cybersecurity: incidents are inevitable. No matter how robust your defenses, how well-trained your team, or how cutting-edge your technology, you will face some form of cybersecurity incident eventually. But here’s the empowering part—this inevitability doesn’t have to spell doom for your organization.
The difference between companies that crumble under cyber pressure and those that emerge stronger lies in one word: preparedness. When you understand what constitutes a cybersecurity incident, have a structured response framework in place, and treat each challenge as a learning opportunity, you transform potential disasters into stepping stones toward better security.
Think of it this way: every cybersecurity incident is like a stress test for your organization’s security posture. It reveals weak points you might never have finded otherwise, highlights gaps in your processes, and shows you exactly where to focus your improvement efforts. The companies that view incidents through this lens don’t just survive—they thrive.
The NIST framework we’ve explored isn’t just a theoretical exercise. It’s a battle-tested approach that has helped countless organizations steer their darkest digital hours and come out stronger on the other side. When you have clear preparation protocols, swift detection and analysis capabilities, effective containment and recovery procedures, and thorough post-incident learning processes, you’re not just managing crises—you’re building resilience.
Continuous improvement becomes your secret weapon. Each incident teaches you something new about your environment, your adversaries, and your own capabilities. Maybe you find that your backup systems need testing, or that your team needs additional training on a specific type of threat. Perhaps you realize that your communication protocols during an incident could be clearer, or that certain tools need fine-tuning. These insights are gold mines for strengthening your overall security posture.
At Concertium, we’ve witnessed how organizations can transform their relationship with cyber threats. With nearly 30 years of expertise in the cybersecurity field, we’ve seen companies turn their most challenging incidents into catalysts for remarkable security changes. Our Collective Coverage Suite (3CS) with AI-improved observability and automated threat eradication doesn’t just help you respond to incidents—it helps you learn from them and prevent similar ones from occurring.
The value of having a structured framework cannot be overstated. When chaos strikes, having a clear roadmap keeps your team focused, reduces response time, and minimizes damage. More importantly, it ensures that every incident becomes a building block for stronger future defenses rather than just another crisis to endure.
Ready to turn your next cybersecurity challenge into an opportunity for growth? Learn more about building robust incident response frameworks and find how the right approach can transform your organization’s security resilience.