AI Overview:
Why It Matters
Network monitoring management is no longer optional—it’s a core survival function for modern businesses. With IT downtime costing enterprises more than $300,000 per hour, organizations need proactive monitoring that prevents outages, protects against cyber threats, and ensures seamless operations across on-premises, cloud, and hybrid infrastructures.
Network Monitoring Management: Ultimate Guide 2025
Why Network Monitoring Management Is Critical for Modern Businesses
Network monitoring management is the continuous process of tracking, analyzing, and maintaining a computer network’s health to prevent costly downtime and security breaches. With a single hour of IT downtime costing over $300,000 for 91% of enterprises, effective network monitoring is essential for business survival.
Quick Answer: Best Network Monitoring Management Approaches
- Real-time Performance Monitoring – Track bandwidth, latency, and device health 24/7
- Proactive Alerting Systems – Get notified before problems impact users
- Comprehensive Visibility – Monitor on-premises, cloud, and hybrid environments
- AI-Improved Analytics – Use machine learning for anomaly detection and predictive insights
- Integrated Security Monitoring – Combine performance and security monitoring for complete protection
Proactive IT management, powered by network monitoring, allows teams to catch issues before they become catastrophes. In today’s complex environments of cloud services, remote work, and IoT devices, traditional monitoring falls short. Without full visibility, you’re left waiting for users to report that something is broken.
The stakes are higher than ever. Network failures lead directly to:
- Lost revenue and damaged customer relationships
- Security vulnerabilities and compliance fines
- Reduced employee productivity
This guide covers the tools and strategies that shift your IT team from reactive firefighters to proactive guardians, from basic protocols to advanced AI-driven solutions that predict problems before they happen.
Network monitoring management vocab explained:
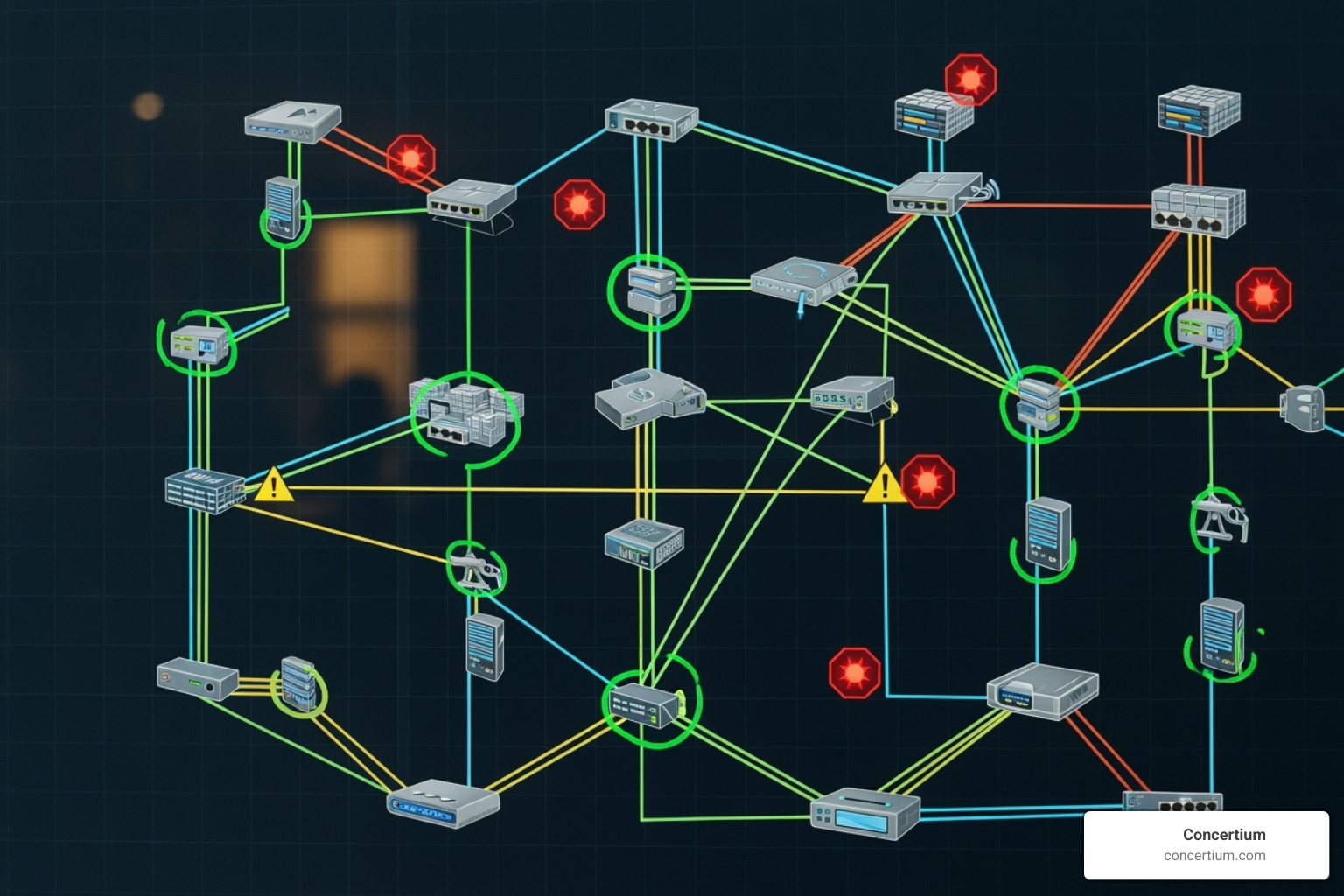
How Network Monitoring Systems Work
Network monitoring management systems operate in four interconnected stages. First, data collection continuously gathers information from every network device, such as routers, servers, and applications. Next, data analysis interprets this raw data, comparing current performance against historical baselines to identify meaningful patterns and anomalies.
When a metric crosses a predefined threshold, the alerting stage notifies the appropriate IT personnel. Smart alerting systems filter out noise to ensure that only significant events trigger a notification. Finally, root cause analysis pinpoints the exact source of a problem, allowing IT teams to fix the underlying issue instead of just treating symptoms. This process is foundational to effective Automated Network Threat Detection.
Key Monitoring Protocols
Monitoring protocols act as universal translators for network devices. Each has a specific purpose:
- Simple Network Management Protocol (SNMP): The industry standard for collecting detailed health and performance data from nearly all network devices.
- Internet Control Message Protocol (ICMP): Used for basic connectivity tests (like a ping) to determine if a device is reachable on the network.
- Windows Management Instrumentation (WMI): Provides deep visibility into Windows-based systems, gathering data on services, software, and hardware.
- Secure Shell (SSH): Allows monitoring tools to securely access and gather metrics from Unix and Linux systems.
- Flow protocols (NetFlow, sFlow): Analyze traffic patterns to show who is talking to whom, what applications are being used, and how much bandwidth is consumed.
- Packet analysis: Involves examining individual data packets for deep-dive troubleshooting and security forensics, crucial for Real-Time Threat Detection in Cybersecurity.
Agent-based vs. Agentless Monitoring
There are two primary methods for collecting network data:
Agent-based monitoring involves installing a small software agent on each monitored device. This provides highly detailed, real-time data from within the system itself. However, it requires managing the installation and updates of agents across all devices, which can be complex at scale.
Agentless monitoring gathers data remotely using standard protocols like SNMP or WMI. This simplifies deployment and reduces maintenance overhead, as no software needs to be installed on the target devices. The trade-off can be less granular data compared to an agent-based approach.
A hybrid monitoring strategy is often the most effective, using agents for critical systems that require deep visibility and agentless methods for the rest of the network. This balances detailed insight with ease of management.
Core Benefits and Types of Network Monitoring
Effective network monitoring management delivers tangible business benefits that directly impact profitability and operational success.
- Reduced Downtime: Proactive monitoring identifies potential failures, like an overloaded server, allowing IT teams to fix them before they cause outages.
- Efficient Resource Utilization: Data-driven insights show exactly where network bottlenecks occur, preventing wasteful spending on unnecessary hardware and ensuring targeted upgrades.
- Faster Troubleshooting: When issues arise, monitoring dashboards point directly to the problem’s source, reducing investigation time from hours to minutes.
- Improved User Experience: A stable, high-performing network keeps employees productive and customers satisfied, allowing IT to focus on strategic initiatives. This aligns with the goals of Managed Network and Firewalls services.
Types of Network Monitoring
Different types of monitoring focus on specific aspects of network health:
- Performance Monitoring: Tracks metrics like latency (delay), bandwidth utilization, packet loss, and jitter (inconsistent packet delivery) to ensure the network is running efficiently.
- Availability Monitoring: Answers the basic question, “Is it working?” by tracking uptime, downtime, and device reachability to ensure services are accessible.
- Configuration Monitoring: Detects unauthorized or accidental changes to device configurations, ensuring consistency and preventing security drifts.
- Cloud Monitoring: Extends visibility to public and private cloud environments (like AWS and Azure), tracking the performance of cloud-based resources and applications.
Network Monitoring vs. Network Security Monitoring
While related, network monitoring and network security monitoring have distinct goals. Traditional network monitoring focuses on operational health and performance, asking, “Is the network running smoothly?”
In contrast, network security monitoring focuses on protection, asking, “Is the network under attack?” It looks for threats, unauthorized access, and malicious behavior.
However, their data often overlaps. A performance issue, like a sudden traffic spike, could indicate a security threat, such as data exfiltration. Integrating these two disciplines provides a complete picture of network health and security posture, strengthening your overall Network Security Management and the effectiveness of Intrusion Detection Systems in Network Security.
Essential Features for Network Monitoring Management Tools
When selecting a network monitoring management tool, focus on core features that deliver tangible value and align with your business needs.
Key features include:
- Real-Time Visibility: Customizable dashboards that provide an at-a-glance view of network health.
- Comprehensive Support: The ability to monitor a wide range of infrastructure, including routers, switches, firewalls, servers, and applications.
- Intelligent Alerting: Customizable rules that notify the right people at the right time, with integrations for email, Slack, and ticketing systems.
- Reporting and Trend Analysis: The ability to generate detailed reports on historical data for capacity planning and compliance, which is vital for Vulnerability Risk Management.
- Scalability: The capacity to grow with your network, handling an increasing number of devices and complexity without performance degradation.
- Multi-Vendor Support: Compatibility with hardware and software from various manufacturers, ensuring complete coverage.
The Role of AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are changing network monitoring from a reactive to a proactive discipline.
- AI-Driven Anomaly Detection: ML algorithms learn your network’s normal behavior and flag deviations, catching subtle issues that static thresholds would miss.
- Predictive Analytics: By analyzing trends, AI can forecast future problems, such as predicting when a server will run out of disk space, allowing you to prevent issues before they impact users.
- Automated Root Cause Analysis: AI can instantly correlate events across multiple systems to identify the true source of a problem, drastically reducing investigation time.
- Reduced Alert Fatigue: AI-powered systems intelligently group and prioritize alerts, significantly cutting down on notification noise so your team can focus on what matters. This is a core component of Advanced Real-Time Threat Detection Solutions.
Additional Essential Features
- Network Mapping: Automated findy and visualization of your network topology to understand device dependencies.
- Bandwidth Analysis: Granular breakdown of network traffic by application, user, and protocol to identify bandwidth hogs and shadow IT.
- Cloud Infrastructure Support: Native visibility into public and private cloud platforms like AWS, Azure, and Google Cloud.
- Integration Capabilities: The ability to connect with other IT tools, such as SIEM and SOAR platforms, to create a unified operational workflow.
Choosing the Right Solution and Overcoming Challenges
Choosing the right network monitoring management solution requires careful consideration of your specific environment and goals.
- Assess Business Needs: First, identify your primary pain points. Are you focused on reducing downtime, improving performance, or meeting compliance requirements?
- Ensure Scalability: Select a tool that can handle not just your current network but also future growth in complexity, including cloud services and remote users.
- Prioritize Integration: The solution must integrate seamlessly with your existing IT stack (e.g., ticketing systems, security tools) to avoid creating data silos.
- Evaluate Usability: An intuitive user interface is critical. During an outage, your team needs clear dashboards that simplify decision-making, not complicate it.
- Calculate Total Cost of Ownership (TCO): Look beyond the initial price. Factor in implementation, training, and maintenance costs. A comprehensive tool may support multiple functions, like Compliance Risk Management Services.
Common Challenges in Network Monitoring Management
Every IT team faces common problems in network monitoring:
- Alert Fatigue: A constant stream of low-priority or false-positive alerts causes teams to ignore notifications, potentially missing critical issues.
- Network Blind Spots: Widespread encryption can obscure traffic details, making it difficult to perform deep packet inspection and spot hidden threats.
- Distributed Networks: Managing a mix of on-premises data centers, multiple cloud environments, and remote workers complicates visibility and consistent monitoring.
- Big Data Handling: The massive volume of logs and metrics generated by modern networks can be difficult to store, process, and analyze effectively.
- Inaccurate Baselines: Static performance baselines quickly become outdated as networks evolve, leading to irrelevant alerts.
Overcoming Monitoring Problems
Modern strategies and technologies can address these challenges:
- Intelligent Alerting: Use AI to learn normal network behavior, prioritize alerts by business impact, and suppress redundant notifications to combat fatigue.
- End-to-End Visibility: Employ tools that track data flows from source to destination across hybrid environments for rapid root cause analysis.
- Centralized Platforms: Aggregate data from all locations into a single, unified interface to eliminate blind spots and simplify management.
- Data Aggregation and Filtering: Process and summarize data at the source to reduce the load on central systems and make insights more manageable.
- Dynamic Baselining: Leverage machine learning to automatically adjust performance baselines as your network changes, ensuring alerts remain relevant.
Frequently Asked Questions about Network Monitoring
What is the primary purpose of network monitoring?
The primary purpose of network monitoring management is to ensure business continuity by proactively maintaining network health and performance. It shifts IT teams from a reactive to a proactive stance by detecting and resolving issues before they impact users and cause costly downtime. The goal is to optimize performance and prevent outages, rather than just fixing things after they break.
How does network monitoring improve cybersecurity?
Network monitoring significantly improves cybersecurity by providing critical visibility. While not a primary security tool, it helps by:
Detecting Anomalies: Identifying unusual traffic patterns, such as large, unexpected data transfers, that could indicate a breach.
Identifying Unauthorized Devices: Spotting rogue devices that connect to the network, which could be a security risk.
Verifying Security Controls: Monitoring firewall rules and other security components to ensure they are functioning correctly.
Aiding Incident Response: Providing historical data and logs that are essential for investigating security incidents. This data is a key input for Cybersecurity Threat Detection systems.
Can you monitor hybrid environments (cloud and on-premise)?
Yes, monitoring hybrid environments is not only possible but essential for modern businesses. Most organizations use a mix of on-premises infrastructure and cloud services (like AWS or Azure). Without unified visibility across both, it's impossible to get a complete picture of network performance and security.
Modern network monitoring management tools are designed for this complexity. They use APIs to pull data from cloud providers and combine it with data from on-premises devices into a single, unified dashboard. This "single pane of glass" view is crucial for managing performance and troubleshooting issues in a distributed environment.
Conclusion
Effective monitoring provides the proactive visibility needed to prevent outages, optimize performance, and secure your infrastructure against evolving threats.
As we’ve covered, the right approach combines comprehensive data collection, intelligent analysis, and actionable alerting. The future of monitoring lies in AI and machine learning, which are turning reactive processes into predictive strategies by learning your network’s unique behavior to reduce alert fatigue and anticipate problems.
While challenges like network blind spots and data overload exist, they can be overcome with modern solutions that offer centralized platforms, intelligent alerting, and dynamic baselining.
At Concertium, we’ve spent nearly three decades mastering the complexities of network evolution. Our Collective Coverage Suite (3CS) leverages AI-improved observability and automated threat eradication to transform your monitoring from a simple tool into a strategic advantage.
Your network is the nervous system of your business. It deserves intelligent, comprehensive protection. Ready to gain the visibility and control your business needs? Learn how our approach to Managed IT: Network Monitoring & Management delivers true network intelligence and peace of mind.