AI cybersecurity management combines artificial intelligence with traditional security practices to protect organizations from cyber threats. It uses machine learning, behavioral analysis, and automated response systems to detect, prevent, and respond to attacks faster than humanly possible.
Key Components of AI Cybersecurity Management:
- Threat Detection: Real-time monitoring and pattern recognition
- Automated Response: Instant containment and mitigation of threats
- Behavioral Analysis: Identifying unusual user and system activities
- Predictive Analytics: Forecasting potential security risks
- Vulnerability Management: Continuous scanning and prioritization
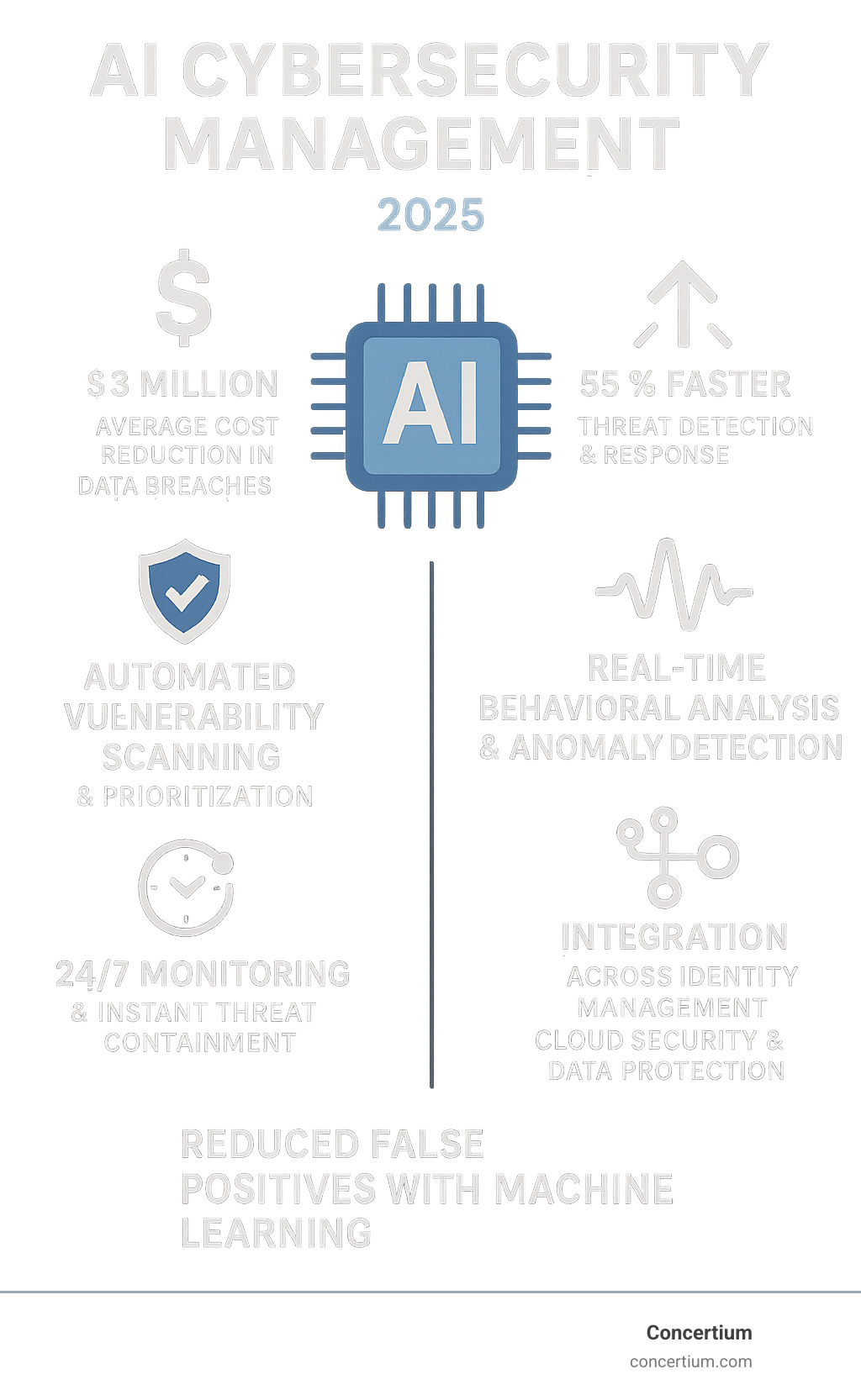
The numbers tell a compelling story. Organizations with fully deployed security AI and automation have experienced an average reduction of $3 million in data breach costs. AI-powered systems can accelerate alert investigations and triage by an average of 55%, while processing data volumes that humans simply cannot manage.
Imagine having a digital guardian that never sleeps, learns from every attack, and adapts faster than any human could. That’s exactly what AI brings to cybersecurity – the ability to stay ahead of threats that evolve at machine speed.
Today’s security teams face an impossible challenge: sophisticated hackers, an expanding attack surface, data explosion, and a critical shortage of cybersecurity professionals. Traditional security approaches that rely purely on human analysis and rule-based systems are no longer sufficient.
AI transforms this dynamic by automating routine tasks, reducing false positives, and identifying subtle patterns that indicate emerging threats. It doesn’t replace human expertise – it amplifies it, allowing security professionals to focus on strategic decisions while AI handles the heavy lifting of data analysis and initial threat response.
Simple guide to AI cybersecurity management terms:
What is AI in Cybersecurity and Why is it a Game-Changer?
Picture having a security guard who never gets tired, learns from every threat they encounter, and can analyze millions of data points in seconds. That’s essentially what AI cybersecurity management brings to modern organizations – intelligent protection that evolves faster than the threats it faces.
At its core, AI in cybersecurity uses smart algorithms and machine learning to detect, prevent, and respond to cyber threats at superhuman speeds. It’s like giving your security team a crystal ball combined with lightning-fast reflexes.
When we talk about AI in security, we’re really looking at three key technologies working together. Machine Learning forms the foundation – these algorithms learn what “normal” looks like in your network so they can instantly spot anything suspicious. Think of it as teaching your computer to recognize the difference between a friendly neighbor and an unwelcome intruder.
Deep Learning takes this further, using complex neural networks that mirror how our brains work. These systems excel at finding intricate patterns in massive amounts of data, making them perfect for catching sophisticated malware or brand-new attack methods that traditional systems would miss.
Natural Language Processing gives AI the ability to understand human language, allowing it to analyze threat reports, decode suspicious emails, or even scan chat logs for security clues. It’s like having a translator who speaks fluent “cyber threat.”
But why has AI become absolutely essential rather than just nice to have? The answer lies in a perfect storm of challenges that human analysts simply can’t handle alone anymore.
We’re drowning in data – generating and collecting more information than ever before. Meanwhile, our attack surface keeps expanding with more devices, cloud services, and remote workers creating new entry points for attackers. Traditional security approaches that rely on human analysis are like trying to drink from a fire hose while juggling.
This is where AI Improved Observability becomes a game-changer, giving security teams unprecedented visibility into their environments without overwhelming them with information they can’t process.
The reality is stark: cybercriminals are already using AI to make their attacks faster, smarter, and more targeted. Fighting AI-powered attacks with purely human defenses is like bringing a calculator to a supercomputer competition.
The Primary Benefits of AI-Powered Security
The change that AI brings to cybersecurity isn’t just impressive – it’s measurable in real dollars and dramatically improved security outcomes.
Cost reduction represents perhaps the most compelling benefit. Organizations that fully deploy security AI and automation see an average $3 million reduction in data breach costs. This isn’t just about preventing breaches; it’s about the incredible efficiency AI brings to investigations, response times, and resource allocation.
Operational efficiency gets a massive boost through automating routine security tasks. Instead of having skilled analysts manually configure firewalls, scan for vulnerabilities, or sort through thousands of alerts, AI handles these repetitive tasks. This frees up your human experts to focus on strategic thinking, complex threat hunting, and the nuanced decision-making that truly requires human insight.
One of the biggest pain points in traditional security – false positives – gets dramatically reduced with AI. Alert fatigue is real, and when security teams are constantly chasing false alarms, genuine threats can slip through the cracks. AI uses pattern recognition, anomaly detection, and contextual awareness to deliver fewer, but much more accurate alerts. Your team receives prioritized threats that actually matter, not just noise.
Scalability becomes effortless with AI-powered systems. As your organization grows and your attack surface expands, AI scales automatically without requiring proportional increases in human resources. It’s like having a security team that can instantly multiply its capacity when needed.
Perhaps most critically, faster response times can mean the difference between a minor incident and a catastrophic breach. AI-powered systems can accelerate alert investigations and triage by an average of 55%, turning hours of manual analysis into minutes of automated intelligence.
Defining AI Cybersecurity Management
AI cybersecurity management represents a fundamental shift from reactive, manual security to intelligent, adaptive defense. It’s the comprehensive approach of using artificial intelligence to create a security system that learns, evolves, and protects your organization around the clock.
Think of it as having proactive defense capabilities that work like a security consultant who never sleeps. AI continuously scans your environment, identifies potential weaknesses, and prioritizes vulnerabilities before attackers can exploit them. It finds shadow IT, finds unprotected sensitive data, and spots configuration issues that could become tomorrow’s headlines.
The reactive defense component kicks in when threats are detected or attacks are underway. AI doesn’t just sound alarms – it helps with rapid containment, guides eradication efforts, and supports recovery processes. It correlates seemingly unrelated activities into coherent incident timelines, helping your team understand not just what happened, but how and why.
Most importantly, AI cybersecurity management is about augmenting human experts, not replacing them. Your skilled analysts remain essential for strategic planning, complex decision-making, and the contextual understanding that only humans can provide. AI simply handles the heavy lifting of data analysis, alert prioritization, and routine responses.
This represents a crucial shift from manual, reactive security to an intelligent, automated, and proactive approach. The Role of AI and Machine Learning in Threat Detection shows how we’re moving beyond traditional signature-based detection to sophisticated behavioral and anomaly-based methods that can catch threats we’ve never seen before.
The result? A security posture that’s not just stronger, but smarter – one that learns from every attack attempt and gets better at protecting your organization over time.
Core Applications: How AI Actively Defends Your Organization
Think of AI cybersecurity management as your organization’s digital immune system – it’s constantly working behind the scenes, learning what’s normal and quickly spotting what’s not. Unlike traditional security tools that wait for known threats, AI actively hunts for suspicious patterns across every corner of your digital environment.
The beauty of AI lies in its ability to process and analyze massive amounts of data at lightning speed. While a human analyst might take hours to review network logs, AI can scan the same information in seconds, correlating seemingly unrelated events to paint a complete picture of potential threats.
Enhancing Threat Detection and Response
When it comes to spotting threats, AI transforms your security team from reactive firefighters into proactive threat hunters. Real-time analysis means AI is constantly watching your network traffic, user behavior, and system activities, establishing what security experts call a “baseline of normal behavior.”
Here’s where it gets interesting: AI doesn’t just look for known bad actors. Through anomaly detection, it spots unusual patterns that might indicate a zero-day attack or insider threat. Maybe an employee is accessing files they’ve never touched before, or data is flowing to an unexpected location. These subtle changes often signal the early stages of an attack.
User and entity behavior analytics (UEBA) takes this concept even further by analyzing not just what users do, but how they do it. The system learns that Sarah from accounting typically logs in at 8 AM from her office computer, so when someone tries to access her account at 3 AM from halfway across the world, red flags go up immediately.
The pattern recognition capabilities of AI are truly remarkable. It can connect dots across thousands of events that would overwhelm human analysts. Our Cybersecurity Predictive Analytics Game Changers leverage this ability to not just detect current threats, but forecast where the next attack might come from.
When threats are detected, speed becomes critical. AI accelerates investigations and triage by an average of 55%, automatically gathering context, generating incident summaries, and even initiating containment measures. This rapid response through Automated Threat Detection can mean the difference between a minor security incident and a major data breach.
Proactive Risk and Vulnerability Management
The best defense is often a good offense, and this is where AI truly shines in vulnerability management. Rather than waiting for attackers to find weaknesses, AI continuously scans your entire digital ecosystem, from network configurations to cloud applications.
Automated scanning goes beyond simple vulnerability detection – it’s about smart prioritization. AI analyzes thousands of potential vulnerabilities and ranks them based on actual risk to your organization. Not all vulnerabilities are created equal, and AI helps you focus on the ones that matter most. Our experts can help you analyze and fix vulnerabilities using intelligent automation.
One of the biggest headaches for IT teams is Shadow IT – those unauthorized apps and devices that employees use without approval. AI acts like a digital detective, analyzing network traffic patterns to identify unknown devices and cloud applications that might be flying under the radar. It’s like having X-ray vision for your network infrastructure.
AI also excels at finding unprotected sensitive data that might be lurking in forgotten databases or misconfigured cloud storage. By understanding your network traffic patterns over time, AI can recommend the right security policies and help ensure your most valuable information stays protected.
The Role of Generative AI in Advanced Defenses
Generative AI is the new frontier in cybersecurity, bringing capabilities that sound almost like science fiction. Attack simulation allows security teams to test their defenses against realistic cyber attacks without putting actual systems at risk. It’s like having a sparring partner that can throw every possible punch.
Synthetic data generation solves a tricky problem in cybersecurity training. When you need to train AI models but can’t use real sensitive data, generative AI creates realistic but fake datasets that maintain the statistical properties of your actual data without the privacy risks.
The automation of incident response playbooks represents a major leap forward. Generative AI can create customized response scripts based on the specific nature of each incident, allowing security teams to automate containment and recovery steps that previously required manual intervention.
Advanced phishing attacks detection has become increasingly important as cybercriminals use AI to create more convincing fake emails. Generative AI fights fire with fire, analyzing email content, links, and attachments with sophisticated understanding that goes beyond traditional spam filters.
Our Applications of AI in Threat Intelligence showcase how generative AI can synthesize threat data from multiple sources into actionable intelligence reports, giving security teams the insights they need to stay ahead of emerging threats.
Securing Key Domains: IAM, Cloud, and Data Security
Identity and Access Management (IAM) becomes infinitely smarter with AI. Instead of relying solely on passwords and permissions, AI continuously monitors user behavior patterns. It learns that John from marketing typically accesses customer databases during business hours, so when his account starts downloading gigabytes of data at midnight, the system knows something’s wrong.
Cloud security presents unique challenges because cloud environments are dynamic and complex. AI helps by continuously monitoring cloud configurations, spotting misconfigurations that could create vulnerabilities, and protecting workloads across different cloud providers. It’s like having a security guard who never sleeps and can be in multiple places at once.
Data security relies heavily on AI for classification and protection. The system learns to identify different types of sensitive information – from credit card numbers to intellectual property – and monitors how this data moves through your organization. Data Loss Prevention becomes proactive rather than reactive, stopping unauthorized data transfers before they happen rather than just alerting you after the fact.
The integration of AI across these domains creates a comprehensive security posture that adapts and evolves with your organization’s needs. It’s not just about having better tools – it’s about having smarter defenses that learn and improve over time.
A Practical Guide to Implementing AI Cybersecurity Management
Implementing AI cybersecurity management isn’t just about buying new tools; it’s about changing how your organization thinks about security. Think of it like renovating your home’s security system – you wouldn’t just bolt on a smart lock without considering how it works with your existing alarms, cameras, and monitoring systems.
The journey requires careful planning, strategic thinking, and a healthy dose of patience. Many organizations rush into AI adoption, only to find themselves overwhelmed by complexity or disappointed by results that don’t match their expectations.
Strategic Implementation Steps
Successfully integrating AI into your cybersecurity framework starts with understanding that this is a marathon, not a sprint. The most effective approach begins with developing a clear strategy that defines exactly what problems you’re trying to solve. Are you drowning in false alerts? Struggling with slow threat response times? Need better vulnerability prioritization? Your strategy should align AI investments with your specific security pain points.
Data quality and quantity form the foundation of any successful AI deployment. Your AI models are only as smart as the information they learn from – feed them poor-quality data, and you’ll get unreliable results. This means collecting comprehensive datasets including network logs, endpoint data, threat intelligence, and user activity records. Don’t forget to ensure your Data Loss Prevention (DLP) systems can handle all this incoming information effectively.
Tool integration is where many organizations stumble. AI works best when it can see the big picture, which means connecting it with your existing Security Information and Event Management systems and security operations centers (SOCs). This comprehensive view allows AI to spot patterns and connections that might be invisible when looking at isolated data sources.
Smart organizations accept phased adoption – starting small with pilot projects and gradually expanding AI’s role as teams gain confidence and experience. This approach lets you learn from early implementations, fine-tune your processes, and build internal expertise before rolling out AI across your entire security infrastructure.
Perhaps most importantly, maintain human-in-the-loop oversight throughout your implementation. While AI excels at processing vast amounts of data and identifying patterns, human experts remain essential for validating decisions, interpreting complex alerts, and handling situations requiring nuanced judgment. Our AI Improved Advanced Observability solutions are specifically designed to improve this crucial collaboration between human expertise and machine intelligence.
Best Practices for Ethical and Effective AI Cybersecurity Management
As we harness AI’s power, we must address the ethical considerations that come with this technology. It’s not enough to simply deploy AI – we need to deploy it responsibly.
Transparency and explainability should be non-negotiable requirements for your AI systems. When an AI flags something as malicious, your team needs to understand the reasoning behind that decision. This isn’t just about trust – it’s crucial for debugging issues, meeting compliance requirements, and learning from both successes and mistakes.
Accountability means establishing clear lines of responsibility for AI actions and outcomes. When an AI system makes an error (and they will), you need processes in place to understand what went wrong and who’s responsible for addressing it. This clarity prevents the dangerous “black box” scenario where no one takes ownership of AI decisions.
Avoiding bias requires ongoing vigilance. AI models can inadvertently learn biases from their training data, leading to unfair or inaccurate outcomes. Regular testing and monitoring help identify these issues before they impact your security posture. AI should augment human decision-making, not replace it entirely – especially in situations where bias could lead to unfair treatment.
Data privacy becomes even more critical when AI systems process vast amounts of information, including personal and sensitive data. Implement robust data governance practices, including encryption and secure coding standards, to protect this information and comply with privacy regulations.
Continuous testing and monitoring ensures your AI models stay effective as threats evolve. Just like traditional security tools need regular updates, AI systems require ongoing retraining and performance evaluation. This vigilance helps identify performance degradation and emerging biases before they compromise your security.
Finally, align your practices with established frameworks and guidelines. The NIST AI Risk Management Framework provides comprehensive guidance for managing AI-related risks, while the Guidelines for Secure AI System Development offer practical advice for building secure AI systems. Consider the broader implications outlined in Engaging with Artificial Intelligence to ensure your practices align with global best practices and established cybersecurity frameworks.
The Double-Edged Sword: Risks, Challenges, and Future Trends
Understanding the challenges and future direction of AI in cybersecurity is crucial for long-term strategy. While AI offers tremendous protective capabilities, it’s a double-edged sword – the same technology that helps us defend can also be weaponized against us.
Think of it this way: if AI makes our security teams smarter and faster, it’s doing the same thing for cybercriminals. This reality doesn’t diminish AI’s value in cybersecurity; instead, it underscores why we need to approach AI cybersecurity management with both enthusiasm and caution.
The rapid advancement of AI has opened new attack vectors that we couldn’t have imagined just a few years ago. Adversaries are already leveraging AI to create more sophisticated and targeted attacks, bringing unprecedented speed, insight, automation, and imitation to their criminal toolkits.
Adversarial AI represents perhaps our most significant challenge. Cybercriminals are becoming increasingly clever about manipulating AI systems themselves. Data poisoning attacks involve feeding malicious or corrupted information to AI models during their training phase, essentially teaching them to make wrong decisions. It’s like poisoning a well – the contamination spreads throughout the entire system.
Model evasion takes a different approach, where attackers craft inputs specifically designed to slip past AI-powered detection systems. They might create malware that adapts and evolves in real-time, staying just one step ahead of our AI defenders. These attacks exploit the very pattern recognition that makes AI so powerful in the first place.
Perhaps most concerning is the rise of AI-powered social engineering. Generative AI can now create incredibly convincing deepfakes – fake audio and video that can impersonate anyone. Imagine receiving a video call from your CEO asking you to transfer funds, only to find later it was entirely AI-generated. These sophisticated phishing attacks are becoming harder to detect with each passing month.
Beyond adversarial threats, we face practical implementation challenges. Implementation complexity can be overwhelming for organizations without the right expertise. Integrating AI solutions with legacy systems often feels like trying to connect a smartphone to a rotary phone – technically possible, but requiring significant adaptation.
The cybersecurity skills gap compounds these challenges. While AI helps us handle routine tasks, we now need professionals who understand both cybersecurity and AI technologies. Finding these hybrid experts is like searching for unicorns – they exist, but they’re rare and highly sought after.
We must also consider securing the lifecycle of an AI system itself. AI systems can become targets, requiring us to protect everything from data collection and model training to deployment and maintenance. It’s security all the way down.
The Future of AI in Cybersecurity
Looking ahead, the landscape of AI cybersecurity management will continue evolving at breakneck speed. Our 2025 CYBER THREAT PREDICTIONS paint a picture of increasingly sophisticated threats, but also more powerful defensive capabilities.
AI-powered attacks will become more targeted and evasive as AI tools become accessible to more threat actors. We’re already seeing this trend accelerate, with attackers using AI to automate reconnaissance, craft personalized phishing emails, and even generate new malware variants on demand.
The emergence of quantum-safe security represents both a challenge and an opportunity. While quantum computing poses a future threat to traditional encryption methods, AI will play a crucial role in developing and implementing quantum-resistant cryptographic solutions. We’re essentially in an arms race between quantum computing capabilities and quantum-safe defenses.
Hyperautomation will transform how we think about security operations. We’ll see AI-powered agents taking on increasingly autonomous roles, handling complex detection and response tasks that currently require human intervention. These digital security guards will work around the clock, learning and adapting to new threats in real-time.
AI red teaming will become standard practice for forward-thinking organizations. Just as we use penetration testing today, we’ll use AI to continuously probe our own defenses, identifying weaknesses before malicious actors can exploit them. It’s like having a friendly hacker on staff who never sleeps and never gets bored.
Perhaps most importantly, the future belongs to human-AI collaboration. We won’t see AI replacing cybersecurity professionals; instead, we’ll see the emergence of hybrid roles where humans and AI work together seamlessly. Security professionals will focus on strategic thinking, complex decision-making, and nuanced threat hunting, while AI handles data analysis, pattern recognition, and routine responses.
This collaborative approach is central to the Future of Cybersecurity. Our Future Trends in AI Improved Advanced Observability emphasize this blend of human expertise and machine intelligence, creating a defense strategy that’s stronger than either could achieve alone.
The key to thriving in this future is maintaining that balance – embracing AI’s capabilities while never losing sight of the human judgment, creativity, and ethical reasoning that remain irreplaceable in cybersecurity.
Frequently Asked Questions about AI in Cybersecurity
Will AI replace cybersecurity professionals?
Absolutely not, and here’s why this concern, while understandable, misses the bigger picture. AI cybersecurity management is fundamentally designed to work with human experts, not against them.
Think of AI as the ultimate research assistant that never gets tired. It handles the repetitive, data-intensive grunt work – sifting through millions of log entries, correlating threat patterns, and generating initial reports. This frees up our cybersecurity professionals to focus on what humans do best: strategic analysis, complex threat hunting, and nuanced decision-making.
The reality is that many cybersecurity roles won’t disappear – they’ll evolve and become more interesting. Instead of spending hours manually reviewing alerts, security analysts can focus on investigating sophisticated threats, developing security strategies, and making critical decisions that require human judgment and experience.
AI will likely assist in decision-making rather than making decisions independently. Humans handle the key strategic choices while AI manages the routine analysis and reporting. This partnership approach actually makes cybersecurity professionals more valuable, not less.
How does AI handle new, unknown threats (zero-day attacks)?
This is where AI truly shines, and it’s one of the most exciting aspects of AI cybersecurity management. Unlike traditional security systems that rely on known threat signatures (basically a “wanted poster” approach), AI takes a completely different strategy.
AI establishes a baseline of what “normal” looks like in your organization. It learns your network traffic patterns, user behaviors, application activities, and system operations. Once this baseline is established, AI becomes incredibly good at spotting anything that deviates from normal – even if it’s never seen that specific threat before.
For example, if a zero-day attack causes unusual data transfers at 3 AM or creates abnormal network connections, AI will flag this suspicious behavior immediately. User and entity behavior analytics (UEBA) enable AI to analyze the activity of devices, servers, and users, helping identify anomalous behavior that could indicate a zero-day attack.
This behavioral analysis approach means AI can detect novel attacks as they happen, rather than waiting for security researchers to identify and catalog new threats. It’s like having a security guard who notices when something just “feels off,” even if they can’t immediately identify what’s wrong.
Is it safe to fully automate cybersecurity with AI?
The short answer is no, and any cybersecurity expert worth their salt will tell you the same thing. Full automation is not recommended – and honestly, it’s not even desirable.
Here’s the reality: a “human-in-the-loop” approach is essential for effective cybersecurity. While AI excels at processing data and identifying patterns, human oversight remains critical for several key reasons.
Human judgment is irreplaceable when it comes to validating high-stakes decisions, interpreting nuanced contexts, and ensuring ethical application of security measures. AI might flag something as suspicious, but humans need to determine the appropriate response – especially when that response could impact business operations or employee access.
Most organizations today trust AI with routine tasks like initial threat detection, log analysis, and basic incident categorization. However, deeper integration and more autonomous decision-making require extensive training, more comprehensive input data, and specialized expertise that many companies are still developing.
Think of it this way: you wouldn’t want your car to drive itself without any way for you to take control when needed. The same principle applies to cybersecurity – AI should improve human capabilities, not replace human judgment entirely.
Conclusion: Securing Your Future with AI-Powered Defense
The change is already happening. AI cybersecurity management has moved from the field of science fiction into the boardrooms and server rooms of forward-thinking organizations worldwide. What we’ve explored throughout this guide isn’t just theoretical – it’s the new reality of digital defense.
Think about where we started: traditional security approaches struggling against an avalanche of threats, overwhelmed human analysts, and attack surfaces expanding faster than we could protect them. Now imagine having an intelligent guardian that never sleeps, learns from every attack, and adapts at machine speed. That’s not tomorrow’s promise – that’s today’s possibility.
The numbers speak for themselves. Organizations implementing comprehensive AI security solutions are seeing $3 million reductions in data breach costs and 55% faster threat detection and response times. But beyond the statistics lies something even more valuable: the peace of mind that comes from knowing your defenses are as intelligent and adaptive as the threats they face.
What makes AI truly in cybersecurity isn’t just its ability to process massive amounts of data or detect patterns humans might miss. It’s the way it amplifies human expertise rather than replacing it. Your security professionals become strategic commanders rather than data analysts, focusing on high-level decisions while AI handles the heavy lifting of monitoring, analysis, and initial response.
The path forward requires more than just purchasing AI tools – it demands a strategic approach that balances cutting-edge technology with human wisdom. We’ve seen how successful implementation involves careful planning, ethical considerations, and that crucial “human-in-the-loop” oversight that ensures accountability and prevents costly mistakes.
Yes, challenges exist. Adversarial AI, implementation complexity, and the evolving threat landscape all present problems. But organizations that accept AI cybersecurity management today are building resilience for tomorrow’s unknown threats. They’re not just keeping up with cybercriminals – they’re staying ahead of them.
The future of cybersecurity isn’t about choosing between human expertise and artificial intelligence. It’s about creating a powerful partnership where technology handles what it does best – speed, scale, and pattern recognition – while humans provide the strategic thinking, ethical oversight, and nuanced decision-making that complex security challenges demand.
Your organization’s digital future depends on the security decisions you make today. The threat landscape will only grow more complex, the volume of data will continue expanding, and the stakes will keep rising. But with AI-powered defense systems, you’re not just protecting your current assets – you’re building an adaptive shield that evolves with every new challenge.
Ready to transform your cybersecurity posture? Leading cybersecurity companies in Tampa like Concertium are already pioneering the future of AI-improved security. With nearly three decades of expertise and innovative solutions like the Collective Coverage Suite (3CS), they’re helping organizations just like yours turn AI cybersecurity management from a competitive advantage into an essential foundation for digital success.
The question isn’t whether AI will reshape cybersecurity – it already has. The question is whether your organization will lead this change or be left trying to catch up.