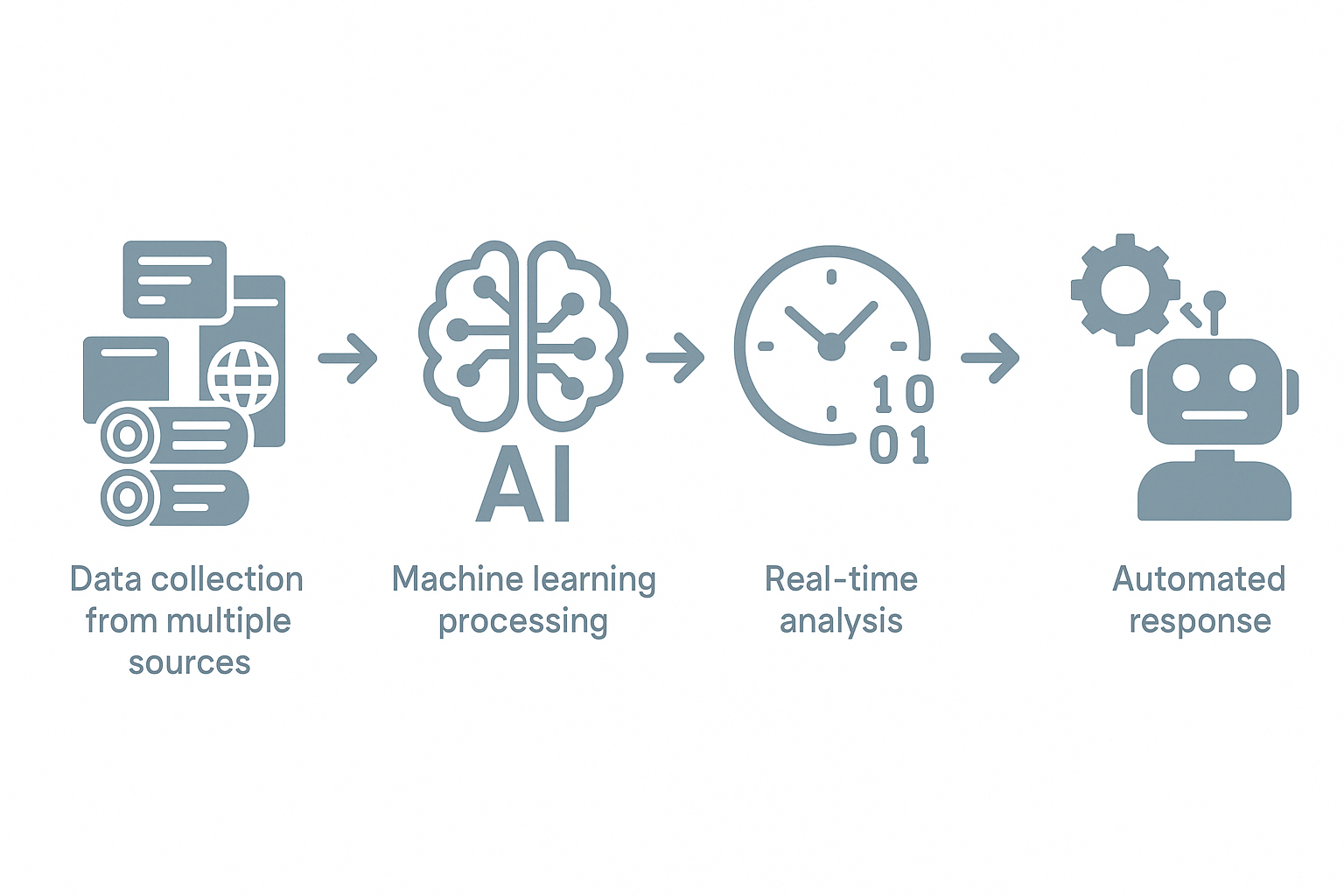
Automated threat intelligence is a sophisticated approach to cybersecurity that uses AI and machine learning to collect, analyze, and respond to cyber threats without constant human intervention.
For business owners searching for quick answers about automated threat intelligence:
| What It Is | Key Benefits | Why It Matters |
|---|---|---|
| AI-powered system that automatically collects and analyzes threat data | • Reduces response time from hours to minutes • Processes millions of indicators daily • Saves up to 65% on breach costs |
With over 2,200 cyber attacks occurring daily, automation helps identify which threats are relevant to your business |
Cyber threats have become more sophisticated, numerous, and damaging. Global cyber attacks jumped 29% in the first half of 2021 compared to the same period in 2020, leaving organizations scrambling to keep pace.
The traditional approach to threat intelligence—manually collecting, analyzing, and responding to threat data—is no longer sustainable. Security teams are drowning in alerts, with many experiencing burnout symptoms (69% according to recent studies) as they struggle to separate critical threats from noise.
“This is going to save me so much time.” — Lead Over All Users At A DOD Customer
Automated threat intelligence transforms this landscape by using advanced technologies to process vast amounts of threat data at machine speed. Rather than relying solely on human analysts to sift through millions of potential indicators, these systems use artificial intelligence and machine learning to identify patterns, prioritize alerts, and even initiate responses automatically.
For mid-sized businesses with limited cybersecurity resources, this technology offers a way to achieve enterprise-grade protection without massive security teams. It allows you to focus your human expertise where it matters most while letting automation handle the repetitive, time-consuming tasks of threat detection and initial response.
Automated threat intelligence terms to remember:
Understanding Automated Threat Intelligence
Automated threat intelligence fundamentally differs from traditional threat intelligence methods in both approach and capability. While traditional methods rely heavily on manual processes—where analysts painstakingly collect, analyze, and respond to threats—automated systems leverage artificial intelligence, machine learning, and natural language processing to perform these tasks at scale and with unprecedented speed.
Traditional threat intelligence often struggles with several key limitations. Analysts spend countless hours on manual data collection and analysis, making it impossible to process the massive volume of daily threat indicators. This creates inevitable delays in response times and leads to inconsistent analysis based on who’s available and their level of experience.
In contrast, automated threat intelligence platforms transform how organizations handle security data. These systems can ingest and process millions of indicators from diverse sources simultaneously, automatically normalizing and deduplicating data to cut through the noise. The sophisticated machine learning algorithms identify patterns and anomalies that might escape human notice, generating actionable insights almost instantly while maintaining vigilance 24/7 without experiencing fatigue.
As one CISO from a federal customer told us, “This platform professionalized our CTI team.” This professionalization comes from changing raw data into structured, actionable intelligence that security teams can use immediately.
At Concertium, we’ve seen how organizations implementing automated threat intelligence can process data in minutes that would take human analysts days or even weeks to handle. This dramatic efficiency boost allows security teams to focus on strategic decisions rather than drowning in endless data collection and preliminary analysis.
Key Applications of Automated Threat Intelligence
Automated threat intelligence has revolutionized multiple aspects of cybersecurity operations. The impact is particularly noticeable in four critical areas:
Email Security remains one of our most vulnerable points, as most cyber attacks still begin with a deceptive message. Automated systems analyze email content, sender details, attachments, and links in real-time, catching sophisticated phishing attempts that traditional filters miss. These systems can process thousands of emails per minute, spotting subtle red flags that would overwhelm human analysts.
When it comes to Behavioral Analytics, establishing what’s “normal” gives us the power to spot what’s not. By learning typical user and system behavior patterns, automated tools quickly flag suspicious deviations. As one security operations leader shared with us, “Before implementing automated behavioral analytics, we were blind to lateral movement within our network. Now we can detect abnormal access patterns within minutes.”
For Threat Hunting, automation has transformed the game entirely. Rather than starting investigations from scratch, security teams now leverage AI and Automated Threat Detection to continuously scan environments for indicators of compromise. This frees human analysts to focus on investigating the most suspicious activities instead of searching for needles in digital haystacks.
Perhaps most impressive is the evolution of Automated Response capabilities. Modern threat intelligence platforms can automatically initiate response actions when threats appear—isolating compromised systems, blocking malicious IP addresses, updating security rules based on new threat data, and initiating remediation workflows without waiting for human intervention.
A Senior Vice President & Security Officer from the financial sector put it perfectly: “The time it takes to analyze a threat has gone down from 30 minutes to just a few minutes, time that adds up over the course of investigating many malicious IPs every week. There has been a substantial decrease in terms of meantime-to-know.”
This dramatic reduction in analysis time shows the transformative power of automated threat intelligence when properly implemented and integrated with existing security infrastructure.
The Role of Human Analysts in AI-Powered Systems
Despite all the power of automation, human analysts remain absolutely essential in the threat intelligence ecosystem. The most effective security operations create a partnership between artificial intelligence and human expertise—a relationship that plays to the strengths of both.
Human analysts bring several irreplaceable qualities to the table that AI simply can’t match. They excel at understanding the broader business context and potential impact of threats on specific operations. When faced with novel threats or unusual situations, human creativity and adaptability shine brightest. The judgment calls required for strategic decision-making often consider factors beyond what pure data can tell us. And perhaps most importantly, human analysts continuously improve automated systems by providing feedback, adjusting algorithms, and ensuring the technology evolves to meet new challenges.
“Collaboration between AI and human analysts creates a synergy that maximizes the strengths of both, leading to a more comprehensive and adaptive defense against cyber threats.”
At Concertium, we’ve consistently observed that the organizations achieving the greatest success with automated threat intelligence don’t view automation as replacing their analysts. Instead, they see it as a force multiplier that enables their teams to work more efficiently and focus on higher-value activities.
A Chief Risk Officer from a prominent UAE bank explained this partnership perfectly: “By bringing in industry experts alongside our automated systems, we expect to gain advanced levels of security that will help us to further heighten our defenses and intercept any possible exploitation by cybercriminals.”
This human-machine collaboration creates security that’s both more efficient and more effective than either component could achieve alone—like having the world’s most powerful magnifying glass in the hands of an experienced detective. The tool amplifies capabilities, but the human provides the insight that makes it truly valuable.
The Lifecycle of Automated Threat Intelligence
Automated threat intelligence isn’t just a one-time setup—it’s a living, breathing process that constantly evolves to keep you protected. Think of it as a continuous cycle that gets smarter with every revolution, much like how we humans learn from our experiences.
Let’s walk through the five phases that make this intelligence cycle so powerful:
- Collection: This is where everything begins. Your automated systems are constantly gathering raw threat data from everywhere that matters—public sources, dark web forums, vendor threat feeds, your own security logs, and trusted security communities. Unlike the old days when an analyst might check a few sources during their shift, these systems are working 24/7, never missing a beat. It’s like having hundreds of security researchers working for you around the clock.
- Structure and Enrichment: Raw data alone isn’t very helpful—it needs context to become meaningful. During this phase, your system cleans up the data (removing duplicates and normalizing formats) and then adds valuable context. It connects new threats with known indicators, adds geographic information, aligns with frameworks like MITRE ATT&CK, and enriches everything with historical context. This change turns scattered puzzle pieces into a coherent picture your team can actually use.
- Analysis: Here’s where the magic happens. Advanced AI and machine learning algorithms sift through mountains of structured data to spot patterns human eyes might miss. The system scores threats based on how relevant and severe they are to your specific environment, and determines which of your assets might be at risk. As one Threat Detection Team Lead at a government customer enthusiastically shared, “We love this product. My team uses it every day.” The analysis phase shows why automation is so valuable—it handles data volumes that would leave even the best human analysts overwhelmed.
- Disseminate and Deploy: Even the best intelligence is useless if it doesn’t reach the right people and systems at the right time. In this phase, actionable insights are automatically distributed where they’re needed most. Your security teams get prioritized alerts, executives receive clear summaries without technical jargon, and your defense systems automatically update their rules. What used to take days now happens in seconds—a game-changer when every moment counts during an attack.
- Planning and Feedback: The final phase ensures your system gets smarter over time. By measuring how effective your intelligence was, incorporating feedback, identifying new requirements, and retraining your models with fresh data, your automated threat intelligence continuously improves. This isn’t just a technical process—it’s how your entire security operation learns and adapts.
What makes this lifecycle so powerful is how interconnected these phases are. Each one feeds into and improves the others, creating a system that grows more effective with every passing day. It’s not just automated—it’s self-improving.
At Concertium, we’ve spent nearly three decades helping organizations implement and optimize this intelligence lifecycle. We know that every business has unique security needs, which is why we tailor each phase to your specific environment, threats, and goals. The result? An automated threat intelligence capability that evolves alongside the threats you face, keeping you protected without overwhelming your team.
Benefits of Automated Threat Intelligence
The shift to automated threat intelligence isn’t just a technological upgrade—it’s a complete change in how organizations protect themselves. If you’ve ever watched your security team drowning in alerts or staying late to investigate potential threats, you’ll appreciate the very real benefits this approach delivers.
Dramatic Efficiency Improvements
Remember the days when analyzing a single threat could eat up half an hour of an analyst’s time? Those days are over for organizations embracing automation.
Automated threat intelligence shrinks response times dramatically—from hours to minutes, or even seconds in some cases. One of our financial sector clients cut their per-incident analysis time by 90%, freeing their analysts to focus on more complex challenges.
The coverage improvement is equally impressive. While a human team might monitor a handful of threat feeds effectively, automated systems can simultaneously watch thousands of sources without breaking a sweat. They never need coffee breaks, never get distracted, and never miss subtle connections between seemingly unrelated events.
The accuracy boost might be the most welcome improvement of all. Machine learning algorithms excel at spotting patterns too subtle for human detection, dramatically reducing those frustrating false positives that waste everyone’s time. As one client told us, “We’re finding threats we would have missed before, and spending less time chasing ghosts.”
Significant Cost Savings
Let’s talk dollars and cents—because that’s what ultimately matters to business leaders. Organizations fully embracing security AI and automation save a whopping 65.2% on total breach costs. That’s not just impressive; it’s transformative for security budgets.
The math is simple: when your skilled (and expensive) security professionals spend less time on routine data processing, you get more value from every dollar of your security investment. These professionals can focus on strategic initiatives that truly require human judgment and creativity.
Perhaps the biggest financial benefit comes from what doesn’t happen—successful attacks. Early detection and prevention mean you avoid the cascade of costs that follow a breach: incident response, legal fees, regulatory penalties, customer notification, and the often-substantial hit to your reputation and customer trust.
Reduced Analyst Burnout
The human factor matters tremendously in cybersecurity. With 69% of cybersecurity professionals reporting burnout symptoms, anything that eases this burden deserves serious attention.
Automated threat intelligence tackles burnout at its source by handling the mind-numbing repetitive tasks that drain analysts’ energy and enthusiasm. Instead of sifting through endless alerts, your team can focus on interesting, challenging work that actually requires their expertise and judgment.
The 24/7 nature of automated systems also means better work-life balance. Your human team doesn’t need to maintain constant vigilance—the system handles that, alerting them only when their skills are truly needed. As one Head of Cyber Threat Intelligence put it: “This is the best TIP I have ever worked with.” The relief in that statement speaks volumes.
Proactive Defense Posture
Perhaps the most powerful benefit is the shift from playing catch-up to staying ahead of threats. Traditional security is reactive—you find a problem, then scramble to fix it. Automated threat intelligence flips this dynamic entirely.
With automation constantly analyzing emerging threats, you can identify and address potential vulnerabilities before attackers exploit them. Your security controls continuously update based on the latest threat data, creating a dynamic defense that evolves as quickly as the threat landscape.
Vulnerability prioritization becomes precision-guided rather than scattershot. Instead of trying to patch everything at once, you can focus resources on the vulnerabilities most likely to be exploited against your specific organization.
One CISO explained this change perfectly: “Before Anomali, we had tons of information without context. We had to look through thousands of alerts quickly just to see what stood out and then react to those. Anomali enabled us to spend less time dealing with noise, and more time focusing on critical issues.”
This shift from reactive to proactive defense represents the true strategic value of Automated Threat Detection. At Concertium, we’ve guided numerous organizations in Tampa and beyond through this change, helping them realize these benefits through thoughtfully implemented automated threat intelligence solutions.
Implementing Automated Threat Intelligence
Bringing automated threat intelligence into your organization doesn’t have to be overwhelming. With a thoughtful, strategic approach, you can integrate these powerful capabilities while minimizing disruption and maximizing value.
Start by taking stock of what you already have. What threat intelligence capabilities exist in your organization today? Where are the gaps? What specific problems do you most need to solve? This assessment creates a foundation for smart decision-making.
Selecting the right tools comes next. The Top Threat Detection Tools should align with your specific needs, not just offer the longest feature list. Consider how well they’ll integrate with your existing security stack, whether they can grow with your organization, and if they can be customized to address your particular threat landscape.
Integration planning deserves careful attention. Your automated threat intelligence solution will need to work harmoniously with your SIEM, endpoint protection, firewalls, and incident response workflows. A well-thought-out integration plan prevents headaches down the road.
We strongly recommend a phased implementation approach. Start by automating data collection and normalization, then gradually implement analysis capabilities. Only introduce automated response actions after thorough testing and validation. This measured approach builds confidence and allows your team to adapt gradually.
Don’t forget to invest in your people. The most sophisticated technology won’t deliver its full value if your team doesn’t understand how to work with it. Make sure they know how to interact with the system, when human judgment is needed, how to provide feedback that improves the automation, and how to interpret and act on the intelligence produced.
As one security operations company founder shared: “We leverage market-leading tools to give our company a competitive advantage and our 24/7 SOC a leg up on bad actors. With Anomali, we improve on both of these goals. By adding intelligence, we achieve a high level of certainty that improves prioritization of the most serious threats our customers face, while improving our mitigation decisions.”
At Concertium, we understand that every organization has unique security requirements. Our approach to implementing automated threat intelligence involves tailoring solutions to your specific environment and objectives, leveraging our Collective Coverage Suite (3CS) with AI-improved observability to maximize the effectiveness of your security operations.
Challenges and Mitigation Strategies
While automated threat intelligence offers tremendous benefits, implementing these systems isn’t always smooth sailing. Let’s talk about the real challenges organizations face and how to overcome them.
Bias in Training Data
AI systems are only as good as the data they learn from – it’s that simple. When your training data doesn’t represent the full threat landscape, your protection has blind spots.
We saw this with a financial institution client whose automated system excelled at catching known malware but consistently missed new attack techniques. Their system had been trained primarily on common threats, creating a dangerous gap in their defenses.
To avoid this pitfall, ensure your training data includes diverse threat types across different industries and attack vectors. Regular audits of your detection patterns can reveal potential blind spots before attackers find them. Don’t just rely on vendor-provided intelligence – supplement it with threat data specific to your industry. The most successful implementations include continuous learning mechanisms that constantly incorporate new threat information.
Adversarial Attacks
Think of this as the cyber equivalent of evolutionary pressure – as our defenses get smarter, so do the attackers trying to bypass them.
Security researchers have demonstrated how even slight modifications to malicious code can trick AI systems into classifying harmful files as safe. It’s concerning to see how vulnerable even sophisticated systems can be to these deliberate evasion tactics.
To strengthen your defenses against these crafty attacks, implement adversarial training that deliberately exposes your AI systems to evasion attempts. Don’t put all your eggs in one basket – deploy multiple detection methods using different analytical approaches. Human oversight remains crucial for catching anomalies that might indicate someone is trying to game your system. And just like you’d test a physical security system, regularly challenge your automated defenses with the latest evasion techniques.
Over-reliance on Automation
It’s tempting to think that once you’ve implemented automated threat intelligence, you can scale back your human security team. This false sense of security has led to serious consequences.
A major retailer learned this lesson the hard way when they experienced a significant breach despite having advanced automated systems. They had reduced their analyst team, assuming the AI would catch everything – a costly mistake.
The solution is balance. Clearly define what your automated systems handle versus what needs human attention. Establish regular human review of automated decisions, especially for high-stakes situations. Maintain complementary security controls that don’t solely rely on AI, and create clear escalation paths for scenarios that require human judgment. Think of your automated system as a very talented assistant, not a replacement for human expertise.
Integration Complexity
Getting your shiny new automated threat intelligence system to play nice with your existing security infrastructure can be like trying to fit puzzle pieces from different boxes together.
One healthcare organization we worked with struggled for months to realize the benefits of their substantial investment because their system couldn’t effectively communicate with their legacy SIEM. The result? Information silos that actually made their security operations less effective, not more.
Before implementation, conduct thorough compatibility assessments. Develop a clear integration roadmap with defined milestones so you can track progress. In some cases, middleware solutions can bridge compatibility gaps between systems that weren’t designed to work together. And consider working with experienced integration partners (like us at Concertium) who’ve seen and solved these challenges before.
Mitigating Risks in Automated Threat Intelligence
Successfully navigating these challenges requires thoughtful planning that balances cutting-edge automation with human expertise.
Data diversity is your first line of defense. Your automated threat intelligence system should ingest information from global threat feeds, industry-specific sources, geographically relevant information, and both technical indicators and strategic intelligence. This creates a more complete picture of the threat landscape.
Safeguarding against adversarial attacks requires vigilance. Implement detection capabilities for known evasion techniques and regularly update your AI models with the latest threat data. Using ensemble methods that combine multiple detection approaches provides redundancy when one method might be fooled. Regular red team exercises will help test your system’s resilience against real-world attack scenarios.
Human oversight remains irreplaceable. Establish clear processes for human review of automated findings and create feedback loops where analysts can correct AI mistakes when they occur. Maintain a balanced security team with both technical and strategic expertise, and develop clear criteria for when threats require human judgment.
Continuous learning keeps your defenses evolving. Implement mechanisms to regularly update AI models with new threat data and retrain systems to adapt to the changing threat landscape. Monitor system performance metrics closely and be ready to make adjustments when needed. Perhaps most importantly, incorporate lessons learned from security incidents into model improvements – don’t let a breach teach you nothing.
At Concertium, we’ve guided many organizations through these challenges using our nearly 30 years of cybersecurity expertise. We emphasize balancing cutting-edge automation with seasoned human judgment, ensuring that automated threat intelligence improves rather than replaces human expertise.
As one cybersecurity leader we work with noted, “Transparency is key, that’s why we’ve rolled out a consolidated False Positive List… false positives happen – it’s just part of managing community-driven data!” This honest acknowledgment of automated systems’ limitations, coupled with transparent processes to address them, exemplifies the balanced approach required for success.
Conclusion
The cybersecurity landscape continues to evolve at a breathtaking pace, with threat actors becoming increasingly sophisticated and attacks growing in both frequency and impact. In this environment, automated threat intelligence has emerged as an essential capability for organizations seeking to protect their digital assets effectively.
Throughout this article, we’ve explored how automated threat intelligence transforms security operations:
Remember when cybersecurity meant a team of bleary-eyed analysts manually sifting through endless alerts? Those days are thankfully behind us. Today’s automated threat intelligence dramatically improves efficiency by handling data collection, analysis, and initial response without human intervention for every step. This means your security team can process millions of threat indicators daily, effortlessly separating genuine threats from background noise.
One of the most human benefits we’ve seen with our clients is the reduction in analyst burnout. By letting machines handle the repetitive, mind-numbing tasks, your talented team members can focus on the strategic work they were hired to do—the creative problem-solving that machines simply can’t match. This not only improves morale but creates a more proactive security posture through early detection and rapid response.
And let’s talk about the bottom line—because we know that matters too. Organizations implementing automated threat intelligence save up to 65.2% on breach costs. That’s not small change, especially for mid-sized businesses watching every dollar.
Of course, we’ve also acknowledged the challenges that come with implementing these systems. From potential bias in training data to the risk of adversarial attacks, success requires a thoughtful approach that balances automation with human expertise. The best security postures we’ve helped build don’t replace humans with machines—they create a partnership where each does what they do best.
At Concertium, we bring nearly 30 years of cybersecurity expertise to help organizations in Tampa and beyond implement effective automated threat intelligence solutions. Our Collective Coverage Suite (3CS) with AI-improved observability and automated threat eradication provides a comprehensive approach to modern security challenges.
We understand that every organization has unique security requirements. That’s why we don’t believe in one-size-fits-all solutions. Instead, we work closely with you to develop and implement automated threat intelligence capabilities that complement your existing security infrastructure and address your most pressing threats. Your business isn’t exactly like anyone else’s—why should your security be?
As cyber threats continue to evolve, so too will the technologies we use to defend against them. Automated threat intelligence represents not just a current best practice, but a foundation for the future of cybersecurity—a future where human expertise is augmented by machine intelligence to create defenses that are both more efficient and more effective than either could achieve alone.
Learn more about our consulting and compliance services to find how Concertium can help your organization harness the power of automated threat intelligence to strengthen your security posture and protect your critical assets.