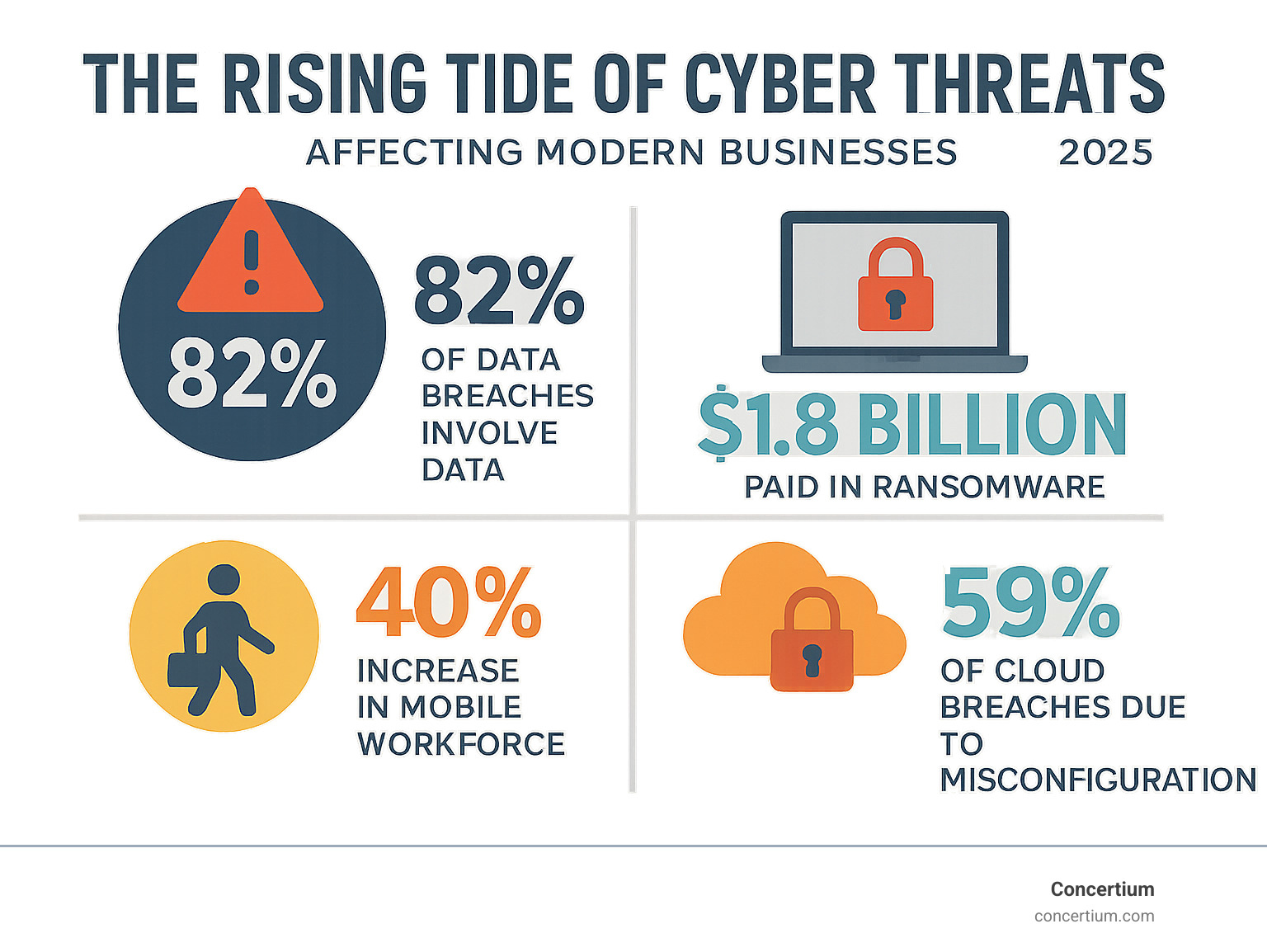
Cybersecurity defense strategies are a structured approach to protecting your organization from cyber threats through layered security, proactive monitoring, and incident response planning. With cybercrime costs projected to hit $10.5 trillion annually by 2025 and breaches taking an average of 200 days to detect, a solid defense strategy is essential for survival.
Core cybersecurity defense strategies include:
- Defense in Depth – Multiple security layers working together
- Zero Trust Security – Never trust, always verify approach
- Risk-Based Defense – Prioritizing protection based on asset value
- Incident Response Planning – Structured approach to handling breaches
- Continuous Monitoring – Real-time threat detection and response
- Employee Security Training – Addressing the human element (68% of breaches involve human error)
The stakes are high. IT downtime can cost businesses up to $540,000 per hour, and the average ransomware payment reached $572,000 in 2021. Small businesses are prime targets, with 43% of cyber attacks aimed at them due to weaker defenses.
Modern cyber defense is more than just antivirus and firewalls. Today’s threats are sophisticated and constantly evolving. Your defense strategy must be equally dynamic, combining technical controls, administrative policies, and human awareness into a cohesive security posture.
Basic cybersecurity defense strategies glossary:
The Foundation: Core Principles of Defensive Cybersecurity
Imagine your business as a fortress. You wouldn’t rely on a single wall; you’d use multiple layers of protection. That’s the essence of cybersecurity defense strategies: building a digital fortress to withstand modern cyber attacks.
Defensive cybersecurity—often called “Blue Team” operations—focuses on protecting your digital assets before, during, and after an attack. While offensive cybersecurity (the “Red Team”) tests your defenses, the Blue Team builds and maintains them. With cybercrime costs expected to hit $10.5 trillion by 2025, strong defenses are critical for business survival. It’s not a matter of if you’ll face a threat, but when.
The foundation of effective defense rests on five core principles: Identify what you need to protect. Protect your assets with controls like firewalls and encryption. Detect threats with early warning systems. Respond with a clear crisis management plan. And Recover to get back to business after an incident.
These principles align with established frameworks like NIST and CIS Controls, providing a practical roadmap for solid Cybersecurity Risk Management.
Developing Your Battle Plan: A Step-by-Step Guide
Creating robust cybersecurity defense strategies requires a methodical approach:
Risk Assessment comes first. Conduct a Business Impact Analysis (BIA) and create a risk register to prioritize critical assets and vulnerabilities.
Policy Development turns your assessment into actionable rules. These guidelines dictate data handling, incident response, and security for your organization.
Implementation is where you deploy technical controls like firewalls and administrative controls like security training. Effective Vulnerability Risk Management systematically addresses known weaknesses.
Monitoring provides continuous vigilance to spot threats early and ensure your controls are working as intended.
Response activates when a problem is detected. Your Incident Response plan needs clear roles and procedures to contain threats quickly.
Recovery focuses on restoring systems from clean backups and resuming operations with minimal downtime.
Review closes the loop. The threat landscape evolves, so your defenses must too. Regular reviews keep your strategy effective.
The Human Element: Your First and Last Line of Defense
A sobering 68% of data breaches involve human error. Technology alone isn’t enough; untrained employees can be a major vulnerability. However, when properly trained, your employees become your strongest defense, spotting suspicious activity and following security protocols.
Phishing awareness training is critical, as phishing is a top attack vector. Regular simulations help employees recognize suspicious emails. Understanding Social Engineering Attacks is also key, as attackers use various methods to manipulate people.
Password hygiene is foundational. Strong, unique passwords, combined with password managers and multi-factor authentication, create a formidable security barrier.
Clear reporting procedures empower employees to act as an extension of your security team. Make reporting easy and encourage it, even for potential false alarms.
Don’t forget about Insider Threats, which are often unintentional. A security-conscious culture where following protocols is second nature is your best defense against accidental breaches.
Defense in Depth: Building an Impenetrable Fortress
Think of a medieval castle. It has a moat, multiple walls, towers, and guarded gates. If one layer is breached, another stands in the way. This timeless military principle is what we mean by defense in depth in cybersecurity. It’s a fundamental strategy that layers multiple, overlapping security controls throughout the IT environment.
This approach is crucial because the traditional network perimeter has dissolved. With cloud environments and a remote workforce, we can no longer draw a clear line around our corporate network. Remote work security requires multiple safety nets to protect against compromised devices and insecure connections.
Defense in depth acknowledges that no single control is perfect. A firewall can be bypassed, and a password can be stolen. But when you layer defenses, an attacker who breaks through one barrier immediately encounters another, making the entire system more resilient.
The Essential Layers of a Defense-in-Depth Strategy
An effective strategy combines three types of controls to protect every entry point:
Physical controls are the foundation. This includes security guards, surveillance, locked doors, and biometric access to protect hardware and infrastructure. Environmental controls for fire and temperature are also vital, as physical access can bypass all digital security.
Technical controls are the heart of digital defense. This includes:
- Network security relies on firewalls to control traffic and Intrusion Detection/Prevention Systems (IDS/IPS) to spot and block threats.
- Cloud Security is complex, requiring secure configurations and specialized tools like Cloud Access Security Brokers (CASB) to protect data and applications.
- Endpoint security protects all connected devices (laptops, smartphones) with modern solutions like Endpoint Detection and Response (EDR) to stop sophisticated threats.
- Application security involves secure coding, vulnerability assessments, and Web Application Firewalls (WAFs) to protect software from attacks.
- Data security protects information itself through Encryption and Data Loss Prevention (DLP) tools that monitor for data theft.
Administrative controls tie everything together with policies and training. These human-centered controls include security policies, awareness training, and risk assessments. They provide the guidelines and knowledge to implement, manage, and improve all other defenses.
When these layers work together, the system becomes stronger. An attacker might bypass a firewall but will still face endpoint protection and network segmentation, while stolen data remains useless due to encryption.
Common Implementation Pitfalls and How to Avoid Them
Even with good intentions, organizations often make costly mistakes when implementing cybersecurity defense strategies.
Technical bloat occurs when organizations accumulate disparate security tools. This creates confusion, performance issues, and coverage gaps. To avoid this, regularly audit your security stack to ensure every tool serves a clear, integrated purpose.
Legacy systems are major vulnerabilities when they are no longer supported by vendors and don’t receive security patches. If immediate replacement isn’t possible, isolate them with compensating controls like network segmentation and improved monitoring.
Insufficient resources plague many businesses. Cybersecurity requires skilled people and funding. If hiring a full security team isn’t feasible, consider managed security services to get enterprise-grade protection at a fraction of the cost.
Cloud misconfigurations are a leading cause of data breaches. The shared responsibility model can be confusing, leading to errors. Regular configuration reviews and automated security scanning can catch these issues before they become breaches.
Shadow IT refers to technology used by employees without IT approval. While often used to boost productivity, these unmanaged tools create security blind spots. The best approach is to provide approved, secure alternatives that meet employee needs.
Advanced Cybersecurity Defense Strategies for the Modern Battlefield
The cyber battlefield has become far more challenging. Threat actors are sophisticated, well-funded, and relentless, with security breaches skyrocketing by 600% during the pandemic. This escalating threat, combined with strict regulations like HIPAA Compliance, PCI Compliance, and GDPR Compliance, means our cybersecurity defense strategies must be smarter and more adaptive than ever.
The old approach of trusting everything inside the network no longer works. We need proactive, intelligent defenses that can anticipate and neutralize attacks before they cause damage.
Proactive and Adaptive Cybersecurity Defense Strategies
Modern cybersecurity defense strategies must stay several moves ahead of opponents. The most effective approaches combine cutting-edge technology with strategic thinking.
- The Zero Trust Model operates on a “never trust, always verify” principle. It requires continuous authentication for every user and device, regardless of location, dramatically reducing breach impact and preventing lateral movement.
- Microsegmentation divides networks into small, isolated segments. Like a submarine’s compartments, it contains breaches and is highly effective at stopping the spread of ransomware.
- Deception Technology uses decoys and honeypots to lure attackers. When they take the bait, their presence and methods are revealed, protecting real assets.
- AI and Machine Learning are game-changers for our Threat Detection and Response, analyzing vast data sets to spot anomalies humans would miss. This speeds up response times and reduces false positives.
- Endpoint Detection and Response (EDR) solutions provide comprehensive visibility into every device, continuously monitoring for suspicious behavior and automatically containing threats.
- For organizations needing 24/7 oversight, Managed Detection and Response (MDR) services provide expert threat hunting. Our MDR approach combines advanced tools with human expertise, leveraging our Collective Coverage Suite (3CS) to deliver enterprise-grade protection.
Securing the New Frontier: Remote Work and Automated Systems
The rise of remote work has created a new security frontier. With the U.S. mobile worker population projected to reach 93.5 million by 2024, we are no longer protecting a single perimeter but a distributed network of home offices and public spaces.
Remote work security requires a multi-layered approach. Virtual Private Networks (VPNs) create encrypted tunnels for data, but they aren’t enough. We enforce Multi-Factor Authentication on all remote access points to render stolen passwords useless.
Secure configurations and diligent patch management are critical for all remote devices to close security gaps. The rise of automated systems and IoT devices presents another challenge, as they often lack basic security features. We address this by implementing network segmentation to isolate these devices, conducting regular vulnerability assessments, and using behavioral analysis to spot compromises.
Securing IoT and OT devices requires a mix of technical controls and policy. For devices at their end-of-life, our IT Asset Disposition (ITAD) services ensure secure disposal to prevent data breaches.
Measuring Success and Adapting for the Future
Effective cybersecurity defense strategies require continuous care and adaptation. This means measuring our defensive effectiveness to stay ahead of evolving threats.
We focus on Key Performance Indicators (KPIs) that tell the real story of our security posture. Mean Time To Detect (MTTD) reveals how quickly we spot trouble, while Mean Time To Respond (MTTR) shows how fast we contain it. Other crucial metrics include our vulnerability patch rate and employee security awareness scores. These metrics indicate if your defenses are working or need adjustment.
Numbers only tell part of the story. We actively test our defenses through:
- Penetration testing, where ethical hackers simulate real-world attacks to find weaknesses.
- Vulnerability assessments, which use automated and manual reviews to identify known security holes.
- Tabletop exercises, which are war games that test our incident response plans without the pressure of a real emergency.
The cyber threat landscape never stands still. We leverage Cybersecurity Threat Intelligence to stay informed about emerging attack trends and adjust our defenses proactively. This continuous adaptation involves regular architecture reviews, investment in new technologies, and ongoing training. In cybersecurity, standing still is moving backward.
Frequently Asked Questions about Cybersecurity Defense Strategies
Here are answers to common questions we hear about cybersecurity defense strategies.
How does defensive cybersecurity differ from offensive cybersecurity?
Defensive cybersecurity (“Blue Team”) focuses on protecting assets by preventing, detecting, and responding to attacks. It’s about building and maintaining the digital fortress. Offensive cybersecurity (“Red Team”) acts as an ethical hacker, testing defenses to find vulnerabilities before real attackers do. The two work together in a continuous cycle of improvement.
What is the most critical component of a cyber defense strategy?
There is no single most critical component. Effective defense relies on a layered approach (defense in depth) where multiple controls work together. Other crucial elements include the human element (training), foundational risk assessment, and continuous monitoring and adaptation to keep the strategy relevant against evolving threats.
How can small businesses afford effective cybersecurity?
Small businesses can achieve effective security without a massive budget. The key is to invest smartly:
- Prioritize critical assets using a risk assessment to focus your resources where they matter most.
- Leverage proven frameworks like the CIS Critical Security Controls for a prioritized, effective roadmap.
- Focus on cyber hygiene. Basics like strong passwords, multi-factor authentication, and employee training can prevent a huge percentage of attacks at a very low cost.
- Consider managed security services as a cost-effective alternative to an in-house team. Partnering with experts like Concertium gives you 24/7 monitoring and enterprise-grade protection at a fraction of the cost.
Conclusion: Winning the Cyber War with Strategic Defense
Cybersecurity defense strategies are essential for business survival, growth, and customer trust. The path to effective cyber defense is clear: there’s no magic bullet, only a proven, strategic approach.
The foundation of any successful defense is that strategy trumps tools every time. Without a coherent plan custom to your specific risks, even the best software is ineffective. The defense-in-depth approach creates the necessary layers of protection that work in concert.
The human element is key. While 68% of breaches involve human error, a security-aware team can prevent countless attacks, turning a potential vulnerability into your strongest asset.
Most importantly, continuous adaptation is essential for survival. The threat landscape evolves daily, so measuring success, testing defenses, and staying informed through threat intelligence must become part of your organization’s DNA.
With nearly 30 years of expertise, Concertium transforms vulnerable targets into resilient operations. Our unique Collective Coverage Suite (3CS), with its AI-improved observability and automated threat eradication, represents the evolution of what’s possible when strategy meets technology. We craft custom solutions that fit your specific business needs and risk profile.
The cyber war isn’t won overnight, but with the right strategic defense, you’re not just surviving—you’re positioning your business for confident growth.