24/7 cybersecurity monitoring is the continuous process of observing, analyzing, and responding to security threats across your IT infrastructure around the clock. It involves real-time threat detection, immediate incident response, continuous vulnerability assessment, and expert oversight from a dedicated Security Operations Center (SOC) team.
The core benefits are clear: it reduces threat detection time from days to minutes, helps prevent attacks that happen outside business hours, ensures regulatory compliance (HIPAA, PCI DSS), and minimizes business disruption and financial losses.
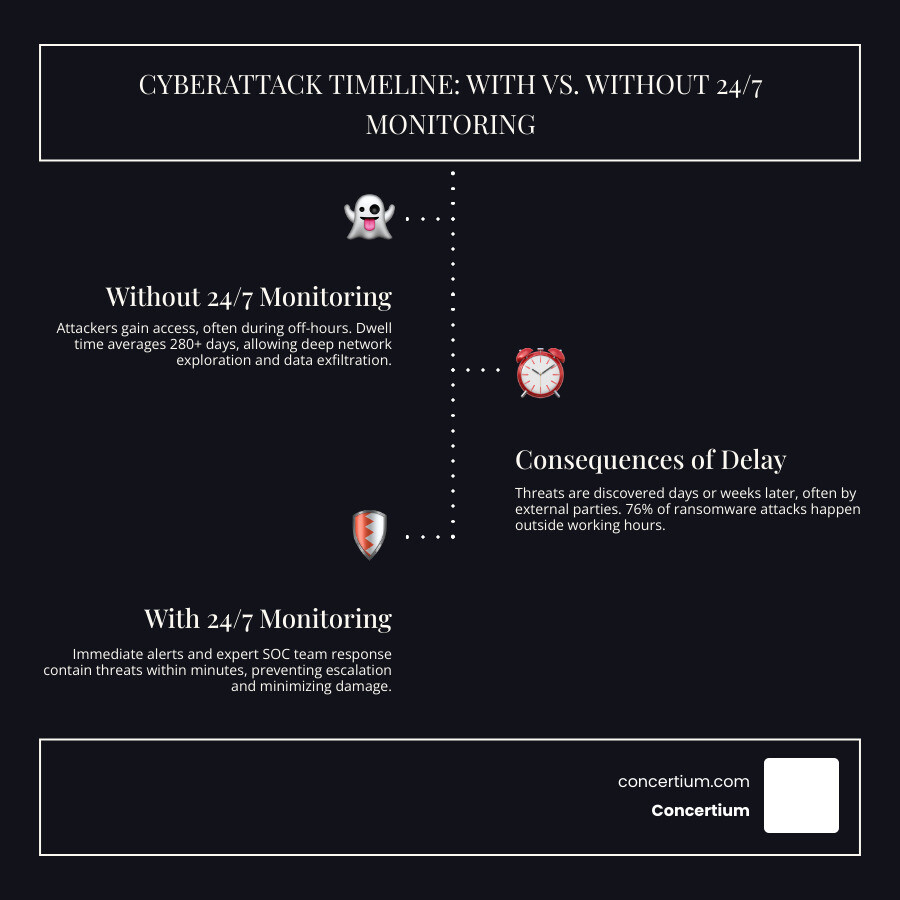
Imagine finding a cyberattack 48 hours after it began because your IT team was offline for the weekend. This delay could be catastrophic, yet it’s a common scenario for businesses with 9-to-5 security.
Cybercriminals never sleep. They deliberately target off-hours when businesses are most vulnerable. Research shows that 76% of enterprise ransomware infections happen outside of working hours. The financial stakes are enormous, with cyber attack losses reaching $16.6 billion in 2024. Worse, a hacker can remain undetected in a network for more than 280 days, giving them ample time to plan devastating attacks.
For mid-sized businesses facing the same sophisticated threats as large enterprises but with fewer resources, 24/7 monitoring is not just beneficial—it’s essential for survival.
24/7 cybersecurity monitoring vocab to learn:
Why 24/7 Monitoring is Non-Negotiable in Today’s Threat Landscape
The harsh reality is that cybercriminals don’t take weekends off. They are professionals who operate like businesses, and they know the best time to strike is when nobody’s watching. The shift to remote work and cloud adoption has expanded the attack surface, giving these criminals more entry points than ever before.
A staggering 76% of enterprise ransomware infections happen outside of working hours. This isn’t a coincidence—it’s a calculated strategy to exploit gaps in traditional security coverage. Three out of four successful ransomware attacks occur when security teams have gone home for the day.
24/7 cybersecurity monitoring transforms your security from reactive to proactive. Instead of finding an attack on Monday morning, you catch threats as they emerge. This continuous vigilance doesn’t just reduce risk; it allows your team to focus on business growth instead of firefighting security incidents. Our Real-Time Threat Detection services make this level of protection accessible to businesses of all sizes.
The Critical Difference: 9-to-5 vs. Round-the-Clock Protection
Traditional 9-to-5 security monitoring creates predictable windows of vulnerability that cybercriminals exploit. An attacker who infiltrates your network at 6 PM on a Friday has over 60 hours of uninterrupted access before your team returns on Monday morning.
The difference between part-time and full-time protection is dramatic:
| Feature | 9-to-5 Monitoring | 24/7 Monitoring |
|---|---|---|
| Coverage | Limited to business hours, significant off-hours gaps | Continuous, round-the-clock protection |
| Vulnerability | High risk during nights, weekends, and holidays | Significantly reduced risk due to constant vigilance |
| Detection | Delayed detection, often hours or days after an event | Real-time detection, often within minutes of an incident |
| Response | Slow and reactive, waiting for staff to return | Immediate and proactive, with rapid containment and remediation |
| Impact | Higher potential for widespread damage, data loss, and business disruption | Minimized damage, faster recovery, and reduced financial and reputational harm |
| Compliance | Difficult to prove continuous adherence to regulations | Easier to meet and demonstrate ongoing compliance with regulatory standards |
With round-the-clock monitoring, threats are identified and contained before they can establish a foothold, preserving your operational integrity. This continuous oversight also helps you meet compliance standards like HIPAA, PCI DSS, and GDPR by providing documented evidence of ongoing data protection.
Slashing Response Times: The Impact on MTTD and MTTR
In cybersecurity, time is everything. Two critical metrics illustrate why speed matters: Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Without continuous monitoring, MTTD can be alarmingly high. The average hacker dwell time is 280 days—nearly ten months of undetected access. MTTR measures how quickly you can contain a threat once it’s found. Every minute an attacker remains active increases the potential for data theft and system compromise.
24/7 cybersecurity monitoring dramatically compresses both timeframes. Threats are identified in minutes, not months, and response is immediate. This speed minimizes damage and business disruption. Quick detection and response can be the difference between a minor incident and a company-threatening breach. Our Incident Response capabilities ensure threats are neutralized swiftly and completely, protecting you from the multi-million dollar costs of a major data breach.
The Anatomy of an Effective 24/7 Cybersecurity Monitoring Strategy
An effective 24/7 cybersecurity monitoring strategy harmonizes people, processes, and technology to provide complete visibility and protection. At its core is the SOC Visibility Triad, a foundational model that ensures stability and comprehensive coverage.
The triad combines people (skilled security analysts), process (established procedures), and technology (monitoring tools). The technology side centers on three key components: SIEM (Security Information and Event Management) for centralized data analysis, EDR (Endpoint Detection and Response) for device-level visibility, and NDR (Network Detection and Response) for monitoring network traffic. Together, these elements provide a unified view of your security posture, enabling rapid threat detection and response. This integrated approach is the foundation of our Threat Detection and Response solutions.
Core Technologies That Power Continuous Defense
The technology stack behind 24/7 cybersecurity monitoring works in concert to keep your business safe.
- SIEM (Security Information and Event Management): Acts as the central nervous system, collecting and analyzing log data from across your IT infrastructure to identify meaningful threats.
- EDR & XDR (Endpoint/Extended Detection and Response): EDR focuses on laptops, servers, and mobile devices, watching for suspicious behavior. XDR extends this visibility across your network, cloud, and email for a more complete picture.
- IDS & IPS (Intrusion Detection/Prevention Systems): Serve as network security guards. IDS solutions alert on suspicious traffic, while IPS systems actively block threats in real-time.
- NDR (Network Detection and Response): Provides comprehensive visibility into network traffic, using behavioral analytics to spot anomalies that might indicate a novel attack.
- Vulnerability Scanning Tools: Regularly check your systems for known weaknesses and misconfigurations, identifying potential problems before attackers can exploit them.
Our Managed Detection and Response (MDR) services integrate these technologies into a cohesive, round-the-clock defense system.
The Human Element: Roles and Responsibilities
Technology is crucial, but human expertise brings it to life. A Security Operations Center (SOC) is typically organized in tiers:
- Tier 1 Analysts: The first line of defense, monitoring alerts and escalating credible threats.
- Tier 2 Analysts: Conduct deeper investigations into escalated incidents to determine the scope and begin containment.
- Tier 3 Analysts: Elite security experts and threat hunters who proactively search for hidden threats and lead complex incident response efforts.
Beyond the analysts, incident responders coordinate the overall response, while the CISO (Chief Information Security Officer) provides strategic leadership. However, building and retaining an in-house team is challenging due to high staff burnout and a severe talent shortage, with 57% of organizations reporting risk due to difficulty finding qualified professionals. This makes managed security services a vital option for many businesses.
The Role of Threat Intelligence and Automation
Effective 24/7 cybersecurity monitoring must be proactive. Threat intelligence provides an early warning system, using information from global threat feeds about emerging threats and attacker tactics. This allows security teams to anticipate attacks, hunt for hidden threats, and prioritize defenses.
Automation is essential for managing the immense volume of security data. Our Automated Threat Detection systems use AI-improved observability to process millions of alerts, achieving a 75% reduction in false positives. This allows our human analysts to focus on real threats. Automation also enables immediate responses, such as blocking malicious IPs or isolating compromised endpoints, buying valuable time for analysts to investigate.
Overcoming Implementation Problems
Setting up 24/7 cybersecurity monitoring can feel overwhelming, with common concerns around cost, complexity, and personnel. However, with the right strategic planning, these challenges are manageable. A solid Vulnerability Risk Management strategy provides a clear blueprint, helping you prioritize what matters most and tackle problems in the right order.
Tackling Common Challenges: Cost, Complexity, and Skills Gaps
Organizations often face several key roadblocks when implementing 24/7 cybersecurity monitoring.
- Budget constraints: Building an in-house Security Operations Center (SOC) is expensive, requiring significant investment in tools, infrastructure, and salaries.
- Complexity and Tool Sprawl: Managing a mix of on-premises, cloud, and remote systems with multiple disconnected security tools creates complexity and dangerous blind spots.
- Alert Fatigue: Security tools can generate thousands of daily alerts. Without proper tuning, real threats can be lost in the noise, overwhelming security teams.
- Cybersecurity Talent Shortage: Finding and retaining qualified professionals is a major challenge. As noted, 57% of organizations face significant risk due to this talent shortage.
- Scalability: As a business grows, its IT environment becomes more complex, and monitoring needs expand exponentially.
We help organizations build solutions that fit their current needs and budget, offering managed services that provide enterprise-grade protection without the associated headaches and that can scale as they grow.
Ensuring Compliance Through Continuous Monitoring
For any business handling sensitive data, compliance with regulations like HIPAA, PCI DSS, GDPR, and SOC 2 is a legal requirement. 24/7 cybersecurity monitoring is critical not just for preventing attacks, but for proving to regulators that you are serious about data protection.
Continuous monitoring creates an automatic audit trail, logging every security event, investigation, and response. When an audit occurs, you can easily generate audit-ready reports that demonstrate how you meet specific compliance requirements. This documentation proves you are continuously protecting sensitive information.
More importantly, this constant oversight helps you catch and remediate compliance gaps before they become major violations finded during an audit. It transforms compliance from a stressful, periodic event into an ongoing, manageable process that strengthens your overall security posture. For more guidance, see our insights on Cybersecurity Compliance.
Building Your Defense: In-House SOC vs. Outsourced MSSP
When implementing 24/7 cybersecurity monitoring, you face a critical decision: build an in-house Security Operations Center (SOC) or partner with a Managed Security Service Provider (MSSP)? This choice depends on your budget, team capabilities, and strategic focus.
The decision requires a careful cost-benefit analysis and consideration of how to best allocate your resources. Whether you choose an in-house approach or partner with us through our specialized 24/7 SOC Services and Managed IT Services, we’re here to support your security goals.
The Case for an In-House Security Operations Center
Some organizations, particularly large enterprises, may prefer to build their own SOC. The primary advantages are total control over security tools and processes and deep cultural alignment, as an internal team understands the business intimately.
However, the challenges are significant. The high initial investment in infrastructure, software, and training can be staggering. The biggest hurdle is staffing. Building a 24/7 team requires hiring 8-10 highly skilled analysts in a competitive market where a 57% talent shortage creates major risks for organizations. Retaining this team and preventing burnout is another constant challenge.
The Advantages of Partnering with a Managed Security Service Provider (MSSP)
For most mid-sized businesses, partnering with an MSSP for 24/7 cybersecurity monitoring is the more strategic choice. The trend is clear: 40% of midsize enterprises used MDR as their only managed security service in 2024, with this figure expected to reach 50% by 2025.
Partnering with an MSSP solves the major challenges of the in-house model:
- Cost-effectiveness: You gain access to enterprise-grade tools and experts for a predictable monthly cost, avoiding massive capital expenditures.
- Access to Experts: MSSPs provide immediate access to entire teams of specialized professionals, including threat hunters and incident responders.
- Advanced Technology: MSSPs invest heavily in cutting-edge security platforms, threat intelligence, and AI-powered tools that are constantly updated.
- Scalability: Services can be easily scaled up or down as your business needs change.
- Focus on Core Business: Outsourcing security allows your internal teams to concentrate on innovation and growth.
Our Managed Cybersecurity Services deliver enterprise-grade protection through our unique Collective Coverage Suite (3CS) with AI-improved observability and automated threat eradication. With nearly 30 years of expertise, we provide robust security without the burden of managing it yourself, reducing breach risk and increasing productivity.
Frequently Asked Questions about 24/7 Cybersecurity Monitoring
Here are answers to the most common questions business owners have about 24/7 cybersecurity monitoring.
What is the primary goal of 24/7 cybersecurity monitoring?
The primary goal is to continuously watch over your organization’s entire IT environment to detect, analyze, and respond to threats in real-time. It’s a complete cycle designed to shrink the critical window between when a threat appears and when it is neutralized—from weeks or months down to minutes. This proactive approach minimizes damage, prevents business disruption, and stops attacks like ransomware before they can take hold.
What types of threats can 24/7 monitoring detect?
24/7 cybersecurity monitoring is designed to detect a wide range of threats by analyzing network traffic, endpoint activity, and user behavior. This includes:
- Malware and ransomware, identified through unusual file behavior and network communications.
- Phishing attacks, flagged via email and web traffic analysis.
- Unauthorized access, both from external attackers and internal users, by tracking suspicious login patterns.
- Insider threats, spotted by using behavioral analytics to identify actions outside of normal patterns.
- Data exfiltration (data theft), detected by monitoring unusual data transfers.
- Zero-day vulnerabilities (new attack methods), caught through behavioral analysis rather than relying on known threat signatures.
How does 24/7 monitoring help with regulatory compliance?
24/7 cybersecurity monitoring is essential for meeting the requirements of regulations like GDPR, HIPAA, and PCI DSS. These frameworks require organizations to prove they are actively protecting sensitive data.
Continuous monitoring provides the documented evidence of security controls that auditors require. Every security event, investigation, and response is logged, creating comprehensive, audit-ready reports. It also ensures you can meet mandated incident response timeframes. By continuously identifying and addressing security gaps, monitoring transforms compliance from a stressful periodic event into an ongoing, manageable process that strengthens your security.
Secure Your Business Around the Clock
Cyber threats never take a break—and neither should your defenses. As we’ve explored, 24/7 cybersecurity monitoring is no longer a luxury for large corporations; it’s an essential investment for any organization that values its data, reputation, and future. Relying on a 9-to-5 security schedule is like leaving your digital front door open uped every night.
The stakes are too high to gamble with outdated security approaches. Moving to a proactive posture means combining advanced technology, expert human analysis, and intelligent automation. While challenges like cost, complexity, and the cybersecurity talent shortage exist, they are surmountable with the right strategy.
The choice between an in-house SOC and a managed service provider depends on your resources, but the trend toward outsourcing is clear for a reason: it makes financial and operational sense for most businesses.
At Concertium, we’ve spent nearly 30 years perfecting this balance. Our Collective Coverage Suite (3CS) with AI-improved observability is not a one-size-fits-all solution. We partner with you to build defenses custom to your specific risk profile and business needs.
Don’t wait for a security breach to realize your defenses are inadequate. The best time to act was yesterday—the second-best time is right now.
Take control of your security with our Managed Cybersecurity Services and let us help you build a defense system that truly never sleeps. Because in cybersecurity, peace of mind is priceless.