Cybersecurity monitoring Tampa services are essential for local businesses facing an unprecedented wave of cyber threats. From small law firms to major healthcare systems, no one is immune.
The numbers paint a stark picture. Small businesses face 46% of all cyber attacks, yet most lack adequate protection. With data breaches costing an average of $4.45 million and taking 277 days to identify and contain, the financial impact can be devastating.
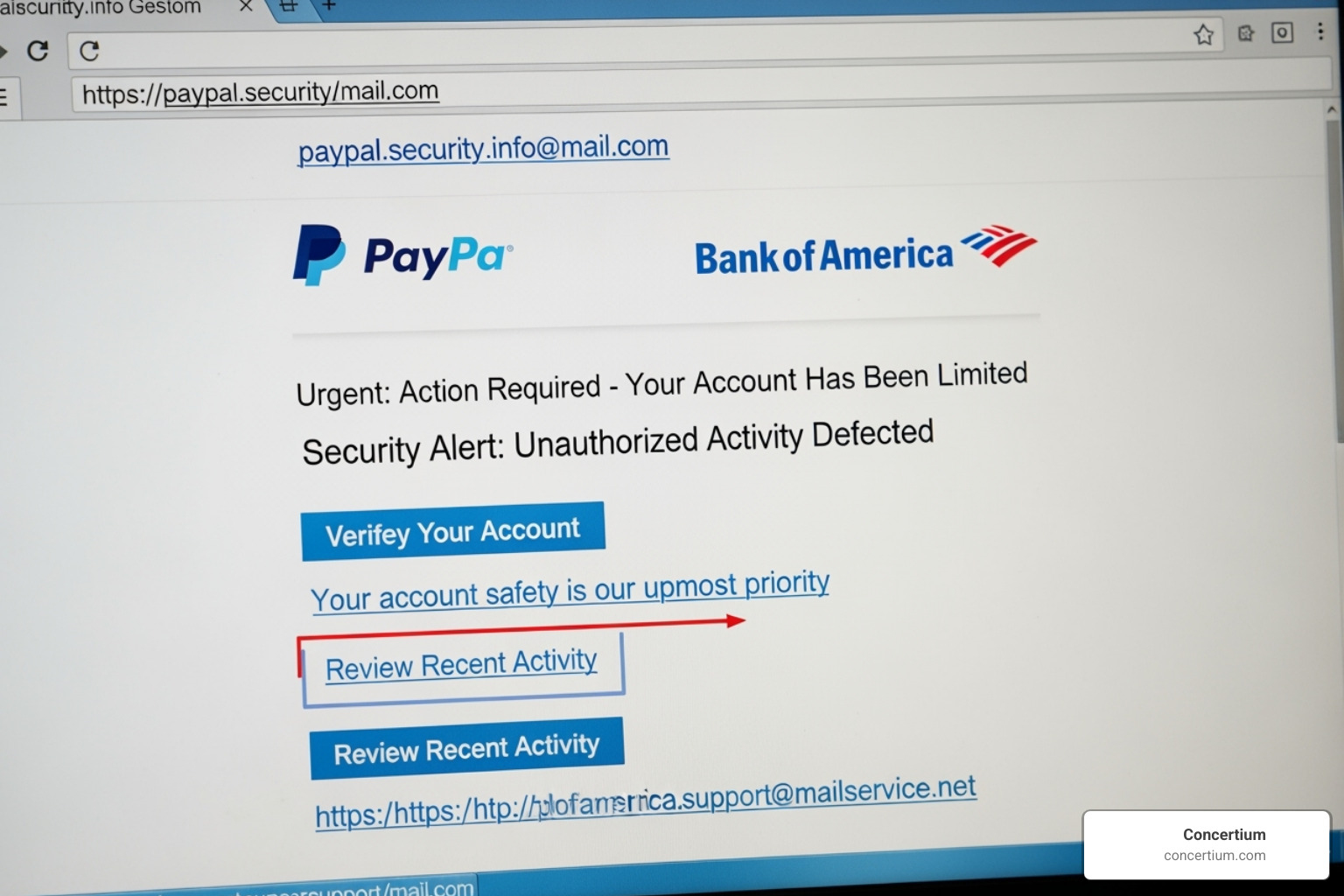
Human error accounts for 95% of cybersecurity breaches, making continuous monitoring critical. Tampa’s diverse economy, from healthcare to finance, creates attractive targets for cybercriminals who exploit underdeveloped security.
Without proper monitoring, 60% of small businesses close within six months of a major cyber incident. The good news is that proactive cybersecurity monitoring can neutralize threats before they cause significant damage. This allows business owners to focus on growth, not the next attack.
The Growing Cyber Threat Landscape for Tampa Businesses
Tampa’s vibrant economy and diverse industries make it a prime target for cybercriminals. Local businesses face a maze of digital dangers, from phishing attacks to devastating ransomware threats, which directly threaten their data, operations, and livelihood.
Nearly half of all cyber attacks (46%) target small businesses, often because they lack the robust security of larger corporations. A single data breach can cost a Tampa business millions, potentially forcing it to close. With 95% of breaches stemming from human error, professional cybersecurity monitoring Tampa services are essential. The sensitive data held by our local healthcare and financial sectors makes them especially attractive targets.
Primary Threats Facing Tampa’s Economy
The threats looming over Tampa businesses are real and have painful consequences.
- Data Theft: Cybercriminals seek sensitive customer information, intellectual property, and financial records to sell on the dark web or use in other scams. Breaches can lead to massive regulatory fines and reputational ruin.
- Financial Fraud: Attacks like wire transfer schemes and business email compromise (BEC) can empty company bank accounts in an instant.
- Business Disruption: Ransomware and denial-of-service (DoS) attacks can grind operations to a halt, causing significant financial loss and customer dissatisfaction.
- Reputational Damage: A cyber attack can destroy customer trust, which is difficult and sometimes impossible to rebuild.
- Supply Chain Attacks: Attackers compromise smaller, less secure vendors to gain a backdoor into larger, more lucrative corporate networks.
Why Small Businesses Are a Prime Target
Cybercriminals often prefer small and mid-sized businesses (SMBs) for several key reasons:
- Underdeveloped Security: Many SMBs lack large IT budgets or dedicated security teams, relying on basic tools that are insufficient against modern threats.
- Valuable Data: SMBs hold valuable customer lists, payment details, and proprietary information, making them attractive targets.
- Gateway to Larger Networks: Compromising an SMB can be a strategic entry point to attack their larger partners or clients.
- Human Error: With 95% of breaches caused by human error and often a lack of comprehensive training, SMB employees are more susceptible to phishing scams and other mistakes.
It’s not a matter of if your business will face a cyber threat, but when. The real question is whether you will be prepared.
Why 24/7 Cybersecurity Monitoring is a Modern Necessity
Relying on reactive cleanup after a cyberattack is a failed strategy. It takes an average of 277 days to find and contain a data breach, giving intruders months to lurk in your systems. This is why continuous cybersecurity monitoring Tampa services are essential for every modern business.
The Power of Proactive Threat Hunting vs. Reactive Cleanup
Proactive security is the difference between a minor issue and a business-ending event. Instead of waiting for an alarm, proactive threat hunting provides continuous vigilance, actively searching for suspicious activity and signs of trouble before they escalate into a crisis.
This approach also means identifying vulnerabilities before exploitation. Through vulnerability assessments, penetration testing, and dark web monitoring, we find and fix weaknesses before attackers can use them. By catching threats early, you significantly reduce downtime and costs. The investment in proactive monitoring is minimal compared to the staggering cost of cleaning up a major breach. Plus, it ensures your defenses are always armed with the latest threat intelligence.
Key Benefits of Continuous Cybersecurity Monitoring in Tampa
For Tampa businesses, the advantages of continuous cybersecurity monitoring Tampa services are transformative:
- Peace of Mind: Knowing experts are watching your digital assets 24/7 lets you stop worrying about cyber threats and focus on growing your business.
- Focus on Core Operations: It frees your in-house IT team from constant threat detection, allowing them to work on strategic projects that drive innovation.
- Data Protection: It shields your most valuable assets, including customer data, intellectual property, and financial records.
- Customer Trust: A strong commitment to cybersecurity shows customers their information is safe, building immense trust.
- Operational Efficiency: Preventing costly and disruptive incidents ensures your business runs smoothly without unexpected interruptions.
Core Components of a Robust Cybersecurity Monitoring Tampa Service
Effective cybersecurity monitoring services build a multi-layered fortress for your digital assets. At Concertium, our Collective Coverage Suite (3CS) integrates leading technology, smart processes, and human expertise for a holistic defense.
The Role of AI and Automation in Modern Monitoring
The volume and speed of modern cyber threats make it impossible for humans to keep up alone. Artificial Intelligence (AI) and automation are indispensable allies in cybersecurity monitoring Tampa, acting as tireless digital guardians. Our 3CS uses AI for improved observability, sifting through vast data to spot subtle patterns that signal a threat.
Once a threat is found, automated threat eradication provides faster response times by instantly blocking malicious activity or isolating a device. This minimizes damage and prevents minor issues from becoming crises. AI also helps reduce false positives and uses predictive analytics to anticipate future attacks, proactively strengthening your defenses.
Essential Services Offered by a Top-Tier Provider
A top-tier cybersecurity monitoring Tampa service combines AI with a team of human experts and proven security practices. Core components include:
- Managed Detection & Response (MDR): Provides 24/7 proactive threat hunting and rapid response to neutralize hidden dangers.
- Security Information and Event Management (SIEM): Centralizes and analyzes security data from your entire IT environment to identify incidents and support compliance.
- Vulnerability Assessments: Regular scans find weaknesses in your systems so they can be fixed before attackers exploit them.
- Penetration Testing: Ethical hackers simulate real-world cyberattacks to test your defenses and uncover hidden vulnerabilities.
- 24/7 Security Operations Center (SOC): A dedicated team of experts monitors your systems around the clock, providing human intelligence to analyze alerts and manage complex incidents.
- Dark Web Monitoring: Scans the dark web for compromised company credentials or data, providing an early warning of potential threats.
- Incident Response Planning: Helps you develop and test a plan to react swiftly and effectively to an incident, minimizing damage.
- Compliance Management: Assists in meeting strict regulatory requirements like HIPAA, PCI-DSS, and CMMC through proper log retention, reporting, and security controls.
- Employee Security Training: Educates your team on recognizing phishing, using strong passwords, and following security protocols to reduce human error.
- Virtual CISO (vCISO): Offers expert strategic guidance to develop long-term security policies that align with your business goals.
How to Choose the Right Cybersecurity Partner in Tampa
Choosing the right cybersecurity monitoring partner in Tampa is one of the most important decisions for your business. This partnership is key to protecting your future and giving you the peace of mind to focus on growth.
Evaluating a Cybersecurity Monitoring Tampa Provider
To find the right partner, evaluate providers based on these key criteria:
- Understanding of Your Needs: A great provider will listen and tailor services to your unique business, whether you’re in healthcare, finance, or another industry.
- Expertise and Experience: Look for a team with a solid history and deep knowledge. Concertium, for example, brings nearly 30 years of experience. Ask about their team’s certifications and experience with businesses like yours.
- Responsiveness and SLAs: A local presence is a plus, but guaranteed response times are critical. A top-tier provider will have clear Service Level Agreements (SLAs) for response and resolution.
- Certifications and Standards: Look for adherence to recognized standards like CMMC, SOC 2 Type II, or ISO 27001. These prove their commitment to high-level security practices.
- Client Testimonials: Check references and testimonials for feedback on reliability, effectiveness, and communication.
- Reporting and Scalability: A good partner provides clear reporting and analytics to keep you informed. Ensure their services are customizable and can scale as your business grows.
Understanding Costs and Measuring ROI
View cybersecurity not as an expense, but as an investment in your business’s safety.
First, understand the pricing models and ensure there are no hidden fees. Consider the total cost of ownership (TCO), including services like incident response or training.
The return on investment (ROI) is measured by key performance indicators (KPIs) like fewer security incidents, faster response times, and less downtime. However, the most compelling ROI is the cost of an avoided breach. A single breach can cost millions and force a business to close. Proactive monitoring prevents these catastrophic losses, making it far more cost-effective than reactive cleanup.
Meeting Compliance Demands with Continuous Monitoring
For many Tampa businesses, cybersecurity is also about meeting regulatory requirements. Failing to comply with rules like HIPAA, PCI-DSS, or CMMC can lead to hefty fines, legal trouble, and reputational damage. Continuous cybersecurity monitoring Tampa services are crucial for meeting these demands with confidence.
Tampa’s diverse industries must adhere to various regulations:
- HIPAA: For healthcare, monitoring tracks access to patient data, flags suspicious activity, and maintains records for audits.
- PCI-DSS: For businesses handling credit cards, monitoring secures the network and protects cardholder data.
- CMMC & ITAR: For DoD contractors, continuous monitoring, vulnerability management, and incident response planning are vital for meeting strict government standards.
A comprehensive monitoring service simplifies compliance. A SIEM solution automates log retention for audits, securely storing records and making them easily accessible. Real-time compliance alerts notify you immediately of any policy violations, allowing for quick remediation. Regular vulnerability reporting demonstrates a proactive commitment to security and helps close compliance gaps.
By implementing robust cybersecurity monitoring Tampa, your business can steer the complex world of regulations, avoid costly penalties, and focus on core operations.
Conclusion: Take the Proactive Step to Secure Your Tampa Business
The digital world offers Tampa businesses incredible opportunities, but it also brings serious threats like phishing and ransomware. The cost of a data breach is devastating, and reacting after the fact is no longer a viable strategy, especially when it takes an average of 277 days to even detect a breach.
Proactive cybersecurity monitoring Tampa is a modern necessity. Continuous, 24/7 vigilance allows threats to be neutralized swiftly, often before they cause real damage. This provides the peace of mind needed to focus on growing your business, not worrying about the next attack.
With nearly 30 years of experience, Concertium understands the challenges Tampa businesses face. Our Collective Coverage Suite (3CS) brings enterprise-grade, AI-improved security to your doorstep, automatically stopping threats before they escalate. We aim to be your trusted partner in security and compliance.
Your data, reputation, and future are too valuable to leave to chance. Don’t become another statistic—take the proactive step to secure your business today.
Why is cybersecurity so important for small businesses in Tampa?
Small businesses are prime targets for cybercriminals. 46% of all cyber attacks target SMBs because they often have underdeveloped security yet hold valuable data. The financial impact is staggering, with the average data breach costing millions. Tragically, 60% of small businesses close within six months of a major cyber incident. Beyond finances, the reputational damage can be impossible to repair. Cybersecurity monitoring Tampa services provide enterprise-grade protection that is essential for survival and growth.
What's the difference between antivirus software and a full monitoring service?
Antivirus software is reactive; it scans for known threats that are already on a device. A comprehensive cybersecurity monitoring Tampa service is proactive. It includes:
• Proactive Threat Hunting: Actively searching for suspicious behavior across your entire network, not just waiting for a known threat.
• 24/7 Human Oversight: A Security Operations Center (SOC) with experts who analyze alerts and respond intelligently to threats around the clock.
• Comprehensive Coverage: Protection for your entire digital environment, including networks, cloud applications, and email systems.
• Rapid Incident Response: Automated systems and human experts work together to contain threats in minutes, minimizing damage.
How quickly should a monitoring service respond to a threat?
In cybersecurity, every second counts. A professional cybersecurity monitoring Tampa service should respond to critical threats within minutes, not hours. This is essential for minimizing damage, as attackers can exfiltrate data or deploy ransomware very quickly. Look for providers with clear Service Level Agreements (SLAs) that guarantee fast response times. Automated containment is also crucial, as it can immediately isolate a threat while human experts develop a full remediation plan. 24/7 monitoring ensures this rapid response is available at any time, day or night.