Managed Security Operations Center Services — 24/7 Threat Detection, Investigation, and Rapid Response
A Managed Security Operations Center (SOC) centralizes continuous monitoring, threat detection, and incident response to protect networks, endpoints, cloud workloads, and critical applications. It collects telemetry across your environment, correlates signals with SIEM and AI-enhanced observability, and pairs automated SOAR playbooks with human-led MDR investigations to contain threats faster and reduce dwell time. Organizations that use a managed SOC gain quicker detection, consistent compliance artifacts, and access to experienced analysts without building a full in‑house team.
This guide explains what managed SOCs do, their core functions and benefits, how AI-enhanced observability and MDR work together, the typical onboarding-to-response workflow, compliance mappings for HIPAA/PCI‑DSS/GDPR/SOC 2, and the business reasons to choose a managed provider. We use common industry terms—managed SOC, MDR, SIEM, XDR, threat hunting, vulnerability management—to give practical steps for evaluating SOC offerings and understanding how technology and process translate into measurable security outcomes.
What Are Managed Security Operations Center Services and Their Core Benefits?
A Managed Security Operations Center (SOC) service is a centralized security capability that provides 24/7 monitoring, detection, investigation, and response on your behalf. It collects logs and telemetry, applies correlation and analytics, and escalates confirmed incidents to analysts for containment and remediation—shrinking mean time to detect and respond and lowering breach impact. The core business benefits include continuous coverage, access to specialized skills, predictable security spend, and simplified compliance reporting. Below are the primary functions and benefits to evaluate when comparing managed SOC offerings.
Managed SOC services deliver clear operational advantages:
- Continuous Detection & Response: Around-the-clock monitoring identifies threats beyond standard business hours.
- Expertise on Demand: SOC analyst teams and threat hunters supplement scarce internal skills.
- Predictable Costs: A managed model converts hiring and tooling overhead into steady OPEX and lowers total cost of ownership.
- Compliance Evidence: Automated logging and audit artifacts make regulatory reporting and evidence collection straightforward.
These advantages explain why many organizations prefer managed SOCs to building internal teams and lead directly into how outsourcing enhances protection.
How Does Outsourcing Cybersecurity Operations Enhance Business Protection?
Outsourcing cybersecurity operations to a managed SOC addresses common constraints—skills shortages, coverage gaps, and variable incident volumes—by delivering a dedicated external team focused on detection, triage, and response. Providers offer shift coverage, peer review, and defined escalation paths so your organization stays continuously vigilant while internal teams work on strategic initiatives. Outsourcing also brings a mature toolchain—SIEM, EDR/XDR, NDR, threat intelligence, and SOAR—without large capital outlay, shortening time to capability. An SLA-driven model improves mean time to detect and respond, lowering financial and reputational risk. These operational gains set the stage for the SOC functions that underpin effective detection and response.
What Key Functions Define a Managed SOC Service?
A managed SOC combines technical platforms and human processes into a cohesive security operations capability. Core functions include telemetry ingestion and correlation (SIEM), endpoint and network detection (EDR/XDR/NDR), automated containment playbooks (SOAR), analyst-led MDR investigations, proactive threat hunting, and vulnerability management. Each function produces practical outputs—risk-prioritized alerts, incident tickets with timelines, remediation playbooks, and compliance reports—that drive continuous improvement. These components directly support business outcomes: reduced dwell time, prioritized remediation, and audit evidence. Seeing how these pieces connect makes clear why integrating observability, detection, and response is critical for a modern managed SOC.
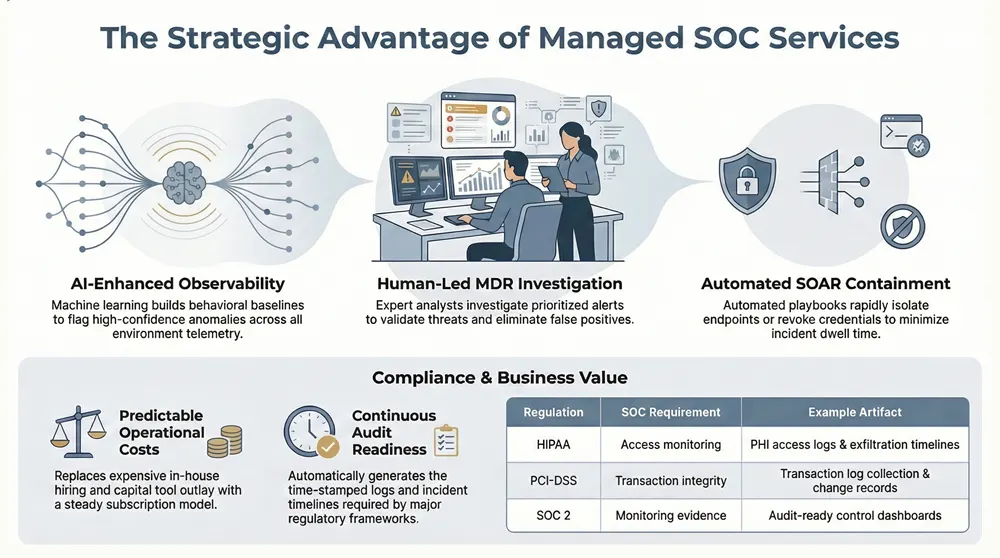
How Do Concertium’s Advanced SOC Services Leverage AI-Enhanced Observability and MDR?
Concertium’s Advanced SOC Services pair AI-Enhanced Observability with Managed Detection and Response (MDR) to speed detection and improve signal quality across complex environments. AI-enhanced observability ingests diverse telemetry—logs, endpoint signals, network flows, and cloud events—and applies anomaly detection and predictive analytics to surface high‑confidence threats. MDR supplies human analysts to investigate and contain incidents. The combined stack reduces false positives, shortens investigations, and delivers contextual alerts that enable fast containment. In short: AI filters and prioritizes, analysts validate and act—reducing dwell time and lowering risk exposure.
AI observability features behavioral baselining, cross-telemetry correlation, and automated enrichment with threat intelligence to increase signal-to-noise. That lets SOC analysts spend time on validated incidents rather than chasing routine alerts, resulting in faster remediation and clearer compliance evidence that supports ongoing tuning. With the observability layer understood, the next section explains how MDR and SIEM integrate in a managed SOC.
What Role Does AI-Enhanced Advanced Observability Play in Proactive Threat Detection?
AI-Enhanced Advanced Observability builds behavioral baselines and flags deviations that often signal early compromise, using machine learning models that compare current telemetry to historical norms. This uncovers anomalies—credential misuse, lateral movement, or data exfiltration attempts—that rule-based detections can miss. Enriching signals with contextual threat intelligence and risk scores produces prioritized alerts that direct analyst investigations. The practical effect: less alert fatigue, more focused threat hunting, faster containment, and reduced business disruption.
How Are Managed Detection and Response and SIEM Integrated in Concertium’s SOC?
In Concertium’s architecture, telemetry ingestion feeds a managed SIEM for aggregation and correlation while MDR teams perform human-in-the-loop investigation and containment guided by SIEM outputs. The data flow is: telemetry collection → correlation and enrichment → prioritized alert generation → MDR analyst triage → containment actions (automated or manual). SOAR playbooks automate repeatable containment steps—quarantine endpoints, block IPs, revoke credentials—under analyst supervision to balance speed and accuracy. Together, SIEM, MDR, and SOAR form a closed-loop system: SIEM spots patterns, MDR validates and responds, and SOAR accelerates remediation to meet consistent SLAs for detection and response.
What Is the Step-by-Step Workflow of Concertium’s Managed SOC Services?
A managed SOC workflow maps phases from assessment to continuous improvement, with clear roles, deliverables, and timeframes. It starts with a gap analysis and onboarding, moves through sensor deployment and tuning, shifts into 24/7 monitoring and incident handling, and continues with reporting and iterative refinement. This phased approach ensures visibility before trust and tailors response playbooks to each client’s environment and risk priorities. Below is a concise numbered workflow for quick evaluation and featured-snippet clarity.
- Initial Assessment: Environment discovery and risk gap analysis to set scope and priorities.
- Deployment & Tuning: Install agents and configure log collection; tune correlation rules and AI models.
- 24/7 Monitoring & Triage: Continuous detection with analyst triage and prioritized incident workflows.
- Containment & Remediation: Run SOAR playbooks and analyst-led response to contain threats.
- Reporting & Optimization: Deliver audit-ready reports, conduct threat hunts, and refine detection logic.
This workflow shows the path from onboarding to mature SOC operations and leads into details about continuous monitoring and vulnerability management.
Introductory table: phases, activities, deliverables and timeframes for decision-makers.
This phase table sets expectations for onboarding and ongoing SOC operations and helps procurement plan resource allocation. The next section explains how continuous monitoring, SLAs, and escalation work in live SOC environments.
How Does Continuous 24/7 Monitoring and Incident Response Operate?
Continuous monitoring depends on a shift-based analyst model, defined escalation paths, and SLA targets that prioritize high-risk alerts for immediate action. Typical SLAs cover time-to-acknowledge for critical alerts and time-to-contain for confirmed incidents; these metrics steer operations and populate executive dashboards. Incident response follows triage, containment, eradication, and recovery, with communication protocols that notify stakeholders based on impact and data sensitivity. Detection-to-containment timelines improve when AI observability supplies high-confidence alerts and SOAR automates containment steps, enabling teams to reduce dwell time consistently. These operational details flow naturally into vulnerability management and threat hunting practices.
What Processes Support Vulnerability Management and Threat Hunting?
Vulnerability management and threat hunting are proactive SOC activities that shrink exposure and reveal hidden compromises before they escalate. Vulnerability workflows include scheduled scanning, prioritized remediation based on exploitability and asset criticality, and integration with patch systems to track closure. Threat hunting builds hypotheses from intelligence—IOC enrichment, lateral movement indicators, and anomaly detection—to run targeted searches across telemetry stores. Outputs are prioritized vulnerability dashboards and hunting reports that feed change management and security roadmaps, lowering systemic risk and improving detection capability over time.
These processes close the loop between detection and remediation, strengthening resilience and preparing organizations for compliance audits.
How Do Managed SOC Services Support Compliance with HIPAA, PCI-DSS, GDPR, and SOC 2?
A managed SOC supports regulatory compliance by enforcing logging and retention policies, monitoring access, and producing audit-ready artifacts mapped to each framework. The SOC’s monitoring and reporting supply the evidence auditors need—time-stamped logs, incident timelines, change records, and policy alerts—so organizations can demonstrate ongoing controls. For each regulation, SOC activities map to specific requirements: HIPAA needs PHI access monitoring, PCI‑DSS requires transaction and access logging, GDPR emphasizes data access and breach notification, and SOC 2 demands control evidence and continuous monitoring. The table below maps regulations to SOC capabilities and example artifacts.
This mapping illustrates how a managed SOC provides both technical controls and the artifacts auditors expect, and it leads into the framework-specific deliverables Concertium supports.
What Compliance Frameworks Are Addressed by Concertium’s SOC Solutions?
Concertium’s SOC solutions address key frameworks—HIPAA, PCI‑DSS, GDPR, and SOC 2—through tailored detection rules, retention policies, and audit packages. For HIPAA we focus on PHI access and privileged activity; for PCI‑DSS we emphasize transaction logging and segmentation monitoring; for GDPR we prioritize data access controls and rapid breach reporting; for SOC 2 we provide continuous control monitoring and attestation support. Deliverables include configurable dashboards, scheduled compliance reports, and incident packages ready for auditors. These framework mappings align security operations with regulatory expectations and reduce audit overhead for internal teams.
How Does SOC Compliance Reporting Facilitate Regulatory Adherence?
SOC compliance reporting standardizes evidence collection and delivers scheduled and on-demand artifacts auditors and regulators require—weekly or monthly SOC summaries, incident logs, and control test outputs. Reports map alerts to policy violations, show remediation timelines, and present KPIs like time-to-detect and time-to-contain that auditors use to evaluate control effectiveness. Customizable thresholds and report cadences let organizations meet industry needs while preserving operational focus. Clear reporting creates an audit trail that supports compliance and drives continuous improvement in detection and response.
What Are the Business Advantages of Choosing Concertium for Managed SOC Services?
Choosing a managed SOC partner affects your risk posture, operating costs, and access to advanced capabilities. Concertium centers its offering on AI-Enhanced Observability, Managed Detection and Response, and a Collective Coverage Suite (3CS) that mixes best-in-class tools with expert analysts. The business benefits are measurable: shorter incident dwell time, predictable security spend, and faster compliance readiness. Concertium’s approach blends telemetry, MDR analyst workflows, and automation to deliver consistent SLAs and detections tuned to your environment. The table below summarizes attributes procurement teams typically weigh when selecting a managed SOC partner.
The list below highlights specific financial and risk-reduction advantages of engaging a managed SOC.
- Lower Operational Costs: Outsourcing avoids fixed hiring and training expenses while providing scale.
- Reduced Breach Impact: Faster detection and containment lower remediation and reputational costs.
- Access to Advanced Technology: Providers deliver AI-enhanced observability and MDR without capital investment.
How Do Managed SOC Services Reduce Risk and Operational Costs?
Managed SOC services lower risk by shortening detection and containment timelines and by prioritizing remediation of the most exploitable vulnerabilities. Operational costs fall because managed services replace expensive hiring cycles with predictable subscription pricing and include tooling, maintenance, and analyst staffing. Avoided breach costs—legal fees, regulatory fines, incident response, and customer notifications—strengthen the business case for outsourcing SOC capabilities. Quantifying these savings helps procurement weigh investment against residual risk. Understanding cost and risk drivers shows why collaborative engagements matter for long-term security outcomes.
Why Is a Collaborative Partnership Approach Critical in Cybersecurity Operations?
A collaborative partnership ensures the managed SOC and client share responsibility: the provider handles detection and response while the client retains contextual knowledge, change control, and remediation workflows. The model includes joint playbooks, shared dashboards, regular reviews, and agreed escalation criteria so security operations align with business priorities. Concertium emphasizes collaboration so playbooks reflect real processes and responses are rapid and coordinated. Clear roles and a steady communication cadence sustain continuous improvement and keep both parties accountable for security outcomes.
For teams ready to act, Concertium offers consultative assessments and evidence-driven onboarding to align SOC operations with business risk—helping organizations reach time-to-value faster and improve detection and response measurably.
Which Industry-Specific Managed SOC Solutions Does Concertium Offer?
Managed SOC deployments must reflect sector-specific telemetry, compliance needs, and threat priorities; Concertium adapts monitoring, detection rules, and playbooks for healthcare, financial services, manufacturing, retail, and government environments. Sector tailoring means prioritizing PHI access and HIPAA in healthcare, transaction integrity and PCI controls in finance, OT/ICS visibility in manufacturing, payment and POS monitoring in retail, and data sovereignty and APT defense in government. These targeted configurations surface meaningful alerts and cut false positives tied to normal industry activity. The bullets below summarize typical sector priorities and controls.
- Healthcare: Monitor PHI access, privileged accounts, and data exfiltration attempts to meet HIPAA requirements.
- Financial Services: Focus on transaction logging, fraud-detection patterns, and enhanced logging for payment systems.
- Manufacturing: Integrate OT/ICS telemetry to spot anomalous control commands and lateral movement in industrial networks.
How Are SOC Services Tailored for Healthcare, Financial, and Manufacturing Sectors?
In healthcare, SOCs prioritize PHI monitoring, access audits, and rapid breach notification to satisfy HIPAA and protect patient data. Financial-sector SOCs increase logging around payment systems, monitor transaction integrity, and enforce segregation of duties to support PCI‑DSS and financial regulations. Manufacturing SOCs extend observability into OT and ICS, combining network flow analysis with asset inventories to detect control-plane anomalies and safety-impacting incidents. Each industry approach includes tailored playbooks, prioritized detection rules, and compliance-oriented reporting to match sector risk profiles.
What Unique Cybersecurity Challenges Do Retail and Government Organizations Face?
Retail faces payment-card compromises, POS-targeting malware, and supply-chain risks from third-party integrations that can introduce vulnerabilities into transaction paths. SOC controls for retail prioritize payment monitoring, third-party integration vetting, and fast containment of POS incidents. Government organizations confront targeted APTs, data sovereignty constraints, and strict regulations; SOCs for government emphasize threat intelligence integration, long-term artifact retention, and secure evidence handling. Addressing these challenges requires specialized detection signatures, bespoke threat-hunting playbooks, and governance that respects regulatory and sovereignty constraints.
This sector-focused analysis shows how managed SOC building blocks—observability, MDR, SOAR, and compliance reporting—are applied to reflect industry priorities and operational realities. Aligning SOC requirements with sector needs yields stronger protection and clearer compliance pathways.
Concertium Contact and Next Steps
When you’re ready to evaluate managed SOC options, Concertium offers consultative assessments, AI-Enhanced Advanced Observability, managed MDR, and a Collective Coverage Suite (3CS) built to accelerate detection and response while supporting compliance objectives. Interested teams can request an assessment or schedule a vulnerability scan to benchmark exposure and plan a tailored SOC deployment. Concertium’s operations and contact resources are available to support procurement and technical teams through the transition to managed security operations.
Frequently Asked Questions
What types of organizations benefit most from Managed SOC services?
Managed SOC services suit organizations that need continuous security coverage but lack the scale or specialist staff to run an in-house SOC. Typical beneficiaries include healthcare, finance, retail, and government—sectors with strict regulatory demands and distinct threat profiles. A managed SOC lets these organizations strengthen security and compliance without the overhead of hiring and training a full internal team, so they can stay focused on their core business.
How does a Managed SOC handle incident response?
A Managed SOC follows a structured incident response lifecycle: detection, triage, containment, eradication, and recovery. Alerts are prioritized by risk and routed to analysts for investigation. Automated playbooks speed containment—isolating affected systems or blocking malicious IPs—while analysts validate actions and guide remediation. This process minimizes damage and reduces dwell time, helping preserve business continuity and protect sensitive data.
What technologies are typically used in a Managed SOC?
A Managed SOC leverages a mix of technologies to maximize visibility and speed: SIEM for log aggregation and correlation, EDR/XDR for endpoint visibility, NDR for network signals, threat intelligence for contextual enrichment, and SOAR for automation. Together these tools enable proactive detection and rapid response, supported by analyst expertise through MDR.
How does a Managed SOC support compliance with regulations?
Managed SOCs help meet regulatory requirements—HIPAA, PCI‑DSS, GDPR, SOC 2—by providing continuous logging, monitoring, and report generation that produce audit-ready artifacts like access logs and incident timelines. By maintaining controls and evidence, a managed SOC streamlines audits and reduces the risk of compliance gaps and penalties.
What is the typical onboarding process for a Managed SOC?
Onboarding usually starts with an assessment to identify gaps and priorities, followed by deployment of agents and log collection, then baseline tuning of detection rules and AI models. Once monitoring begins, the SOC runs 24/7 detection and incident management while continuously refining rules and playbooks based on real incidents and evolving threats.
Can a Managed SOC integrate with existing security tools?
Yes. A Managed SOC integrates with an organization’s existing SIEM, EDR, ticketing, and other security tools to boost visibility without forcing a wholesale tool replacement. Integration enables efficient use of current investments while improving monitoring and response capabilities.
What are the cost implications of using a Managed SOC?
Using a Managed SOC typically lowers total cost of ownership by converting fixed hiring and tooling expenses into predictable operational fees. The model includes tooling, maintenance, and analyst staffing, and faster detection/response reduces the financial impact of incidents—making managed SOCs a cost-effective option for many organizations.
Conclusion
Managed Security Operations Center services give organizations continuous threat detection, expert analysis, and compliance support to strengthen cybersecurity posture. By combining advanced technology with skilled analysts, businesses can shorten response times and lower operational costs. Partnering with a managed SOC also streamlines regulatory alignment and supports a proactive risk-management approach. To learn how Concertium can tailor a managed SOC for your organization, request an assessment today.