Quick Answer: Best Online Web Security Scanners in 2025
- Advanced Scanner Pro – Best for comprehensive scanning with low false positives
- OWASP ZAP – Best free open-source option
- SecureCheck – Best for malware detection and blacklist monitoring
- Concertium Scanner – Best all-in-one vulnerability management platform
- VulnDetect – Best for realistic attack simulation
Your website is the face of your business—and unfortunately, it’s also a prime target for cyberattacks. Over the past year alone, millions of websites have been compromised, leading to data breaches, financial losses, and damaged reputations. For business owners with limited cybersecurity expertise, this presents a significant challenge.
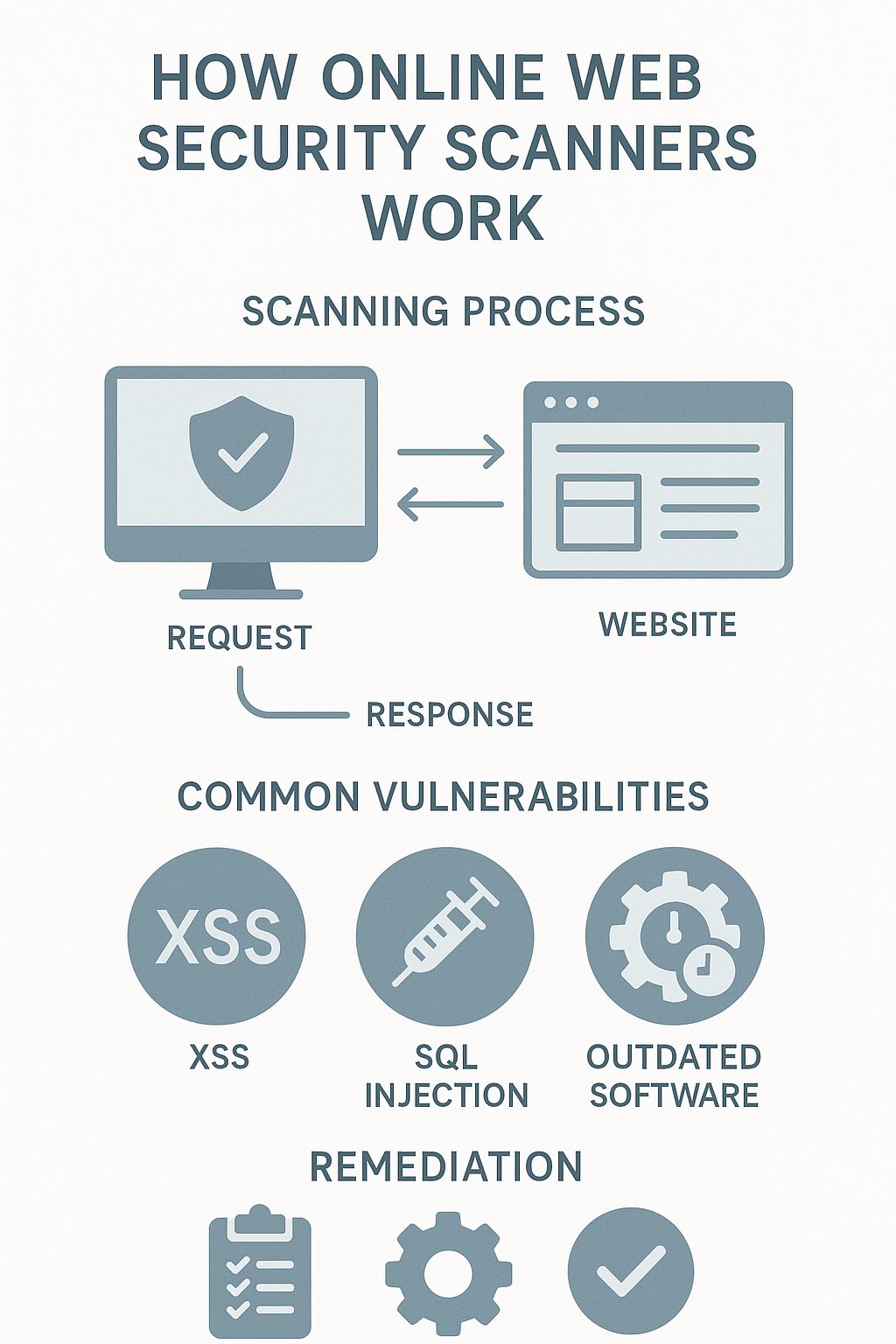
Think of an online web security scanner as a virtual security guard that continuously patrols your digital property. These tools work by sending specially crafted requests to your website and analyzing the responses for signs of vulnerabilities. They can detect everything from cross-site scripting (XSS) and SQL injection to outdated software and misconfiguration issues.
As one security professional quoted in our research noted: “We use daily vulnerability testing to guarantee our security and support our ISO certification requirements.” This highlights the dual benefit of these tools—they both protect your assets and help maintain compliance with industry standards.
What sets cloud-based scanners apart from traditional security solutions is their accessibility and ease of use. There’s no complex software to install, and they’re constantly updated to detect the latest threats. For business owners juggling multiple priorities, this “set it and forget it” approach provides peace of mind without adding to your workload.
What Is an Online Web Security Scanner and How Does It Work?
Think of an online web security scanner as your website’s personal health checkup tool. It’s like having a security expert continuously examining your digital storefront, but without the hefty consulting fees. These cloud-based tools are specifically designed to spot security weaknesses in your websites and web applications before the bad guys can exploit them.
The Mechanics Behind the Magic
When you run an online web security scanner, it performs a sophisticated dance of detection that mimics how actual hackers would approach your site—but with good intentions! The process unfolds in several stages:
First, during what we call the “Findy Phase,” the scanner identifies all the places on your website where someone could potentially interact—think forms, login pages, and other interactive elements. Next comes the crawling stage, where the scanner explores your site like a curious visitor, following links and mapping out how everything connects.
The real security magic happens during active testing. Here, the scanner sends special requests (sometimes called “payloads”) to your website. These aren’t harmful, but they’re designed to see how your site responds—kind of like pressing on different parts of a wall to see if any sections feel hollow.
After gathering all these responses, the scanner analyzes them for telltale signs of security weaknesses. Finally, you receive a comprehensive report that not only highlights problems but also suggests how to fix them.
How Online Scanners Differ from Traditional Antivirus Software
Many people confuse online web security scanners with antivirus programs, but they serve completely different purposes. Your antivirus is like a bodyguard for your computer’s files and processes, while a web security scanner is more like a building inspector for your website.
| Feature | Online Web Security Scanner | Traditional Antivirus |
|---|---|---|
| Focus | Web applications and websites | Local files and system processes |
| Deployment | Cloud-based, no installation needed | Installed on local systems |
| Detection Method | Active testing of web components | File signatures and behavior analysis |
| Target Threats | Web vulnerabilities (XSS, SQL injection, etc.) | Malware, viruses, trojans |
| Updates | Automatic, cloud-based | Requires regular definition updates |
Real-world professionals rely on these tools every day. As an Information Security Officer we interviewed explained: “We use vulnerability scanning as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.” Translation: smart companies check for security issues before their websites even go live.
At Concertium, we’ve seen how organizations using online web security scanners experience fewer successful attacks. They also bounce back faster when vulnerabilities are finded, because they’ve already got a system in place to find and fix problems. From our nearly 30 years of cybersecurity experience, we can confidently say that regular scanning is one of the most effective ways to shrink your digital risk footprint.
The best part? Unlike complex security solutions that require a team of experts to manage, most cloud-based scanners are designed to be user-friendly, making professional-grade security accessible to businesses of all sizes.
Common Vulnerabilities Detected by Online Web Security Scanners
Ever wondered what lurks in the shadows of your website code? Online web security scanners are like digital detectives, sniffing out potential threats before hackers can exploit them. Let’s explore the common vulnerabilities these scanners catch—understanding these risks helps you appreciate just how valuable these tools really are.
The OWASP Top 10 and Beyond
The cybersecurity world has a “most wanted” list of sorts—the OWASP Top 10. This list, maintained by the Open Web Application Security Project, highlights the most critical web application security risks that keep security professionals up at night.
Quality online web security scanners are specifically designed to detect these heavy-hitters:
| Vulnerability Type | Description | Potential Impact |
|---|---|---|
| Injection Flaws (SQL, Command) | Untrusted data sent to an interpreter as part of a command | Data theft, deletion, or modification |
| Cross-Site Scripting (XSS) | Code injected into trusted websites viewed by other users | Session hijacking, credential theft |
| Broken Authentication | Weaknesses in authentication mechanisms | Account takeover, identity theft |
| Sensitive Data Exposure | Inadequate protection of sensitive information | Privacy violations, fraud |
| XML External Entities (XXE) | Poorly configured XML processors | Server-side file disclosure, denial of service |
| Broken Access Control | Restrictions on authenticated users not properly enforced | Unauthorized access to functionality |
| Security Misconfiguration | Insecure default configurations, open cloud storage | System compromise, data leaks |
| Cross-Site Request Forgery (CSRF) | Forces authenticated users to submit unwanted requests | Unauthorized actions on user’s behalf |
| Using Components with Known Vulnerabilities | Using libraries or frameworks with known security issues | Various impacts depending on vulnerability |
| Insufficient Logging & Monitoring | Lack of adequate logging, monitoring, and response | Prolonged time to detect breaches |
Beyond the OWASP Top 10
The OWASP Top 10 is just the beginning. Advanced online web security scanners cast a much wider net, catching less famous but equally dangerous threats.
Think of HTTP Response Splitting as digital sleight of hand, where attackers manipulate HTTP responses to perform various attacks. Or Host Header Injection, where the seemingly innocent host header becomes a pathway for exploitation.
HTTP Parameter Pollution might sound like environmental jargon, but it’s actually a clever technique where attackers confuse applications by sending multiple parameters with the same name. Meanwhile, Insecure Deserialization exploits flaws in how applications reconstruct data structures—like putting together a puzzle with pieces that don’t quite fit.
One particularly sneaky vulnerability is Server-Side Request Forgery (SSRF), which forces your server to make requests to places it should never contact. Imagine your trusted server suddenly knocking on a hacker’s door—not good!
Configuration and Outdated Software Issues
Not all vulnerabilities come from complex code flaws. Sometimes, it’s the digital equivalent of leaving your front door open uped.
SSL/TLS Misconfigurations are like having a state-of-the-art lock installed incorrectly. Your website might use encryption, but if it’s configured with weak ciphers or outdated protocols, it’s still vulnerable.
Missing HTTP Security Headers leave your users’ browsers without important security instructions. Think of these as the safety briefing before a flight—without them, everyone’s more vulnerable during turbulence.
Perhaps the most facepalm-worthy issue is Default Credentials—where admin usernames and passwords remain set to factory defaults like “admin/admin” or “password123.” It’s the digital equivalent of using “1234” as your ATM PIN.
Directory Listing Enabled is another common oversight, where servers are configured to show directory contents to anyone who asks—essentially providing a map of your website’s structure to potential attackers.
And then there’s the perennial problem of Outdated CMS Components. Those WordPress plugins you haven’t updated in months? They’re like open windows in your security perimeter.
As one Technical Director told us during our research: “We use daily vulnerability testing to guarantee our security and support our ISO certification requirements.” This highlights how regular scanning has become standard practice for organizations that take security seriously.
With over 7,000 known vulnerabilities detectable by advanced scanners in 2025, implementing an online web security scanner isn’t just smart—it’s essential. At Concertium, our nearly 30 years of experience has shown us that most websites harbor at least a few of these vulnerabilities without their owners even realizing the risk they’re taking.
Benefits of Using a Cloud-Based Online Web Security Scanner
The beauty of cloud-based online web security scanners lies in their simplicity and power. Unlike traditional security tools that demand constant attention, cloud scanners work quietly in the background, protecting your digital assets while you focus on running your business.
No Installation or Maintenance Required
Remember the days of installing software from CDs or downloading massive installation files? Cloud-based scanners have done away with all that hassle. There’s absolutely nothing to download or install on your servers. You simply sign up, point the scanner at your website, and you’re protected.
This zero-installation approach means your IT team can focus on what really matters—addressing actual security issues rather than maintaining yet another piece of software. The scanner itself gets better over time without you lifting a finger, as updates happen automatically in the cloud.
One Operations and Security Manager we worked with put it perfectly: “Every time I log in, it absolutely amazes me how much work the HostedScan team has gotten done on the interface and new integrations.” That’s the magic of cloud solutions—they evolve and improve while you sleep.
Scalability to Meet Your Needs
Whether you’re protecting a single website or managing security for hundreds of web applications, cloud-based scanners can handle it all. They grow with you.
Need to scan multiple websites simultaneously? No problem. Want to run a quick scan today but a deep, comprehensive assessment next week? That’s easily configurable. As your business expands and your web presence grows, your security tools scale right alongside you without requiring new hardware or complex reconfiguration.
The flexibility extends to threat coverage too. As new types of vulnerabilities emerge (and they always do), cloud scanners quickly incorporate detection capabilities for these new threats, keeping you protected against the latest attack methods.
Continuous Monitoring and Immediate Updates
In cybersecurity, timing is everything. Cloud-based online web security scanners excel at maintaining constant vigilance through scheduled, automated scanning. Set up daily, weekly, or monthly scans based on your risk profile, and the system takes care of the rest.
When security researchers find new vulnerabilities—which happens almost daily—cloud scanners incorporate this intelligence immediately. You benefit from these updates the moment they’re released, not days or weeks later when you remember to update your software.
This continuous approach also provides valuable historical data. Over time, you can track your security posture, watching it strengthen as you address vulnerabilities. This historical view helps demonstrate security improvements to stakeholders and auditors.
Cost-Effectiveness
Cloud-based security makes financial sense too. Rather than investing heavily upfront in expensive hardware and software licenses, you pay a predictable subscription fee. This shift from capital expenditure to operational expenditure makes budgeting more straightforward and often reduces overall costs.
The subscription model typically scales with your needs—you pay for what you use, adding coverage as your web presence expands. This flexibility prevents both overspending on unused capacity and scrambling to expand when you suddenly need more protection.
Accessibility and Collaboration
The days of security reports trapped on a single computer are long gone. Cloud-based scanners make your security information accessible from anywhere with internet access. Your team members can log in from the office, home, or while traveling to check on the latest scan results or verify that a vulnerability has been fixed.
This accessibility improves collaboration. Security findings can be shared instantly with developers who need to fix issues, executives who need to understand risk, and compliance teams who need to document your security efforts. Role-based access ensures everyone sees exactly what they need—no more, no less.
As the CEO of one of our clients noted: “We partnered with HostedScan to solve a critical need for our business: continuous, effective, and automated vulnerability scanning.” This perfectly captures why so many organizations are moving to cloud-based scanning solutions.
At Concertium, we’ve witnessed how organizations using cloud-based online web security scanners typically identify and fix vulnerabilities 60% faster than those using traditional approaches. In cybersecurity, speed matters—and cloud solutions deliver it without sacrificing thoroughness or reliability.
Integrating Online Web Security Scanners into Your Cybersecurity Infrastructure
Adding an online web security scanner to your toolkit is a bit like getting a new security guard for your building. But that guard needs to know how to work with your existing team. Let’s talk about how to make your new scanner play nicely with everything else you’ve got going on.
API Integration for Automation
Think of APIs as the universal language that lets your security tools talk to each other. Modern online web security scanners come with powerful APIs that can transform how your security operations work:
Your scanner can automatically kick off when developers push new code, making security a natural part of your development cycle rather than an afterthought. You can pull scan results directly into your existing dashboards, so you’re not constantly switching between different tools to get the full picture.
One Web Architect we spoke with put it perfectly: “I like the autonomy of running and re-running tests after fixes. This ensures that we will never deploy new vulnerabilities to production.” This shows how seamless integration turns security from a roadblock into a natural part of your workflow.
Compatible with Existing Security Tools
Good security is like a symphony – all the instruments need to play together harmoniously. Your online web security scanner can connect with:
Your SIEM system to provide context for other security events you’re monitoring. When the scanner finds something concerning, it can automatically create tickets in systems like Jira or GitHub, ensuring issues don’t fall through the cracks. It can even send alerts to Slack or Teams when critical vulnerabilities appear, so your team knows immediately.
Just remember to configure your Web Application Firewall (WAF) to allow legitimate scanning traffic – otherwise, your security tools might end up fighting each other!
Incorporating Scanning into Your Cybersecurity Strategy
To get real value from your online web security scanner, it needs to be a core part of your broader security approach, not just a box to check. Start by establishing clear policies about what gets scanned and how often. Different assets have different risk profiles – your customer-facing payment portal probably needs more frequent scanning than your internal holiday calendar app.
Be clear about who’s responsible for reviewing scan results and making sure vulnerabilities get fixed. Without accountability, even the best scanner becomes just another tool generating reports nobody reads.
At Concertium, we often recommend a tiered approach based on risk exposure. Your public-facing production websites might need daily comprehensive scans, while development environments could get by with quick scans triggered by new code deployments. This balanced approach gives you thorough coverage where it matters most without overwhelming your team.
Real-World Integration Example
Here’s how this might look in practice:
| Asset Type | Scan Frequency | Scan Depth | Integration Points |
|---|---|---|---|
| Public-facing production websites | Daily | Comprehensive | SIEM, WAF, Ticketing |
| Customer portals | Weekly | Comprehensive | SIEM, WAF, Ticketing |
| Internal web applications | Monthly | Standard | Ticketing |
| Development environments | With each build | Quick | CI/CD, Developer notifications |
This isn’t just theory – we’ve seen this approach work for numerous organizations, providing the right balance of security and efficiency.
Leveraging AI-Improved Observability
At Concertium, our Collective Coverage Suite (3CS) with AI-improved observability works hand-in-hand with online web security scanners. This partnership does more than just find vulnerabilities – it helps you understand which ones matter most right now.
By correlating scan findings with actual attack attempts, we can help you focus on fixing the vulnerabilities that hackers are actively trying to exploit. In some cases, we can even automatically block attack attempts while you’re working on the permanent fix.
As the Technical Director at a network security company told us: “We use daily vulnerability testing to guarantee our security and support our ISO certification requirements.” Their experience shows how regular scanning becomes a cornerstone of a mature security program, not just an occasional check-up.
For more information on building a comprehensive cybersecurity strategy that incorporates vulnerability scanning, visit our Cybersecurity Strategy guide.
Limitations of Online Web Security Scanners and How to Mitigate Them
Let’s face it—while online web security scanners are incredible tools, they’re not magical security solutions that catch everything. Understanding their limitations is like knowing your favorite superhero’s weaknesses—essential for making sure you’re truly protected. Let’s explore these limitations and how you can work around them to keep your digital assets secure.
The Challenge of False Positives and Negatives
One of the most common frustrations with any scanning technology is accuracy issues. It’s a bit like fishing—sometimes you catch things you didn’t want, and sometimes the big one gets away.
False positives happen when your scanner frantically waves red flags about vulnerabilities that don’t actually exist. This can send your team on wild goose chases, investigating issues that aren’t real threats. It’s like your car’s check engine light coming on when nothing’s actually wrong—annoying and time-consuming.
Even more concerning are false negatives—actual vulnerabilities that your scanner misses completely. These are particularly dangerous because they leave you with a false sense of security, like thinking your doors are locked when they’re actually wide open to intruders.
To tackle these accuracy issues, consider using scanners with built-in verification features. Many of our clients at Concertium find that using multiple scanning tools provides a more comprehensive safety net, as different scanners excel at finding different types of vulnerabilities.
Having security professionals manually verify a sample of scan results periodically can also help gauge how accurate your scanner really is. Think of it as a “trust but verify” approach—the scanner does the heavy lifting, but human expertise provides the final say.
Server-Side and Authentication Limitations
Online web security scanners primarily test what they can see from the outside, which creates some blind spots:
They can’t directly peek at your server-side code to analyze it for vulnerabilities—they can only infer issues from how your application responds to their tests. Areas of your site hidden behind login screens might remain unexplored unless you specifically configure authenticated scanning. And complex user flows with multiple steps can be challenging for scanners to steer completely.
To overcome these limitations, set up authenticated scanning by providing your scanner with valid credentials to test protected areas. For thorough protection, complement your online web security scanner with Static Application Security Testing (SAST) tools that analyze your source code directly. If your application relies heavily on APIs, implement specific API security testing to cover those components.
Some advanced scanners can follow recorded user paths, allowing them to test complex flows more thoroughly. Think of it as giving your scanner a map instead of having it wander around trying to find everything on its own.
Dynamic Content and Modern Web Technologies
Modern websites with their fancy JavaScript frameworks and dynamic content loading can give scanners headaches:
Single-page applications (SPAs) and JavaScript-heavy sites often confuse basic scanners because they don’t render pages the same way browsers do. Content that loads asynchronously might be missed entirely if the scanner doesn’t wait long enough or doesn’t properly execute JavaScript. And if you’re using custom or proprietary frameworks, scanners might struggle to understand how they work.
To address these modern web challenges, look for scanners with browser-based crawling capabilities. These are specifically designed to handle JavaScript-heavy sites more effectively. Sometimes the simple solution of configuring longer scan times gives scanners the opportunity to interact more thoroughly with dynamic content.
Another practical approach is providing your scanner with a sitemap or API specification, essentially giving it a blueprint of your application to improve coverage.
Business Logic Vulnerabilities
Some of the trickiest vulnerabilities to detect are those related to your application’s specific business logic:
Flawed authorization checks might allow users to access functionality they shouldn’t. Process sequence issues can create vulnerabilities in the way operations are carried out. And data validation problems that are specific to your business context might slip through general scanning approaches.
“While online scanners are powerful, they should be part of a comprehensive security approach that includes manual testing, code review, and developer education.” – Cybersecurity Expert
These business logic vulnerabilities require a more human touch. Supplement your scanning with manual testing to identify logical flaws that automated tools might miss. Design specific tests that validate your application’s business rules and conduct periodic reviews of your application logic and security controls.
Comprehensive Mitigation Approach
At Concertium, our nearly 30 years of cybersecurity experience has taught us that a layered approach works best. We recommend combining automated scanning with manual testing and code review for maximum protection. Implementing continuous security through regular scanning, plus event-triggered scans after deployments, helps catch issues early.
Educating your development team about common vulnerabilities creates an additional line of defense, as they can prevent issues before they even make it into the code. And don’t hesitate to leverage expert support to interpret results and provide guidance—sometimes an experienced eye can spot patterns that might otherwise be missed.
By understanding these limitations and implementing thoughtful mitigation strategies, you’ll ensure your online web security scanner delivers maximum value while maintaining comprehensive security coverage. It’s not about finding a perfect solution—it’s about creating a balanced approach that significantly reduces security incidents while making the best use of your resources.
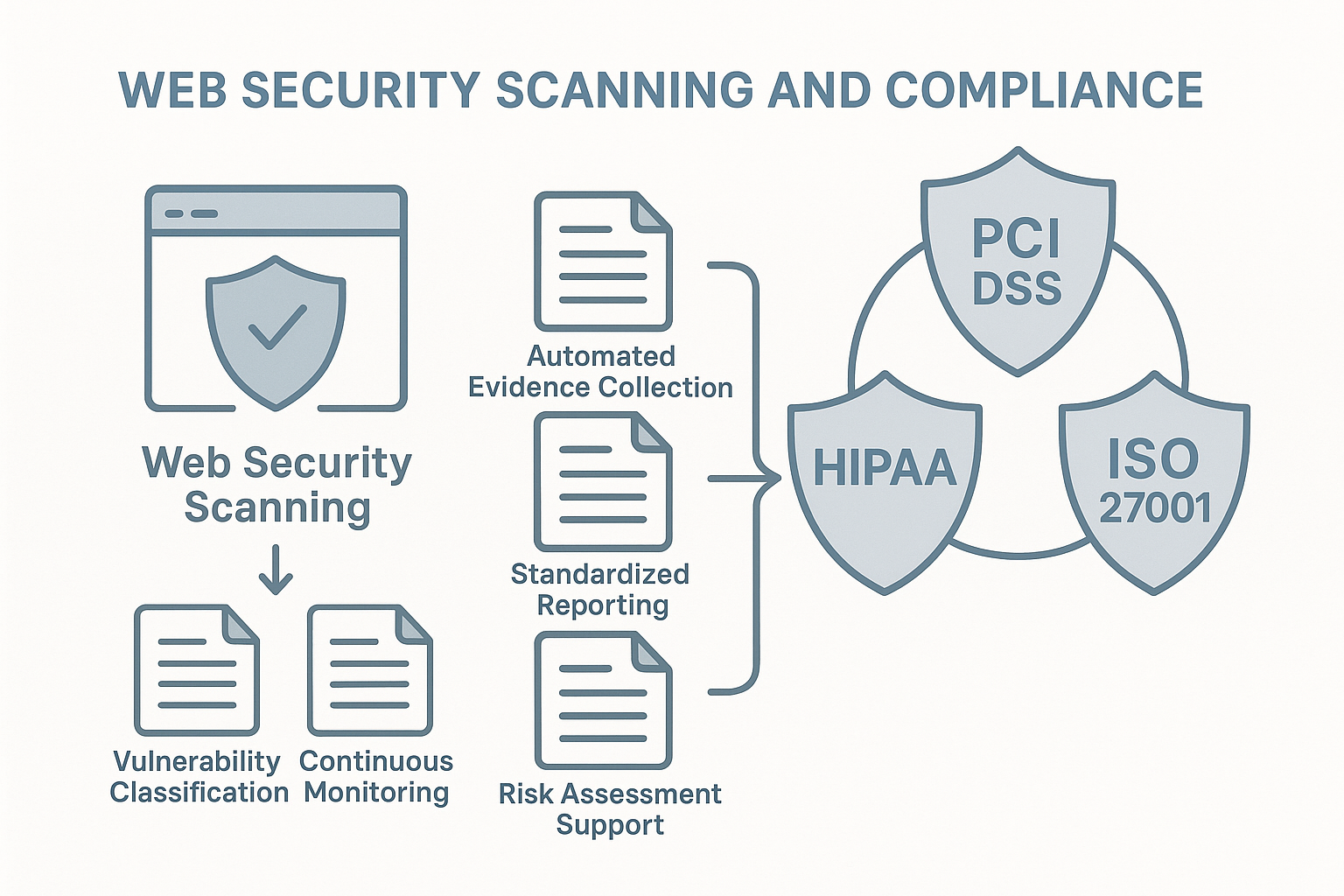
How Online Web Security Scanners Aid in Compliance and Regulation
In today’s complex regulatory landscape, compliance isn’t just a nice-to-have—it’s absolutely essential. Online web security scanners have become invaluable allies for businesses navigating the maze of security standards and regulatory requirements. These tools don’t just protect your systems; they provide the documentation and evidence you need to demonstrate your commitment to security.
Meeting Key Compliance Standards
Different industries face varying compliance demands, and this is where web security scanners truly shine. If you’re handling payment card data, PCI DSS requires regular vulnerability scanning—and your scanner delivers those quarterly scans with proper documentation. Healthcare organizations under HIPAA need to safeguard electronic protected health information, while businesses operating in Europe must implement appropriate security measures under GDPR.
The beauty of online web security scanners is their versatility across compliance frameworks. Whether you’re working toward SOC 2 certification with its focus on security controls or implementing ISO 27001’s systematic approach to information security, these scanners provide concrete evidence of your security testing efforts.
I was particularly struck by what the Technical Director at Principle Networks shared in our research: “We use daily vulnerability testing from HostedScan to guarantee our security and support our ISO certification requirements.” Their experience perfectly illustrates how scanning directly supports certification processes—turning what could be a painful audit into a much smoother experience.
Comprehensive Reporting for Audits
When audit time rolls around, you’ll be grateful for the detailed reports these scanners generate. Modern online web security scanners create executive summaries that even your non-technical stakeholders can understand, alongside detailed technical findings for your security team.
These reports don’t just list problems—they provide risk ratings so you know what to fix first, specific remediation guidance so you know how to fix it, and historical comparisons so you can demonstrate improvement over time. Many scanners even offer compliance-specific report templates designed for particular frameworks, saving you hours of documentation work.
Continuous Compliance Monitoring
Remember when compliance was a once-a-year scramble before an audit? Those days are gone. Online web security scanners enable what we call “continuous compliance”—an ongoing state of readiness rather than periodic fire drills.
Scheduled scans run automatically, keeping you compliant without manual intervention. When something changes in your environment, change detection features alert you to new vulnerabilities. If your security posture drifts away from compliance requirements, you’ll know immediately rather than finding it during an audit.
Perhaps most valuable is the automatic evidence collection. The scanner quietly gathers and stores compliance evidence in the background, building your audit documentation day by day. When your auditor asks for evidence of your security testing program, you’re just a few clicks away from providing it.
Supporting Security Audits
Formal security audits used to strike fear into the hearts of IT teams. With online web security scanners, they become much more manageable. You can identify and address issues before auditors arrive, generate the documentation they’ll request, and verify that your security controls are functioning as expected.
I’ve seen clients use scanners for gap analysis—identifying areas where additional controls might be needed—and for remediation verification to confirm that previously identified issues have been properly resolved. This proactive approach transforms the audit from an adversarial process to a collaborative one.
Real-World Compliance Benefits
At Concertium, we’ve witnessed remarkable benefits when our clients implement online web security scanners as part of their compliance strategy. The numbers speak for themselves: organizations with regular scanning programs typically experience 30-40% shorter audit durations and significantly lower compliance costs.
Beyond the time and cost savings, we see better audit outcomes with fewer findings during formal assessments. The path to security certifications like ISO 27001 and SOC 2 becomes much smoother. Perhaps most importantly, our clients report improved stakeholder confidence—they can clearly demonstrate robust security practices to their clients and partners.
As the CEO of Cobrowse.io noted in our research: “We partnered with HostedScan to solve a critical need for our business: continuous, effective, and automated vulnerability scanning.” Their experience highlights how these tools address both security and compliance needs simultaneously—a double win for busy organizations.
With nearly 30 years in cybersecurity, we’ve helped countless organizations implement online web security scanners as part of their compliance programs. Time and again, we’ve seen that this approach not only satisfies regulatory requirements more efficiently but also results in genuinely better security. After all, that’s what compliance should be about in the first place—not just checking boxes, but actually protecting your business and your customers.
Frequently Asked Questions about Online Web Security Scanners
How do online web security scanners handle the detection of false positives and negatives?
Let’s face it – no security tool is perfect. Online web security scanners sometimes flag issues that aren’t actually there (false positives) or miss real vulnerabilities (false negatives). It’s like having a very enthusiastic security guard who occasionally mistakes your mailman for an intruder, while sometimes missing the actual burglar!
Modern scanners have gotten much smarter about this challenge. The best ones use automated verification to double-check findings before reporting them. Instead of simply saying “this might be vulnerable,” quality tools perform additional tests to confirm their suspicions.
Context matters too. Advanced scanners consider what type of application they’re testing and its environment before making judgments. It’s similar to how you might be more concerned about an open window on the ground floor than one on the 20th floor.
In our research, we found that leading scanners in 2025 “automatically validate findings to reduce false positives, labeling issues as ‘Confirmed’ when confident.” This extra verification step makes a huge difference in accuracy.
To catch those sneaky vulnerabilities that might otherwise slip through (false negatives), good scanners use multiple detection techniques for each vulnerability type. They’re constantly updated with new patterns and can test even the JavaScript-heavy parts of your application that older scanners might struggle with. Some advanced tools boast accuracy rates of up to 99.98% – not perfect, but impressively close!
What are the limitations of online web security scanners, and how can they be mitigated?
Even the best online web security scanners have their blind spots. Understanding these limitations helps you build a more complete security approach.
The biggest challenge is that scanners can only see what’s visible from the outside – they can’t directly analyze your server-side code. Think of it like a home inspector who can check your doors and windows but can’t see inside your walls. To address this, you should complement scanning with Static Application Security Testing (SAST) tools that examine your source code directly.
Areas behind login screens present another hurdle. Without proper configuration, scanners might not test your user dashboard or admin panel. Modern scanners offer authenticated scanning where you can provide login credentials or record login sequences, allowing them to test these protected areas.
Complex multi-step processes can also be tricky. A scanner might not understand that users need to add items to a cart, enter shipping info, and then payment details in a specific sequence. The solution? Record these user journeys for the scanner to follow, or supplement with some manual testing.
Perhaps the most challenging limitation is with application-specific logic. If your business rule says “premium users shouldn’t access basic user data,” a scanner won’t inherently know that’s a rule to test. This is where human testers shine and why manual penetration testing remains valuable alongside automated scanning.
Modern web technologies with heavy JavaScript and API usage can also be challenging. Choose scanners specifically designed for these architectures that include browser-based crawling capabilities.
As one security professional noted in our research: “I very much enjoy using the tool for all my mission-critical checks and final checks before launching a new website service.” This highlights an important point – scanners are incredible tools, but they work best as part of a larger security strategy.
How do online web security scanners help in maintaining compliance with security standards and regulations?
Compliance requirements can feel like a never-ending maze of paperwork and technical controls. Online web security scanners make this process significantly easier by providing much of the documentation and evidence you need.
When regulations like PCI DSS (for payment card data) or HIPAA (for healthcare information) require regular security testing, scanners automatically document when tests were performed and what was found. It’s like having a diligent assistant who keeps perfect records of all your security work.
Many scanners offer compliance-specific reports custom to particular frameworks. Need to show your PCI DSS assessor evidence of quarterly vulnerability scanning? There’s a report for that. These reports typically map findings to specific requirements within the relevant standard, making it crystal clear how your security efforts align with compliance needs.
Scanners also speak the language of compliance by categorizing vulnerabilities according to industry standards like the OWASP Top 10 or Common Weakness Enumeration (CWE). This standardized approach helps demonstrate that you’re addressing all the major risk categories.
The continuous monitoring aspect is particularly valuable. Rather than scrambling before an audit with last-minute security checks, regular scanning shows ongoing vigilance. This aligns perfectly with modern compliance frameworks that emphasize continuous security rather than point-in-time assessments.
The Technical Director at a leading security firm shared this insight: “We use daily vulnerability testing to guarantee our security and support our ISO certification requirements.” This direct connection between regular scanning and maintaining formal certifications is something we see consistently.
At Concertium, our experience shows that organizations with robust scanning programs typically spend 40% less time preparing for compliance audits and have fewer findings during formal assessments. With nearly 30 years in cybersecurity, we’ve seen how online web security scanners not only streamline compliance efforts but genuinely improve overall security.
Conclusion
In today’s threat landscape, implementing an online web security scanner isn’t just a good practice—it’s an essential component of any comprehensive cybersecurity strategy. As we’ve explored throughout this article, these powerful tools provide automated, continuous protection against an ever-changing array of web vulnerabilities.
Key Takeaways
When it comes to protecting your digital assets, online web security scanners offer incredible value. They give you proactive protection by identifying vulnerabilities before attackers can exploit them—like having a security guard who spots weaknesses in your defenses before the bad guys do.
Modern scanners offer truly comprehensive coverage, detecting thousands of vulnerability types from common issues like XSS and SQL injection to complex configuration problems. And the cloud-based nature of these tools means you’ll never have to worry about maintenance or updates—everything happens automatically behind the scenes.
What I particularly love about today’s scanning solutions is how seamlessly they integrate with existing systems. Whether you’re using Jira for ticketing or have a complex CI/CD pipeline, these scanners can plug right in and improve your overall security workflow. Plus, they generate the documentation you need for compliance requirements, making audit season much less stressful.
As one customer we researched put it: “Acunetix has played a very important role in the identification and mitigation of web application vulnerabilities. Acunetix has proven itself and is worth the cost.” This sentiment mirrors what we’ve seen at Concertium across hundreds of client engagements.
Next Steps for Protecting Your Digital Assets
If you’re ready to improve your web security posture, here’s what you should do next:
Start by assessing your current exposure with a baseline scan—you need to know where you stand before you can improve. Then, develop a thoughtful scanning strategy based on your specific assets. Which systems are most critical? Those should be scanned more frequently and thoroughly.
Don’t treat scanning as a standalone activity. Integrate it with your existing processes, especially your development lifecycle. When developers check in code, that’s a perfect trigger for an automated scan. And be sure to establish clear remediation workflows so that when vulnerabilities are finded, everyone knows exactly what to do next.
Scanning is just one piece of the security puzzle. At Concertium, we’ve spent nearly 30 years helping organizations build layered security approaches. Our Collective Coverage Suite (3CS) with AI-improved observability works alongside online web security scanners to provide additional context and automated threat response.
The digital landscape continues to evolve, and so do the threats targeting your web assets. By implementing a robust scanning program today, you’re taking a significant step toward protecting your organization’s data, reputation, and bottom line. Think of it as an insurance policy that actively works to prevent disasters rather than just paying for them afterward.
For more information about comprehensive vulnerability risk management and how it fits into your overall security strategy, visit our Vulnerability Risk Management resource page.
Remember: in cybersecurity, an ounce of prevention is worth far more than a pound of cure. Start scanning today, and sleep better tonight.